Method for confirming service information offline by utilizing fingerprint technology
A technology of business information and instruction information, applied in the field of business authorization, can solve the problems of lack of true consistency, inability to guarantee consistency, and differences in information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment ( 1
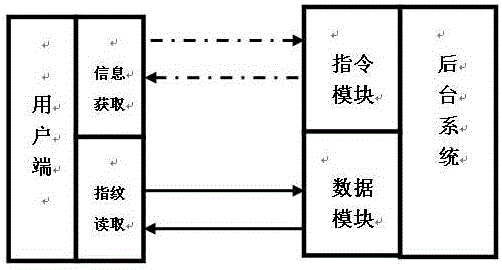
[0024] Embodiment (1): The business information and fingerprint data of business personnel collected by the system in advance are compared with the business information and fingerprint data of business personnel obtained offline to realize the confirmation of the authenticity of business and business personnel, including the following Business Process:
[0025] S1. The system completes the authentication of the business, and stores the collected business information and fingerprint data of the business personnel in the system.
[0026] S2. The system first sends instruction information to the user terminal to confirm the identity of the business and business personnel; or the user first sends request information to the system through the user terminal to confirm the identity of the business and business personnel.
[0027] S3. Start the functional module on the user end to confirm the identity of the business personnel by fingerprint, and read the fingerprint data of the busin...
Embodiment ( 2
[0030] Embodiment (2): By comparing the business information and fingerprint data of business personnel previously collected by the system with the business information and fingerprint data of business personnel obtained offline, the mandatory confirmation of the authenticity of the identity of business and business personnel is realized. Including the following business processes:
[0031] S1. The system completes the authentication of the business, and stores the collected business information and fingerprint data of business personnel in the system.
[0032] S2. The system first sends instruction information to the user terminal to confirm the identity of the business and business personnel; or the user first sends request information to the system through the user terminal to confirm the identity of the business and business personnel.
[0033] S3. Start the functional module on the user end to confirm the identity of the business personnel by fingerprint, and read the fin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com