Trusted boot method and apparatus for mobile operation system
A mobile operating system and trusted technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve the problems of low security, achieve good security performance, improve security reliability, security algorithms and storage areas are reliable Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] The following will clearly and completely describe the technical solutions in the embodiments of the present invention with reference to the accompanying drawings in the embodiments of the present invention. Obviously, the described embodiments are only some, not all, embodiments of the present invention.
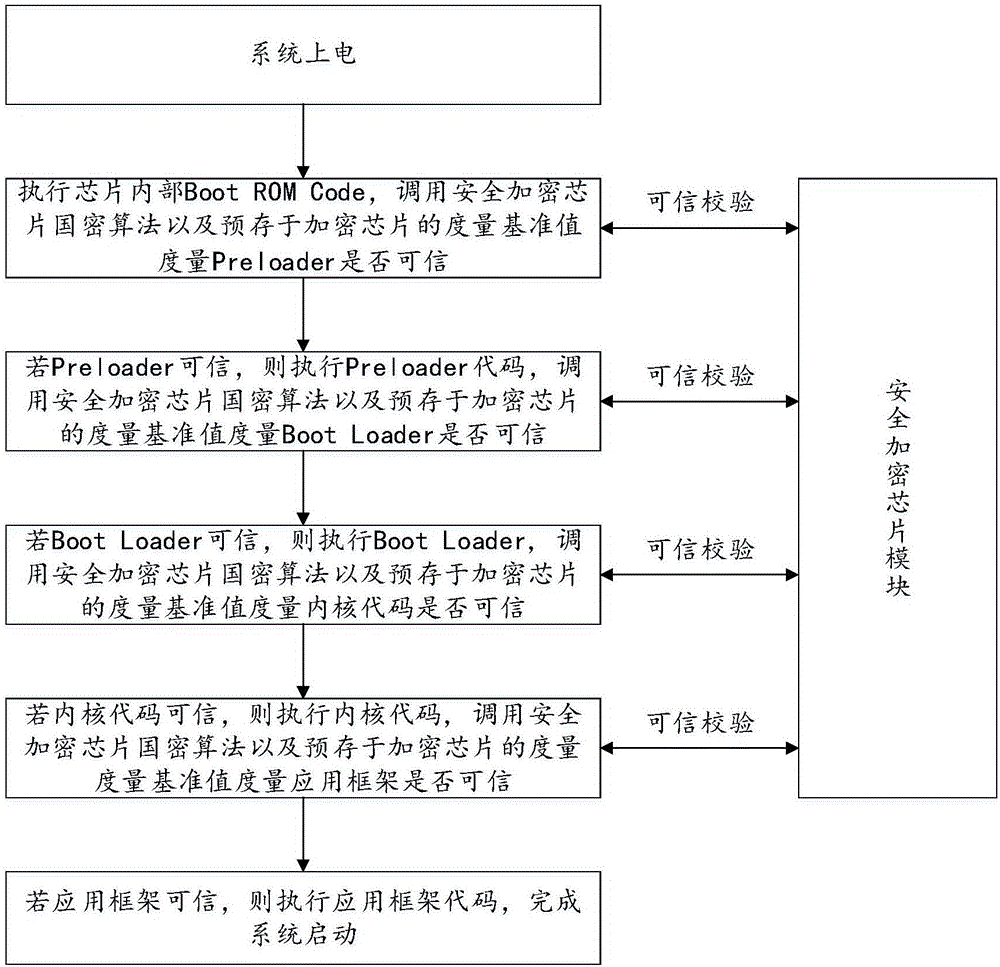
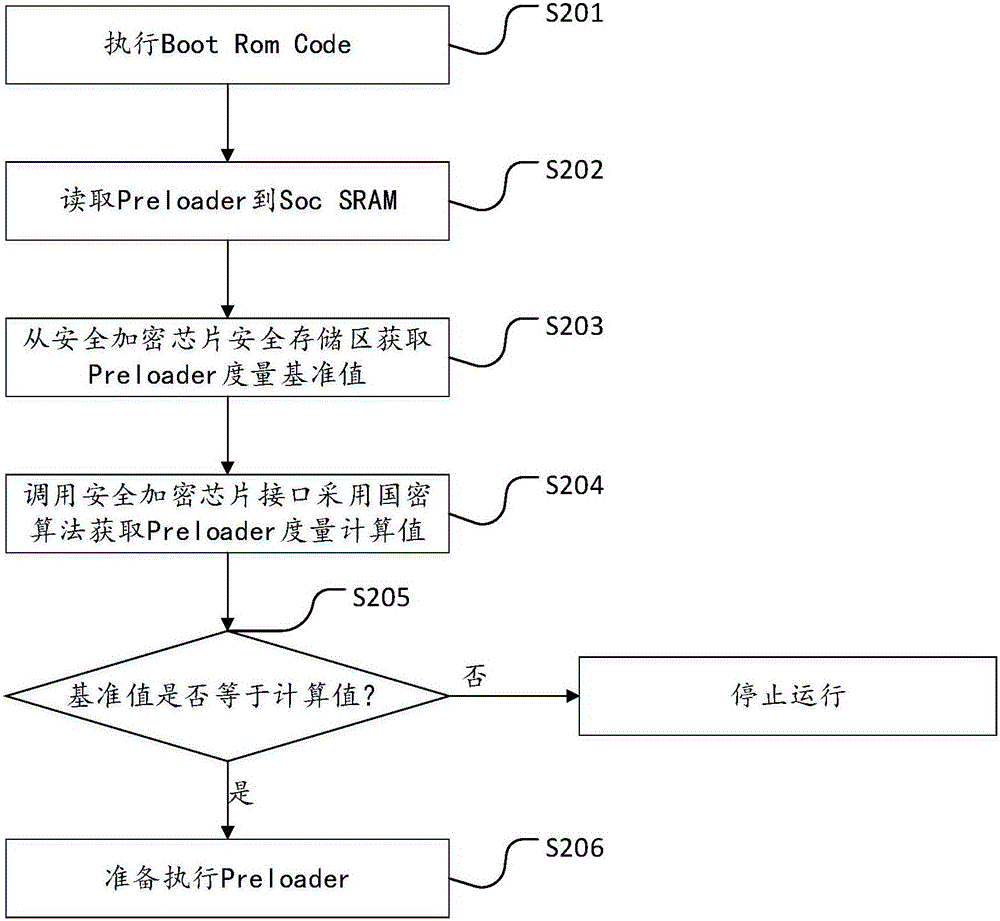
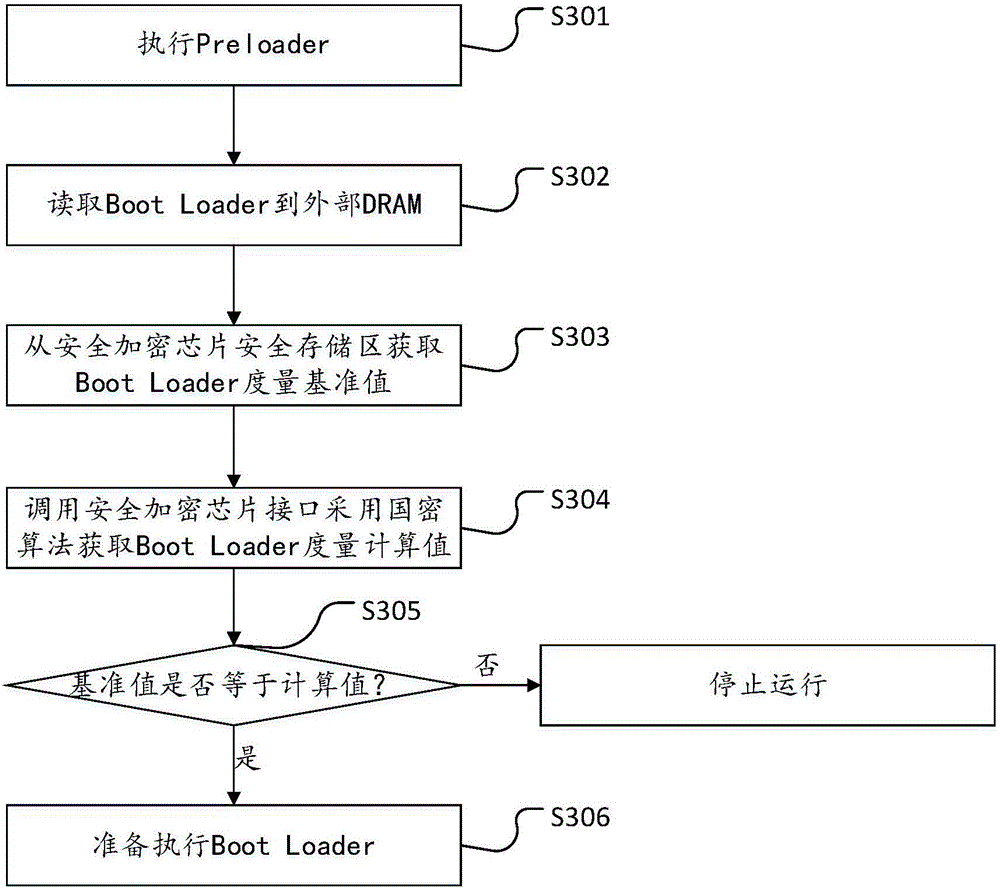
[0058] see figure 1 , figure 1 It is the mobile operating system start-up flow chart provided by the embodiment of the present invention, combined with the trusted start-up method of the mobile operating system provided by the embodiment shown in the present invention, the difference between the structure diagram shown in this embodiment and the flow of the mobile operating system in the prior art It lies in: adding a secure encryption chip module and a trusted verification process. The secure encryption chip has the highest security level, supports national secret encryption algorithms and has a built-in secure encrypted storage area.
[0059] The overview of the ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap