User login method, user terminal and server
A technology of user terminals and servers, applied in the electronic field, can solve problems such as low security, achieve the effect of improving security and solving low security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
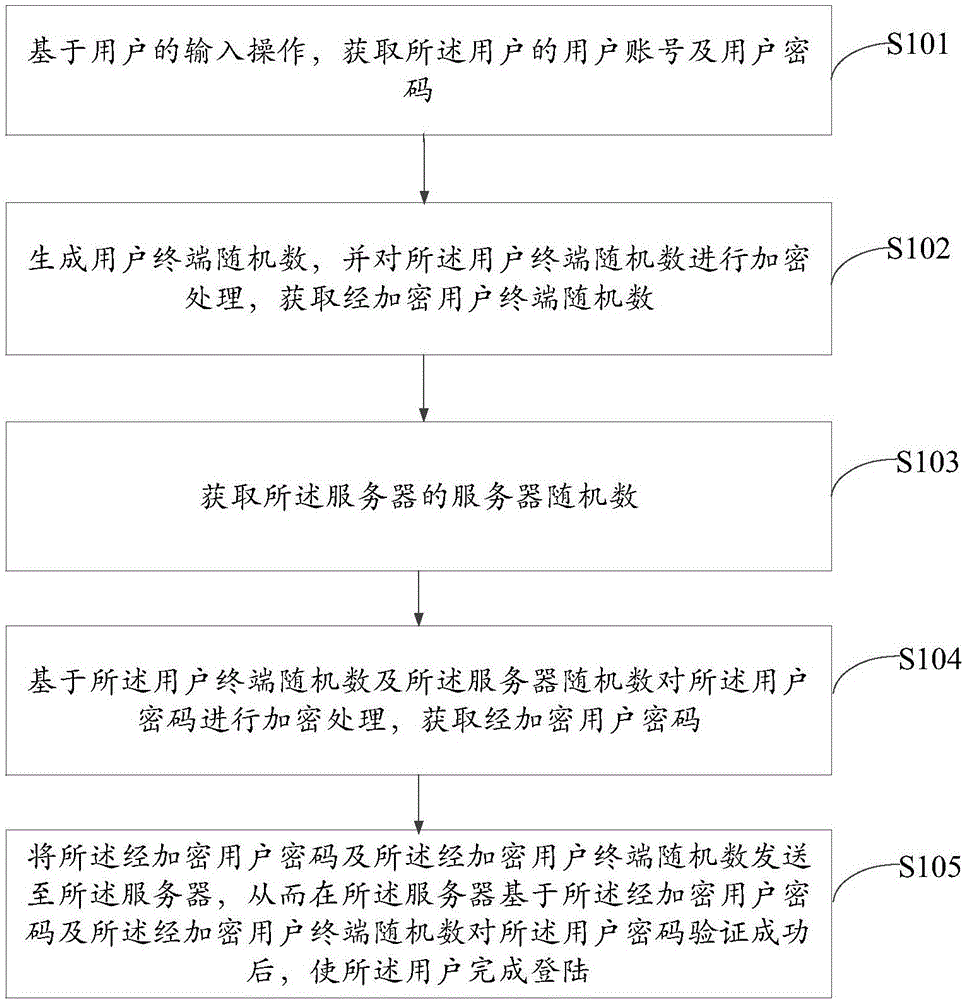
[0078] Please refer to figure 1 , is a flow chart of a user login method provided in Embodiment 1 of the present application, the method is applied to a user terminal, and the user terminal is connected to a server, and the method includes:
[0079] S101: Obtain the user account and user password of the user based on the user's input operation;
[0080] S102: Generate a random number of the user terminal, and encrypt the random number of the user terminal, and obtain the encrypted random number of the user terminal;
[0081] S103: Obtain the server random number of the server;
[0082] S104: Encrypt the user password based on the user terminal random number and the server random number to obtain an encrypted user password;
[0083] S105: Send the encrypted user password and the encrypted user terminal random number to the server, so that the user password is verified at the server based on the encrypted user password and the encrypted user terminal random number After the v...
Embodiment 2
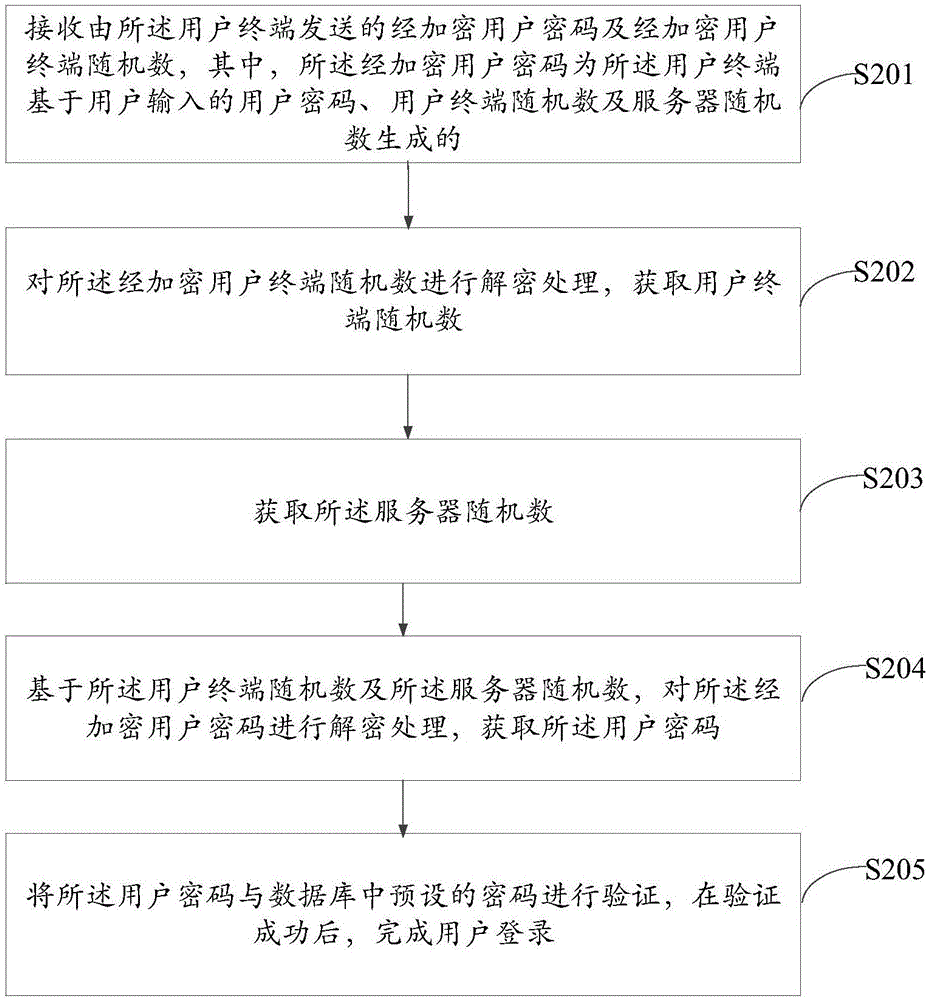
[0107] Based on the same inventive concept as Embodiment 1 of this application, please refer to figure 2 , is a flow chart of a user login method provided in Embodiment 2 of the present application. The method is applied to a server, and the server is connected to the user terminal as in Embodiment 1. The method includes:
[0108] S201: Receive the encrypted user password and the encrypted user terminal random number sent by the user terminal, wherein the encrypted user password is the user password input by the user terminal based on the user, the user terminal random number and the server random number Generated;
[0109] S202: Decrypt the encrypted user terminal random number to obtain the user terminal random number;
[0110] S203: Obtain the server random number;
[0111] S204: Based on the user terminal random number and the server random number, decrypt the encrypted user password to obtain the user password;
[0112] S205: Verify the user password with the preset p...
Embodiment 3
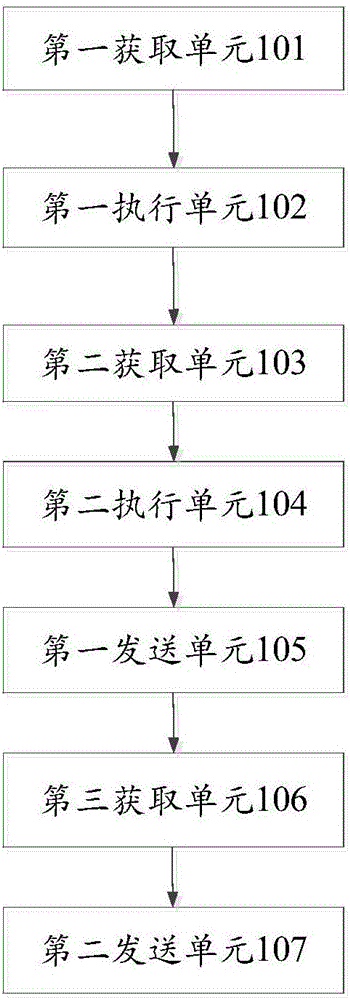
[0132] Based on the same inventive concept as Embodiment 1 of this application, please refer to image 3 , which is a structural block diagram of a user terminal provided in Embodiment 4 of the present application, where the user terminal includes:
[0133] The first obtaining unit 101 is configured to obtain the user account and user password of the user based on the user's input operation;
[0134] The first execution unit 102 is configured to generate a user terminal random number, and perform encryption processing on the user terminal random number, to obtain an encrypted user terminal random number;
[0135] The second acquiring unit 103 is configured to acquire the server random number of the server;
[0136] The second execution unit 104 is configured to encrypt the user password based on the random number of the user terminal and the random number of the server, and obtain an encrypted user password;
[0137] The first sending unit 105 is configured to send the encry...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com