Data interaction method, device and system
A data interaction and data packet technology, applied in the field of data interaction, can solve the problems of data packet filtering failure and low network security, and achieve the effect of improving network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
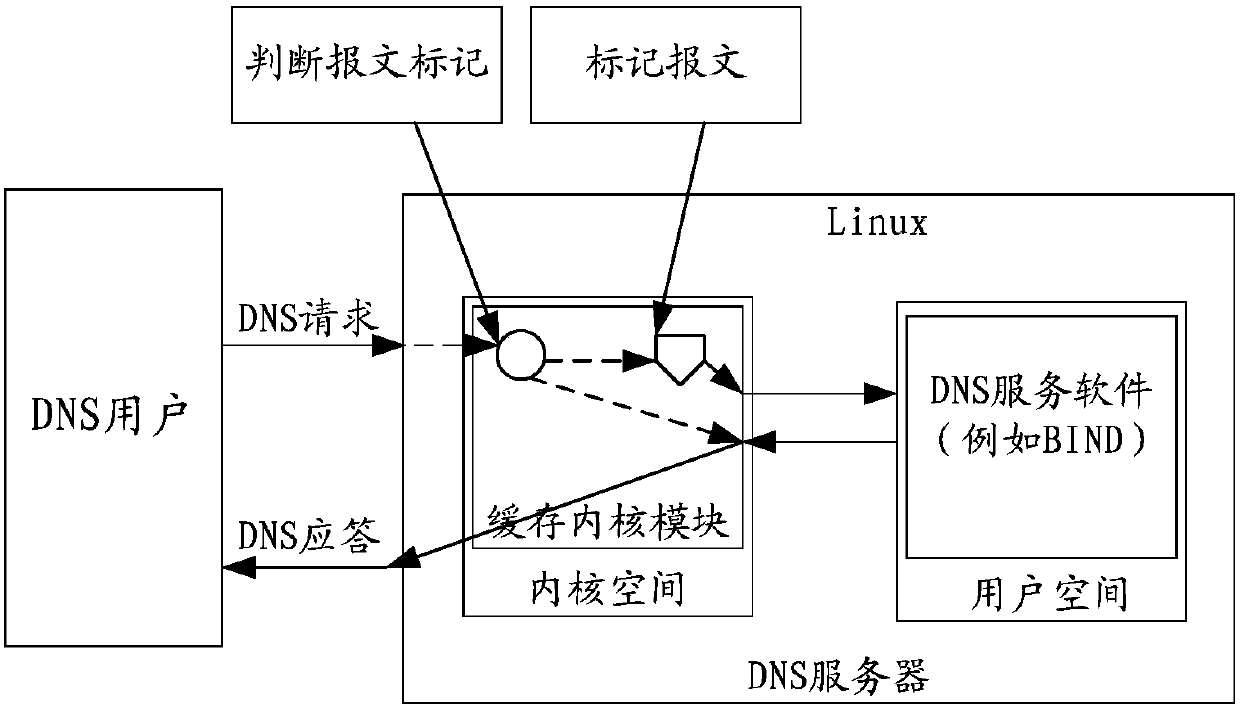
[0045] This application provides a system for data interaction. The data interaction system includes: a terminal and a server, wherein the kernel cache module in the server marks the received data packet request message, wherein the mark is a preset mark.
[0046] Specifically, the data interaction system provided by the embodiment of the present application can be applied to the DNS response method. In order to prevent DNS messages from being repeatedly processed by the system due to unmarked preset marks, and the kernel state DNS cache is intercepted by using the netfilter network framework After the request is made, the NIC interface will be called directly to return the packet after the packet is sealed, making other packet filters such as iptables invalid, making the data unusable in security verification scenarios and cloud vpc scenarios.
[0047] The preset message type provided in the data interaction system provided by the present application is a DNS message, and if ...
Embodiment 2
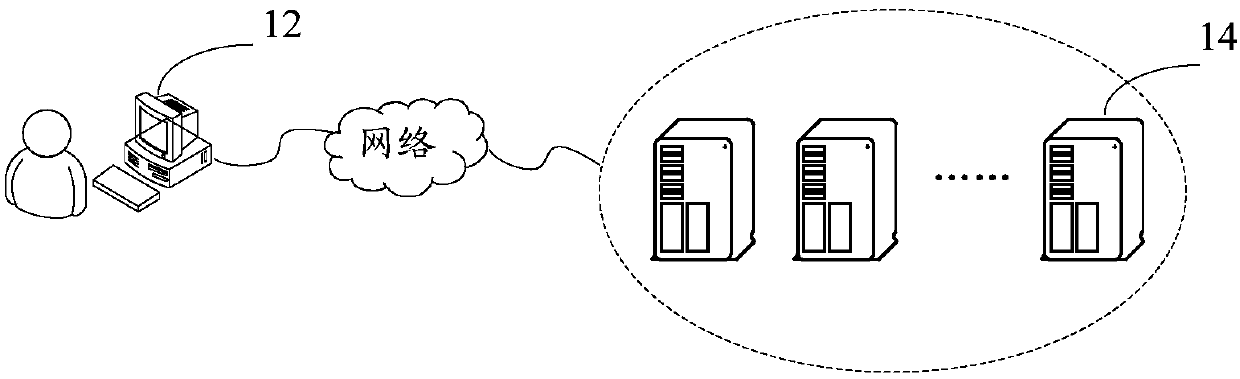
[0050] This application provides figure 1 The data interaction system shown. figure 1 It is a schematic structural diagram of a data interaction system according to Embodiment 2 of the present application. Including: terminal 12 and server 14, wherein,
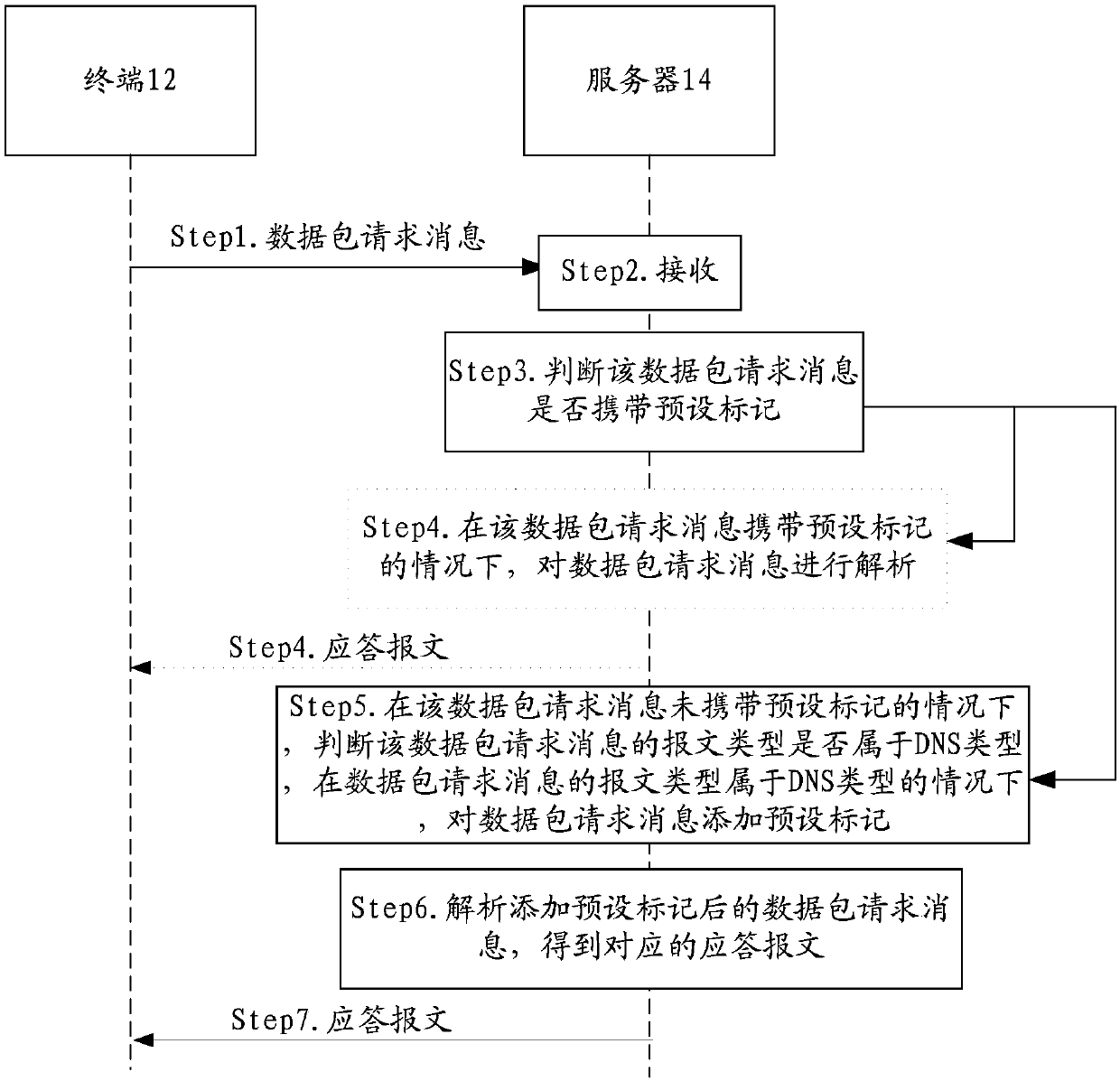
[0051] The terminal 12 is used to send a data packet request message to the server 14; the server 14 is used to judge whether the received data packet request message carries a preset mark, and if the data packet request message does not carry a preset mark, judge whether the data packet Whether the message type of the request message is the same as the preset message type, if the message type is the same as the preset message type, mark the preset mark on the data packet request message, and return the corresponding message to the terminal 12.
[0052] Here, the preset flag carried in the data packet request message in the data interaction system provided by this application can make the data packet request message not pass...
Embodiment 3
[0079]According to the embodiment of the present application, an embodiment of a data interaction method is also provided. It should be noted that the steps shown in the flow chart of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and, Although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
[0080] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device. Take running on a computer terminal as an example, Figure 4 It is a block diagram of the hardware structure of the server of a method for data interaction in the embodiment of this application. Such as Figure 4 As shown, the server 40 may include one or more (only one is shown in the figure) processors 402 (the processors 402 may include...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com