Patents
Literature
77results about How to "Solve technical problems with low security" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
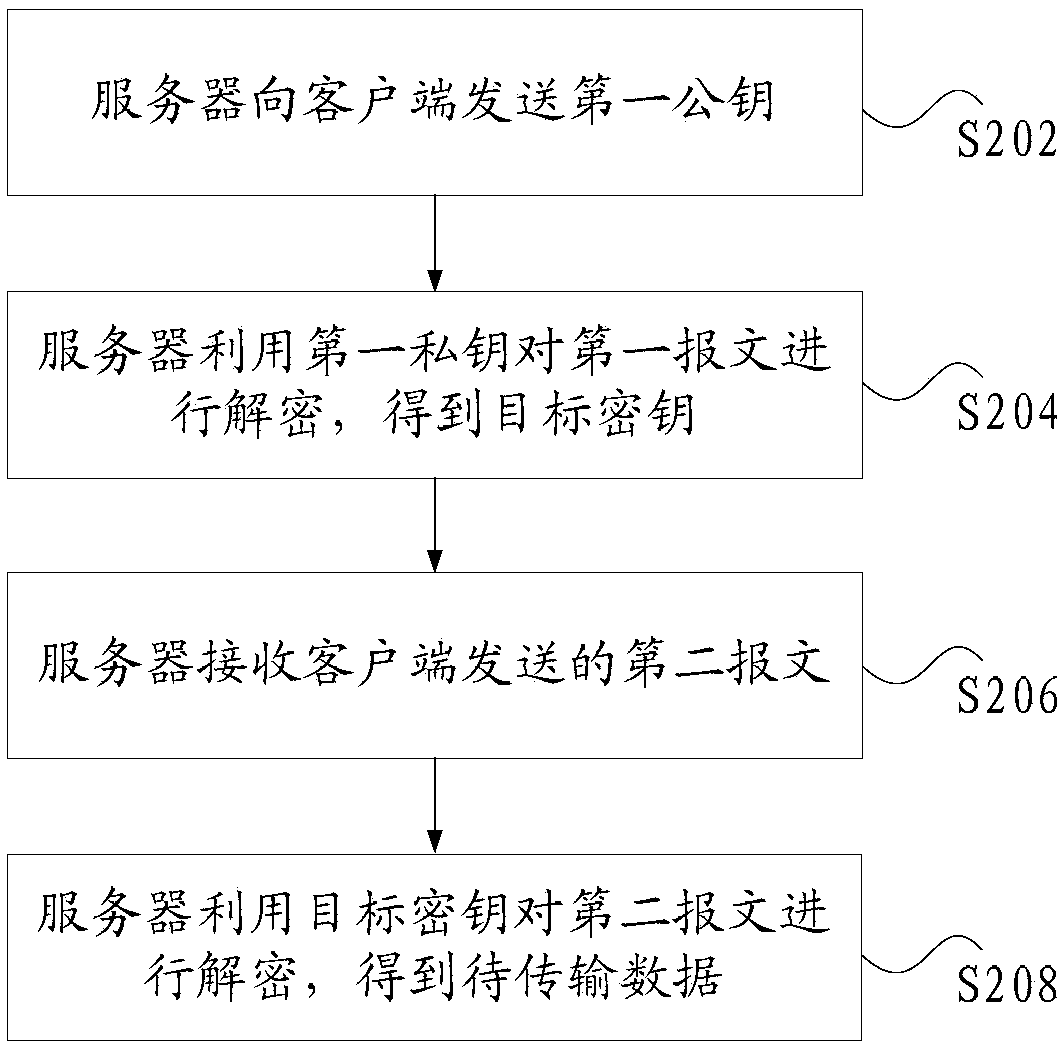
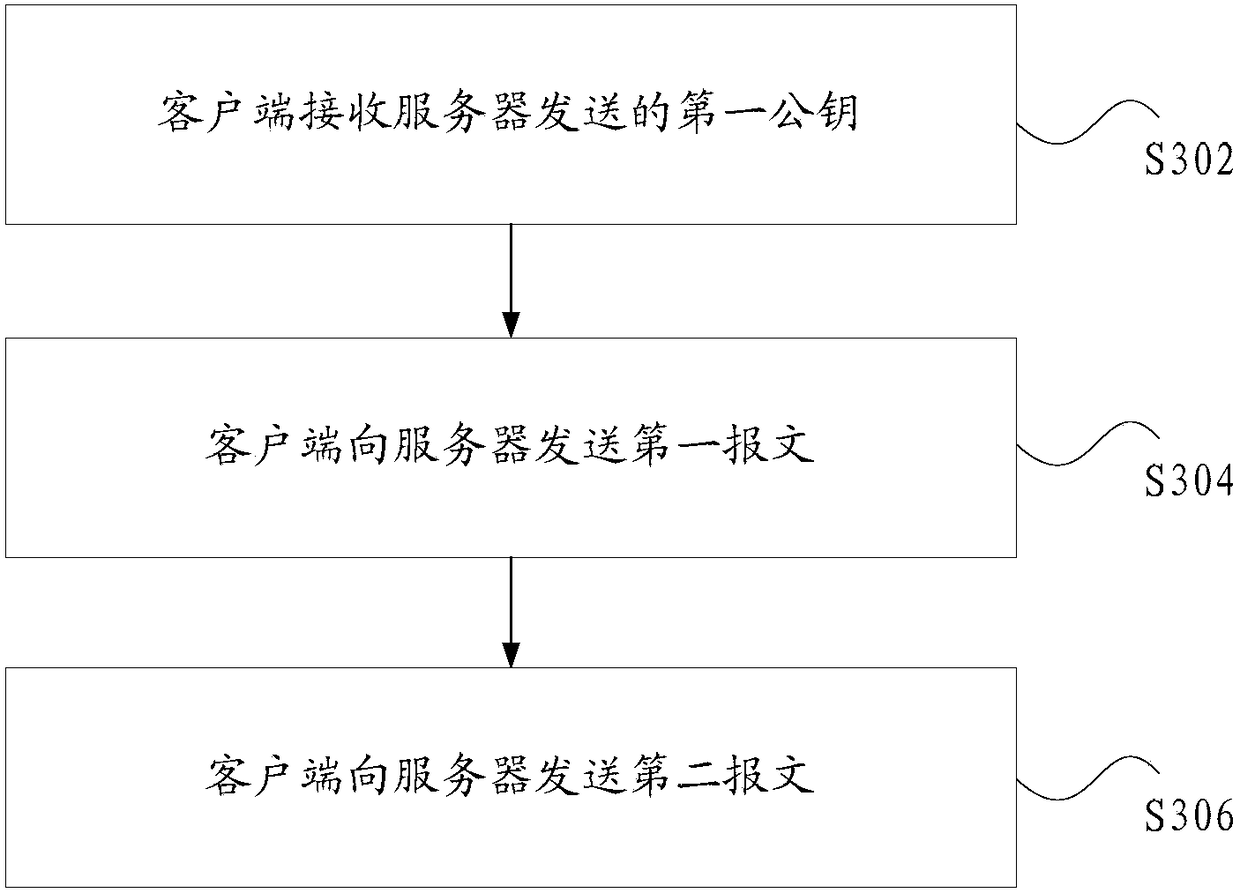
Data transmission method and device
InactiveCN108347419AEnsure safetyImprove securityKey distribution for secure communicationCiphertextClient-side
The invention discloses a data transmission method and device. The data transmission method comprises the following steps: a server sends a first public key to a client; the server uses a first private key to decrypt a first message to obtain a target key, wherein the first public key and the first private key are a pair of keys, the first message is obtained through encrypting the target key withthe first public key by the client, and the target key is generated according to a random string sent by the server; the server receives a second message sent by the client, wherein the second message comprises the encrypted data obtained through encrypting first data with the target key by the client and second data, and the data to be transmitted includes the first data and the second data, wherein the first data is data that needs to be encrypted during the data transmission process, and the second data is data that does not need to be encrypted during the data transmission process; and the server uses the target key to decrypt the second message to obtain the data to be transmitted. The data transmission method and device solves the technical problem of low data transmission securityin the prior art.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Lithium battery electrode plate and manufacturing method therefor
ActiveCN106486639AThe coating process is simple and easyEase of mass productionSecondary cellsElectrode collector coatingLithium iron phosphateEngineering
The invention discloses a lithium battery electrode plate and a manufacturing method therefor. The lithium battery electrode plate comprises a positive electrode inner layer electrode plate and a positive electrode outer layer electrode plate, wherein the positive electrode inner layer electrode plate comprises a positive electrode inner layer active material; the positive electrode outer layer electrode plate comprises a positive electrode outer layer active material; the stability of the positive electrode inner layer active material is higher than that of the positive electrode outer layer active material, wherein the positive electrode inner layer active material comprises one or more of lithium iron phosphate, lithium cobalt oxide, a nickel-cobalt-manganese ternary material, a nickel-cobalt-aluminum high-nickel material and lithium titanate; and positive electrode outer layer active material comprises one or more of lithium iron phosphate, lithium cobalt oxide, the nickel-cobalt-manganese ternary material, the nickel-cobalt-aluminum high-nickel material and lithium titanate. The lithium battery electrode plate provided by the invention adopts a dual-layer electrode structure, so that relatively high safety performance can be obtained.
Owner:SHENZHEN BAK POWER BATTERY CO LTD +1
Identity verification method and apparatus
InactiveCN108206996AImprove securityLow securityParticular environment based servicesConnection managementEmbedded systemSoftware engineering
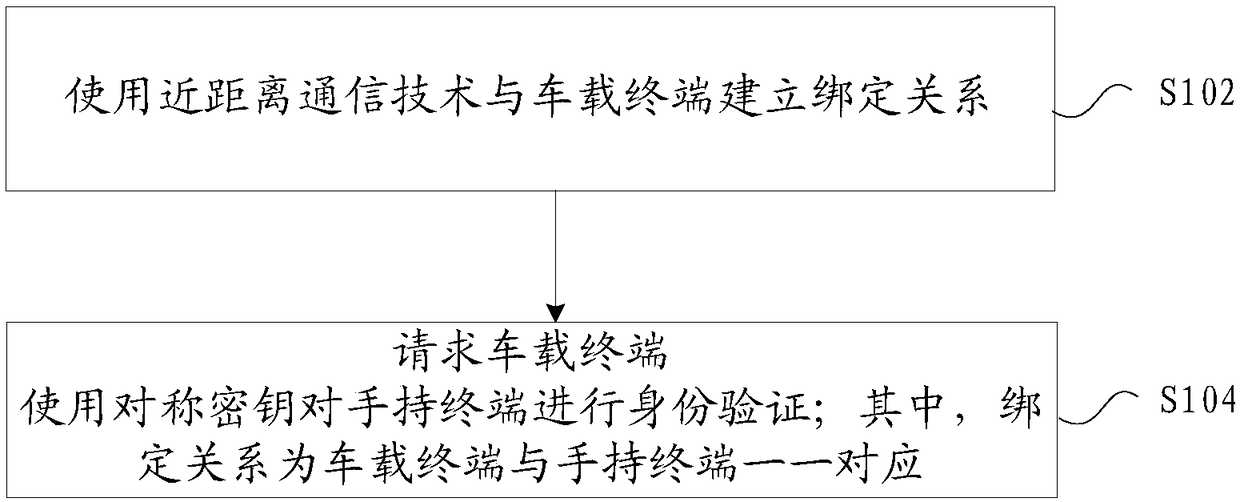
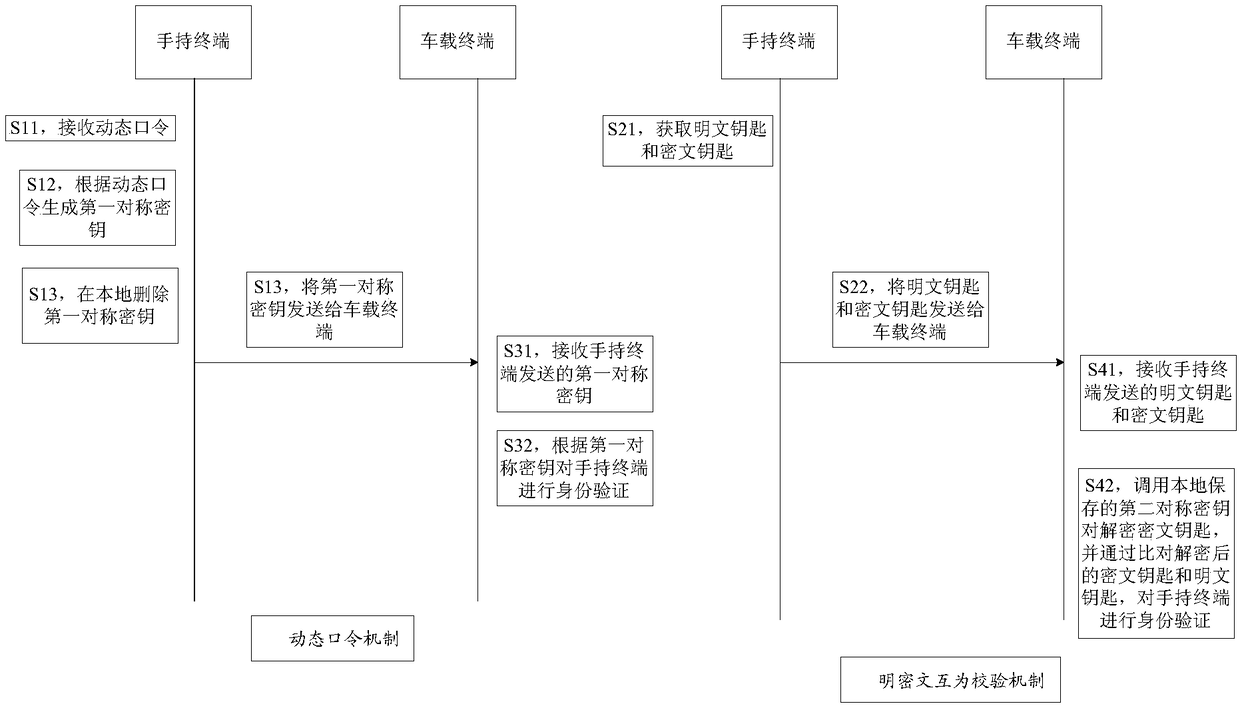
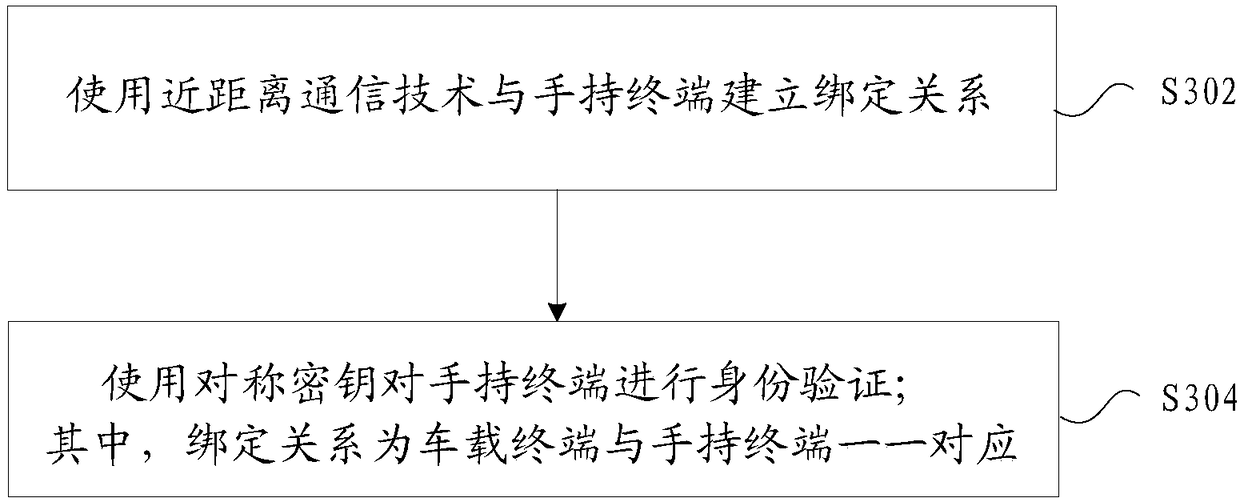
The invention provides an identity verification method and apparatus. The method includes the steps of establishing a binding relationship with a vehicle terminal by using a short-range communicationtechnology; and requesting the vehicle terminal to perform identity verification on a handheld terminal by using a symmetric key; wherein the binding relationship is that the vehicle terminal has a one-to-one correspondence with the handheld terminal. Through the identity verification method and apparatus, the technical problem of low security when the vehicle terminal verifies the handheld terminal in the related art is solved.
Owner:ZTE CORP
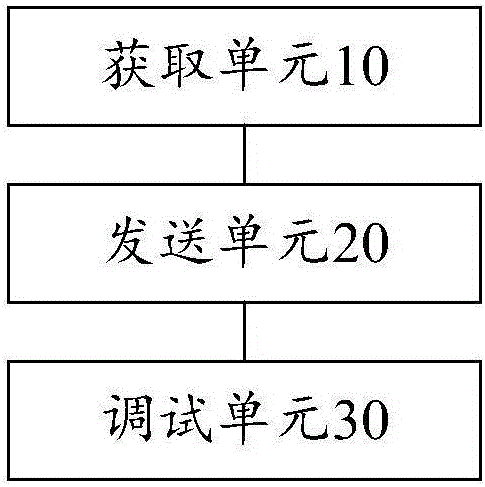
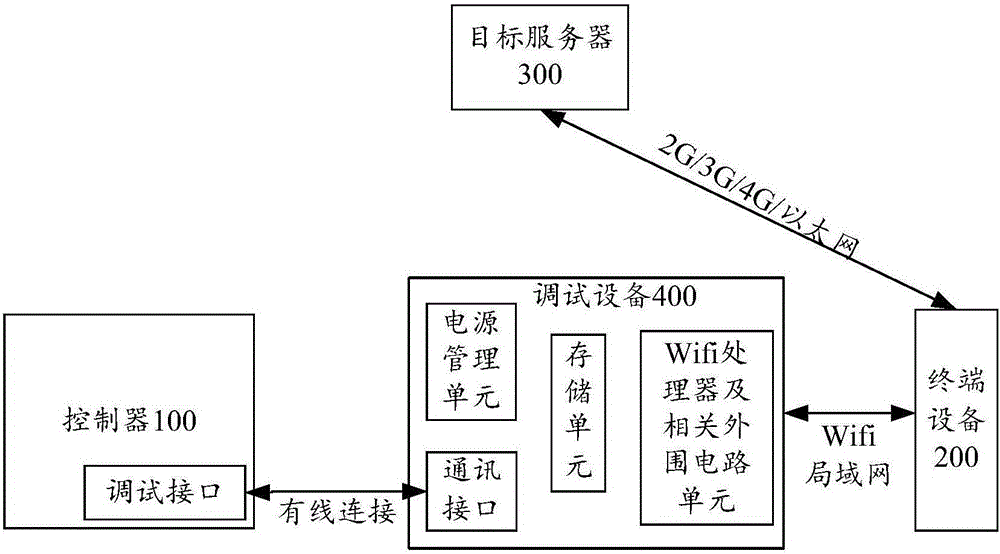
Debugging method and device of air conditioner
InactiveCN105135615ASolve technical problems with low securitySpace heating and ventilation safety systemsLighting and heating apparatusTerminal equipmentComputer engineering
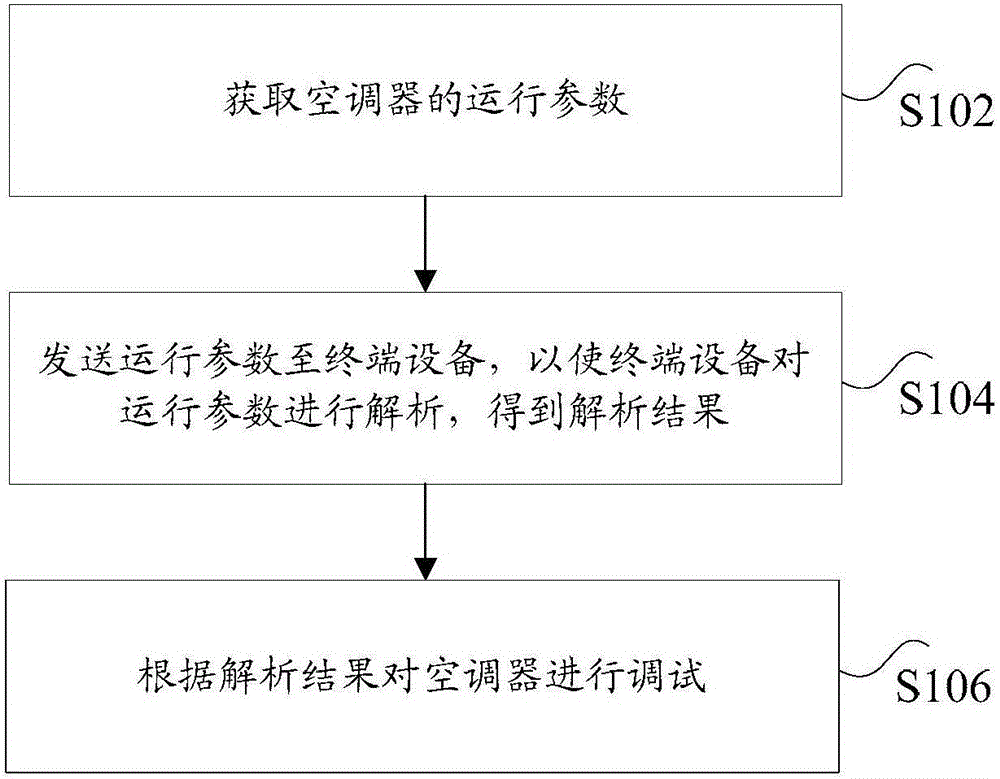
The invention discloses a debugging method and a debugging device of an air conditioner. The method comprises the following steps: acquiring operation parameters of the air conditioner; sending the operation parameters to terminal equipment, analyzing the operation parameters of the terminal equipment to obtain analyzed results, wherein the terminal equipment is equipment which is in communication connection with debugging equipment; and debugging the air conditioner according to the analyzed results. The debugging method solves the technical problem that an air conditioner debugging process in the prior art is low in safety.
Owner:GREE ELECTRIC APPLIANCES INC
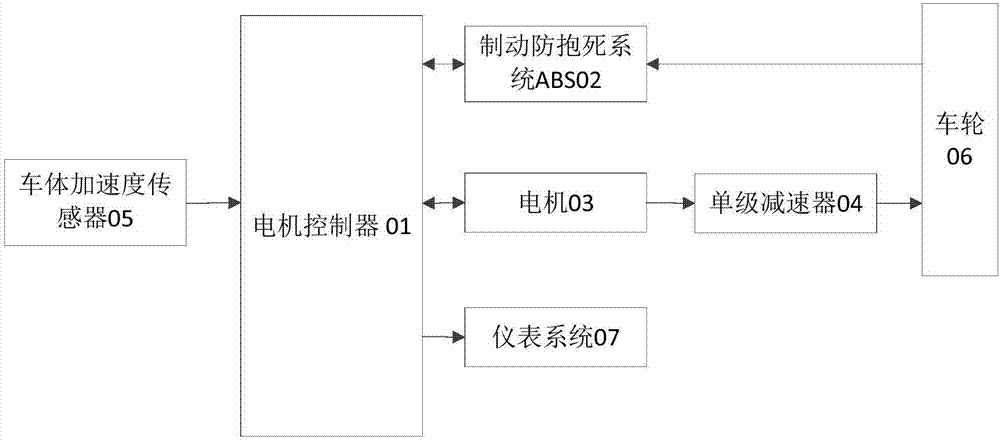
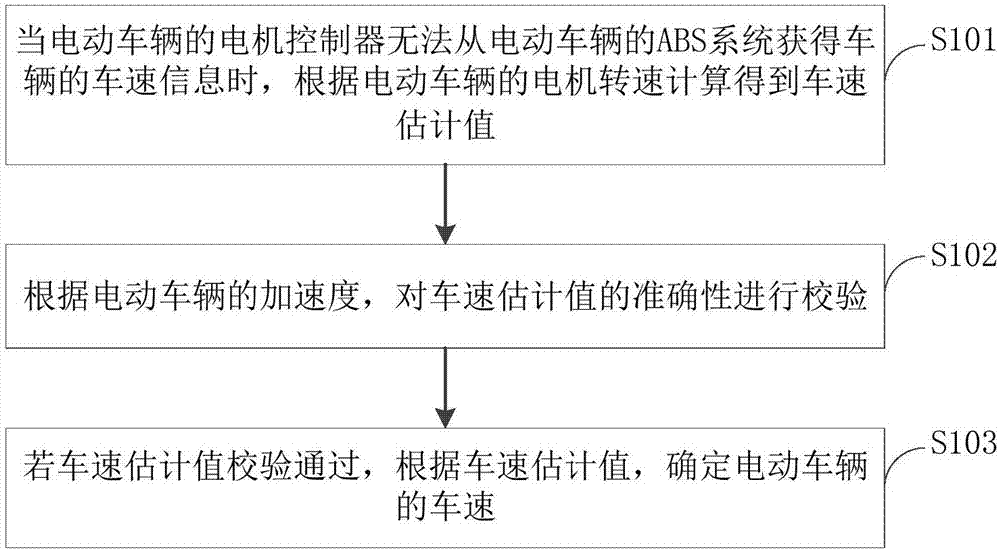
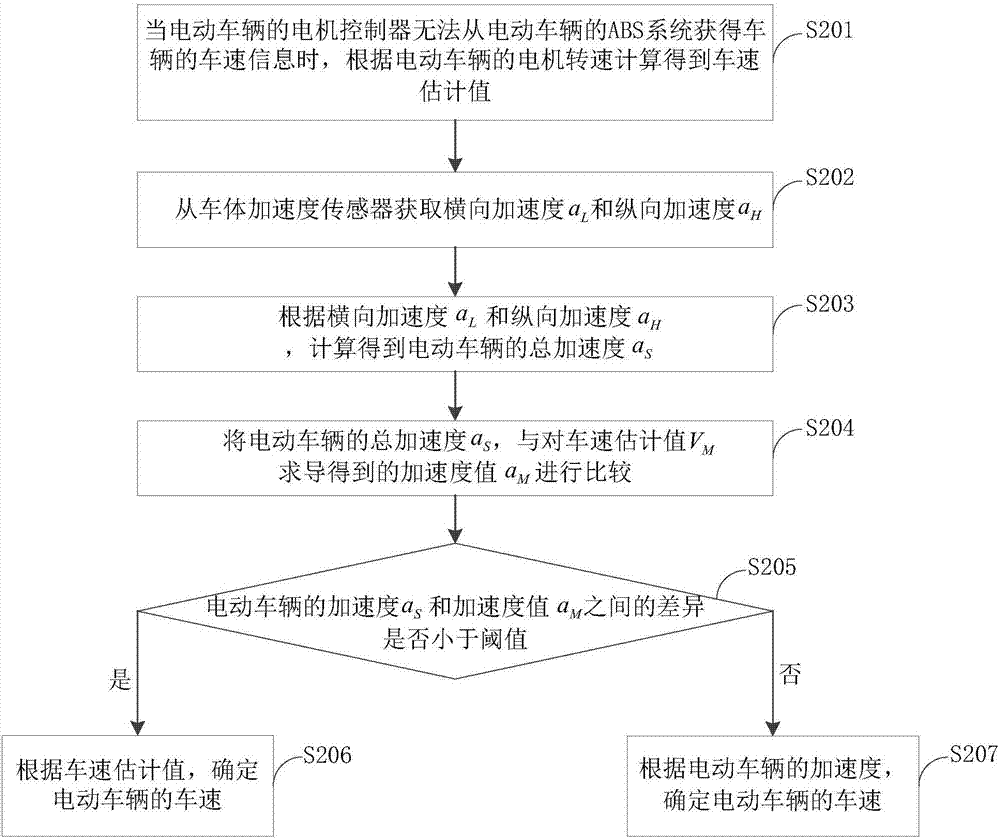
Vehicle speed measuring method and device based on electric vehicle
InactiveCN107264287ASolve technical problems with low securityElectric devicesElectric machineMotor controller
The invention provides a vehicle speed measuring method and device based on an electric vehicle. The vehicle speed measuring method based on the electric vehicle comprises the steps that when a motor controller of the electric vehicle cannot obtain vehicle speed information from an antilock brake system (ABS) of the electric vehicle, according to the motor rotary speed of the electric vehicle, the vehicle speed estimated value is calculated and obtained, according to the accelerated speed of the electric vehicle, the accuracy of the vehicle speed estimated value is verified, and if verification of the vehicle speed estimated value is passed, according to the vehicle speed estimated value, the vehicle speed of the electric vehicle is determined. Compared with the prior art, when the ABS breaks down, the vehicle speed information cannot be obtained, and the vehicle speed calculated and obtained through the motor rotary speed can cause the calculated and obtained vehicle speed to be inaccurate due to skidding or locking of the vehicle so that the situation that whether safety exists or not is judged by a driver according to the accurate vehicle speed information cannot achieved, and the potential safety hazard of driving operation exists; and according to the vehicle speed measuring method, the technical problem that in the prior art, safety is low is solved.
Owner:BEIJING ELECTRIC VEHICLE
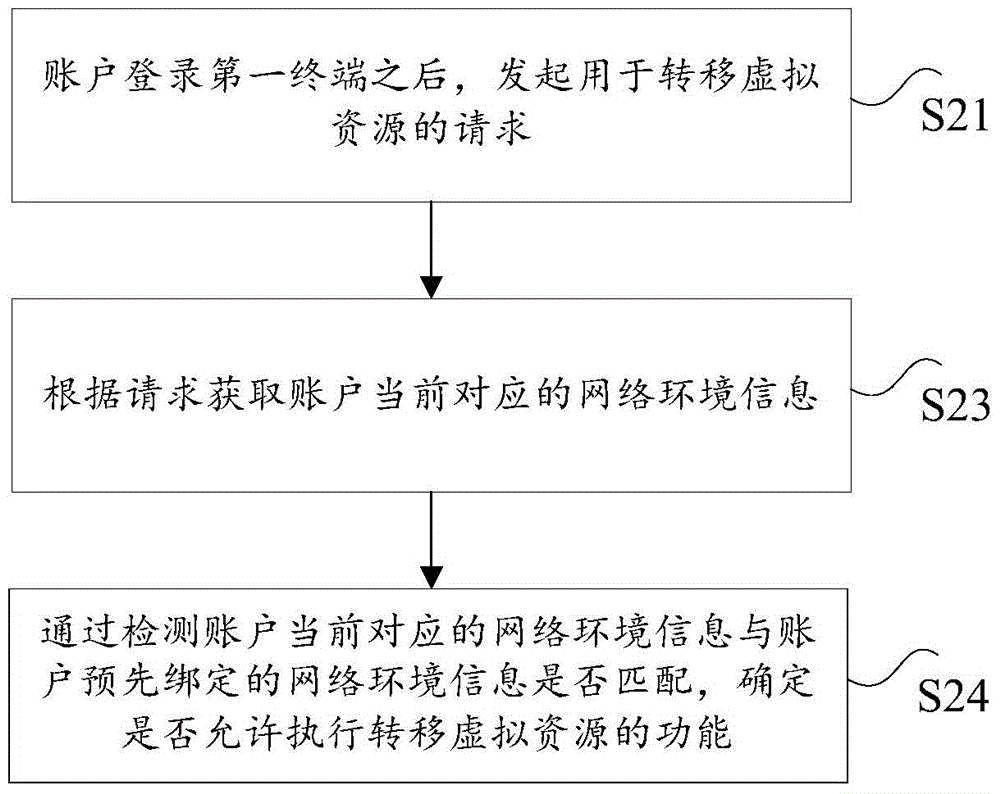
Safe transferring method, device and system of virtual resources
ActiveCN106204003AImprove securitySolve technical problems with low securityTransmissionProtocol authorisationComputer terminalMobile payment
The invention discloses a safe transferring method, device and system of virtual resources. The method comprises the following steps: after an account logs in a first terminal, initiating a request used for transferring the virtual resources; according to the request, obtaining network environment information corresponding to the account at present, wherein the network environment information corresponding to the account at present comprises the equipment information of the first terminal and / or the equipment information of first network equipment where the first terminal is accessed into, and the first network equipment is any one piece of network equipment in a network equipment group; and detecting whether the network environment information corresponding to the account at present is matched with network environment information bound with an account in advance or not to determine whether a function of transferring the virtual resources permits to be executed or not. By use of the method, the technical problem of low safety of an existing mobile payment way is solved.
Owner:ADVANCED NEW TECH CO LTD
Device, method and system for burning firmware by factory
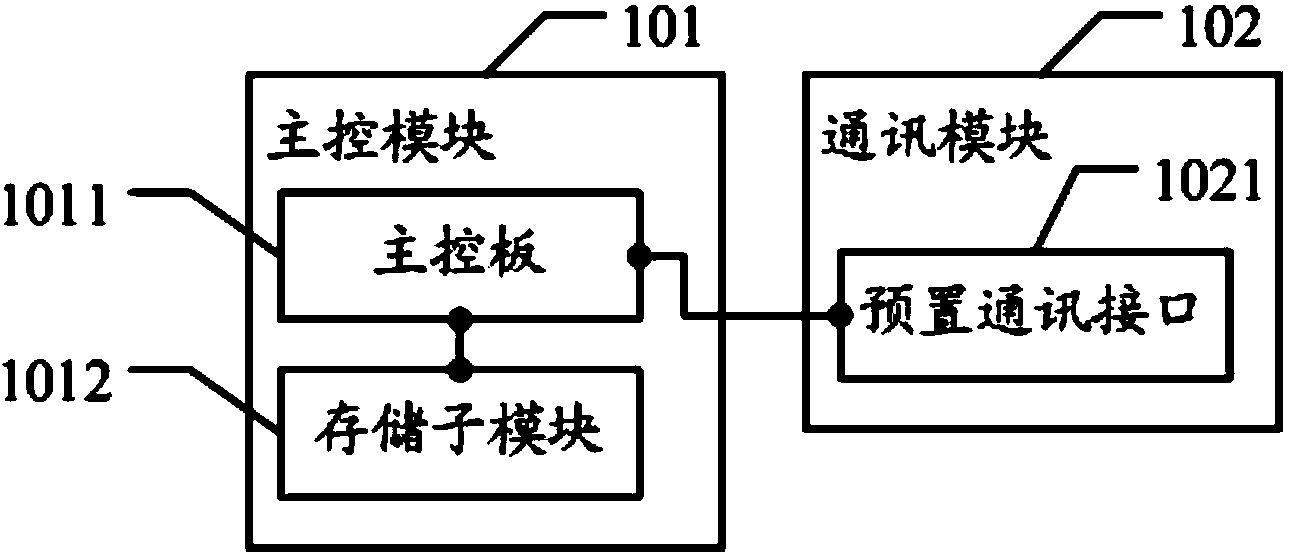
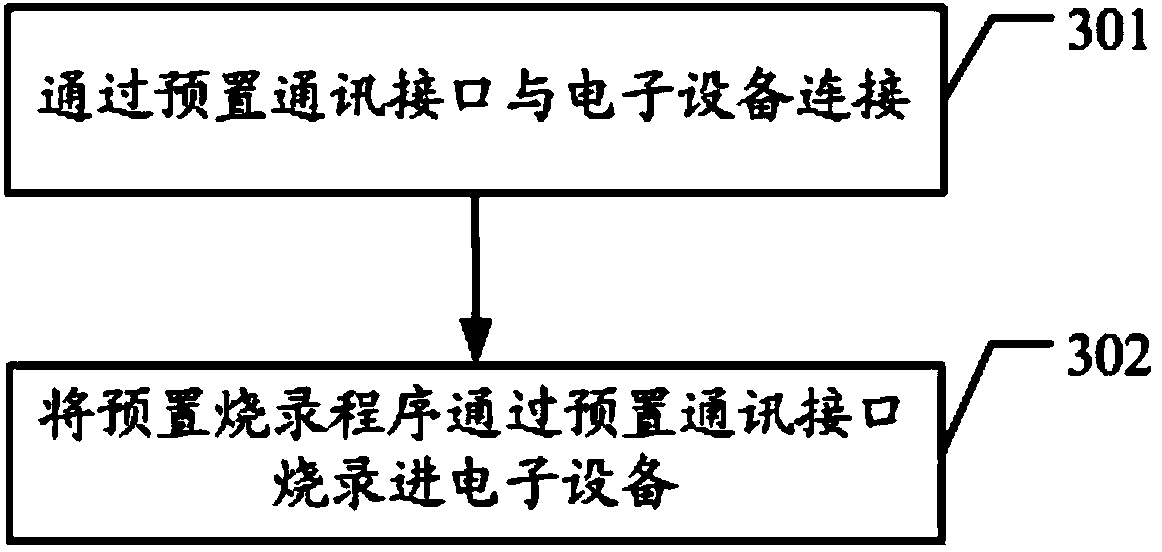
ActiveCN103838612AEasy to operateLow input costProgram loading/initiatingCommunication interfaceTransmission belt
The embodiment of the invention discloses a device, method and system for burning firmware by a factory. The technology for burning the firmware by the factory can be achieved, the operation is easy, the invested economic cost is reduced, and meanwhile due to the fact that the burning program is preset in a master control module, the technical problem that the safety is low is solved, the system transmission belt design is achieved, and the technology of intelligently burning the firmware by the factory in mass is further achieved. The device comprises the master control module and a communication module, the master control module comprises a master control board and a storage submodule, the communication module is connected with the master control module, and is used for being connected with electronic equipment through a preset communication interface, the electronic equipment is connected with the master control module through the communication module with the preset communication interface, and the master control module burn the burning program preset in the storage submodule in the electronic equipment.
Owner:GUANGZHOU SHIRUI ELECTRONICS
Data query method and data query device
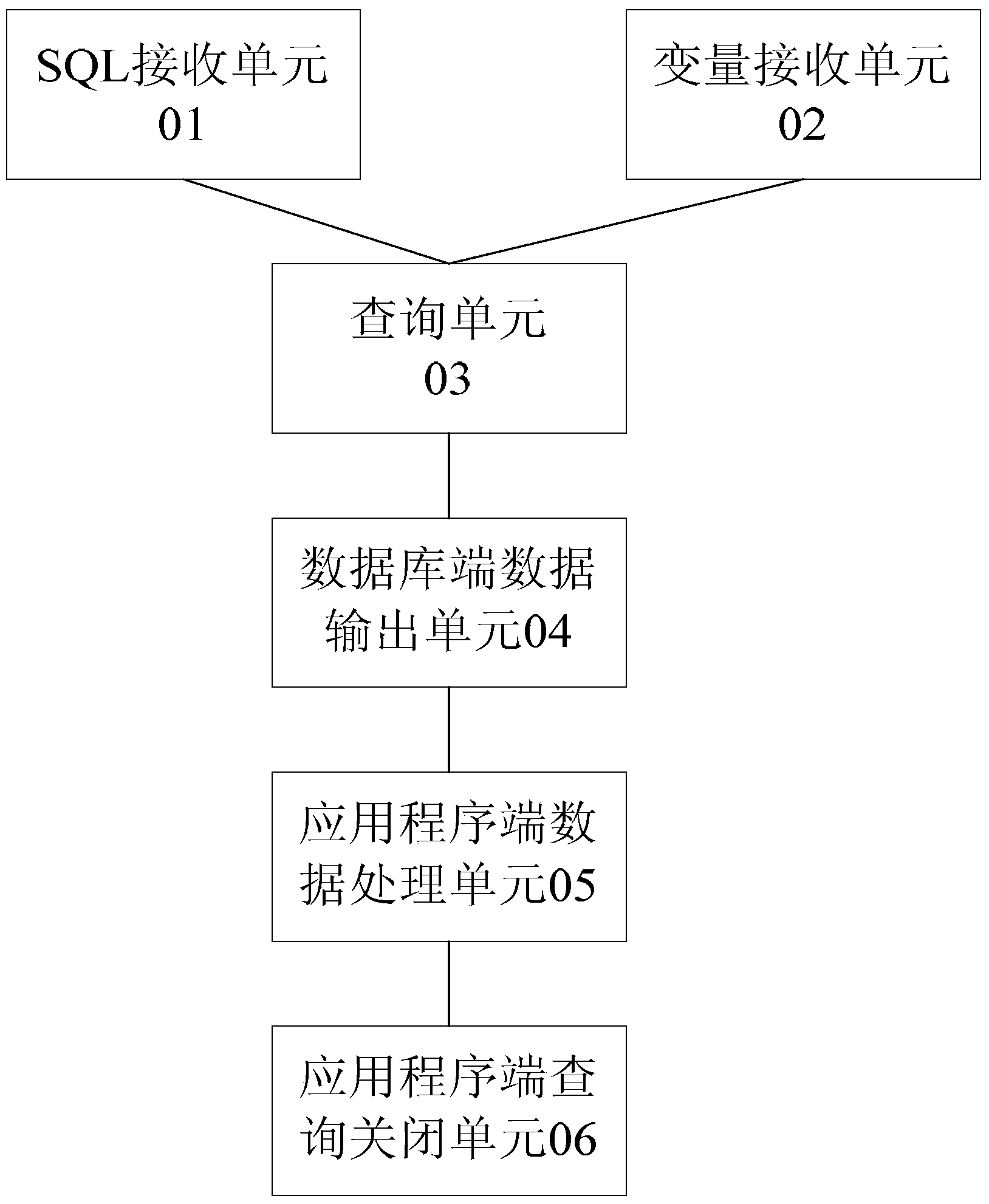
ActiveCN104239508ASolve technical problems with low securityImprove securitySpecial data processing applicationsArray data structureData query
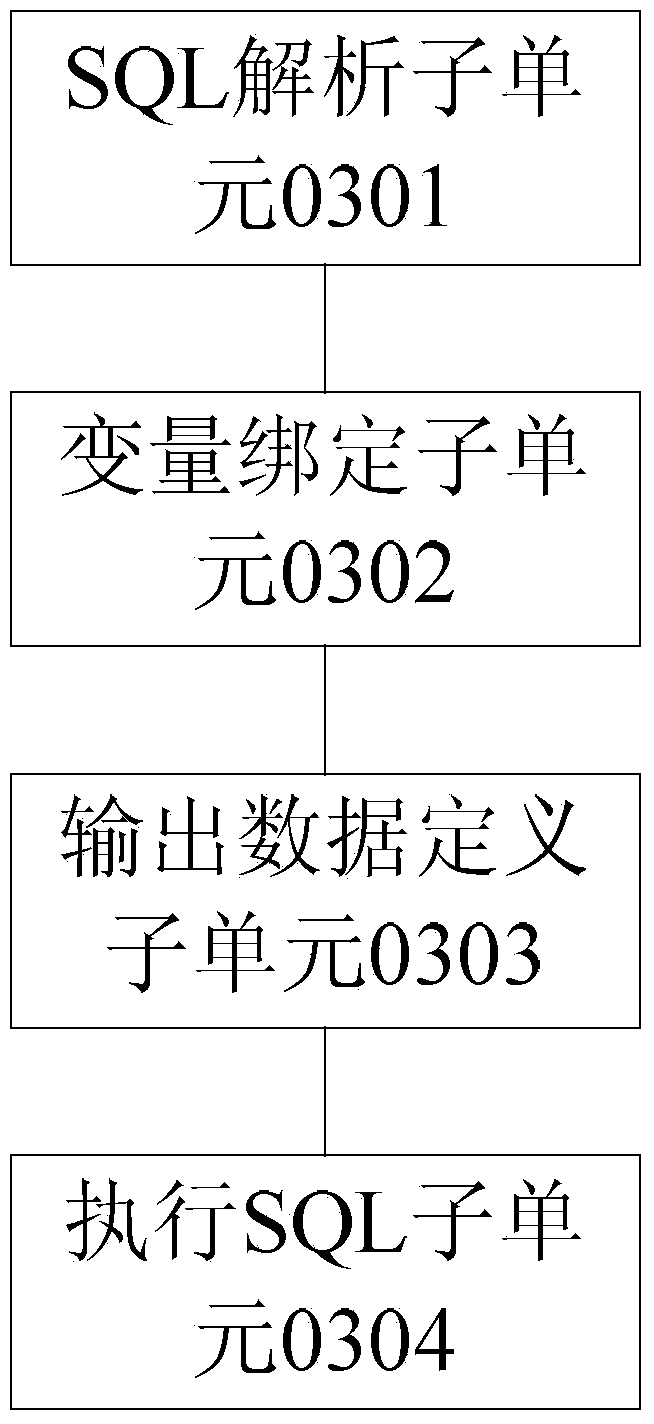
The invention provides a data query method and a data query device, wherein the method comprises the following steps that when variable names carried in structured query language (SQL) statements are received, query condition values which are inputted by a user according to the variable names are obtained; the variable names and the query condition values are bound; the data types of query results outputted by the execution of the SQL statements are prejudged; according to the prejudged data types, data storage variable arrays are assigned to the query results outputted by the execution of the SQL statements; the SQL statements are executed, the query results are stored into the assigned data storage variable arrays, and the query results stored in the data storage variable arrays are provided for an application. The invention solves the technical problem that under the condition of uncertain query conditions, the SQL method of binding variables cannot be adopted to query data, which causes the low security of data query and the low data processing efficiency of a system, and therefore the technical effect of effectively increasing data query security and data processing efficiency is achieved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Cross-window data submitting method and system
ActiveCN105491116AImprove securitySolve technical problems with low securityUser identity/authority verificationData transmissionOperating system
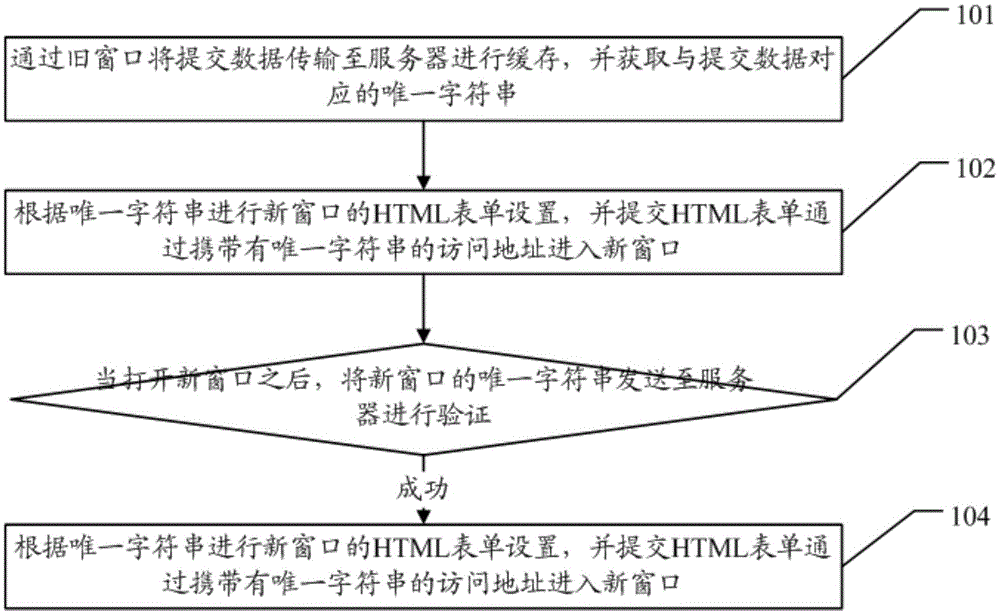
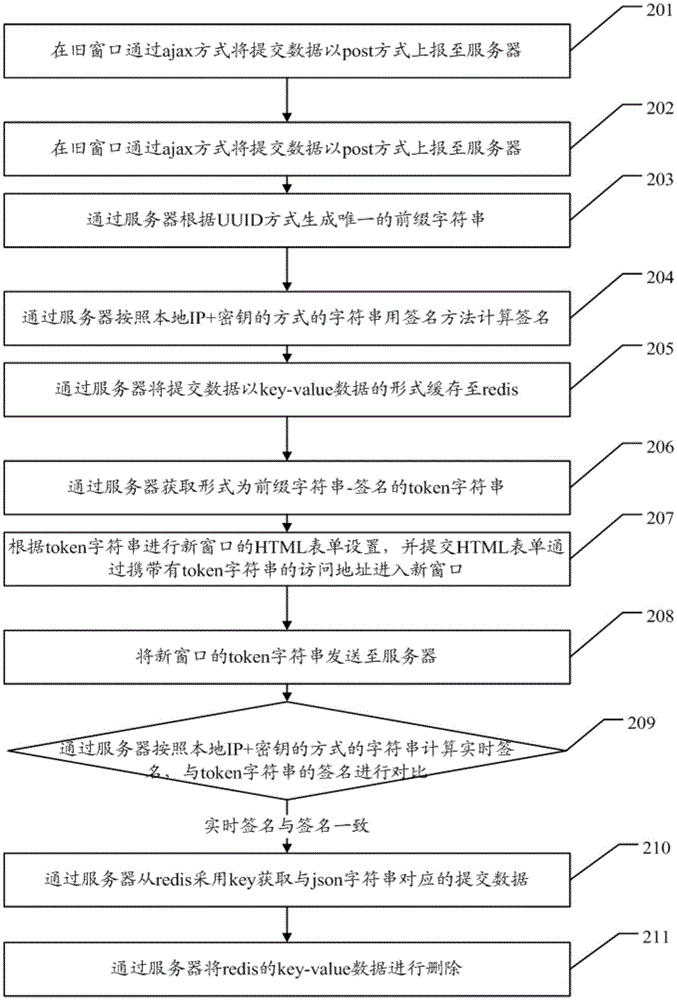
The embodiment of the invention discloses a cross-window data submitting method and system, solving the current technical problems that data transmission is realized by directly getting a request from a new window and bringing all parameters, therefore insecurity is caused, cross-website attack is liable to be caused, and the security of the user data is low. The cross-window data submitting method of the embodiment of the invention comprises: transmitting submitted data to a server for cachingthrough an old window, obtaining a unique character string corresponding to the submitted data; setting the HTML form of the new window according to the unique character string, submitting the HTML form, entering the new window through an access address carryingthe unique character string; when the new window is opened, sending the unique character string of the new window to the server for verification, if the verification is successful, obtaining the submitted data corresponding to the unique character string through the server.
Owner:GUANGZHOU HUADUO NETWORK TECH
Domain name request processing method and device
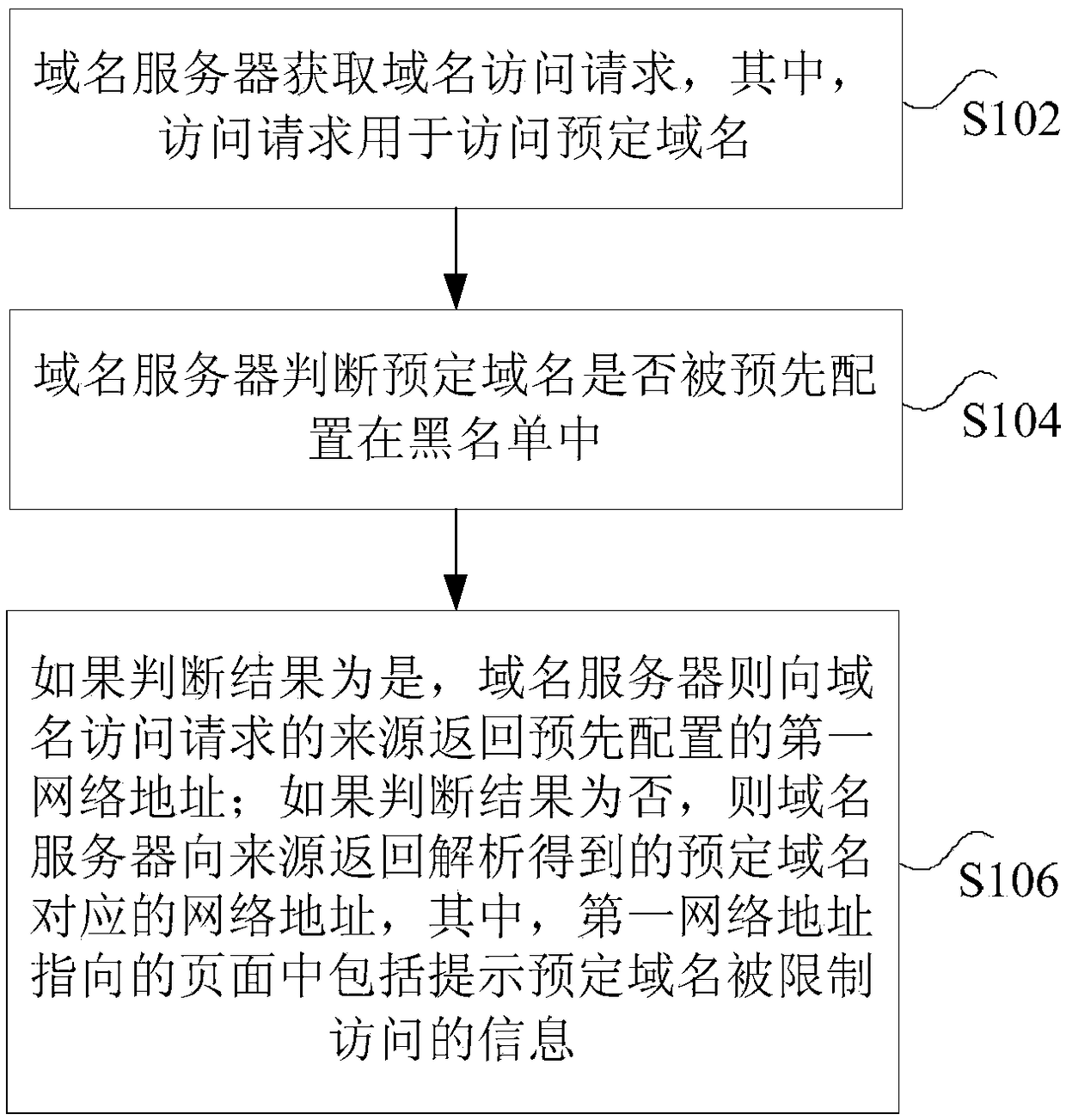
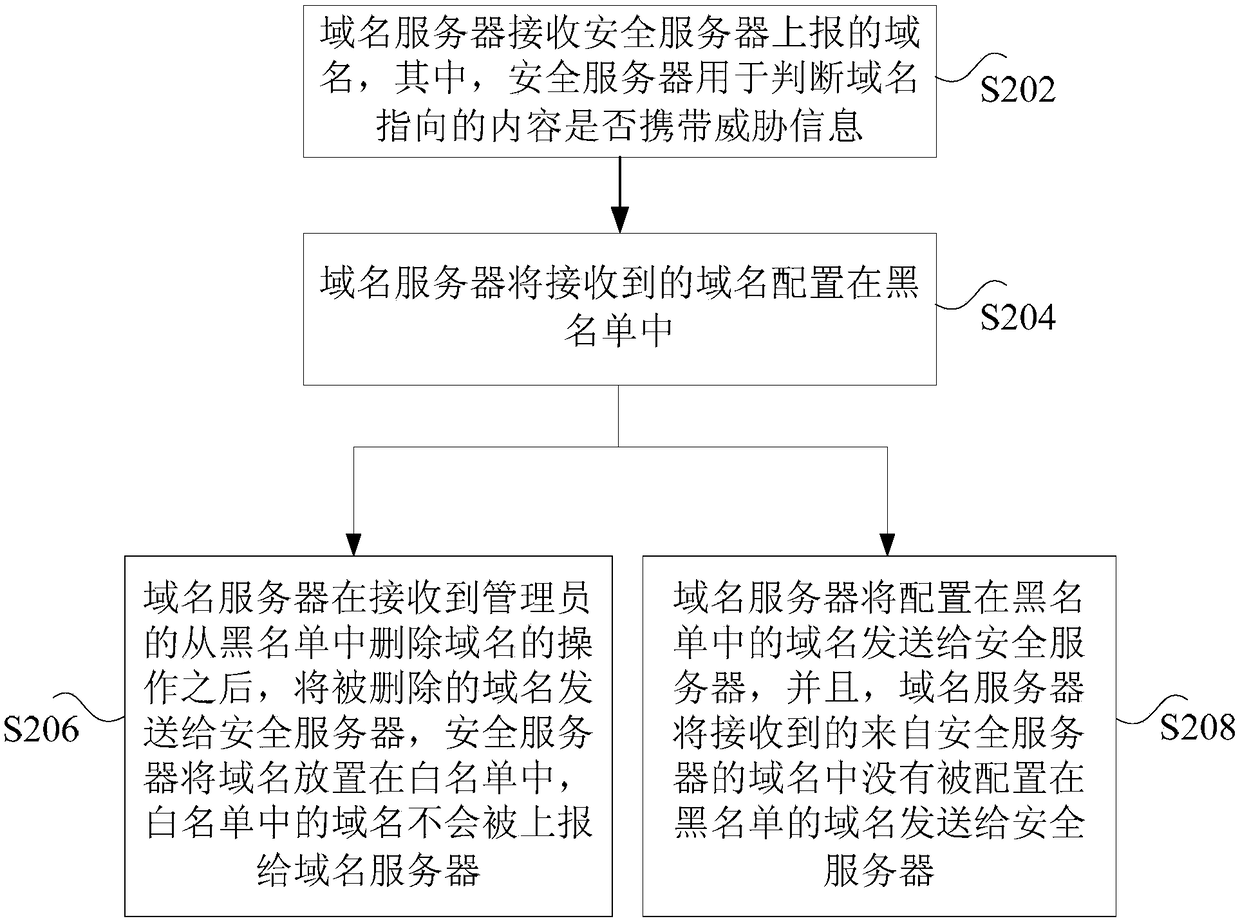
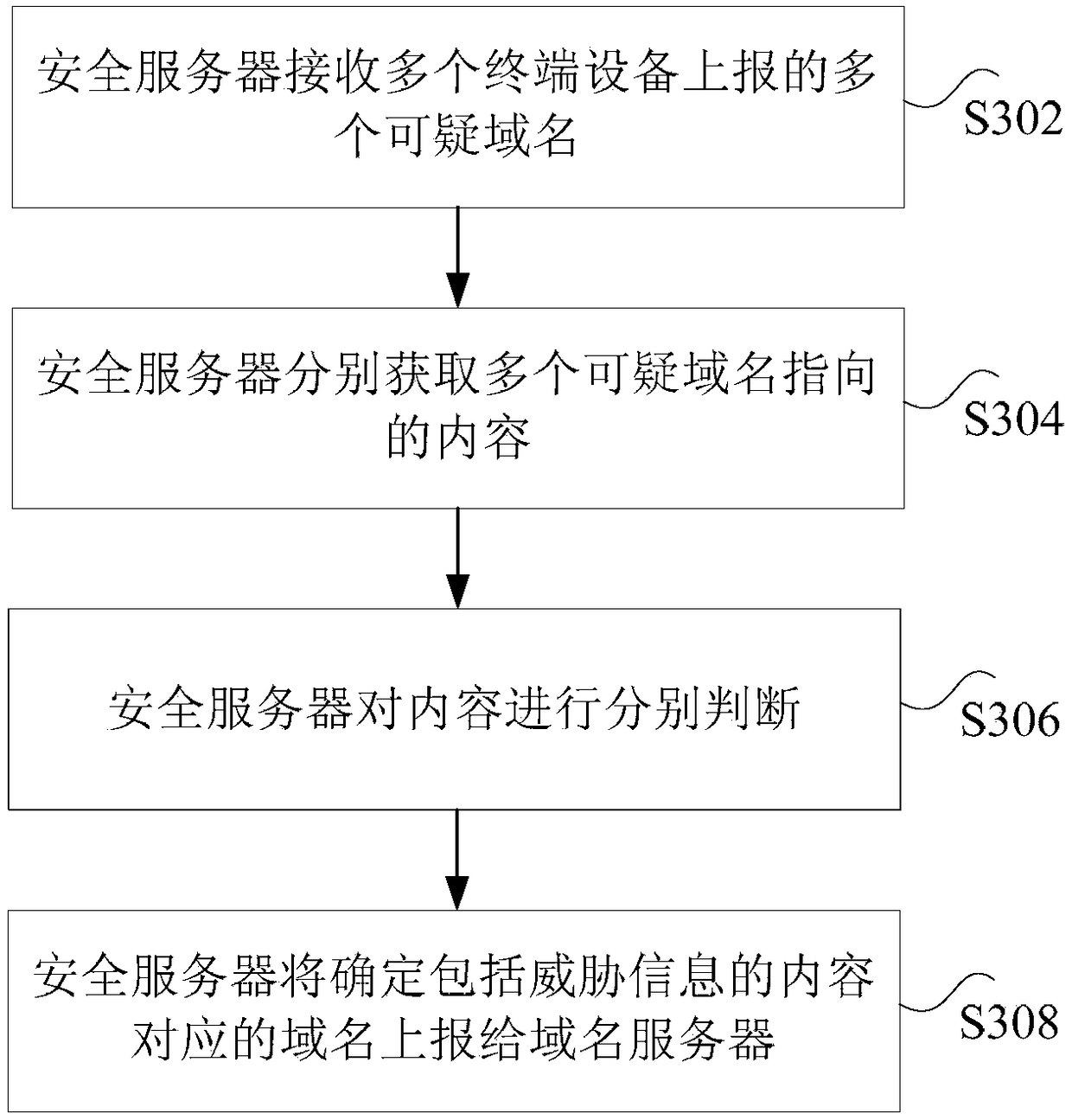
ActiveCN108156270ATo achieve the purpose of restricting accessImprove securityTransmissionDomain nameName server
The invention discloses a domain name request processing method and device. The method includes the following steps: a domain name server obtains a domain name access request, wherein the domain nameaccess request is used to access a predetermined domain name; the domain name server determines whether the predetermined domain name is pre-configured in a blacklist; if the judgment result is yes, the domain name server returns a pre-configured predetermined network address to the source of the domain name access request; and if the judgment result is no, the domain name server returns a networkaddress corresponding to the resolved predetermined domain name to the source, wherein a page specified in the predetermined network address includes information indicating that the access to the predetermined domain name is restricted. According to the scheme of the invention, the technical problem that an existing domain name server directly resolves all domain name requests and leads to low network security can be solved.
Owner:BEIJING KINGSOFT SECURITY MANAGEMENT SYST TECH CO LTD
Information processing method and electronic device
ActiveCN103902865AQuick responseInconvenient to operateDigital data authenticationComputer hardwareInformation processing
The invention discloses an information processing method and an electronic device. N standard encrypted messages are preset in the electronic device and correspond to a first program, and M sensors are arranged on the electronic device, wherein M and N are positive integers larger than 2. The method includes the steps that a request message for executing the first program is acquired; the M sensors are controlled to collect N messages to be compared based on the request message; matching between each message to be compared and one standard encrypted message corresponding to message to be compared is carried out to generate N confidence coefficient matching values; when the N confidence coefficient matching values meet a first preset condition, the request message is responded to and the first program is executed.
Owner:LENOVO (BEIJING) LTD
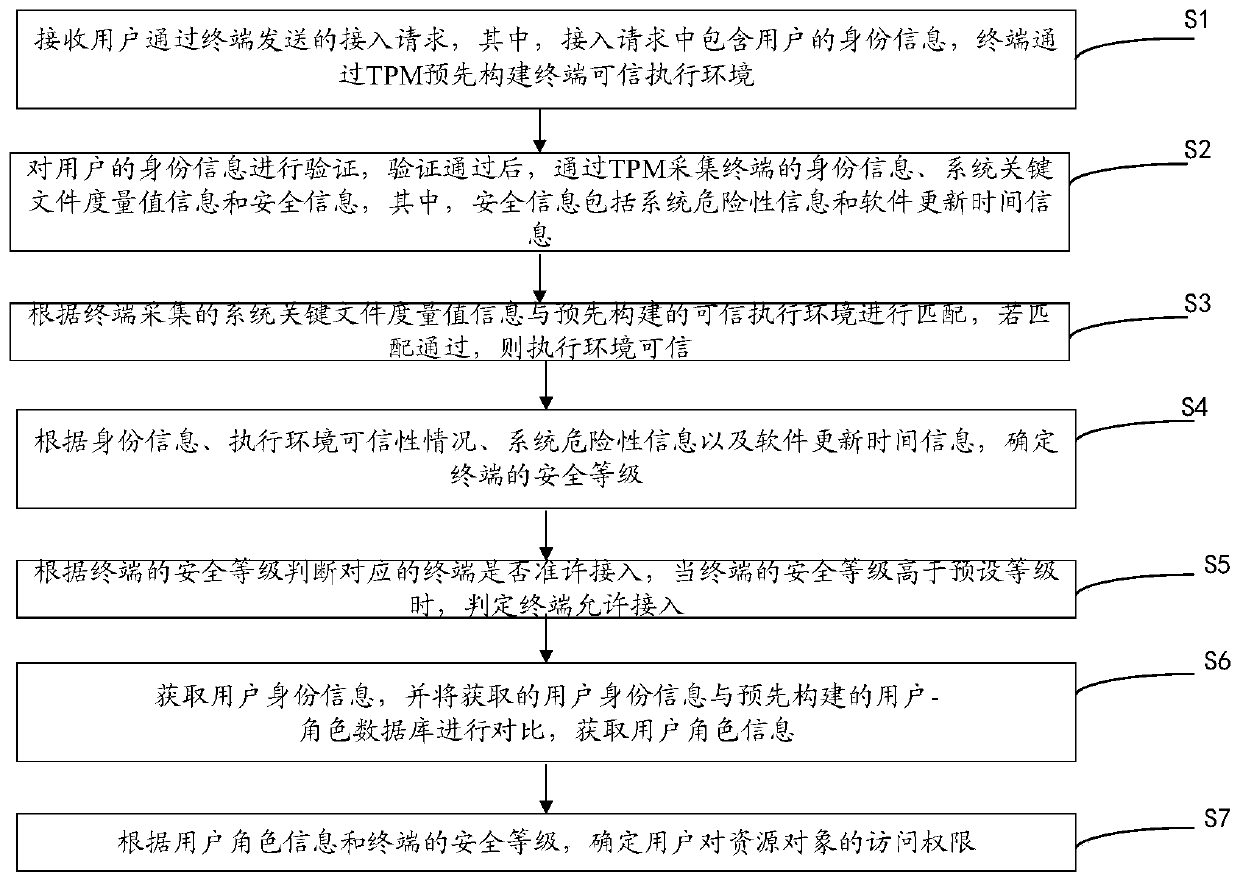
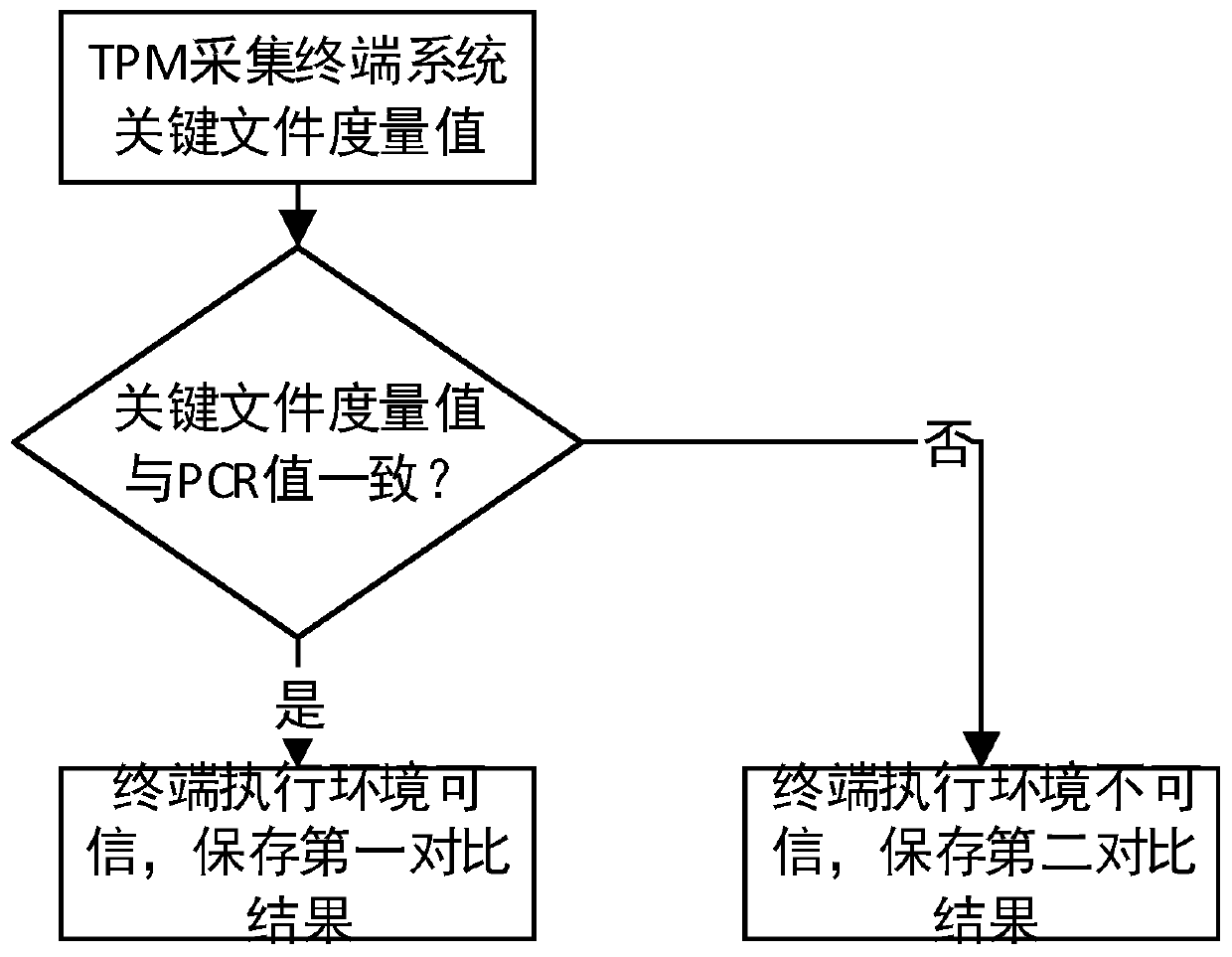
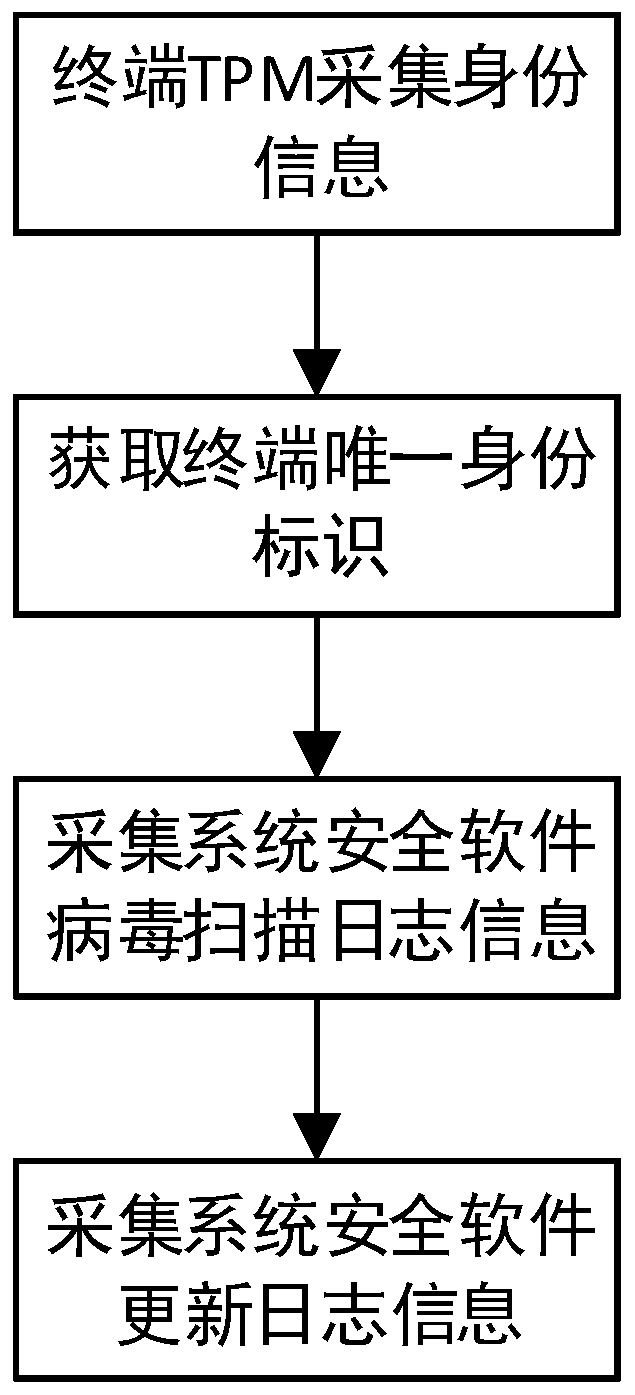
Access control method and device based on roles and terminal credibility
ActiveCN110061987ADetermine access rightsEnsure safetyUser identity/authority verificationNetwork Access ControlSecurity level
The invention discloses an access control method and device based on roles and terminal credibility. The access control method comprises the following steps: constructing a terminal trusted executionenvironment by using TPM, calculating an environment security state when a terminal is accessed, judging a terminal security level, and associating an internal network access control permission with auser role and the terminal security level, thereby realizing access control. According to the method, the security of the intranet access terminal and the security of intranet access control authority distribution can be effectively ensured, the user authority can be adjusted according to the user role and the current security level of the access terminal, and the method has the advantages of high security, convenient authorization management, capability of flexibly adjusting terminal measurement contents according to working requirements and easiness in implementation.
Owner:WUHAN UNIV
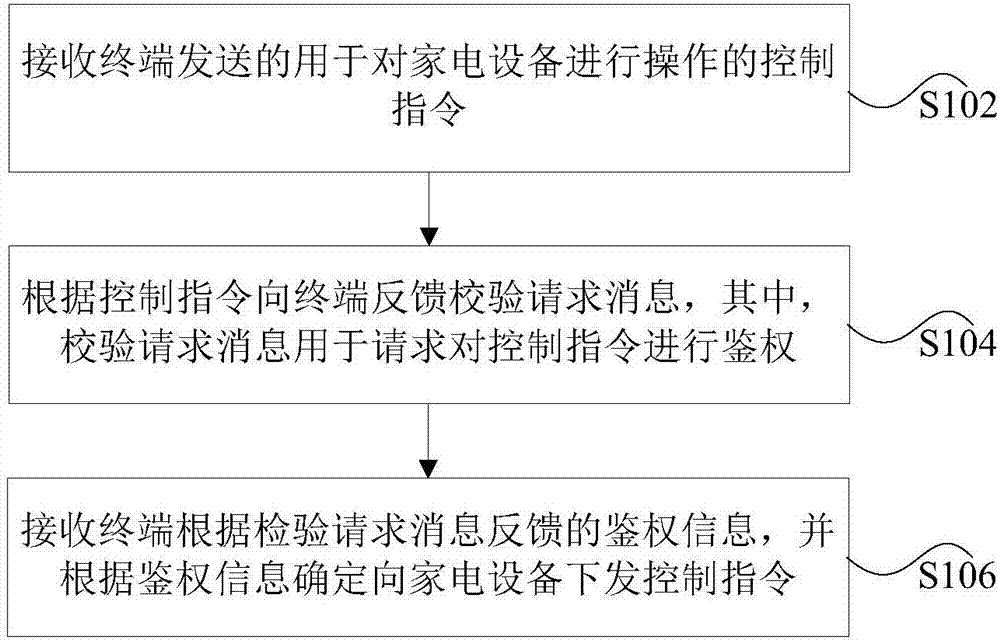
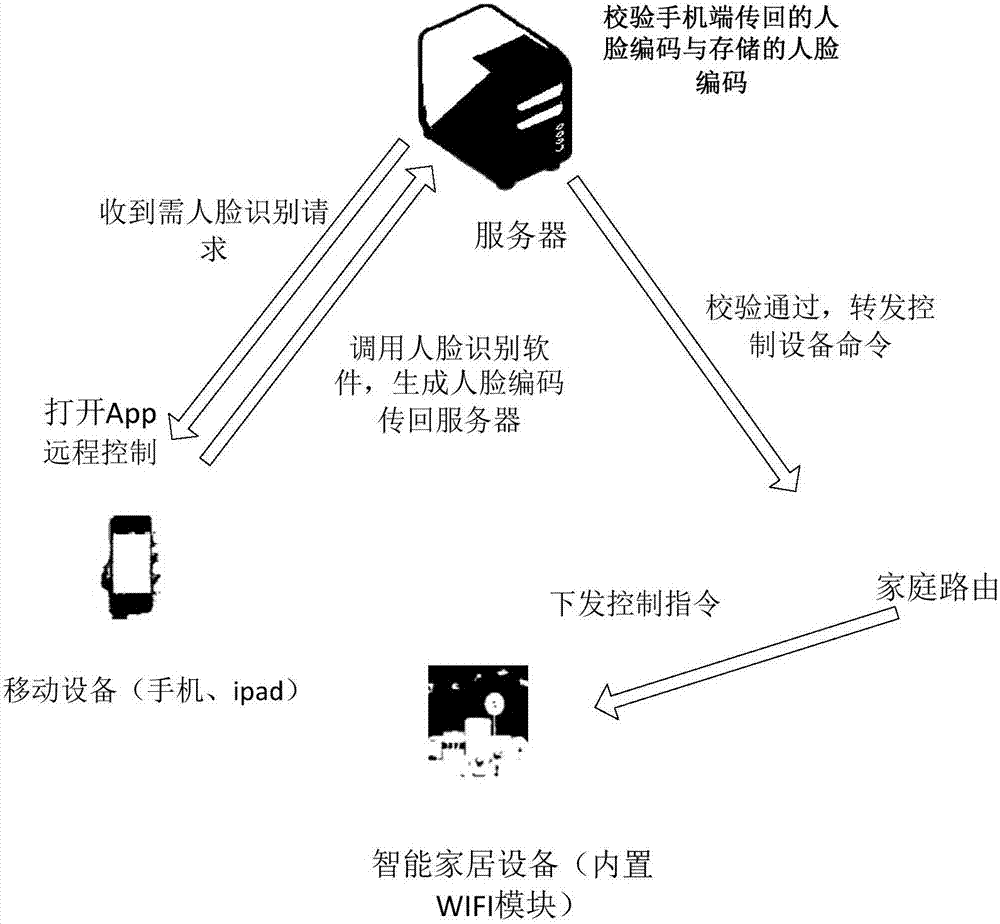
Method and apparatus for controlling appliance
ActiveCN107367946AImprove securityLow securityComputer controlProgramme total factory controlControl equipmentHome appliance
The invention discloses a method and apparatus for controlling an appliance. The method includes the steps of receiving a control instruction sent by a terminal and used for operating a household appliance; and feeding back a verification request message to the terminal according to the control instruction, the verification request message being used for requesting the authentication of the control instruction; and receiving authentication information fed back by the terminal according to the verification request message, and determining to deliver the control instruction to the home appliance according to the authentication information. The method and apparatus invention solve the technical problem of low safety in controlling the appliance in the related art.
Owner:GREE ELECTRIC APPLIANCES INC
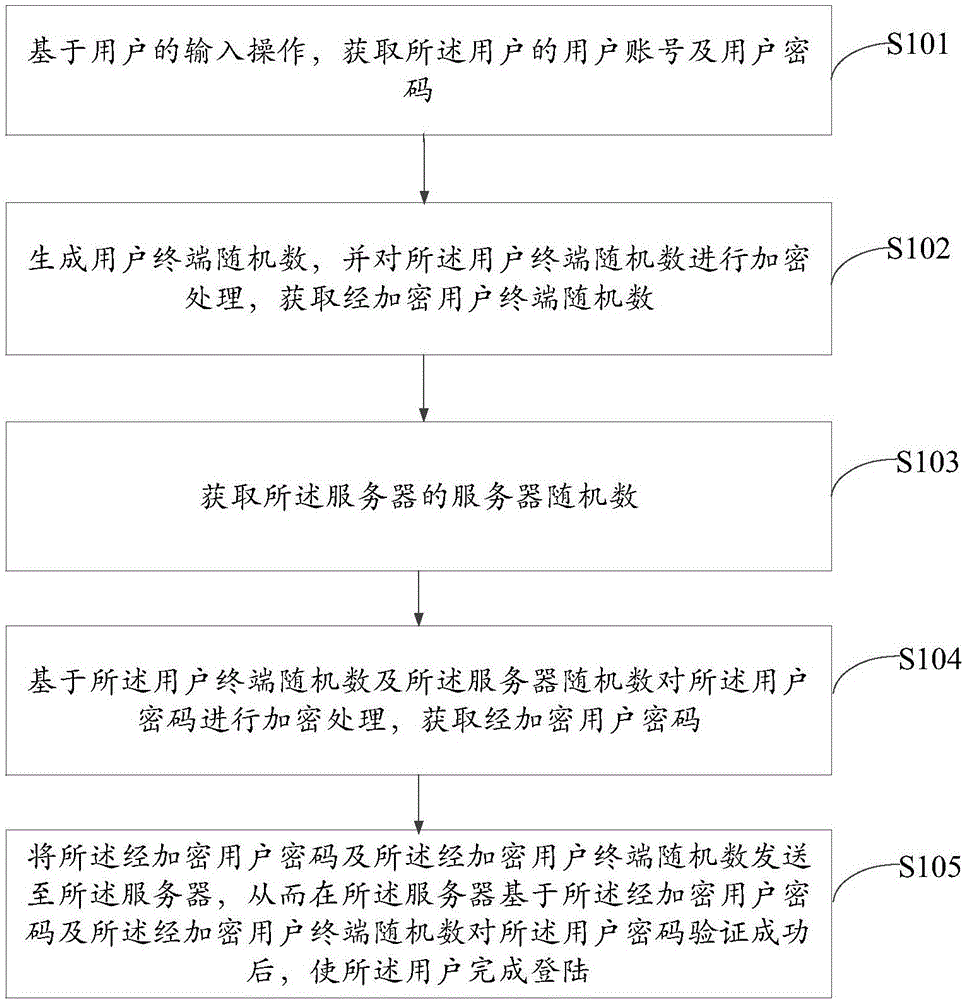
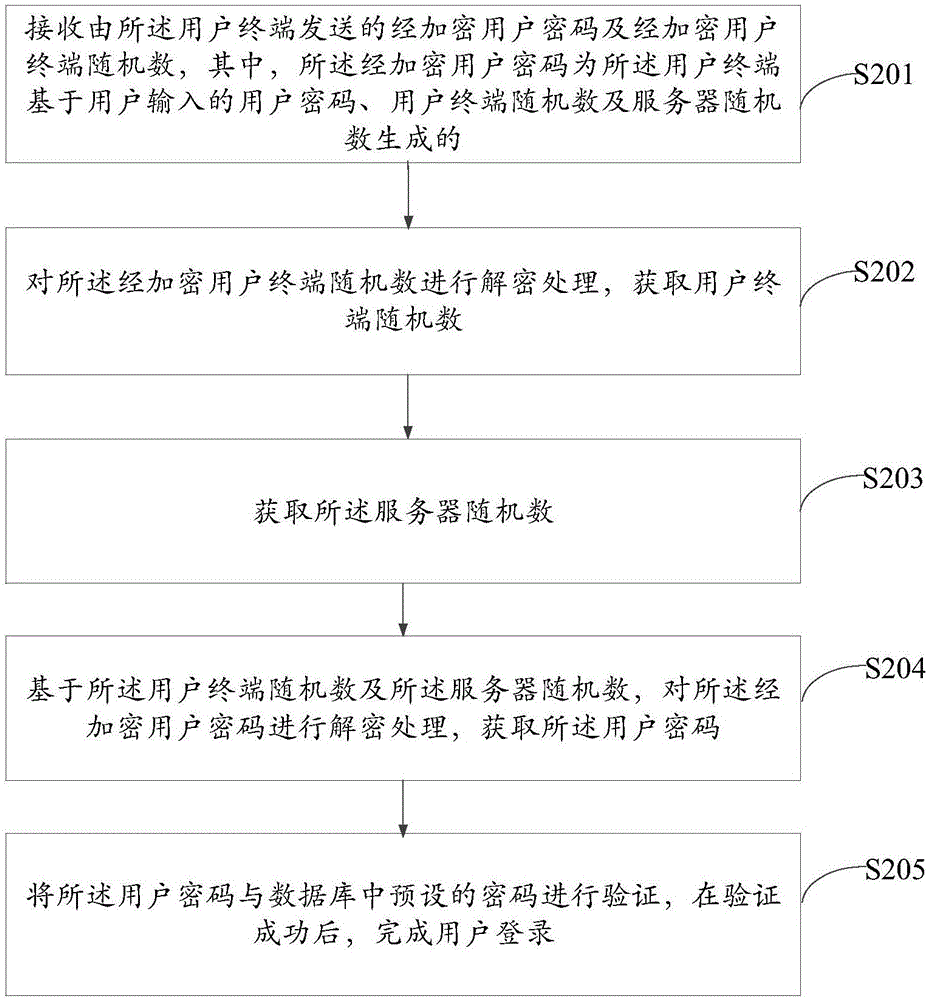
User login method, user terminal and server
ActiveCN106533677ASolve technical problems with low securityImprove securityKey distribution for secure communicationPasswordCipher
The invention discloses a user login method, a user terminal and a server. The user terminal is connected with the server. The method comprises the following steps: acquiring a user account and a user password of a user based on an input operation of the user; generating a user terminal random number, encrypting the user terminal random number, and acquiring an encrypted user terminal random number; acquiring a server random number of the server; encrypting the user password based on the user terminal random number and the server random number, and acquiring an encrypted user password; and transmitting the encrypted user password and the encrypted user terminal random number to the server, so that the user finishes login after successful verification of the user password based on the encrypted user password and the encrypted user terminal random number by the server.
Owner:SICHUAN JIUZHOU ELECTRIC GROUP
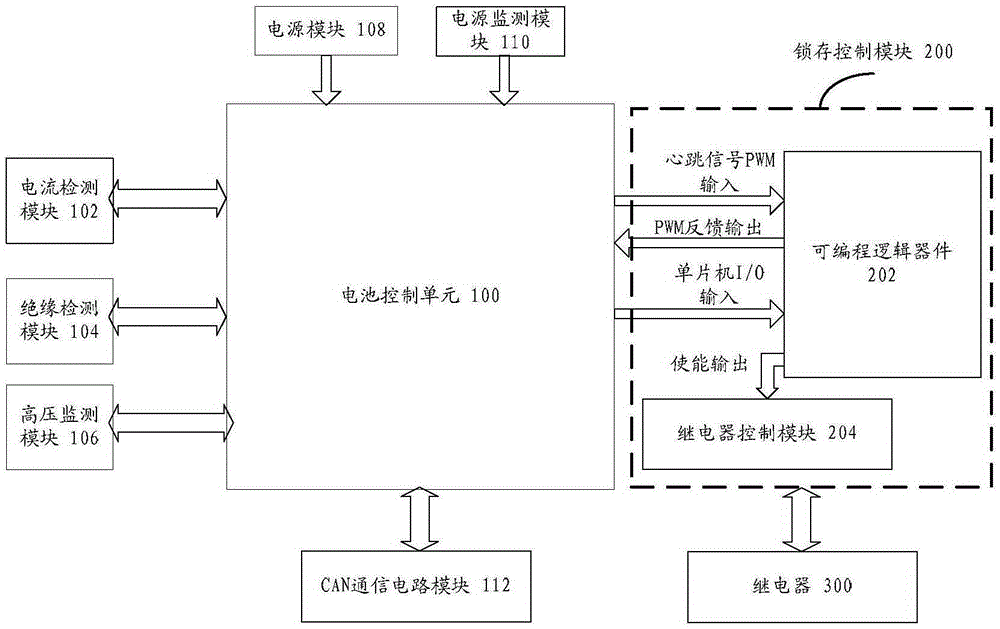
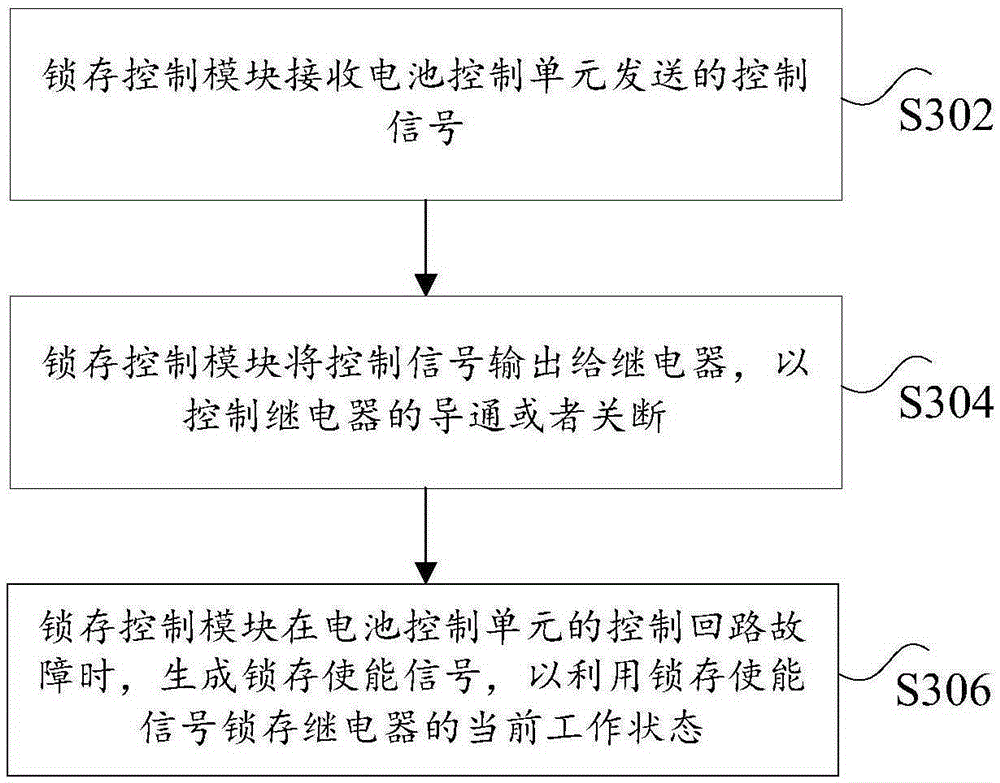
Battery management system and control method therefor
InactiveCN105429202AAvoid technical issues with power outagesSolve technical problems with low securityElectric powerVehicular energy storageControl signalWork status
The invention discloses a battery management system and a control method therefor. The battery management system comprises: a battery control unit used for outputting a control signal; a relay used for controlling the on or off state of a high-voltage relay loop according to the control signal; and a latch control module connected between the battery control unit and the relay and used for detecting a working state of the relay and latching the current working state of the relay when a control loop of the battery control unit has a fault. According to the battery management system and the control method, the technical problem of relatively low security of the battery management system is solved.
Owner:BEIJING ELECTRIC VEHICLE
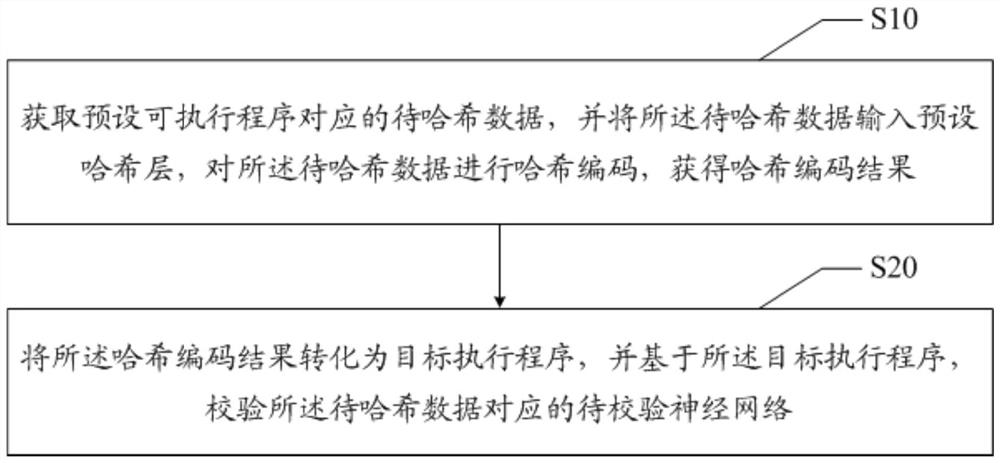
Neural network verification method, device and equipment, and readable storage medium
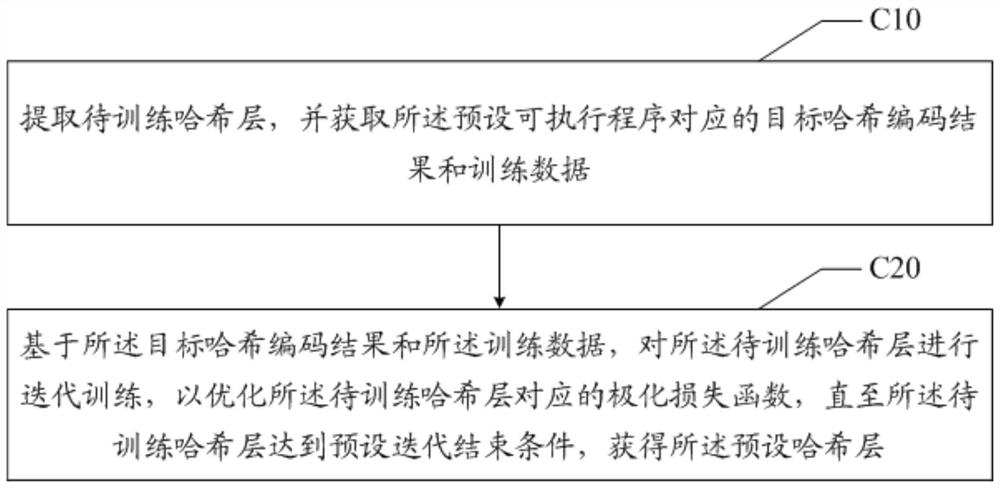
ActiveCN111628866AAvoid safety hazardsImprove securityEncryption apparatus with shift registers/memoriesUser identity/authority verificationHash codingNeural network nn
The invention discloses a neural network verification method, device and equipment and a readable storage medium. The neural network verification method comprises the following steps: obtaining to-be-hashed data corresponding to a preset executable program, inputting the to-be-hash data into a preset hash layer, performing hash encoding on the to-be-hash data to obtain a hash encoding result, converting the hash encoding result into a target execution program, and verifying a to-be-verified neural network corresponding to the to-be-hash data based on the target execution program. According tothe invention, the technical problem of low neural network verification security is solved.
Owner:WEBANK (CHINA)
File access control method and device, storage medium and electronic device
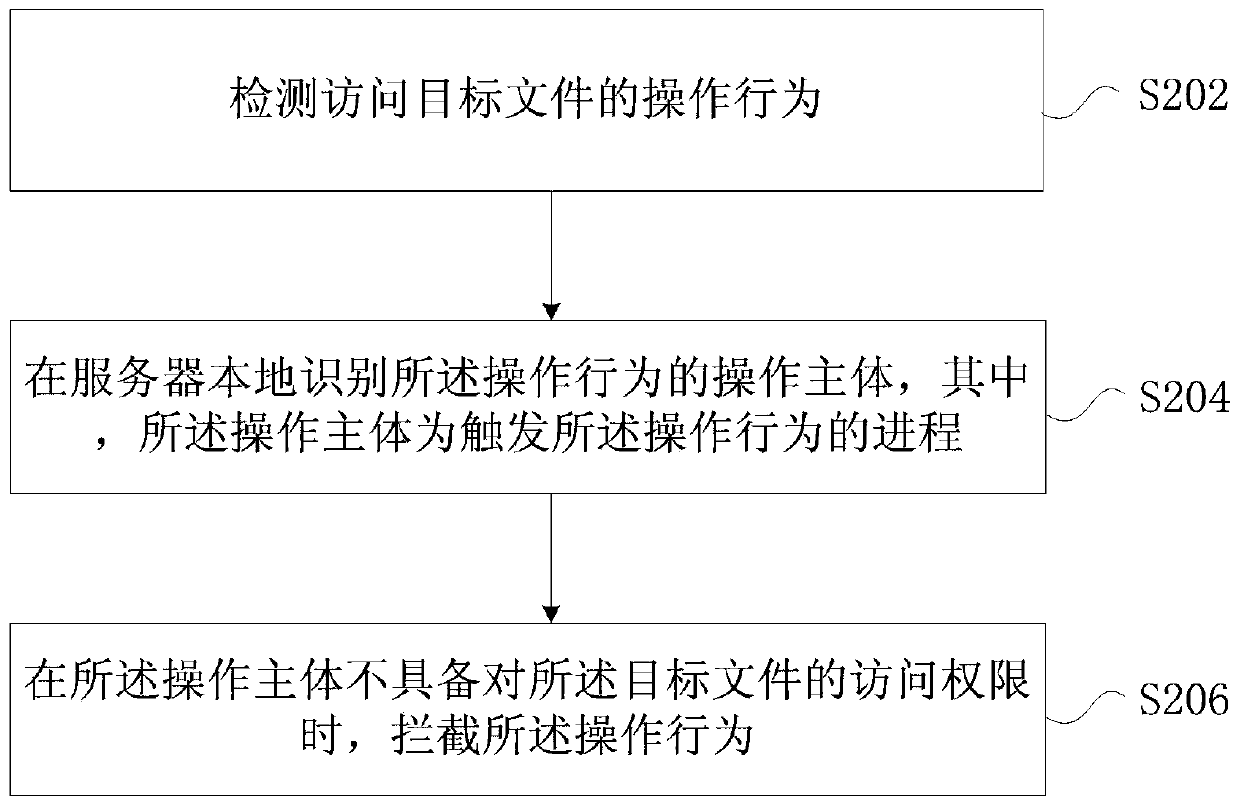
InactiveCN109766700AAvoid illegal operationSolve technical problems with low securityPlatform integrity maintainanceOperational behaviorObject file
The invention provides a file access control method and device, a storage medium and an electronic device, and the method comprises the steps of detecting an operation behavior of accessing a target file; locally identifying an operation main body of the operation behavior in a server, the operation main body being a process for triggering the operation behavior; and when the operation subject does not have the access permission to the target file, intercepting the operation behavior. Through the present invention, the technical problem of low file security in related technologies is solved, and the file security is improved.
Owner:QI AN XIN SECURITY TECH ZHUHAI CO LTD +1
Information processing method and electronic equipment
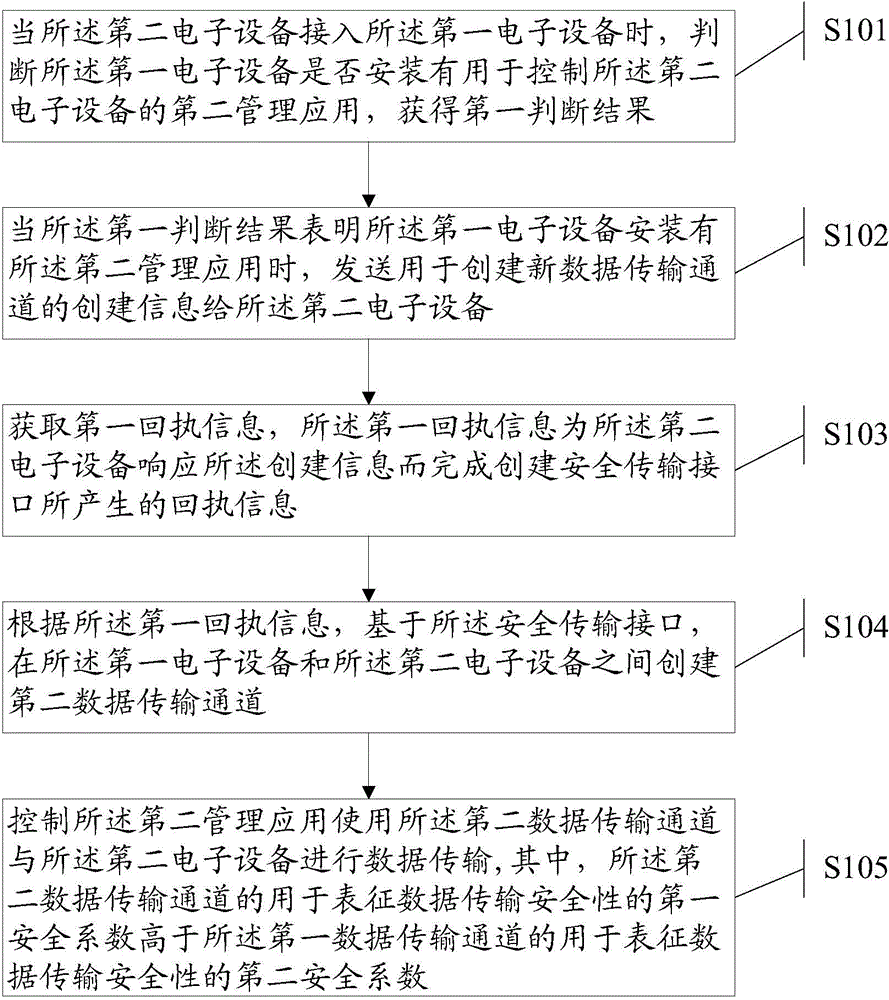
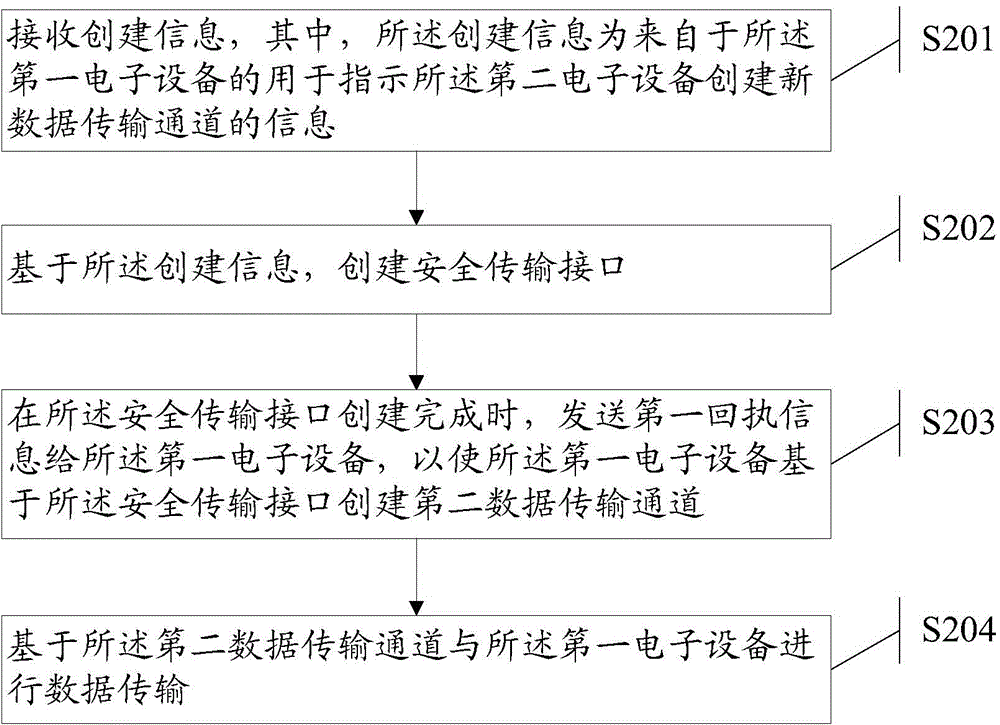
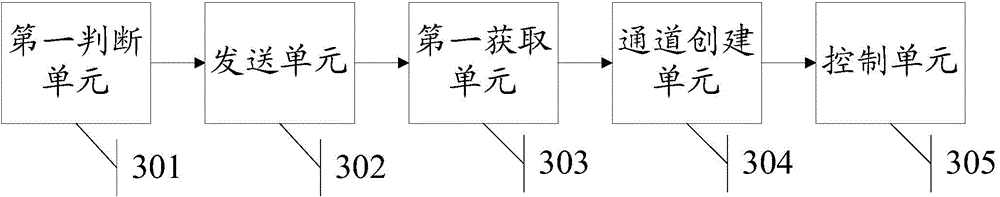
ActiveCN104462002AImprove securitySolve technical problems with low securityNetwork topologiesDigital data protectionData transmissionComputer hardware
The invention discloses an information processing method and electronic equipment and aims to solve the technical problem that in the prior art, the electronic equipment are based on transmission interfaces with open source codes, and the established data transmission channels are low in security. The method includes when second electronic equipment is connected to first electronic equipment, judging whether a second management application used for controlling the second electronic equipment is installed in the first electronic equipment or not; if yes, transmitting establishment information used for establishing a fresh data transmission channel to the second electronic equipment; acquiring first receipt information produced by completing security transmission interface establishment of the second electronic equipment; according to the first receipt information, on the basis of the security transmission interface, establishing a second data transmission channel; controlling second management application to use the second data transmission channel to perform data transmission with the second electronic equipment. The security of the second data transmission channel is higher than that of the first data transmission channel.
Owner:LENOVO (BEIJING) CO LTD
Terminal device unlocking method and terminal device unlocking device
ActiveCN104951690ASolve technical problems with low securityImprove securityDigital data authenticationPasswordTerminal equipment
The invention discloses a terminal device unlocking method and a terminal device unlocking device. The terminal device unlocking method includes: displaying a first character generated randomly and an input box when a terminal device is in a screen locked state, wherein the first character includes one or more bits; receiving an inputted second character through the input box; comparing the second character with a third character obtained by converting the first character according to a preset conversion formula; if the second character is consistent with the third character, the terminal device is switched from the screen locked state into an unlocking state. The terminal device unlocking method and the terminal device unlocking device have the advantage that the technical problem of low safety of password unlocking in the prior art is solved, so that safety of password unlocking is improved.
Owner:TENCENT TECH (BEIJING) CO LTD
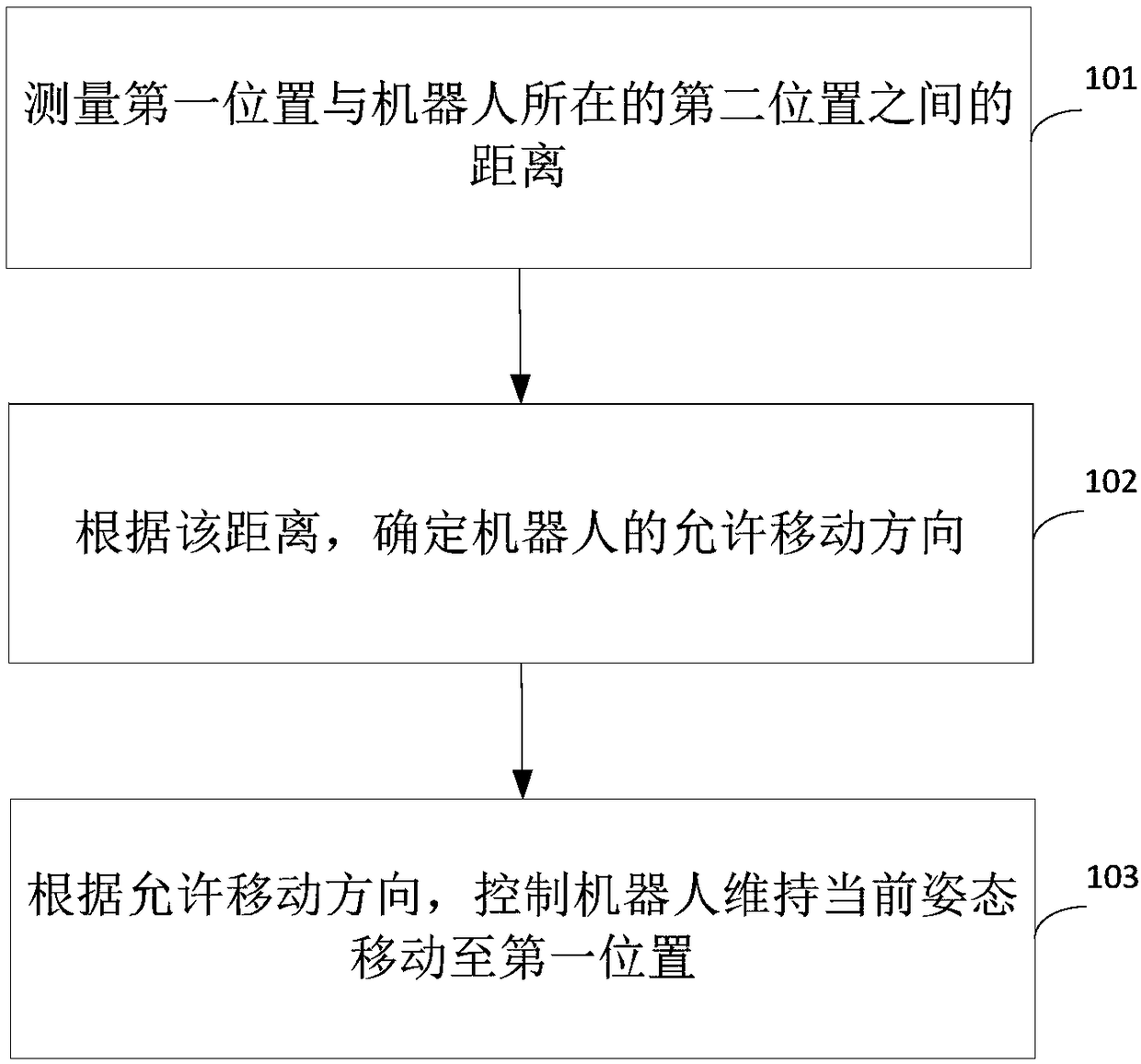
Robot moving control method and device
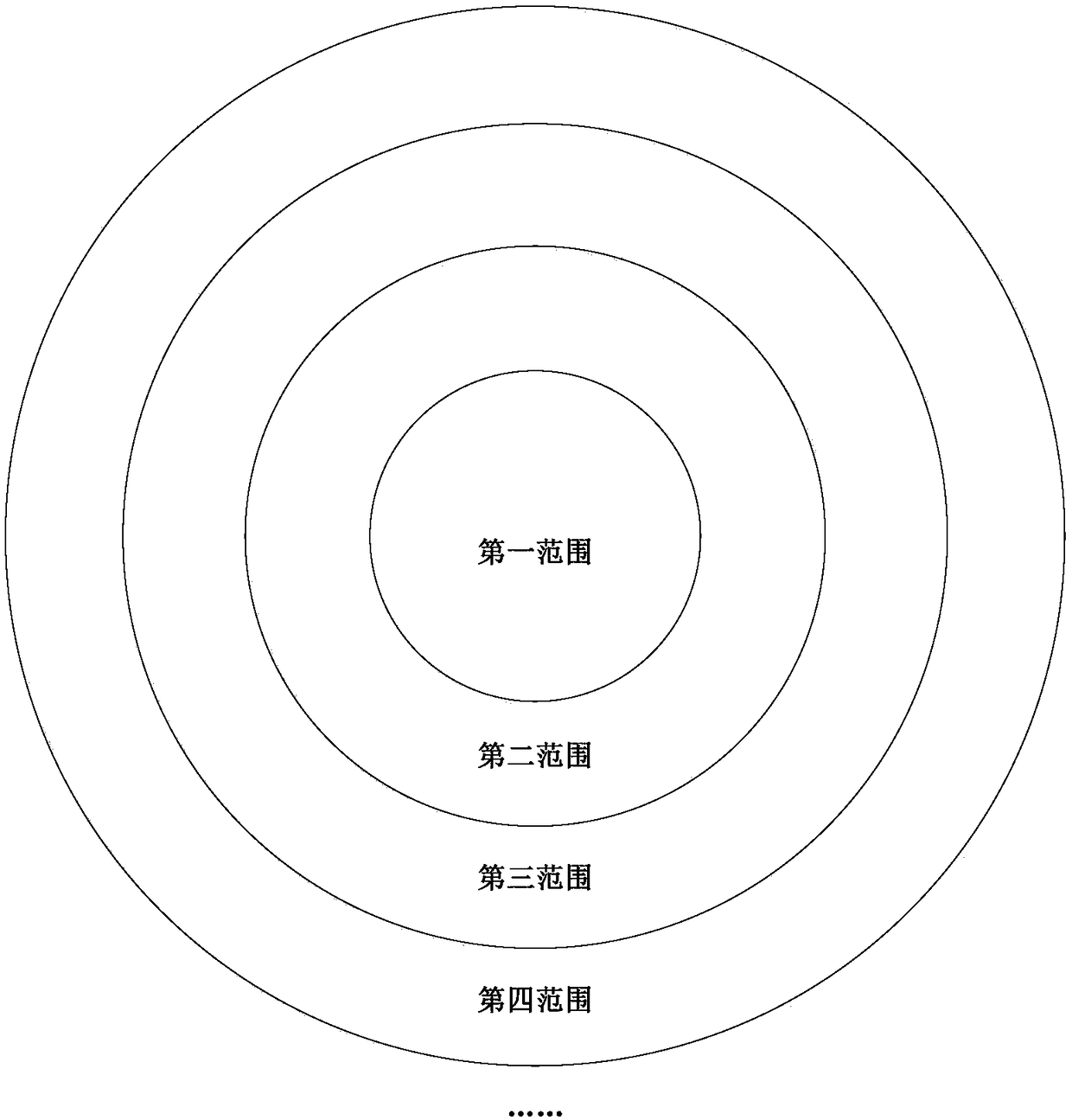
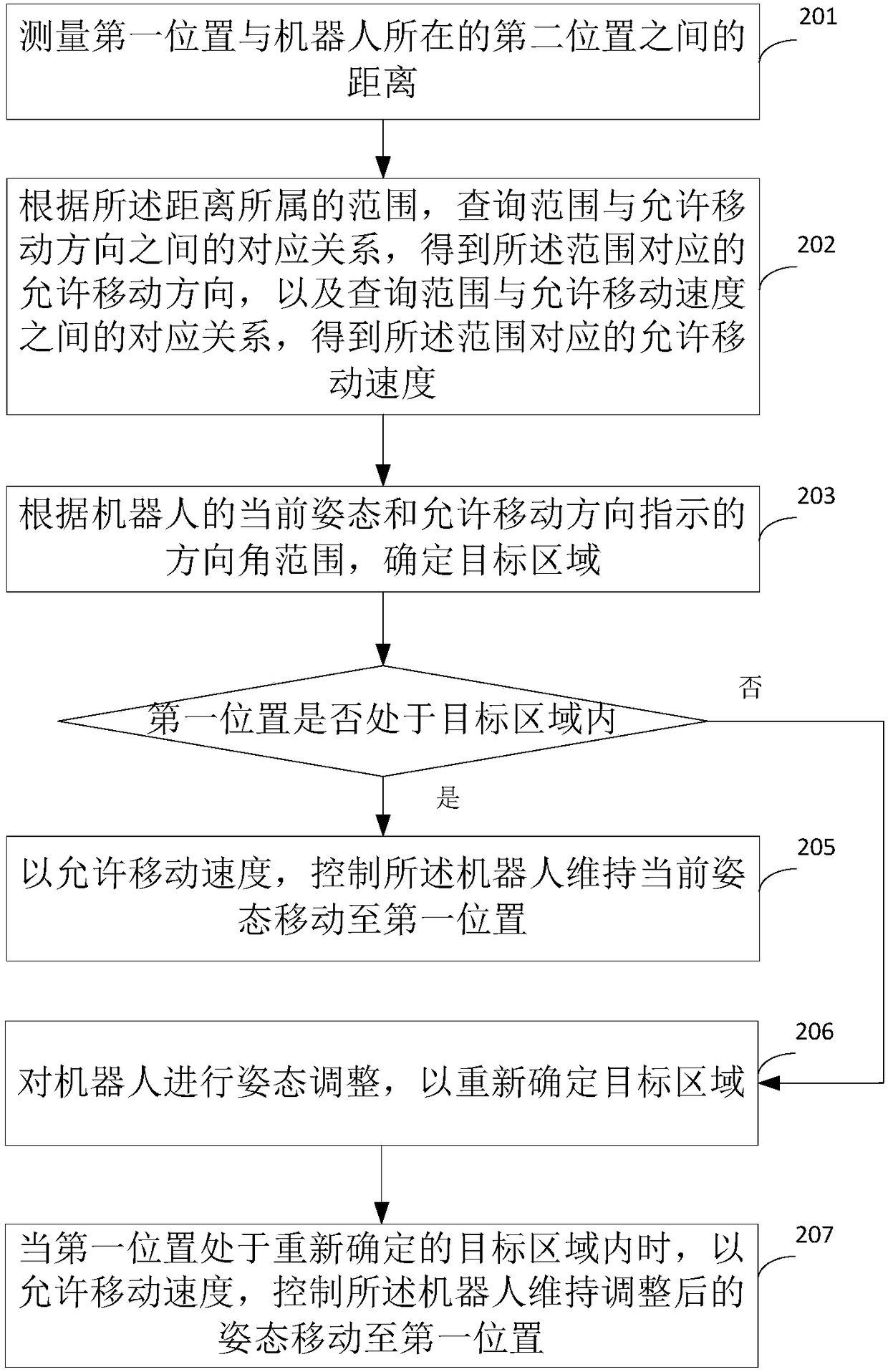
ActiveCN108733043AAvoid technical problems with low securitySolve technical problems with low securityPosition/course control in two dimensionsVehiclesShortest distanceEngineering
The invention provides a robot moving control method and a robot moving control device. The robot moving control method comprises the steps of: measuring a distance between a first position and a second position where a robot locates, determining an allowable moving direction of the robot according to the distance, and controlling the robot to maintain a current attitude and move to the first position according to the allowable moving direction. Since, in the case of ensuring safety, different distances correspond to different allowable moving directions, the robot maintains the current attitude and is moved to the first position within a range specified by the allowable moving direction after the corresponding allowable moving direction is determined according to the distance, thus the technical problem that the security is not high because the moving direction of the robot is controlled simply by means of the shortest distance or the fastest speed without considering the allowable moving direction in the prior art can be avoided.
Owner:BEIJING ORION STAR TECH CO LTD
Bluetooth encrypted communication system and communication method
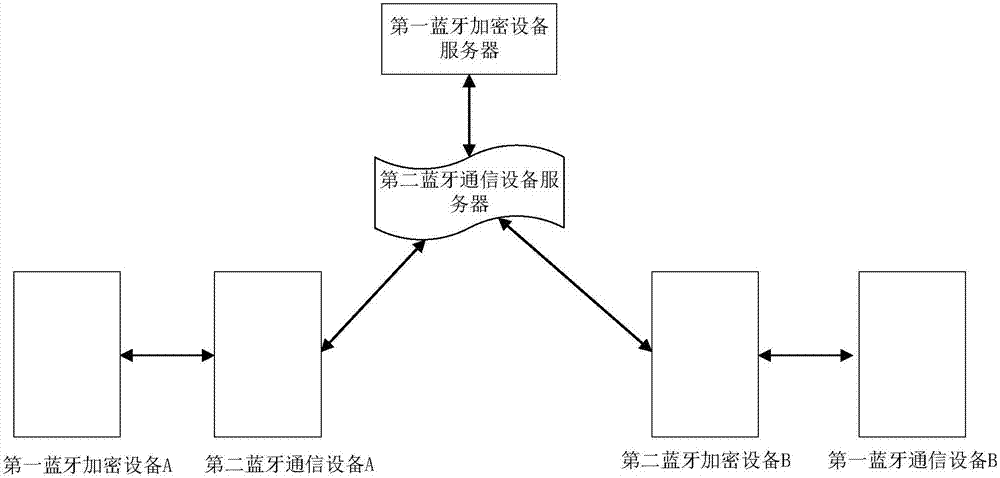
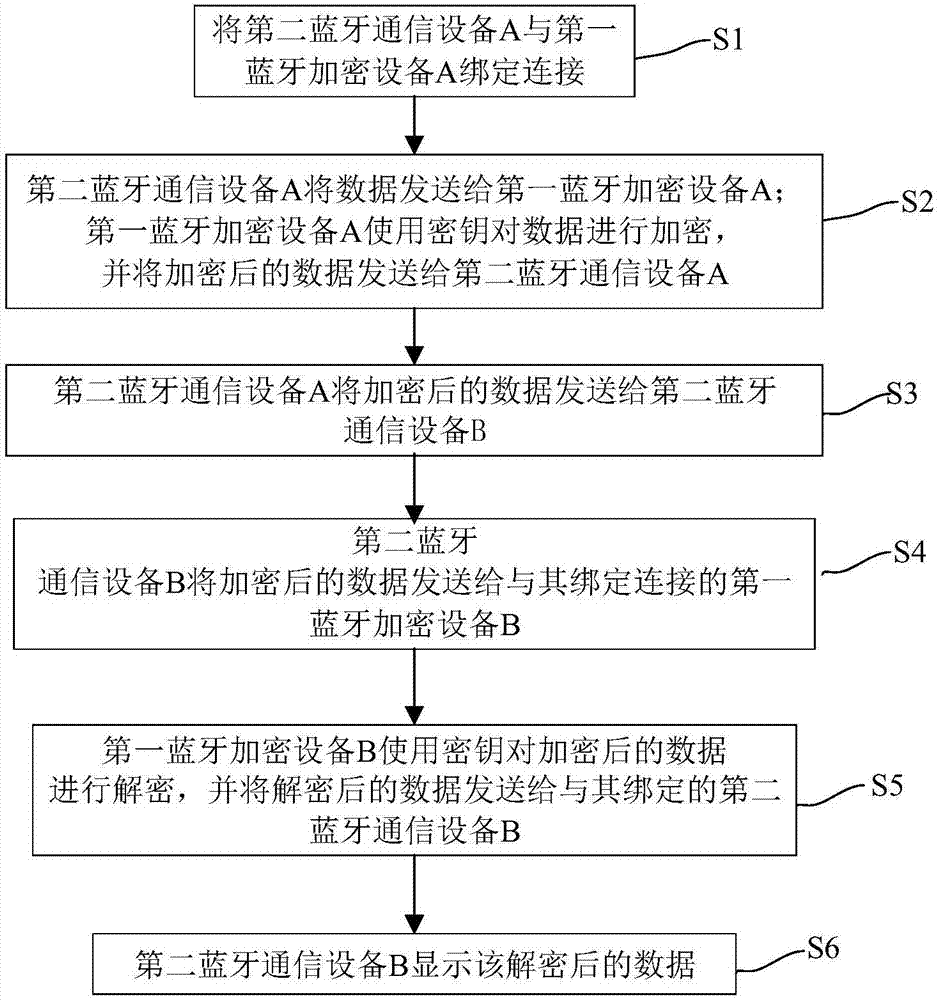
ActiveCN107426670AImprove securityPrevent leakageConnection managementWireless commuication servicesComputer hardwareCommunications security
The present invention provides a Bluetooth encrypted communication system and a communication method, which relate to the communication security field and solve the technical problem of low communication security in the prior art. The Bluetooth encrypted communication system of the present invention includes a plurality of first Bluetooth encrypted devices and a plurality of second Bluetooth communication devices. The communication software of the first Bluetooth encrypted devices and the second Bluetooth communication devices has a unique identification number, and each second Bluetooth communication device is linked to a first Bluetooth encrypted device, and the first Bluetooth encrypted devices encrypt or decrypt the data sent by the second Bluetooth communication devices. The system and the method of the present invention are applied to information transmission.
Owner:HENGBAO
Firmware upgrade method, device and system thereof
ActiveCN106802810AImprove securityRealize multiple protectionSoftware engineeringProgram loading/initiatingMultiplexerUpgrade
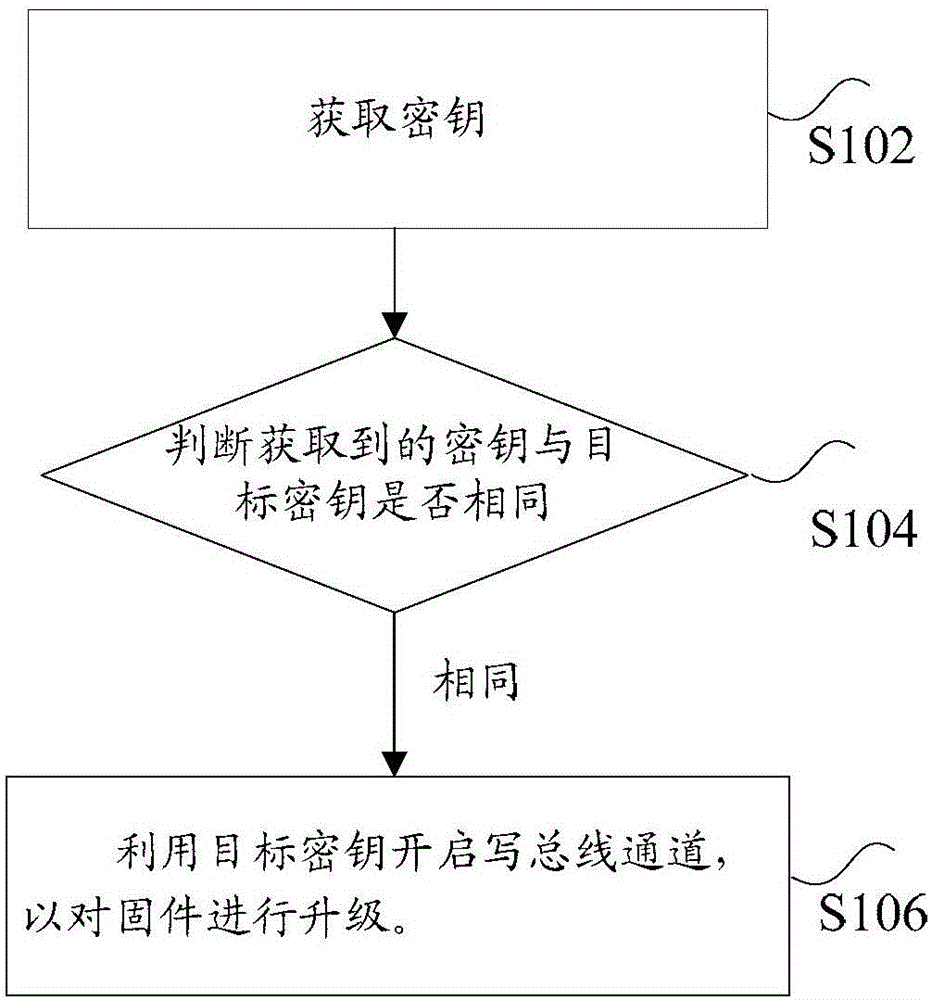
The invention discloses a firmware upgrade method, device and system thereof. The method comprises obtaining secret key and judging whether the obtained secret key is same as the target secret key or not, wherein the target secret key is used for opening the writing bus channel between the communication module and multiplexer to upgrade the firmware which is solidified in the target hardware, and the communication module and multiplexer are both installed on the target hardware. If obtained secret key is same as the target secret key, the target secret key is utilized to open the writing bus channel to upgrade the firmware. The firmware upgrade method, device and system thereof solve the technical problem of low safety when the firmware upgrades in upgrading process in the related art.
Owner:ANALOGIX SEMICON (SUZHOU) INC +1
FPGA-based SPWM variable-frequency speed control system and control method thereof
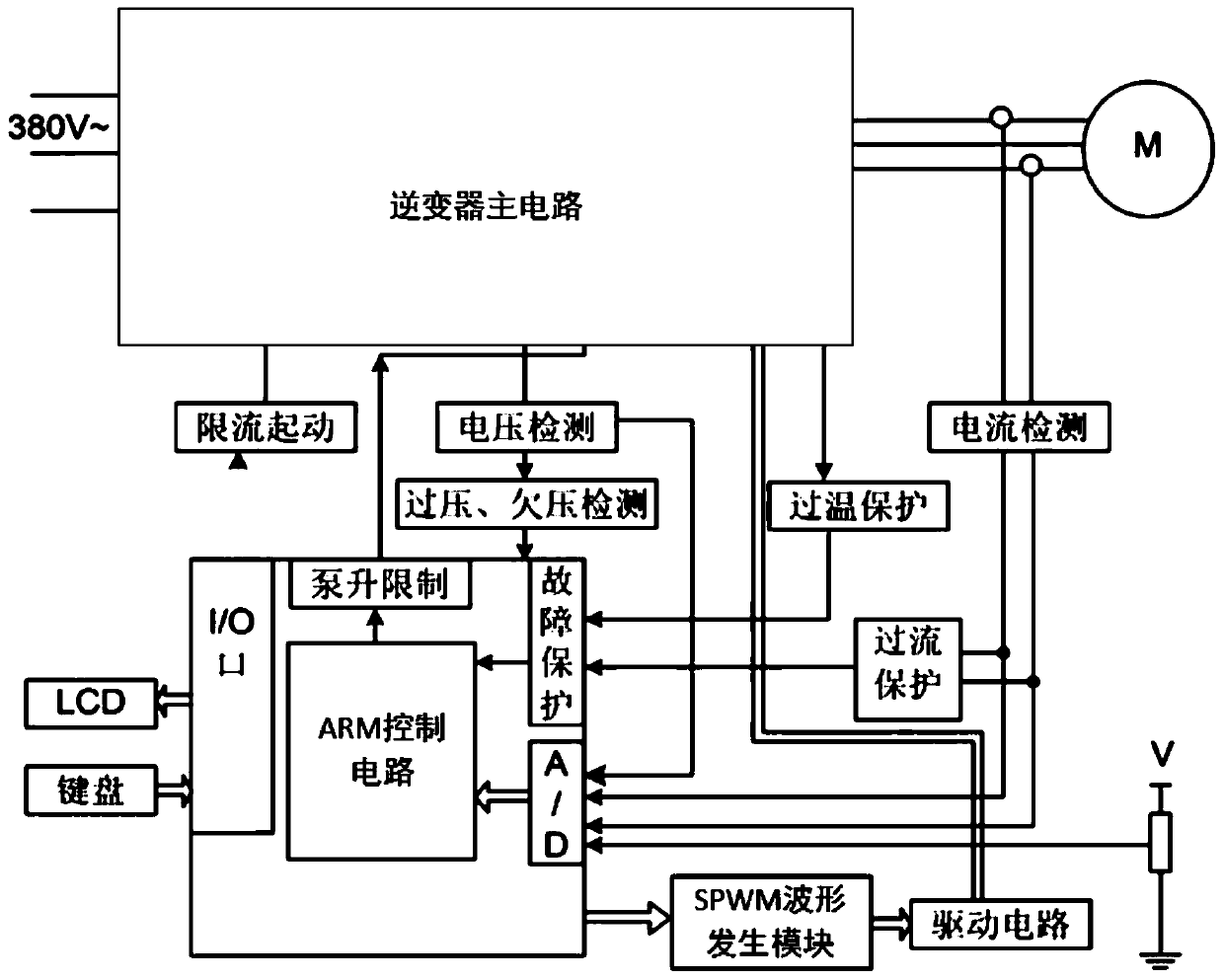
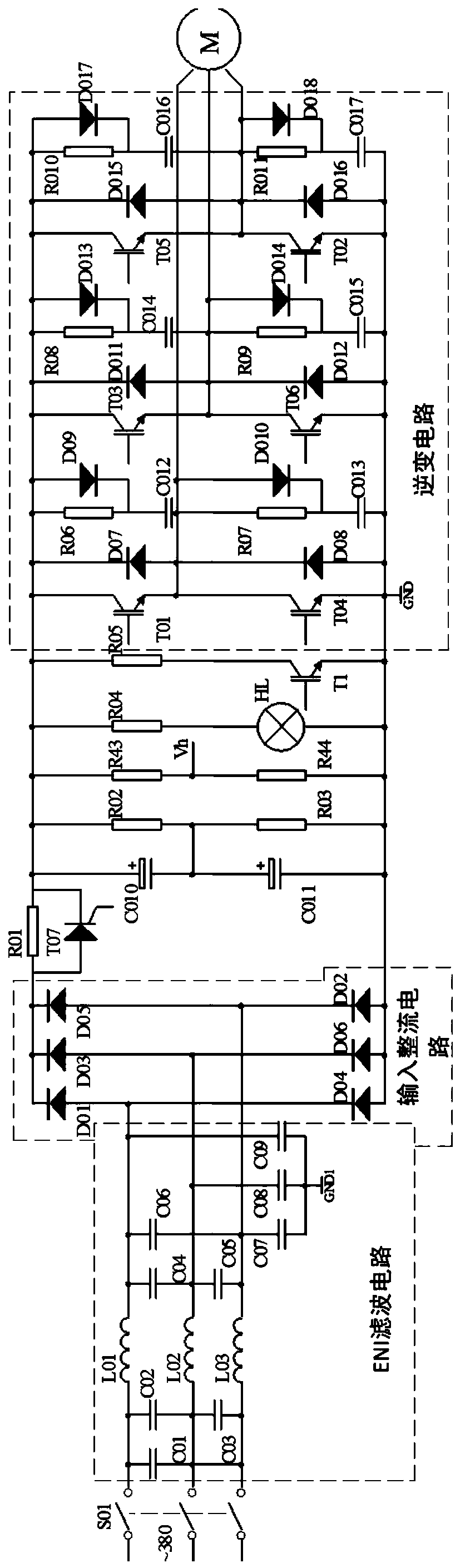
InactiveCN110474598ARealize all-digital frequency conversion speed regulationHighly integratedAC motor controlEmergency protective arrangements for automatic disconnectionOvervoltagePower inverter
An FPGA-based SPWM variable-frequency speed control system and a control method thereof belong to the technical field of variable-frequency control. A system in the prior art has low security. The FPGA-based SPWM variable-frequency speed control system comprises an inverter main circuit connected with an electric device to be called, wherein the inverter main circuit is connected with an ARM control circuit through a current-limiting starting circuit; the inverter main circuit is connected to an overvoltage and undervoltage detection circuit and the ARM control circuit through a voltage detection circuit; the overvoltage and undervoltage detection circuit is connected with the ARM control circuit; the inverter main circuit is connected with the ARM control circuit through an overtemperature protection circuit; the ARM control circuit is connected to a driving circuit through a SPWM waveform generating module; the inverter main circuit and the electric device to be called are connectedwith the overcurrent protection circuit and the ARM control circuit through the current detection circuit respectively; the overcurrent protection circuit is connected with the ARM control circuit; and the ARM control circuit and the inverter main circuit are connected to achieve pump rise limit control. The FPGA-based SPWM variable-frequency speed control system is improved in safety and reliability. The SPWM variable-frequency speed control system is further improved in cooperation with the method.
Owner:GUANGDONG VOCATIONAL & TECHNICAL COLLEGE
Data encryption method and device, storage medium and processor
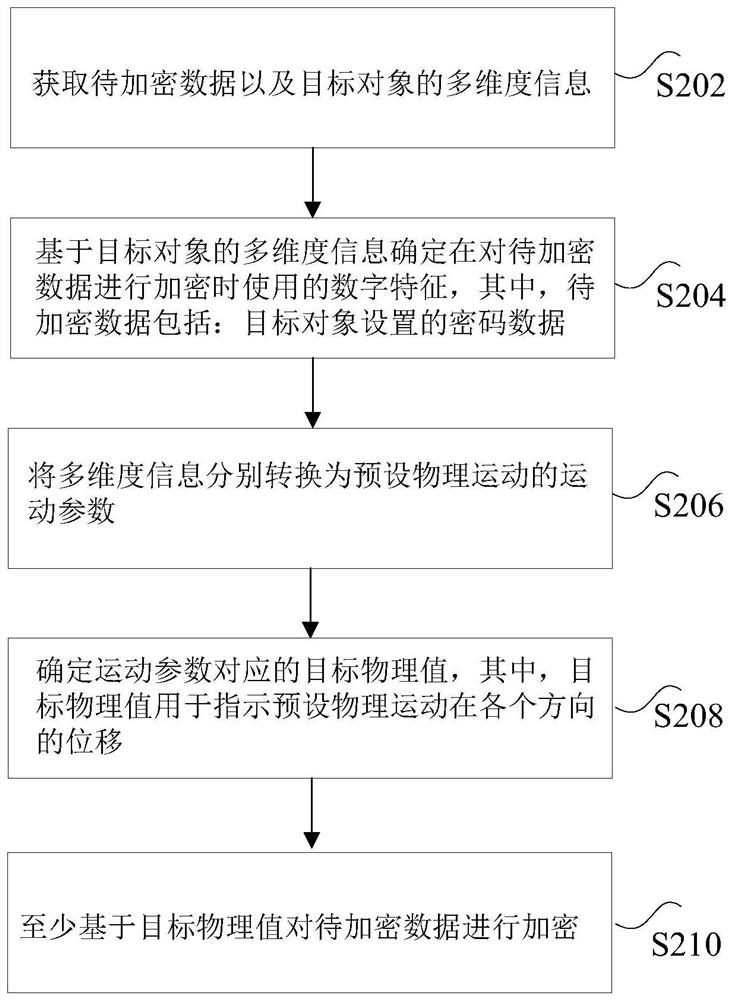
PendingCN114282239APrevent leakageSolve technical problems with low securityDigital data protectionComputer hardwareMotion parameter
The invention discloses a data encryption method and device, a storage medium and a processor. The method comprises the steps of obtaining to-be-encrypted data and multi-dimensional information of a target object; based on the multi-dimensional information of the target object, determining a digital feature used when the to-be-encrypted data is encrypted; converting the multi-dimensional information into motion parameters of preset physical motion; and determining a target physical value corresponding to the motion parameter, and encrypting the to-be-encrypted data at least based on the target physical value. According to the method and the device, the technical problem of low user information security caused by secret key leakage when user information is encrypted in the prior art is solved.
Owner:CHINA TELECOM CORP LTD
Anti-addiction triggering method and device based on fingerprint unlocking, terminal and storage medium
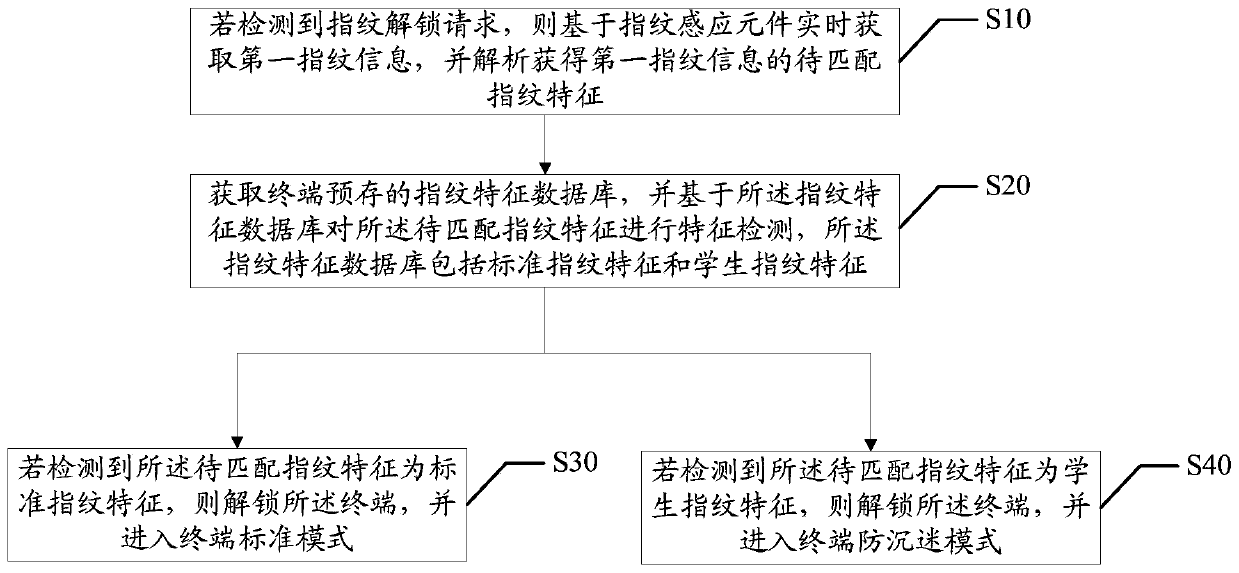
PendingCN110222494AIncrease the cost of useReduce the use effectDigital data authenticationPasswordData mining
The invention discloses an anti-addiction triggering method and device based on fingerprint unlocking, a terminal and a storage medium, the method is applied to the terminal, and the method comprisesthe following steps: if a fingerprint unlocking request is detected, obtaining first fingerprint information in real time based on a fingerprint sensing element, and analyzing to obtain to-be-matchedfingerprint characteristics of the first fingerprint information; acquiring a fingerprint feature database pre-stored in a terminal, and performing feature detection on the to-be-matched fingerprint features based on the fingerprint feature database, the fingerprint feature database comprising standard fingerprint features and student fingerprint features; if it is detected that the to-be-matchedfingerprint feature is a standard fingerprint feature, unlocking the terminal, and entering a terminal standard mode; and if it is detected that the to-be-matched fingerprint feature is the student fingerprint feature, unlocking the terminal, and entering a terminal anti-addiction mode. The security of the anti-addiction mode of the terminal is improved, and the technical problem that the securityis not high due to the fact that password unlocking of a traditional terminal is easy to crack is solved.
Owner:NUBIA TECHNOLOGY CO LTD
Authorization method of electronic key, storage medium and computer equipment
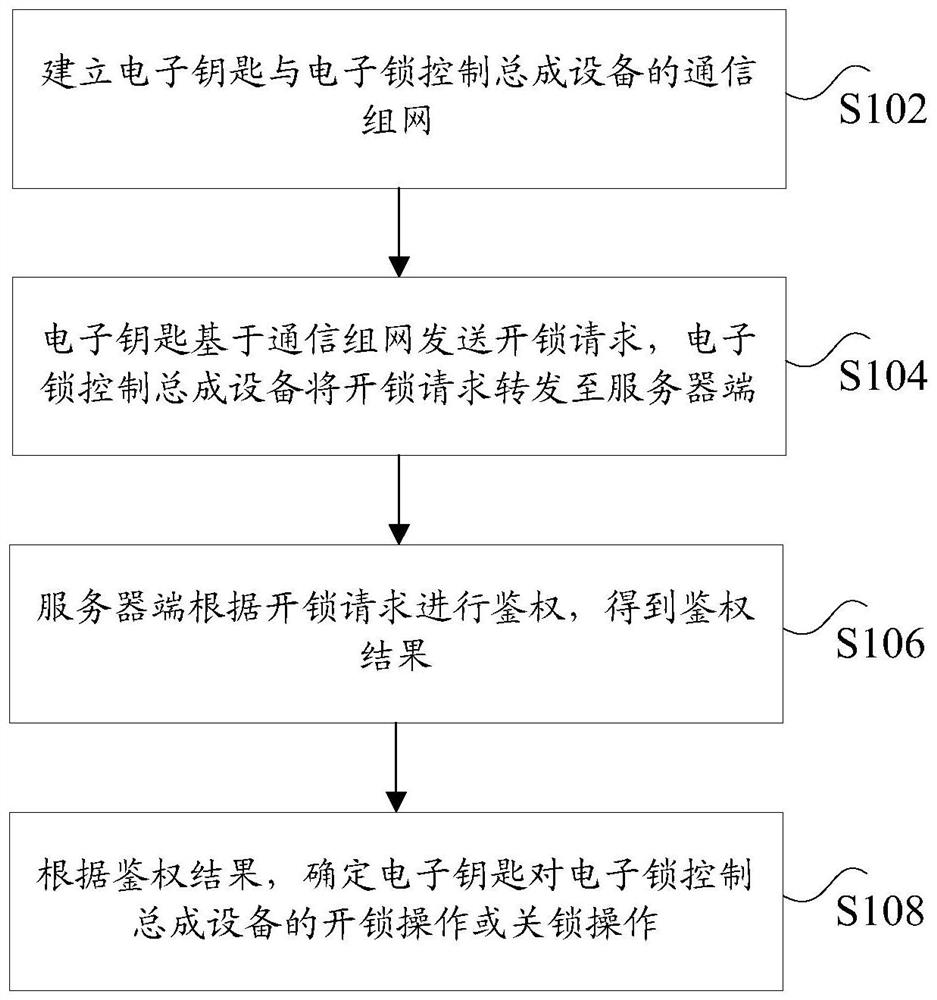
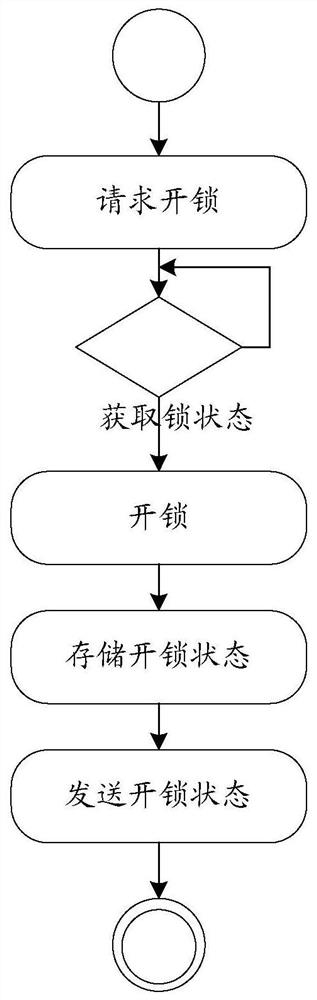
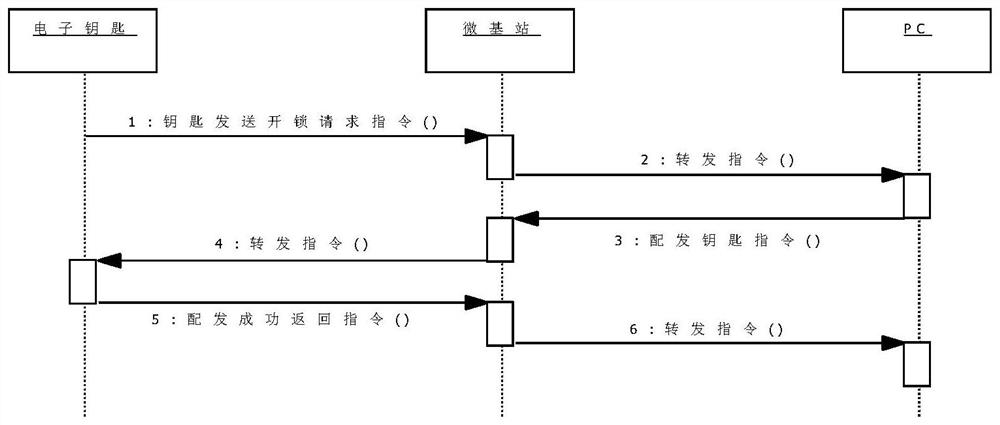
ActiveCN113034734AImprove safety and reliabilityImprove securityIndividual entry/exit registersTransmissionComputer equipmentAuthorization
The invention discloses an authorization method of an electronic key, a storage medium and computer equipment. The method comprises the following steps that a communication network of an electronic key and electronic lock control assembly equipment is established; the electronic key sends an unlocking request based on communication networking, and the electronic lock control assembly equipment forwards the unlocking request to the server side; the server performs authentication according to the unlocking request to obtain an authentication result; according to the authentication result, the unlocking operation or the locking operation of the electronic key on the electronic lock control assembly equipment is determined. According to the method, the technical problem of low safety caused by incapability of effectively detecting authorization information due to adoption of off-line electronic key authorization in related art is solved.
Owner:PETROCHINA CO LTD
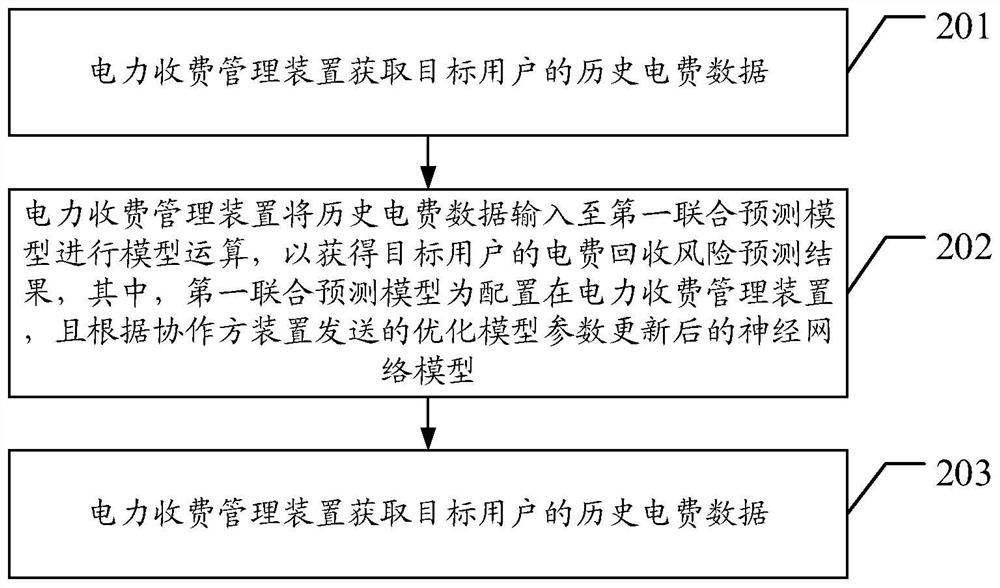
User electric charge recovery risk prediction method, device and system
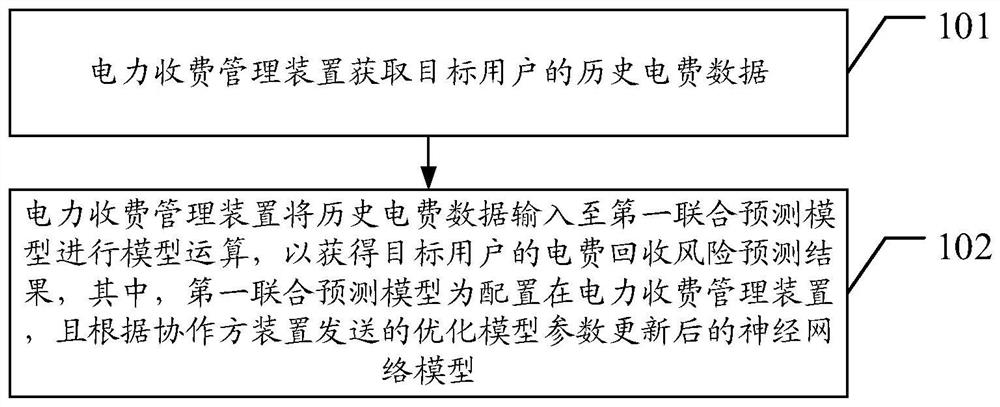
PendingCN111724000APrevent leakageSolve technical problems with low securityForecastingDigital data protectionEngineeringNetwork model
The invention provides a user electric charge recovery risk prediction method, device and system. The method comprises the steps that an electric charge management device acquires historical electriccharge data of a target user; the power charge management device inputs the historical electric charge data into a first joint prediction model for model operation to obtain an electric charge recovery risk prediction result of the target user, wherein the first joint prediction model is a neural network model which is configured in the power charging management device and is updated according tothe optimization model parameters sent by the collaboration party device. The method is based on a federated learning architecture. On the premise that the power charging management device does not need to carry out data interaction with data of other departments, data of a plurality of participating departments are fused, the prediction effect is ensured, internal confidentiality of each department is prevented from being leaked, and the technical problem that existing electric charge recovery risk prediction is low in information security is solved.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +1
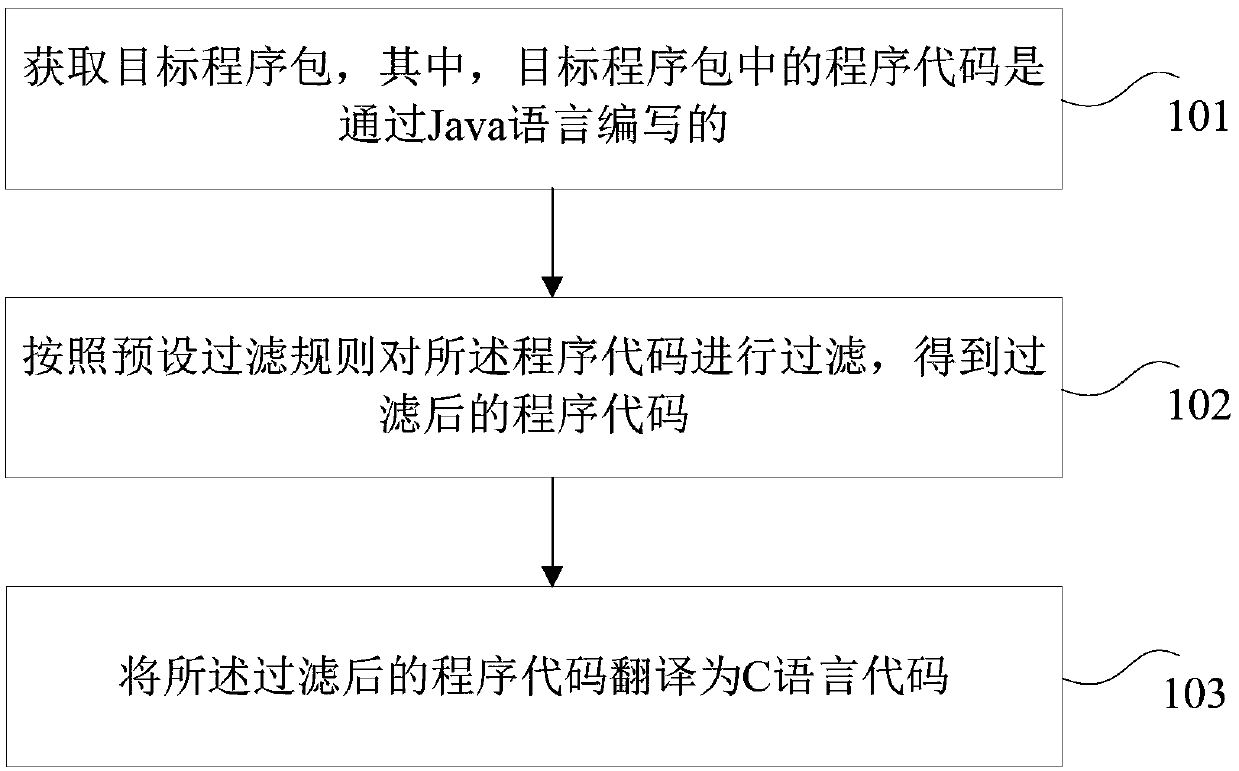
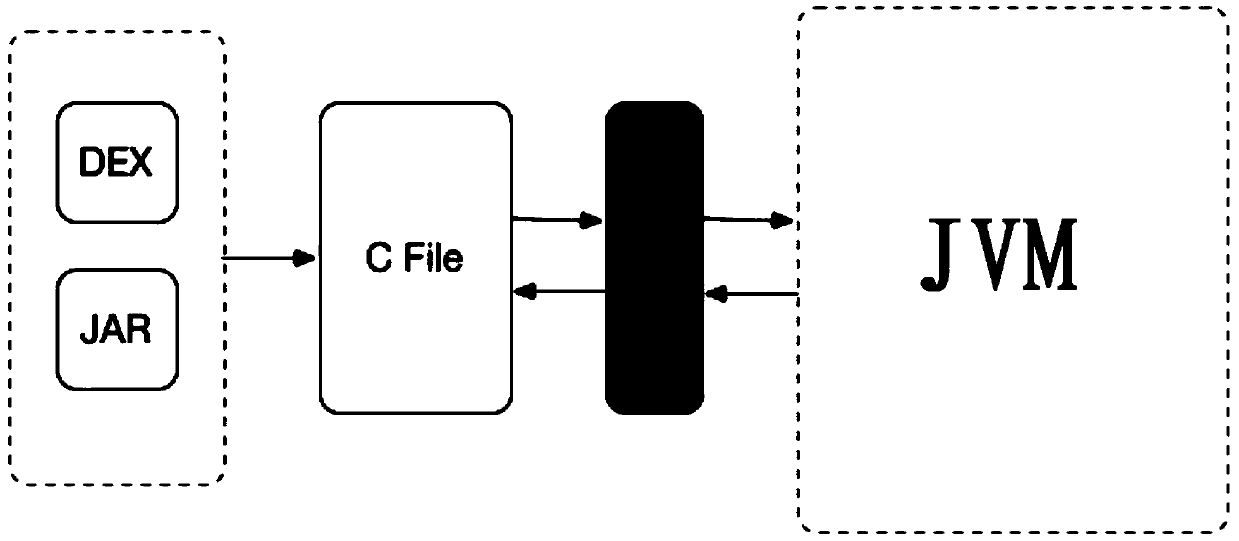
Data processing method and device, program running method
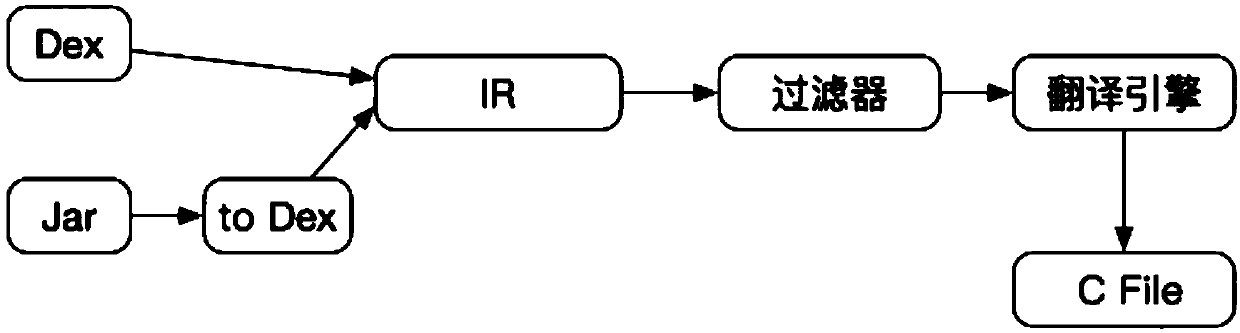
PendingCN110531965ASolve technical problems with low securityImprove securityCreation/generation of source codeFiltering rulesProgram code
The invention provides a data processing method and device, and a program running method. The data processing method comprises the steps: obtaining a target program package, wherein a program code inthe target program package is written through a Java language; filtering the program code according to a preset filtering rule to obtain a filtered program code; and translating the filtered program code into a C language code. By means of the scheme, the technical problem that existing Java program codes are not high in safety is solved, and the technical effects of effectively improving the codesafety and improving the cracking difficulty are achieved.
Owner:ALIBABA GRP HLDG LTD
Data interaction method, device and system
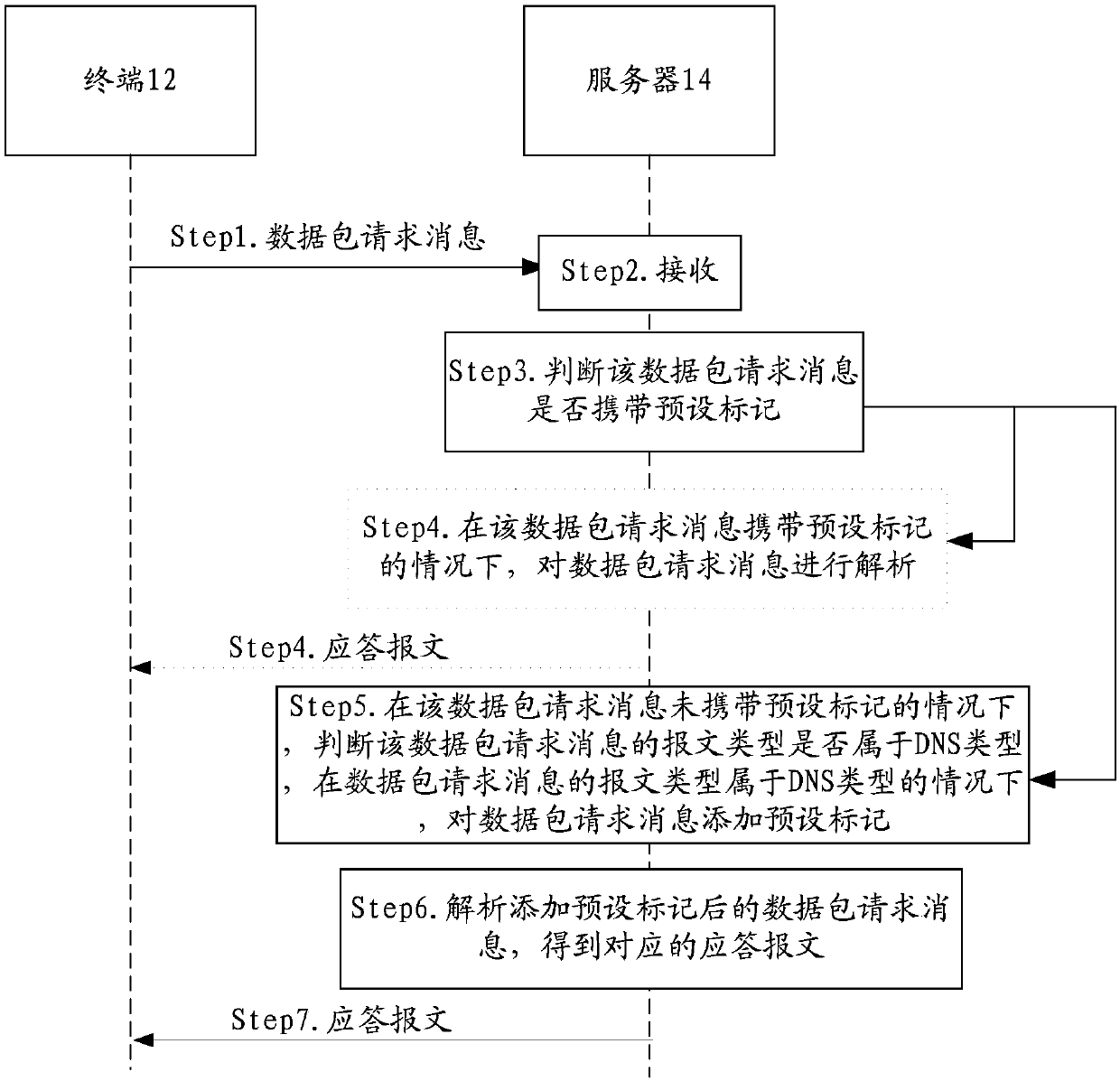
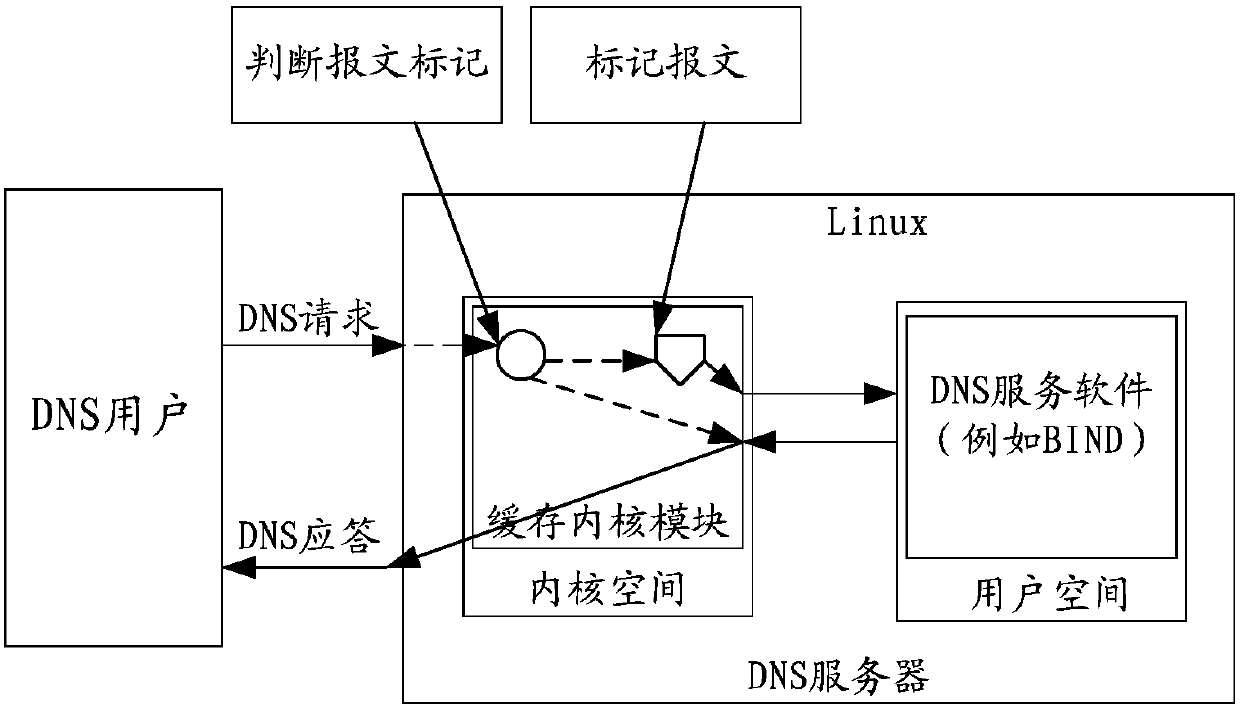
ActiveCN109756454ATo achieve the purpose of filtering and identifyingImprove securityTransmissionMessage typeComputer science
The invention discloses a data interaction method, device and system. The method comprises the following steps: under the condition that a data packet request message does not carry a preset mark, judging whether the message type of the data packet request message is the same as the preset message type or not; Marking a preset mark on the data packet request message under the condition that the message type is the same as the preset message type; and returning a message corresponding to the data packet request message to the terminal. The technical problem that the network security is low dueto the fact that data packet filtering fails due to the fact that a network card interface is called for packet returning in the prior art is solved.
Owner:ALIBABA GRP HLDG LTD
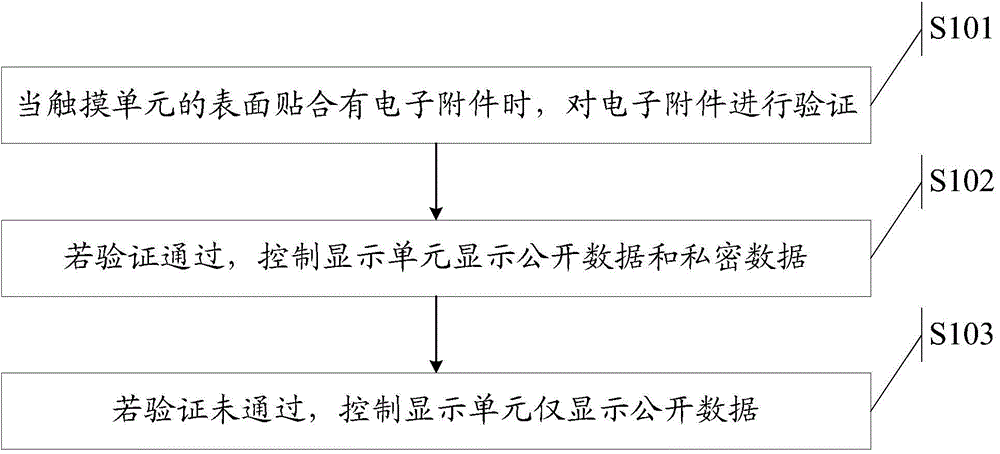
Method for displaying data and electronic equipment
InactiveCN104573542ASolve technical problems with low securityImprove securityStatic indicating devicesDigital data protectionComputer hardwareData display
A data display method and an electronic device thereof are provided by the invention to address the technical problem in the prior art of the low security for displaying data due to the indistinguishable data display of the electronic device. The method is applied in an electronic device. The electronic device comprises a display unit and a touch unit. The electronic device is able to communicate data with an electronic accessory and there are public data and private data corresponding to the electronic accessory. The method comprises steps of verifying the electronic accessory when the electronic accessory has been attached on the surface of the touch unit; controlling the display unit to display both the public data and the private data if the verification is successful; and controlling the display unit to display only the public data if the verification is not successful.
Owner:LENOVO (BEIJING) LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com