Access control method and device based on roles and terminal credibility
A technology of access and reliability, applied in the field of information security, can solve the problem of low security, and achieve the effect of solving low security, high scalability and adaptability, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
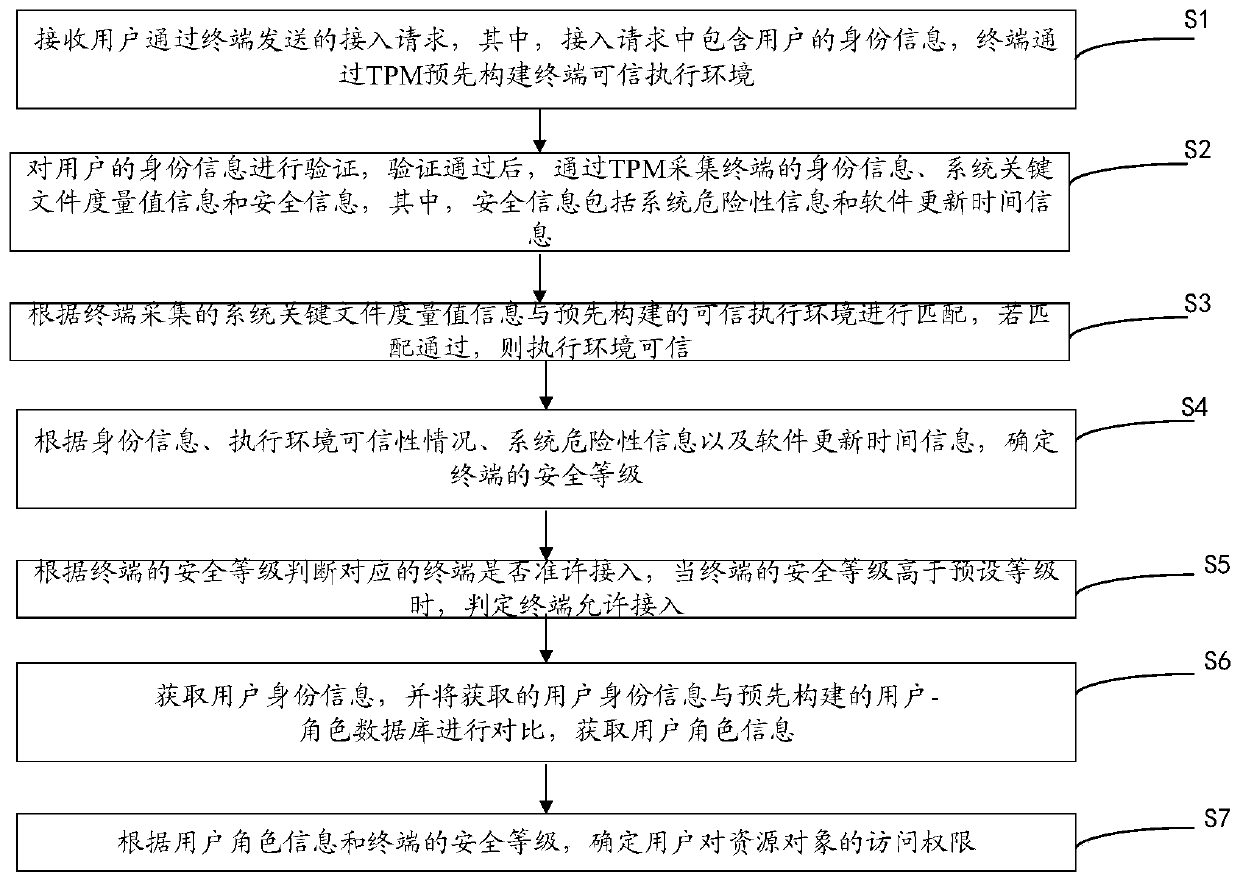
[0063] This embodiment provides an access control method based on role and terminal credibility, which is applied to the server. Please refer to figure 1 , the method includes:
[0064] Step S1: Receive the access request sent by the user through the terminal, wherein the access request includes the user's identity information, and the terminal pre-builds a terminal trusted execution environment through the TPM.
[0065] Specifically, the TPM (Trusted Platform Module) security chip refers to a security chip that meets the TPM (Trusted Platform Module) standard, which can effectively protect the PC and prevent unauthorized users from accessing it.
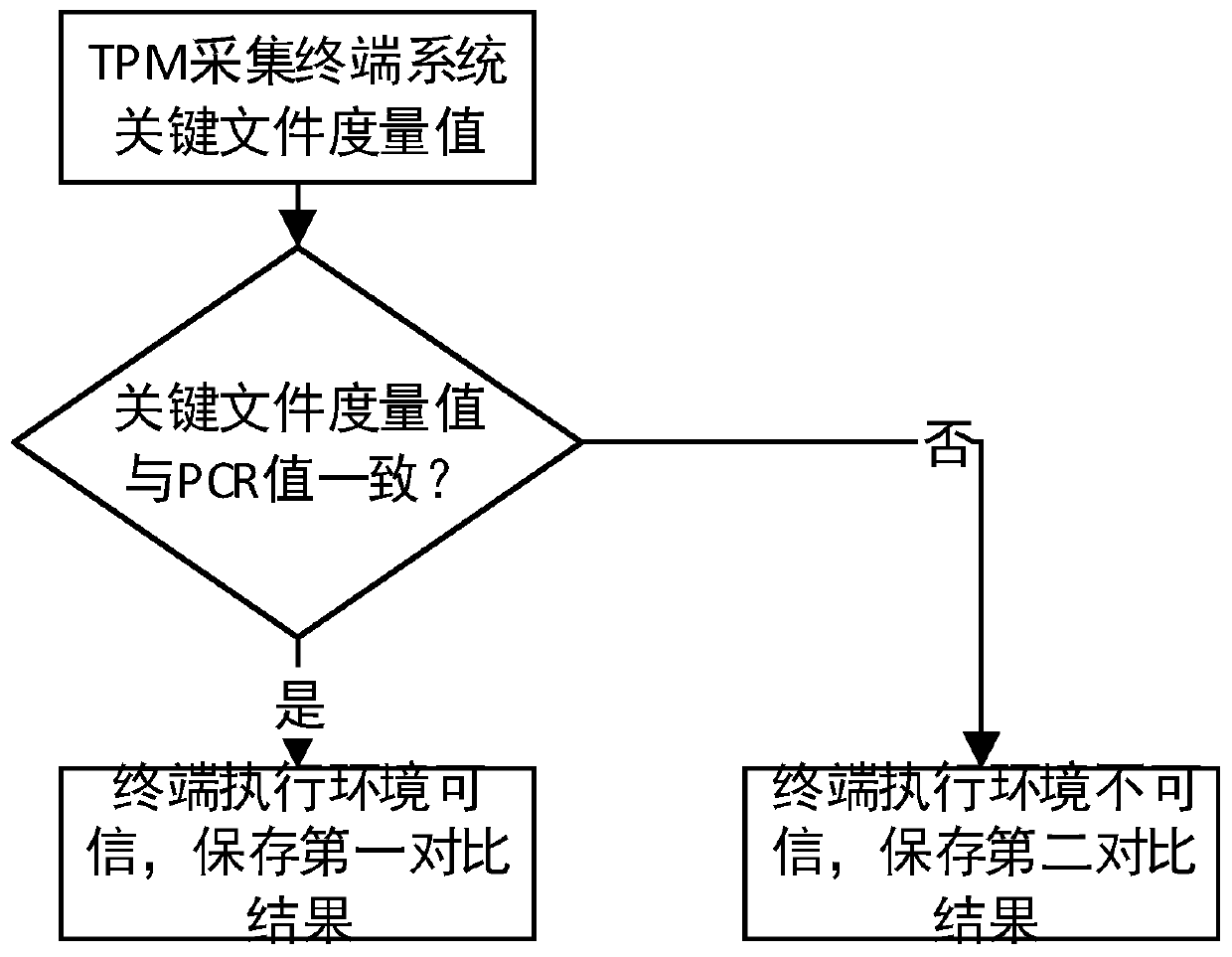
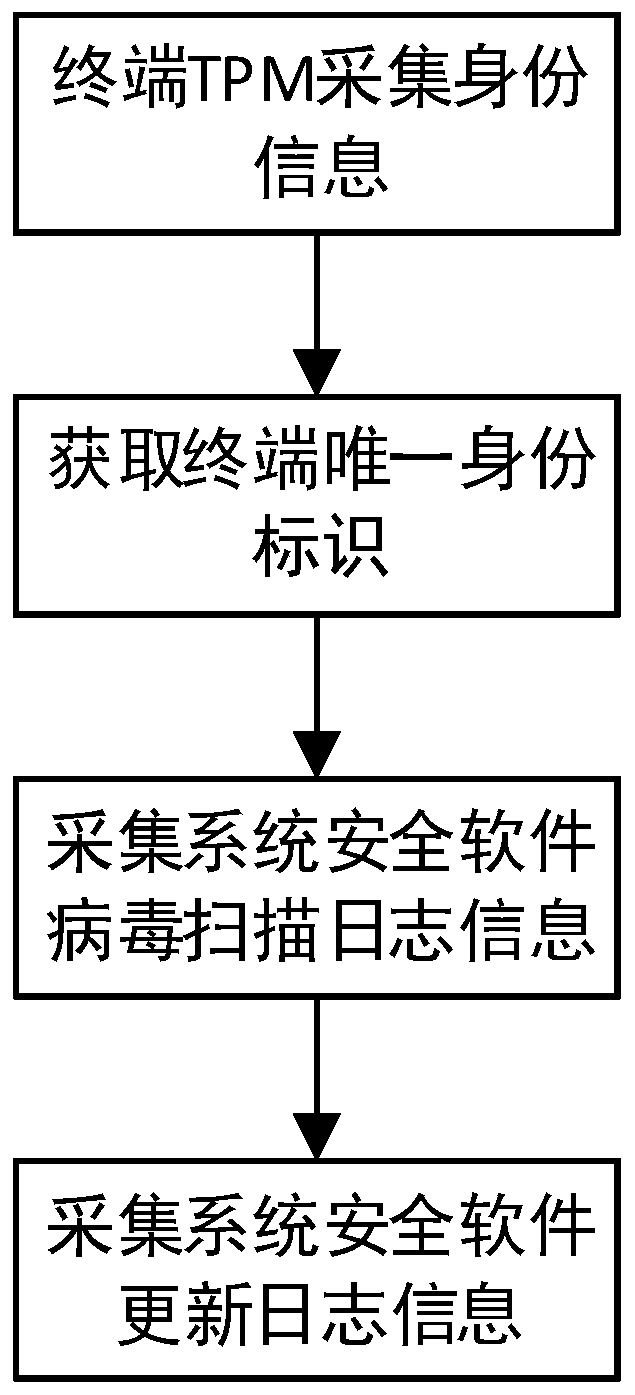
[0066] Step S2: Verify the user's identity information. After the verification is passed, collect the terminal's identity information, system key file measurement value information and security information through the TPM, wherein the security information includes system risk information and software update time information.
[006...
Embodiment 2
[0115] This embodiment provides an access control device based on role and terminal credibility, please refer to Figure 7 , the device is a server, including:
[0116] The access request receiving module 201 is configured to receive an access request sent by the user through the terminal, wherein the access request includes the identity information of the user, and the terminal pre-builds a terminal trusted execution environment through the TPM;
[0117] The identity verification module 202 is used to verify the user's identity information. After the verification is passed, the terminal's identity information, system key file measurement value information and security information are collected through the TPM, wherein the security information includes system risk information and software update time information;
[0118] Execution environment credibility determination module 203, configured to match the system key file metric value information collected by the terminal with ...
Embodiment 3
[0144] Based on the same inventive concept, the present application also provides a computer-readable storage medium 300, please refer to Figure 8 , on which a computer program 311 is stored, and the method in Embodiment 1 is implemented when the program is executed.
[0145] Since the computer-readable storage medium introduced in the third embodiment of the present invention is the computer-readable storage medium used in implementing the access control method based on roles and terminal credibility in the first embodiment of the present invention, it is implemented based on the present invention For the method introduced in Example 1, those skilled in the art can understand the specific structure and deformation of the computer-readable storage medium, so details are not repeated here. All computer-readable storage media used in the method of Embodiment 1 of the present invention belong to the scope of protection of the present invention.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com