Privacy information leakage prevention method and device as well as terminal
A technology of private information and private data, which is applied in the field of preventing privacy information leakage, can solve the problems of not being able to adapt to changes in the application security situation, security policies are not flexible enough, etc., and achieve the effect of stability and universal applicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
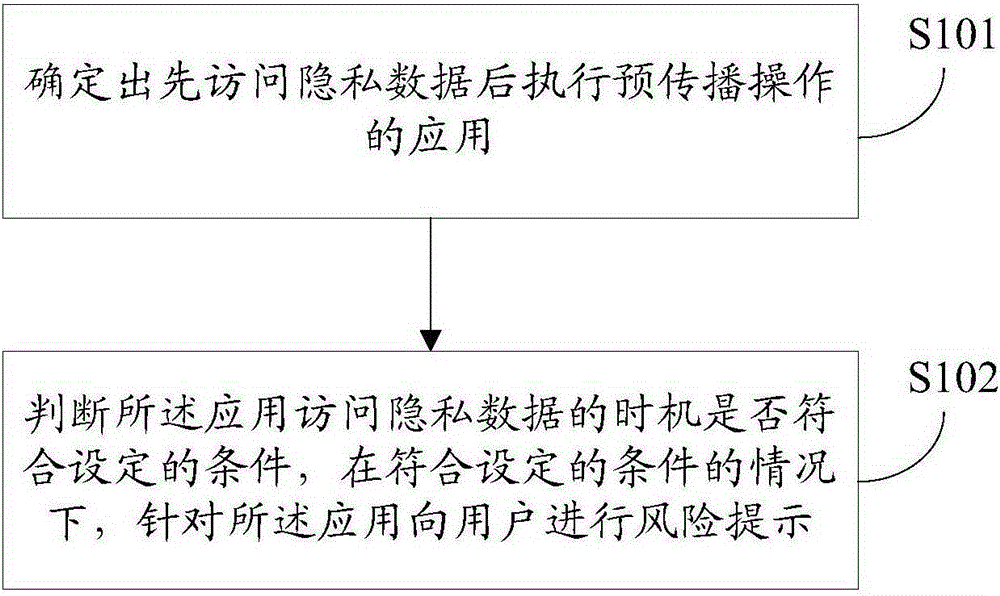
[0042] In the first embodiment of the present invention, a method for preventing leakage of private information, such as figure 1 shown, including the following specific steps:
[0043] Step S101, determining the application that first accesses the private data and then performs the pre-propagation operation;
[0044] Specifically, determine the applications that first access private data and then perform pre-propagation operations, including:
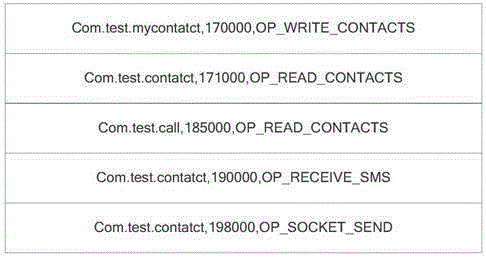
[0045] According to the operation information recorded by the application behavior control service in the operating system for each application, determine the application that first accesses the private data and then performs the pre-propagation operation; the recorded operation information includes: application name, operation type and time when the operation is performed, in,
[0046] The operation type is used to determine whether the application performs access to private data and pre-propagation operations;
[0047] The time wh...
no. 2 example
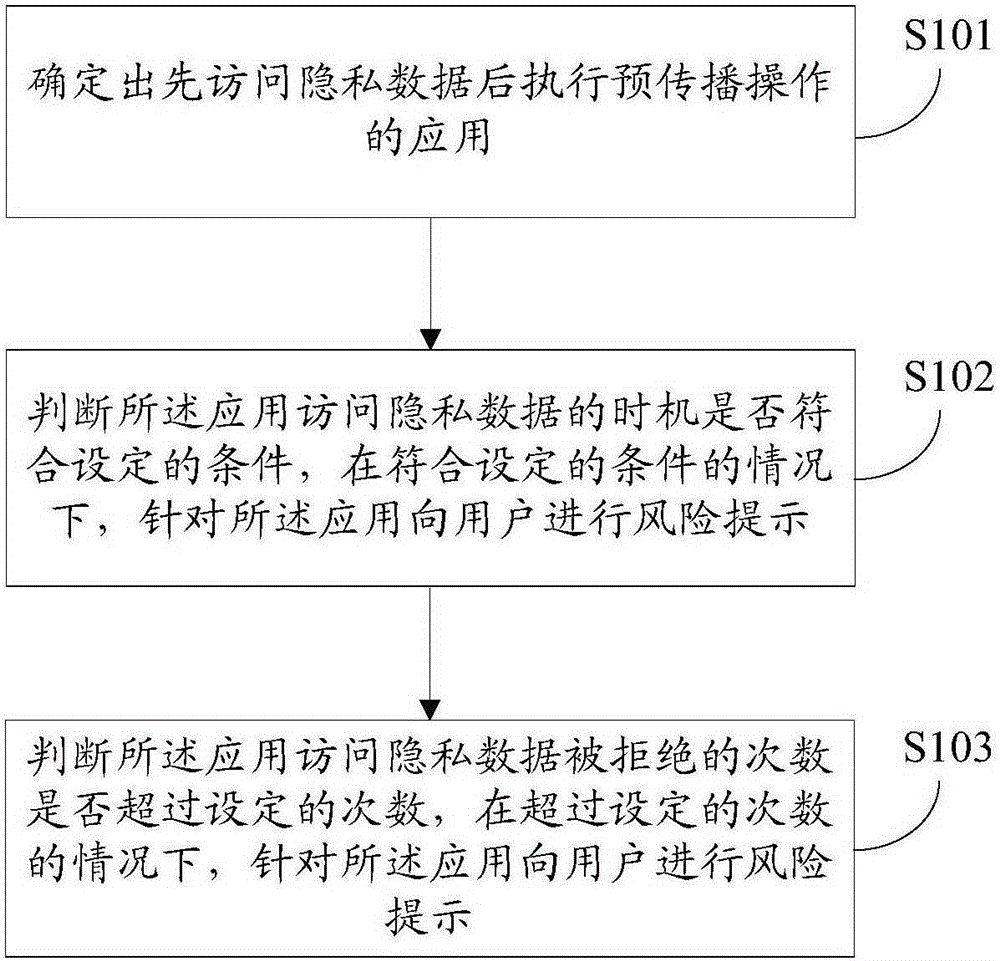
[0057] The second embodiment of the present invention is a method for preventing privacy information leakage. The method in this embodiment is substantially the same as that in the first embodiment, the difference is that in the method in this embodiment, the recorded operation information, Also includes: the last time the app was denied an action;
[0058] Such as figure 2 As shown, the method for preventing privacy information leakage also includes:
[0059] Step S103 , judging whether the number of times the application is rejected for accessing the private data exceeds a set number, and if the number exceeds the set number, a risk prompt is given to the user for the application.
[0060] It should be noted that, in this embodiment, step S103 and step S102 are judged based on different aspects, and there is no strict sequence of execution.
no. 3 example
[0061] The third embodiment of the present invention corresponds to the first embodiment. This embodiment introduces a device for preventing leakage of private information, such as image 3 shown, including the following components:
[0062] 1) A determining module 301, configured to determine an application that first accesses private data and then performs a pre-propagation operation;
[0063] Specifically, the determination module 301 is used for:
[0064] According to the operation information recorded by the application behavior control service in the operating system for each application, determine the application that first accesses the private data and then performs the pre-propagation operation; the recorded operation information includes: application name, operation type and time when the operation is performed, in,
[0065] The operation type is used to determine whether the application performs access to private data and pre-propagation operations;
[0066] The ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com