An information identification method, device and system
A technology for information identification and communication information, applied in the field of communication, can solve problems such as failure to achieve interception, user property loss, user terminal virus Trojan intrusion, etc., and achieve the effect of improving security and interception effect.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0030] This embodiment will be described from the perspective of an information identification device. The information identification device may specifically be integrated in a terminal, such as a receiving terminal. The terminal may include a mobile phone, a tablet computer, a notebook computer, or a personal computer (PC, Personal Computer), etc. equipment.
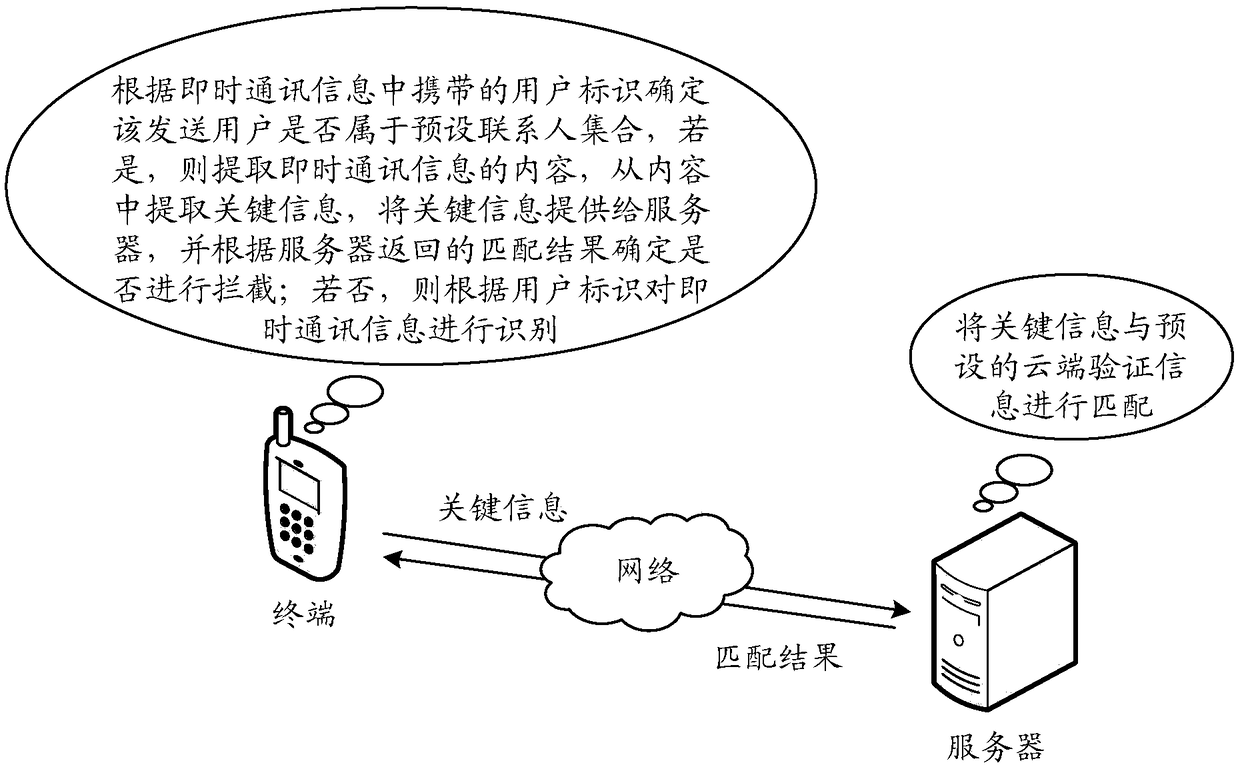
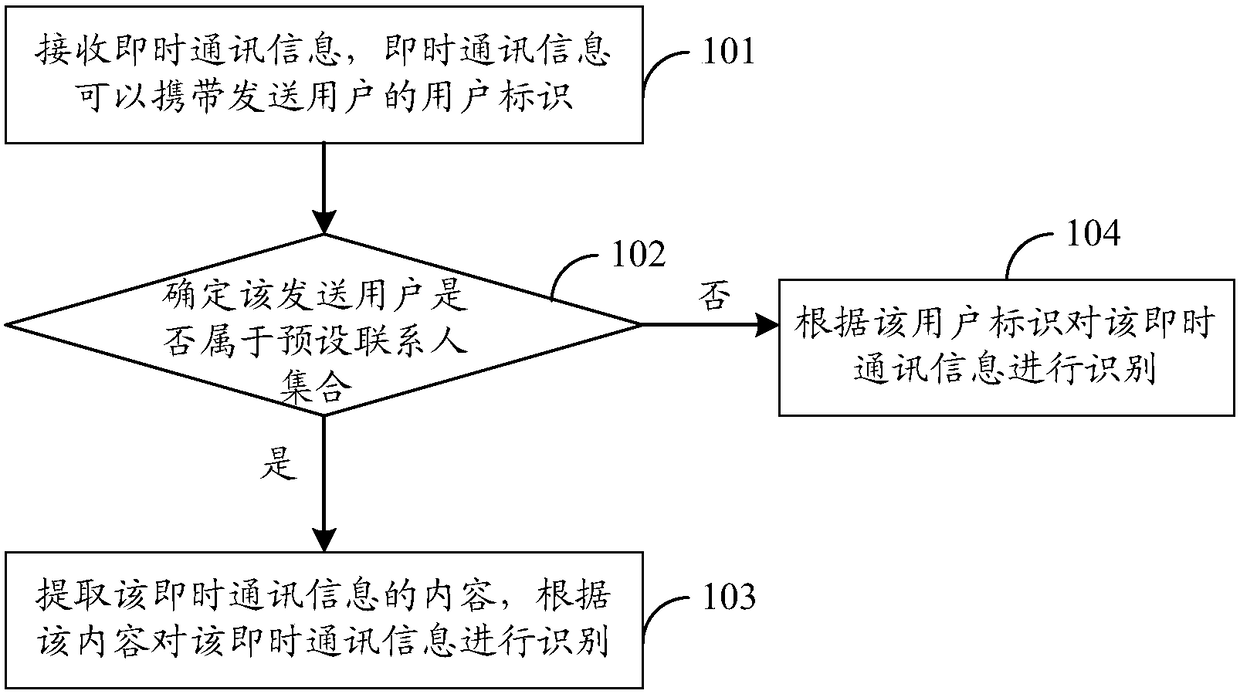
[0031] An information identification method, comprising: receiving instant messaging information, the instant messaging information carries the user identifier of the sending user; determining whether the sending user belongs to a preset contact set according to the user identifier; if so, extracting the content of the instant messaging information , identify the instant messaging information according to the content; if not, identify the instant messaging information according to the user ID.
[0032] Such as Figure 1b As shown, the specific process of the information identification method can be as follows:
[0033...
Embodiment 2
[0062] According to the method described in Embodiment 1, an example will be given below for further detailed description.
[0063] In this embodiment, it will be described by taking that the information identification device is integrated in the terminal A and the instant messaging information is a short message as an example.
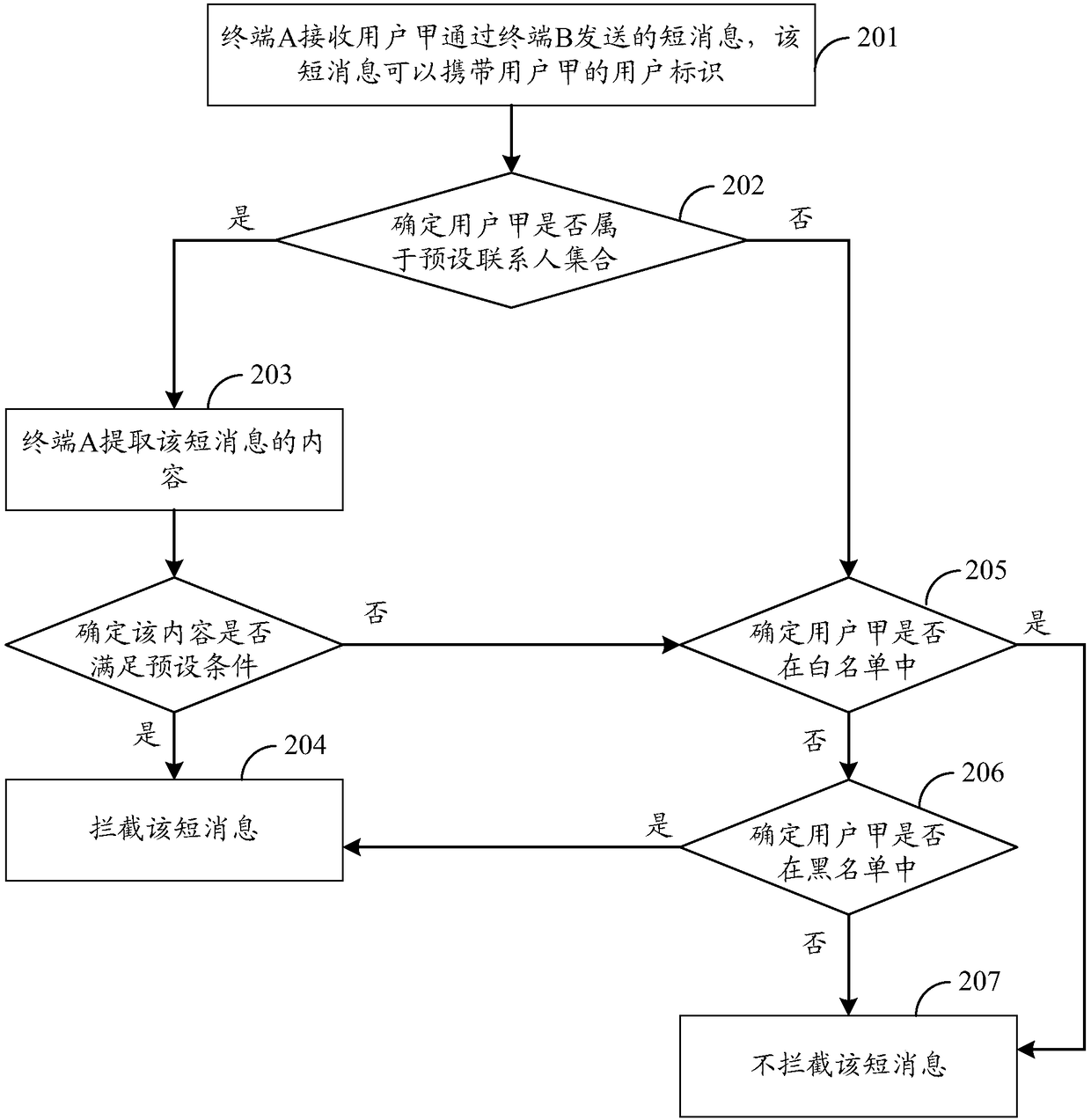
[0064] Such as figure 2 As shown, an information identification method, the specific process can be as follows:
[0065] 201. Terminal A receives a short message sent by user A through terminal B, where the short message may carry information such as user A's user ID.
[0066] The user identifier may include a terminal identifier, such as a SIM card number (such as a mobile phone number) or an IMEI code, or the user identifier may also include information such as a user name, a user mailbox, and / or a user's instant messaging number.
[0067] 202. Terminal A determines whether user A belongs to the preset contact set according to the user identifier...
Embodiment 3
[0093] In order to better implement the above method, the embodiment of the present invention also provides an information identification device, such as Figure 3a As shown, the information identification device includes a receiving unit 301, a determination unit 302, a first identification unit 303 and a second identification unit 304, as follows:
[0094] (1) receiving unit 301;
[0095] The receiving unit 301 is configured to receive instant messaging information.
[0096] For example, the receiving unit 301 may be specifically configured to receive instant messaging information sent by the sending terminal, where the instant messaging information may carry information such as the user ID of the sending user.
[0097] Wherein, the instant messaging information may include information such as short messages, multimedia messages, and communication messages in various instant messaging applications; the user identifier may include a terminal identifier, such as SIM or termin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com