A Privacy Preserving Method for Publishing Transactional Data Streams
A privacy protection and data flow technology, applied in the field of data security, can solve the problem that privacy protection technology cannot be directly applied
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
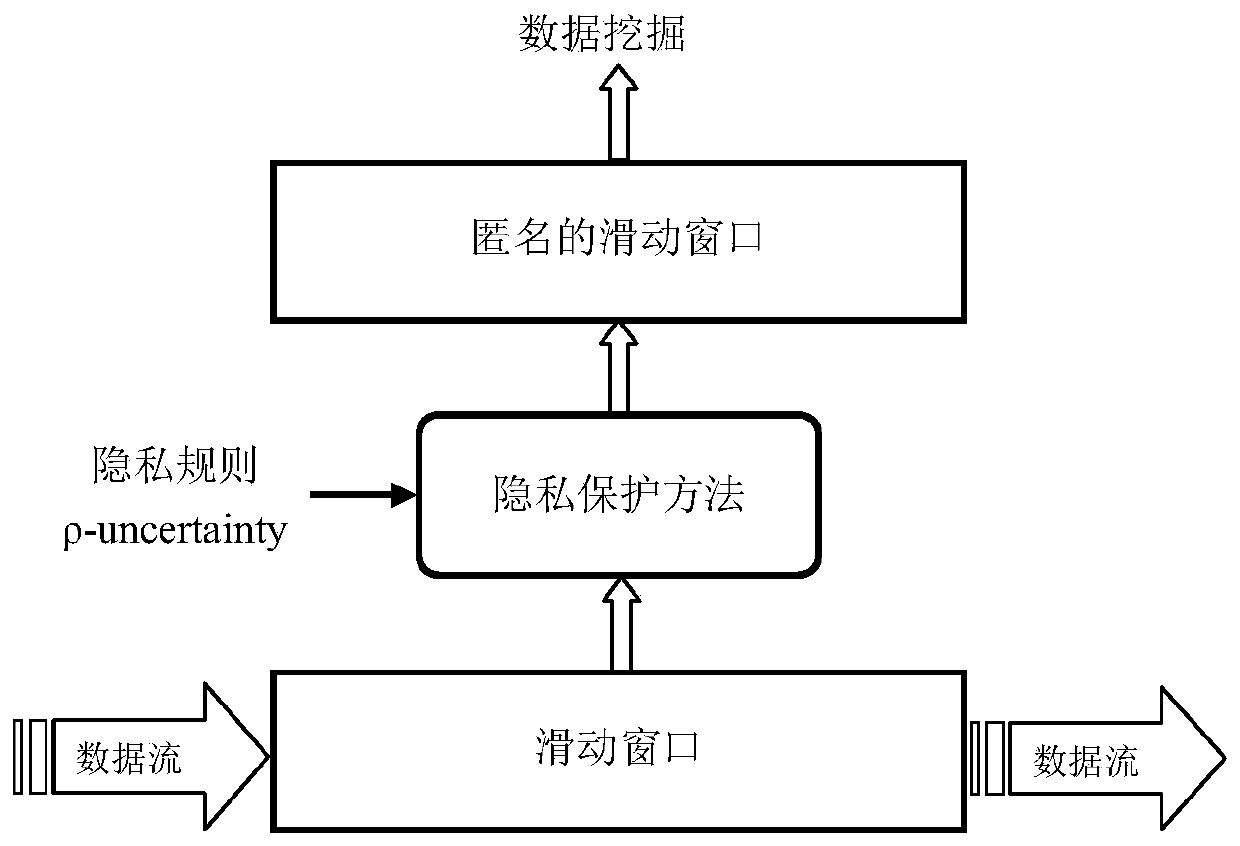
[0031] The privacy protection method published by transactional data flow, its application environment is as follows figure 1 As shown, the sliding window data is anonymized to satisfy ρ-uncertainty and released for use by data miners.
[0032] The process of a privacy protection method published by a transactional data flow is as follows:
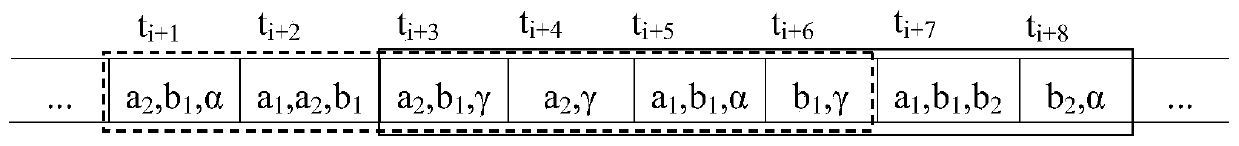
[0033] Step 1: In order to facilitate the calculation of support and confidence, the data of the initial sliding window is converted into a cover set, that is, for cover(item) is a collection of transactions containing items, and uses the static anonymous method proposed by Jianneng Cao et al. to anonymize it to satisfy ρ-uncertainty and publish it.
[0034] Step 2: Dynamically anonymize the sliding window, establish the affected sensitive association rule tree ASRT (Affected Sensitive Rules Trie) according to the deleted and added transactions, and use the payoff tree to suppress the project. During the process:
[0035] First, initial...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com