Application software security vulnerability detection method and system
An application software and vulnerability detection technology, applied in the field of information security, can solve problems such as affecting the efficiency of security vulnerability detection, and achieve the effects of avoiding false positives and false negatives, reducing workload and achieving accurate results.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
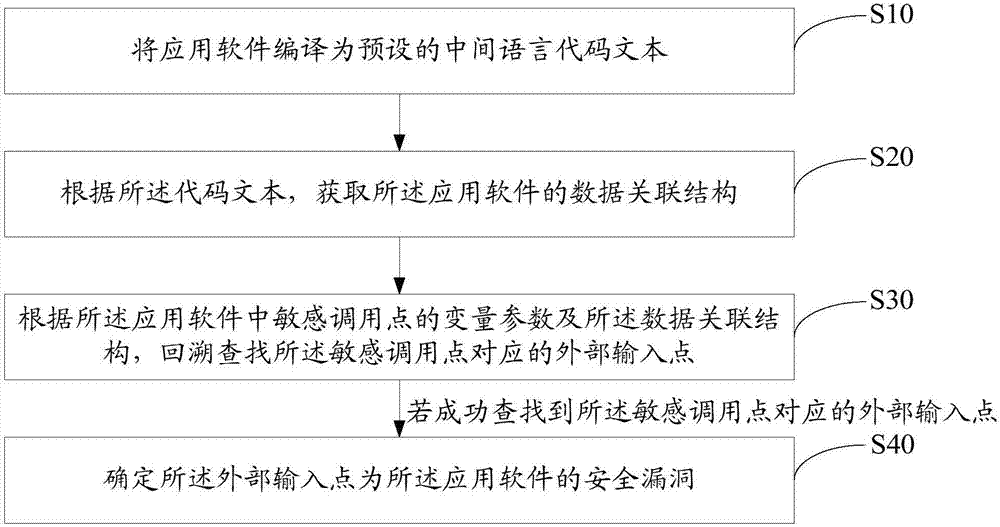
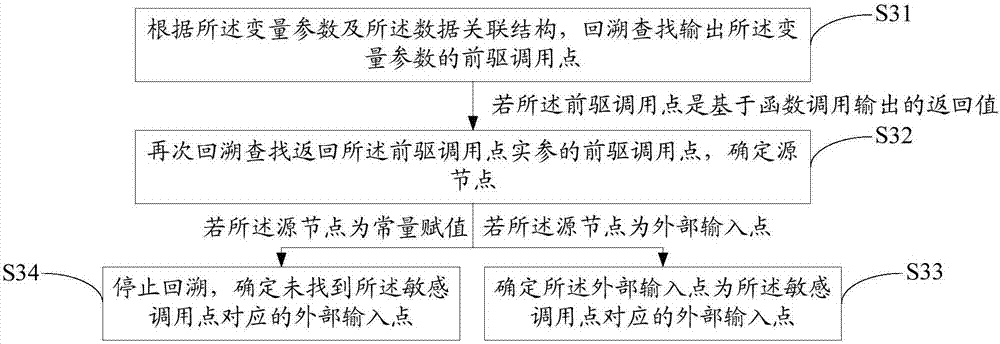
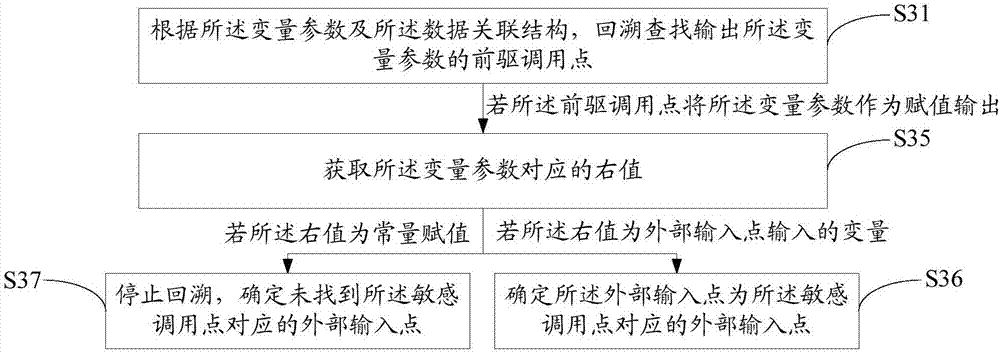
[0046] refer to figure 1 The first embodiment of the application software security vulnerability detection method of the present invention provides an application software security vulnerability detection method, and the application software security vulnerability detection method includes:
[0047] Step S10, compiling the application software into a preset intermediate language code text.
[0048] In the present invention, by compiling the application software to be detected into an intermediate language text, one statement of the obtained application software code contains one semantic meaning, which will not cause ambiguity, and the language strength is relatively thinner than high-level languages, and thicker than low-level languages, which is suitable for static applications Software security vulnerability detec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com