An integrated circuit and method for detection of malicious code in a first level instruction cache
A high-speed cache, integrated circuit technology, applied in the field of malicious code
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The word "exemplary" is used herein to mean "serving as an example, instance, or illustration." Any embodiment described herein as "exemplary" is not necessarily to be construed as preferred or advantageous over other embodiments.
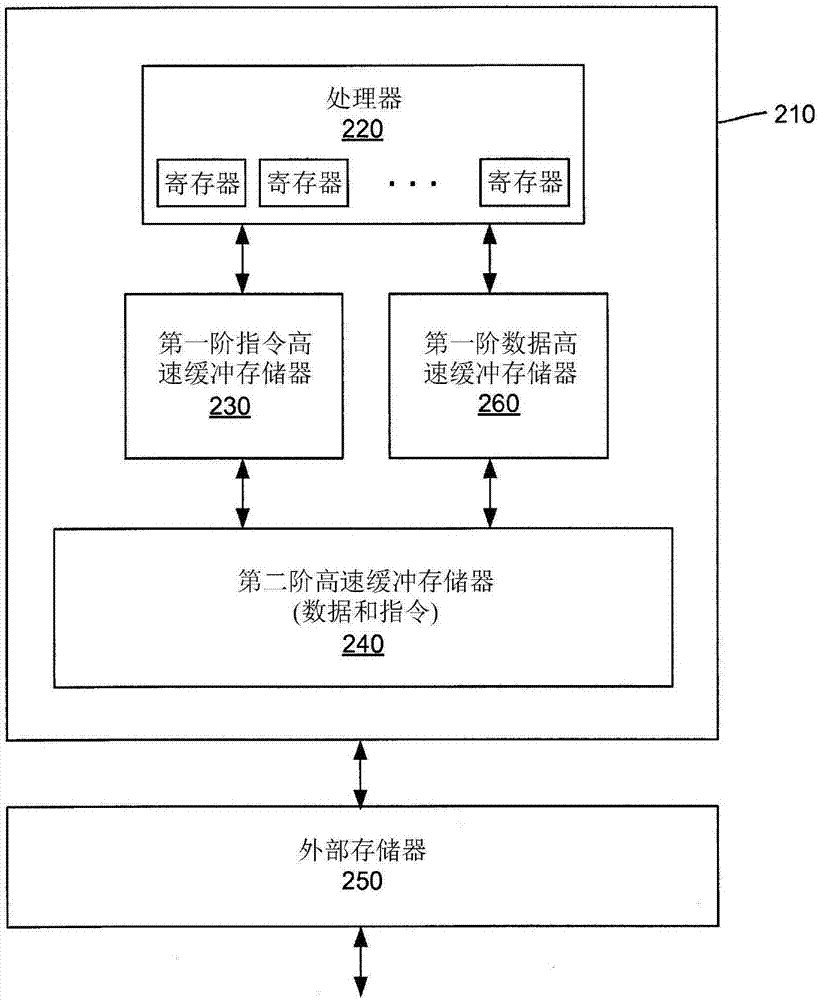
[0017] see figure 2 and 3 , an aspect of the invention may reside in an integrated circuit 210 comprising: a processor 220, a first-level instruction cache 230 having a first storage capacity, and a second-level instruction cache 230 having a second storage capacity greater than the first storage capacity Buffer memory 240 . A first level instruction cache is coupled between the processor and the second level cache and is configured to store a subset of the instructions stored in the second level cache. The second level cache is coupled between the first level instruction cache and the external memory 250 and is configured to store a subset of the data and instructions stored in the external memory. The processor is configured to execut...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap