A data security storage method and device based on alliance block chain
A data security storage and data storage technology, which is applied in the field of data security storage based on the alliance blockchain, can solve the problems of malicious tampering in the data center, single-point failure of the master node, opaque data sharing, etc., so that it is not easy to lose and improve security , Improve the effect of sharing transparency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
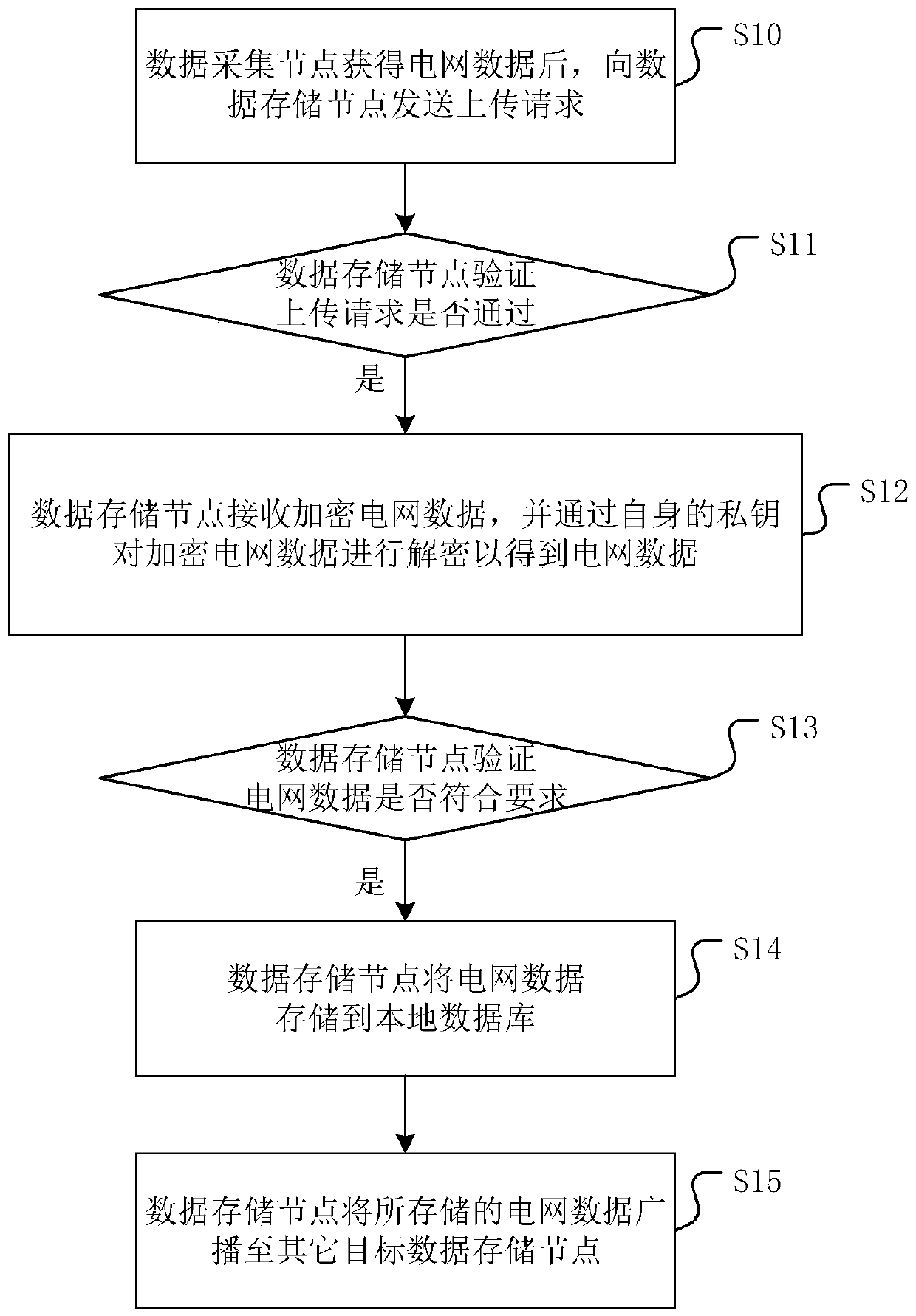
[0037] figure 1 It is a flow chart of a data security storage method based on consortium blockchain provided by an embodiment of the present invention. Please refer to figure 1 , the specific steps of the data security storage method based on the alliance block chain include:
[0038] Step S10: After the data acquisition node obtains the grid data, it sends an upload request to the data storage node.
[0039] In this step, the data acquisition node is used to obtain grid data generated during grid operation, and the data needs to be stored in a data storage node for subsequent viewing of grid data by users. It can be understood that the data acquisition node needs to first send an upload request to the data storage node to request the data storage node to verify itself and agree to receive the grid data acquired by itself.
[0040] Step S11: the data storage node verifies whether the upload request is passed, and if so, executes step S12.
[0041] It can be understood that...
Embodiment 2
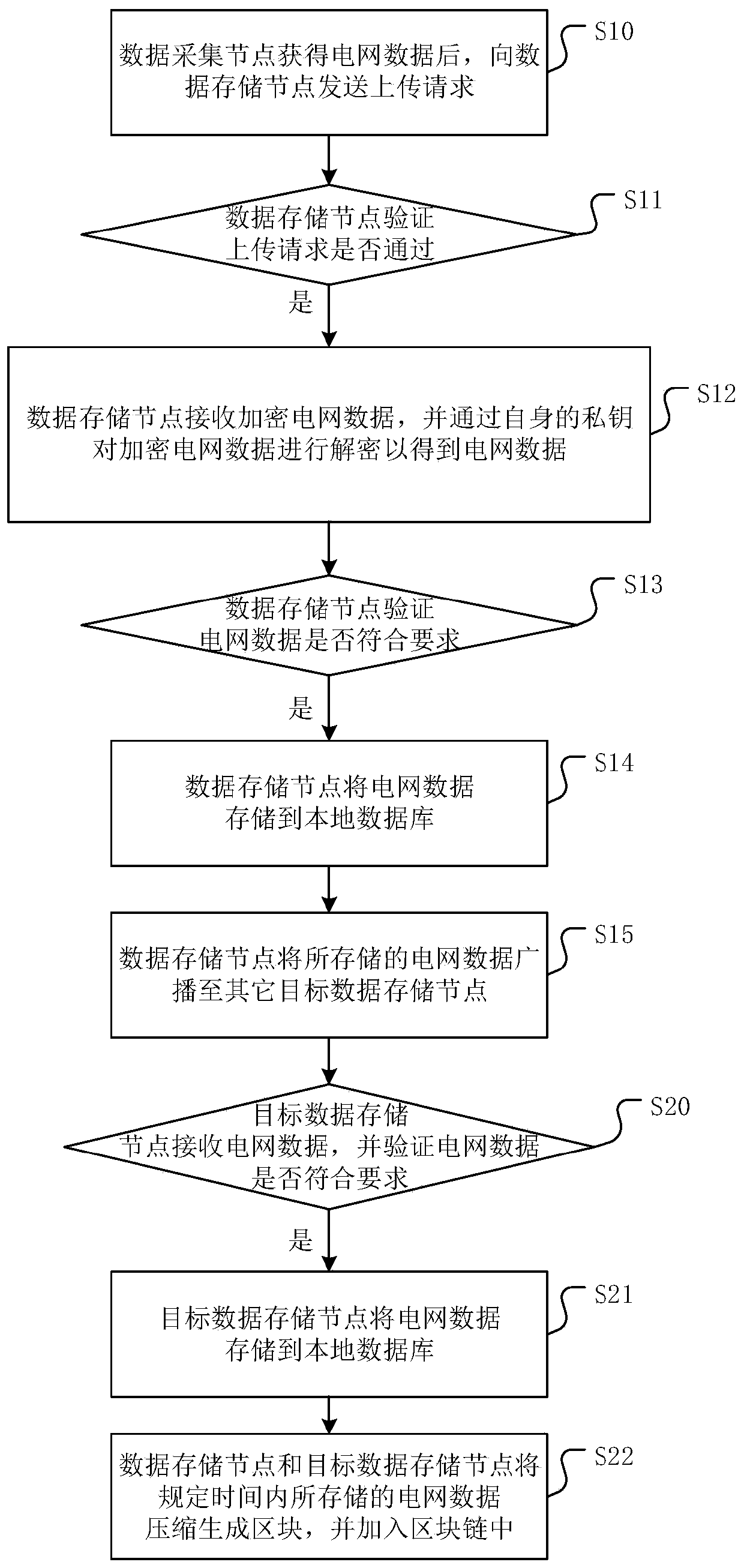
[0056] figure 2 It is a flow chart of another data security storage method based on consortium blockchain provided by the embodiment of the present invention. figure 2 In steps S10-S15 and figure 1 Same, no more details here.
[0057] Such as figure 2 As shown, as a preferred embodiment, it also includes:
[0058] Step S20: The target data storage node receives the grid data, and verifies whether the grid data meets the requirements, and if so, executes step S21.
[0059] The target data storage node can specifically verify whether the grid data is safe and effective. The main purpose is to ensure that all the grid data stored on the target data storage node are meaningful data that can correctly reflect the real situation of the grid system.
[0060] Step S21: The target data storage node stores the grid data in a local database.
[0061] It is understandable that the target data storage node stores the grid data of the data storage node in its own relatively safe and...
Embodiment 3
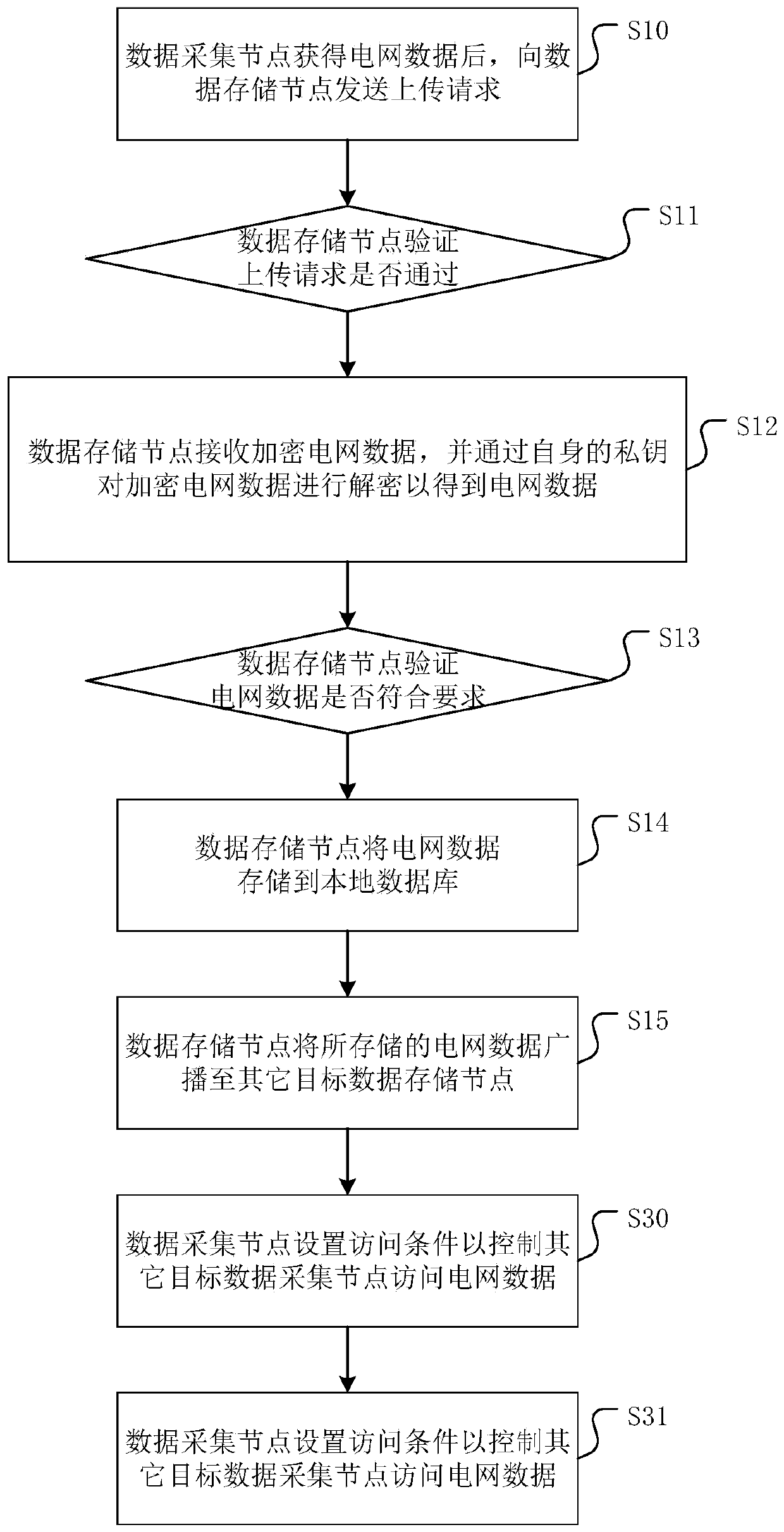
[0066] Corresponding to the data collection node storing the power grid data in the data storage node, this embodiment further provides a method for the target data collection node to access the power grid data of the data collection node. For specific steps, please refer to image 3 .
[0067] image 3 It is a flow chart of a power grid data access method based on consortium blockchain provided by an embodiment of the present invention. Such as image 3 As shown, on the basis of the foregoing embodiments, it also includes:
[0068] Step S30: the data acquisition node sets access conditions to control other target data acquisition nodes to access the grid data.
[0069] In this step, the access conditions may include: the target data collection node is within the range of allowed access nodes set by the data collection node, the grid data accessed by the target data collection node is within the grid data sharing range set by the data collection node, and the target data T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com