Real-time detection of Android malware using a random forest classifier
A malware and random forest technology, applied in the field of communications, can solve the problems of reducing the success rate of Android malicious detection, ineffective detection, and reducing the accuracy of malware detection, and achieve the effect of good detection accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
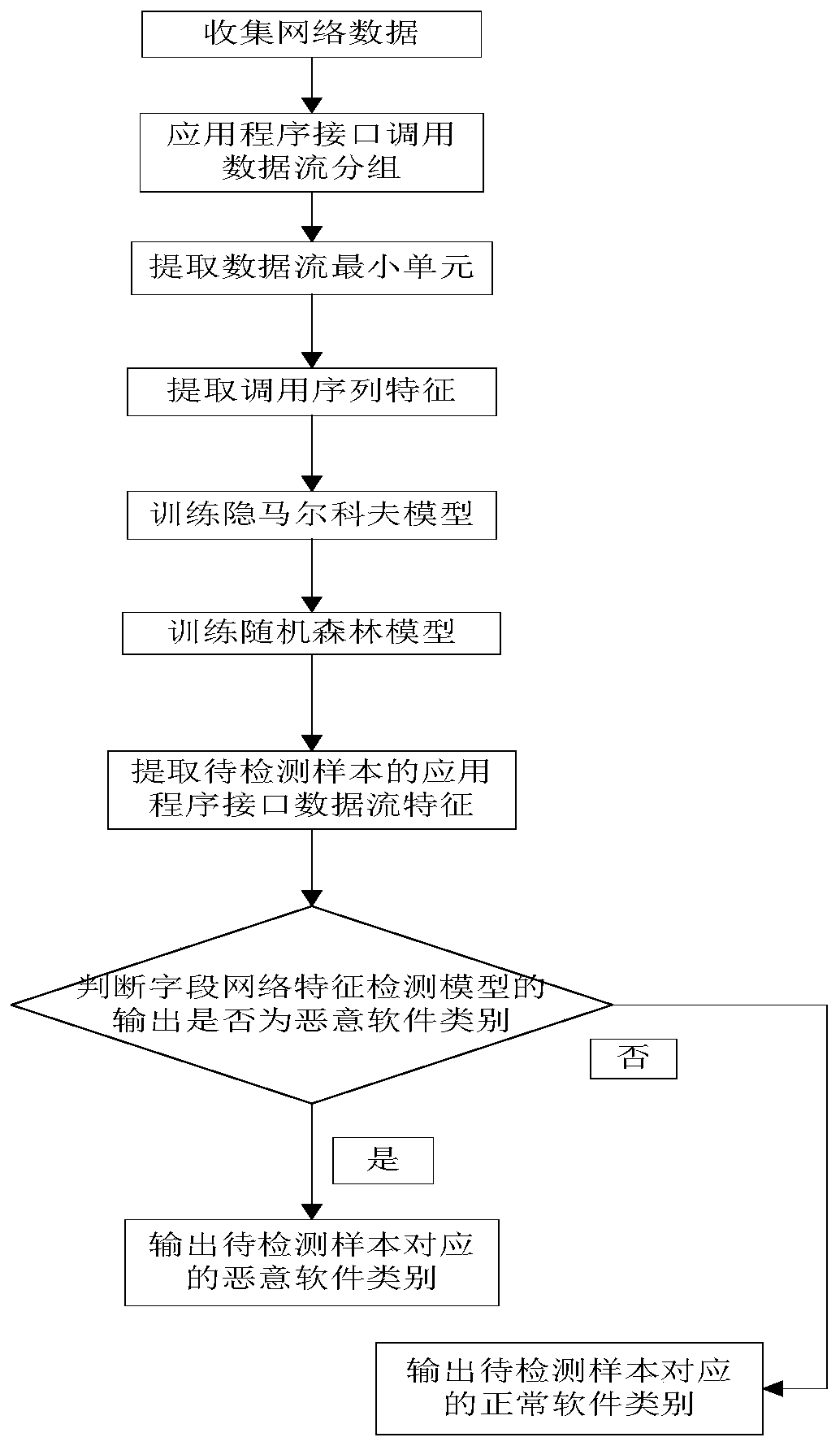
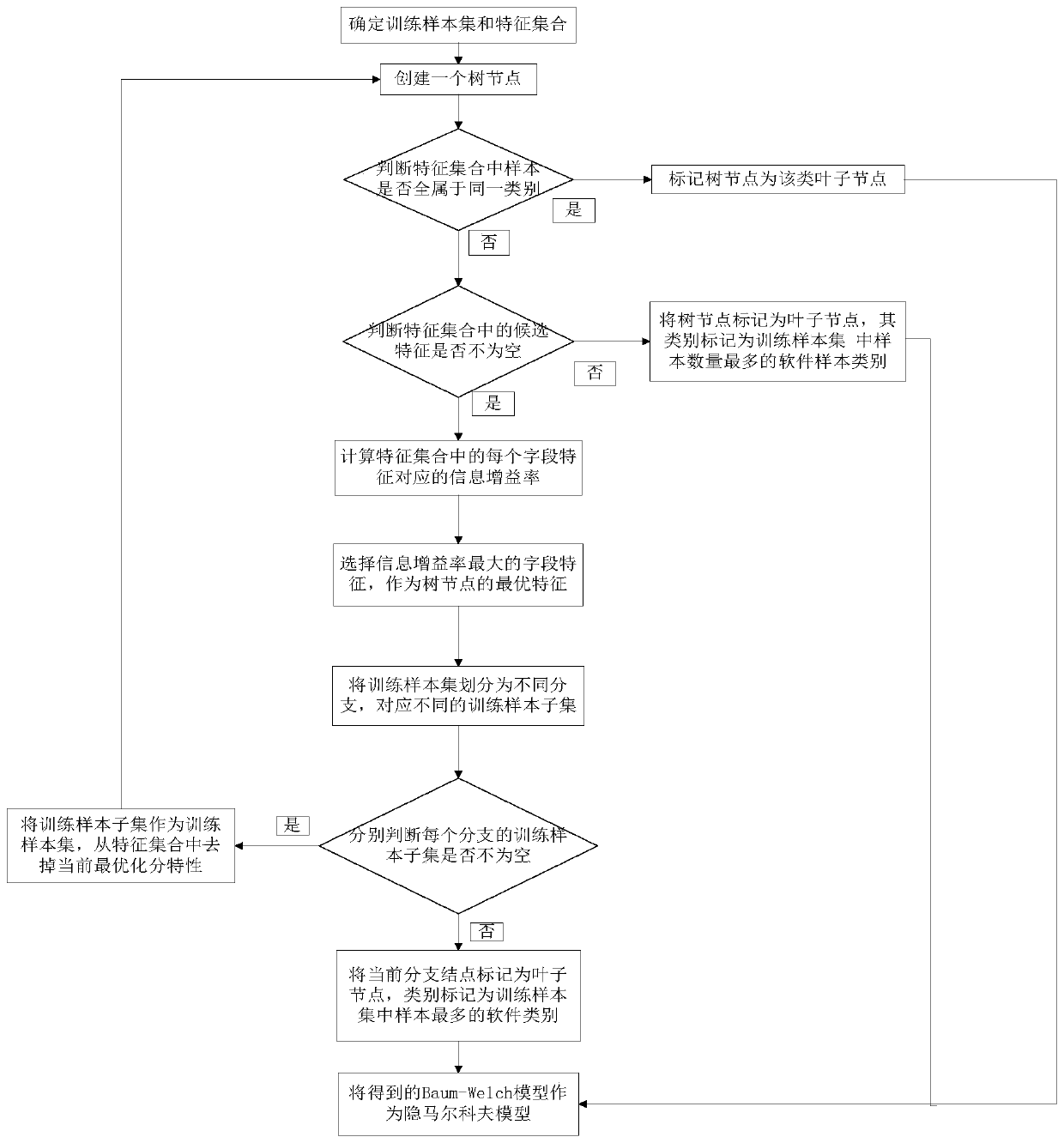
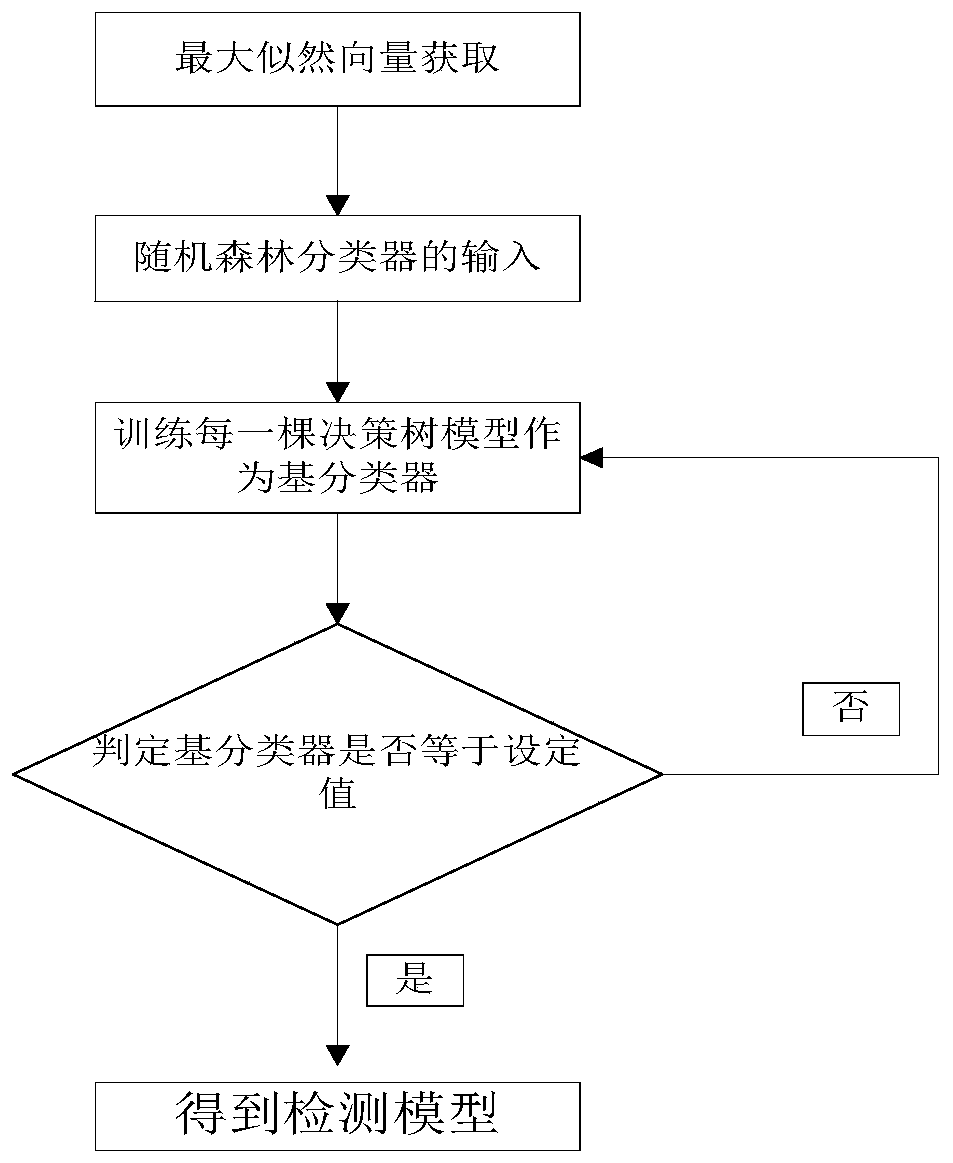
[0041] The present invention proposes a method for real-time detection of Android malware using a random forest classifier, the method is based on a hidden Markov model, and the similarity between the application program and each category can be judged by the inherent similarity; on this basis The random forest model, which is more suitable for dealing with classification problems, is introduced to reflect the differences of different categories and similar behaviors to a certain extent, that is, the random forest classifier model is used to identify similar behavior sequences.
[0042] refer to figure 1 , the double security authentication process of the present invention is as follows:
[0043] Step 1, collect network data.
[0044] Use the data packet capture tool to collect the runtime API call data flow generated by normal software samples and malware samples respectively, and use the collected runtime API call data flow as the initial data set for training the malware d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com