Private key protection method, system and device based on key updating
A key update and private key technology, applied in the field of private key protection based on key update, can solve the problems of high risk level of digital certificate private key theft, difficulty in ensuring digital signature, poor compatibility, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
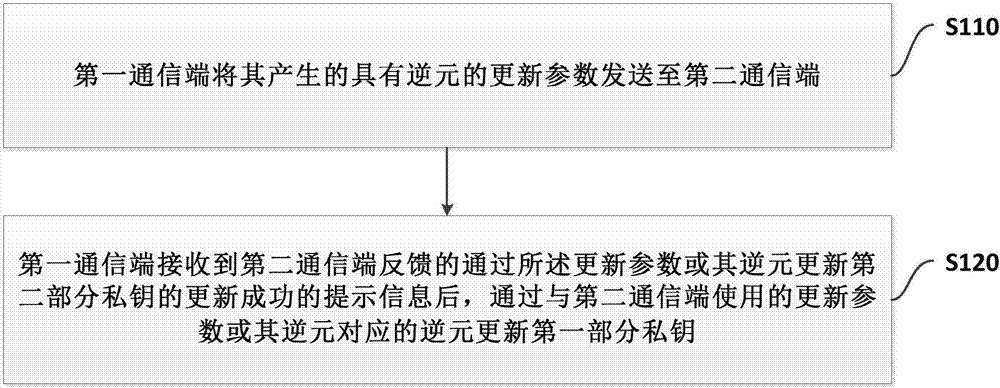
[0113] refer to figure 1 , figure 1 A flow chart of an embodiment of a private key protection method based on key update provided by the present invention is shown. Wherein, the first communication terminal stores the first part of the private key, the second communication terminal stores the second part of the private key, and the first part of the private key and the second part of the private key are cooperatively operated to generate an electronic signature. This embodiment is the first communication terminal side, The method includes: step S110 to step S120.
[0114] In step S110, the first communication terminal sends the generated update parameters with inverse elements to the second communication terminal.
[0115] In step S120, after the first communication terminal receives the prompt message that the update of the second part of the private key is successfully updated through the update parameter or its inverse element fed back by the second communication terminal...
Embodiment 2
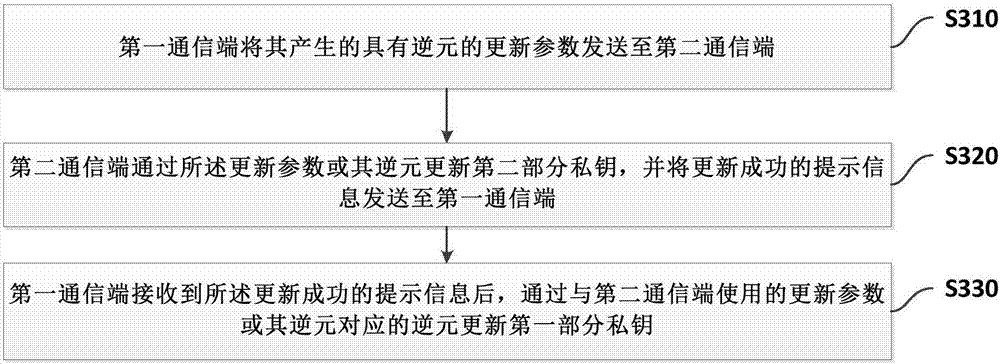
[0126] refer to figure 2 , figure 2 A flow chart of an embodiment of a private key protection method based on key update provided by the present invention is shown. Wherein, the first communication terminal stores the first part of the private key, the second communication terminal stores the second part of the private key, and the first part of the private key and the second part of the private key are cooperatively operated to generate an electronic signature. This embodiment is the second communication terminal side, The method includes step S210.
[0127] In step S210, the second communication terminal receives the update parameter with the inverse element generated by the first communication terminal sent by the first communication terminal, updates the second part of the private key through the update parameter or its inverse element, and updates the successfully updated The prompt information is sent to the first communication terminal, so that after receiving the p...
Embodiment 3
[0198] refer to Figure 4 , Figure 4 It shows a private key protection system 300 based on key update provided by the present invention, wherein, the first communication terminal stores the first part of the private key, the second communication terminal stores the second part of the private key, and the first part of the private key and the second Electronic signatures are generated after part of the private key collaborative operation, including:
[0199] The first communication terminal 31 is used to send the update parameter with the inverse element generated by it to the second communication terminal; after receiving the update parameter or its inverse element fed back by the second communication terminal to update the second part of the private key After the prompt message of successful update, the first part of the private key is updated with the inverse element corresponding to the update parameter used by the second communication terminal or its inverse element.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com