Signature method based on sm2 algorithm
An algorithm, the technology of elliptic curve algorithm, is applied in the direction of public key of secure communication, digital transmission system, secure communication device, etc. It can solve the problems of lower computing efficiency, too large private key, and signature overflow, so as to improve processing efficiency, The effect of improving computing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
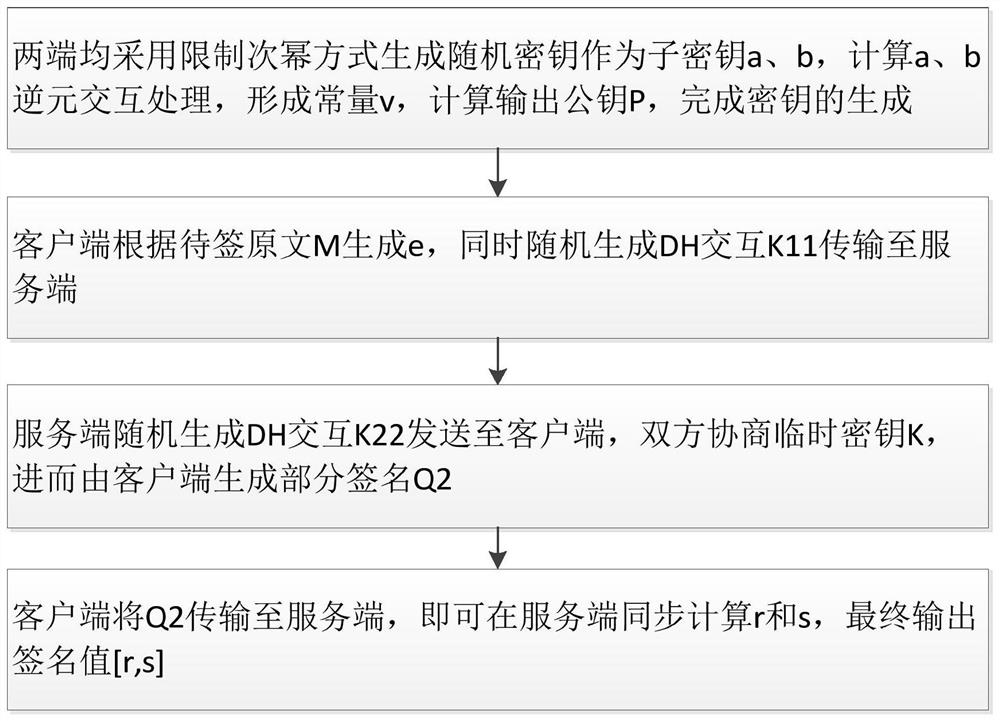
[0034] Such as figure 1 As shown, the general flow of this method is: S1. Both the client and the server use the restricted power method to generate random subkeys a and b, and calculate the inverse elements of a and b for interactive processing to form a constant v, and calculate and output the public key P . S2. The client generates e according to the original text M to be signed, and at the same time randomly generates DH interaction k11, and transmits e and k11 to the server. S3. The server randomly generates a DH interaction k22 and sends it to the client. The client and the server negotiate a temporary key k, and then the client generates a partial signature Q2. S4. The client transmits Q2 to the server, and the server calculates r and s synchronously, and finally outputs the signature value [r, s].
[0035] The specific flow of this method will be described in detail below: this method mainly includes two processes of key generation and signature calculation.
[0036...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com