Image encryption method based on memristive chaotic system, elementary cellular automata and compressed sensing
A cellular automaton and chaotic system technology, applied in image data processing, image data processing, instruments, etc., can solve problems such as tampering, low correlation of algorithm keys, and difficulty in resisting chosen plaintext attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
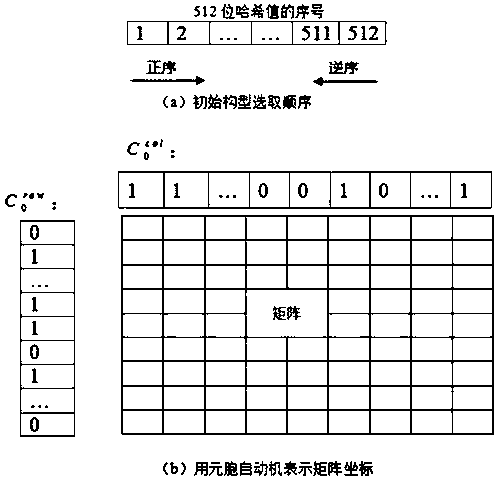
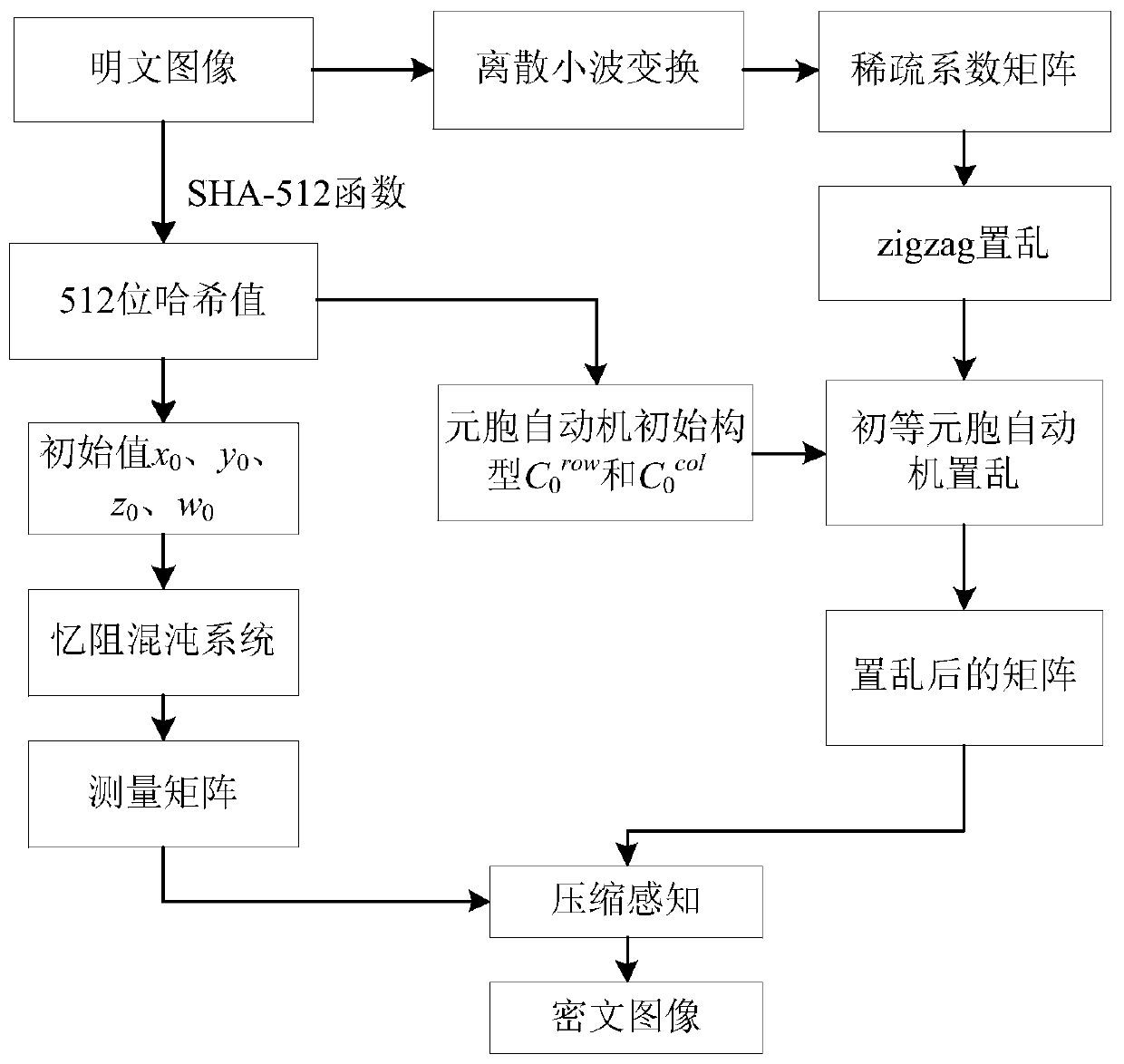
[0083] Embodiment 1, for the existing image encryption process is not highly correlated with the plaintext or the key space is not large enough, see figure 1 As shown, this embodiment provides an image encryption method based on the memristive chaotic system, elementary cellular automata and compressed sensing. The plaintext image uses the SHA-512 function to obtain the initial value of the memristive chaotic system and the initial structure of the cellular automata. type; the plaintext image is transformed by discrete wavelets to obtain a sparse coefficient matrix; the sparse coefficient matrix is scrambled by the zigzag scrambling method, and then the elementary cellular automata is used for the scrambling operation; the initial value of the memristive chaotic system is brought into the memory The chaotic system generates the measurement matrix, and compresses the scrambled matrix through the measurement matrix to obtain the final ciphertext image.
[0084] Using the image...
Embodiment 2
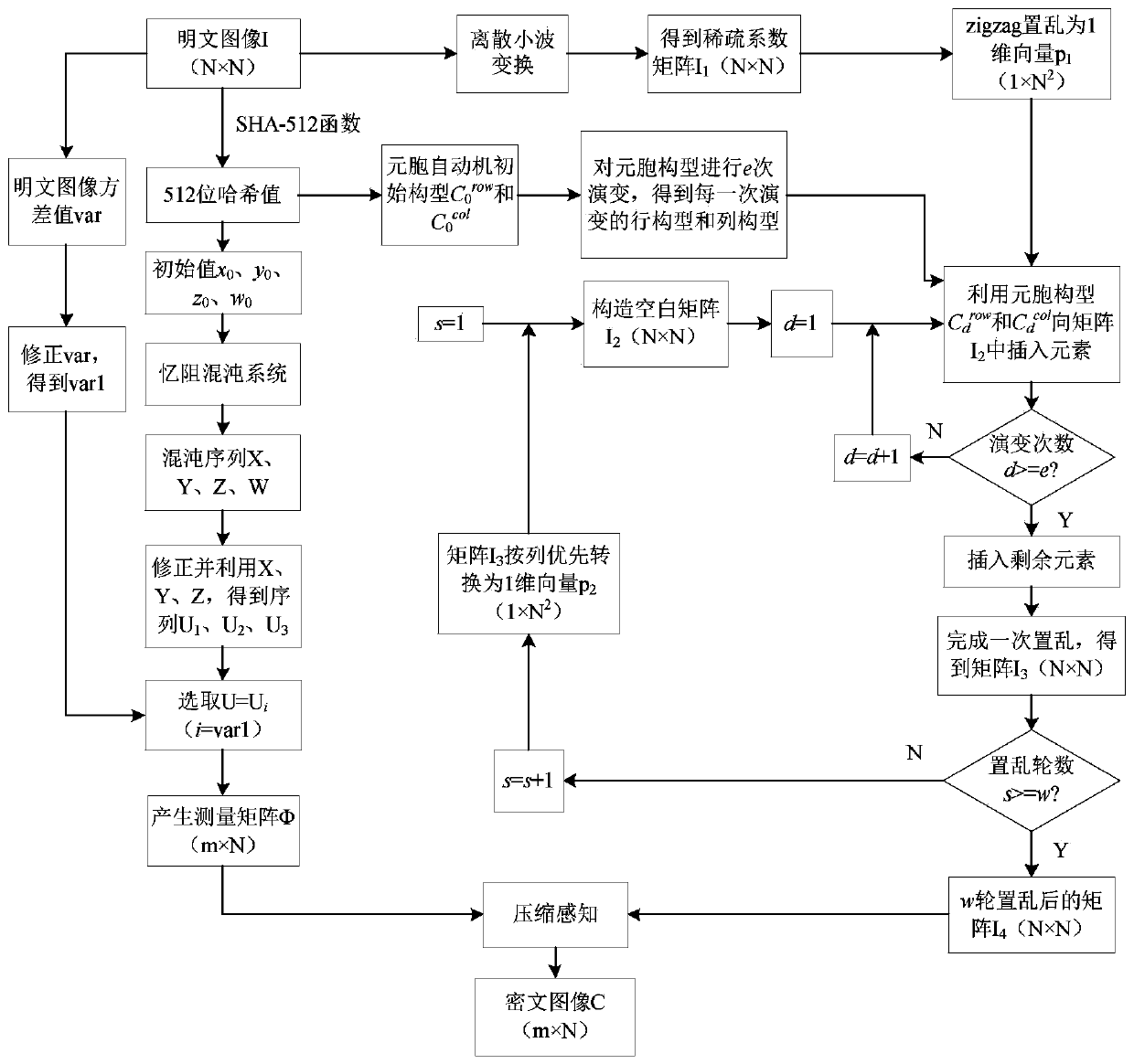
[0085] Embodiment two, see figure 2 As shown, an image encryption method based on memristive chaotic system, elementary cellular automata and compressed sensing is provided, and its implementation process specifically includes the following steps:
[0086] Step 1. Use the discrete wavelet transform DWT to transform the plaintext image I with a size of N×N to obtain a sparse coefficient matrix I with a size of N×N 1 .
[0087] Step 2. Use the SHA-512 function to calculate the plaintext image I, obtain a set of 512-bit hash values and use it as the image key Key, and then convert the 512-bit image key Key into 64 decimal numbers k 1 ,k 2 ,...,k 64 , to calculate the initial value x of the memristive chaotic system 0 、y 0 ,z 0 、w 0 ; Specifically calculate the initial value of the memristive chaotic system through the following steps:
[0088] Step 2.1, convert the 512-bit key Key into a group of 8 bits into 64 decimal numbers k 1 ,k 2 ,...,k 64 , and then use the f...
Embodiment 3
[0155] Embodiment three, see Figure 8-11 As shown, in this embodiment, the programming software used is Matlab R2016a, and the Lena grayscale image with a size of 512×512 is selected as the experimental object. The specific encryption process is as follows:
[0156] Step 1: Input the Lena grayscale image with the original size of 512×512, use I=imread('Lena.bmp') to read the image information, and use the discrete wavelet transform (DWT) to transform the image I to obtain a size of 512 ×512 sparse coefficient matrix I 1 .
[0157] Step 2: Use the SHA-512 function to calculate the plaintext image I, get a set of 512-bit hash values and use it as the image key Key, and then convert the 512-bit image key Key into 64 decimal numbers k 1 ,k 2 ,...,k 64 , to calculate the initial value of the memristive chaotic system. Specific steps are as follows:
[0158] 2.1) Use the SHA-512 function to calculate the plaintext image I, and obtain a set of 512-bit hash values (hexadeci...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com