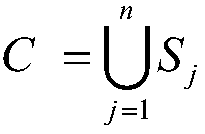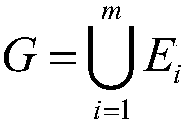Access method for controlling network service composition by means of ABAC model
A network service and service combination technology, which is applied in the field of access control of network services based on attribute access control model ABAC, can solve the problems of waste of network services, fine-grained control of network service visitors, and few types of object attributes, and achieves overcoming strategies. The waste of search time, the effect of reducing the influence of policy search time, and the effect of avoiding the influence of policy search time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
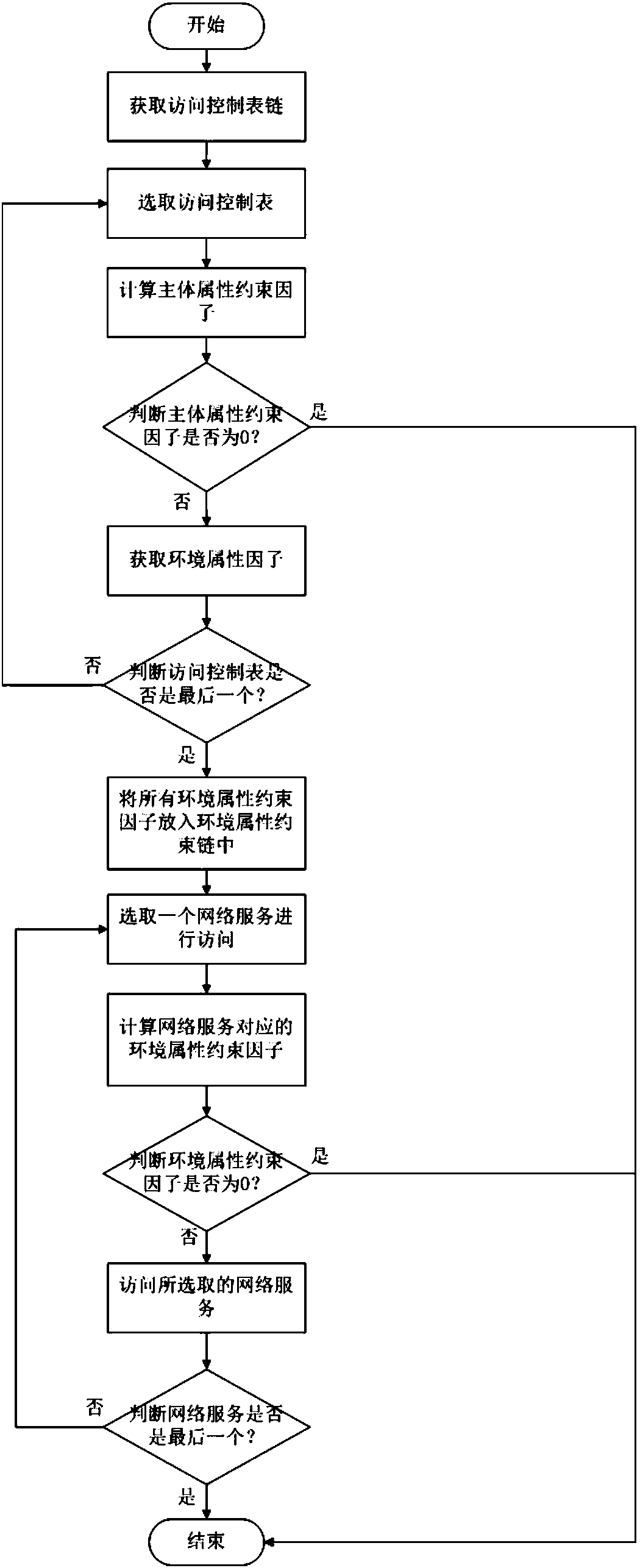
[0035] Attached below figure 1 The present invention is further described.
[0036] Step 1, obtain the access control list chain of the network service combination to be accessed.
[0037] From the ABAC policy library of the attribute-based access control model, the subject attribute constraints and environment attribute constraints in the attribute constraint definitions of all network services in the network service composition to be accessed are extracted.
[0038] Attribute constraints are defined as follows:
[0039] D=
[0040]
[0041]
[0042] Among them, D represents the attribute type expression, represents the attribute type, and represents {≤,≥,,=,! =A logical operator in the set}, this set can be user-defined logical operators, indicates the attribute value, F indicates the attribute constraint subform, x indicates the total number of attribute type expressions, D p Indicates the pth attribute type expression, T indicates the attribute constraint, the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com