Input authentication method
An input verification and user technology, which is applied in the field where the time interval of password input is the verification basis, and can solve problems such as insufficient security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] In order to describe the technical content, purpose and effect of the present invention in detail, the following examples are listed and described in detail with the accompanying drawings.
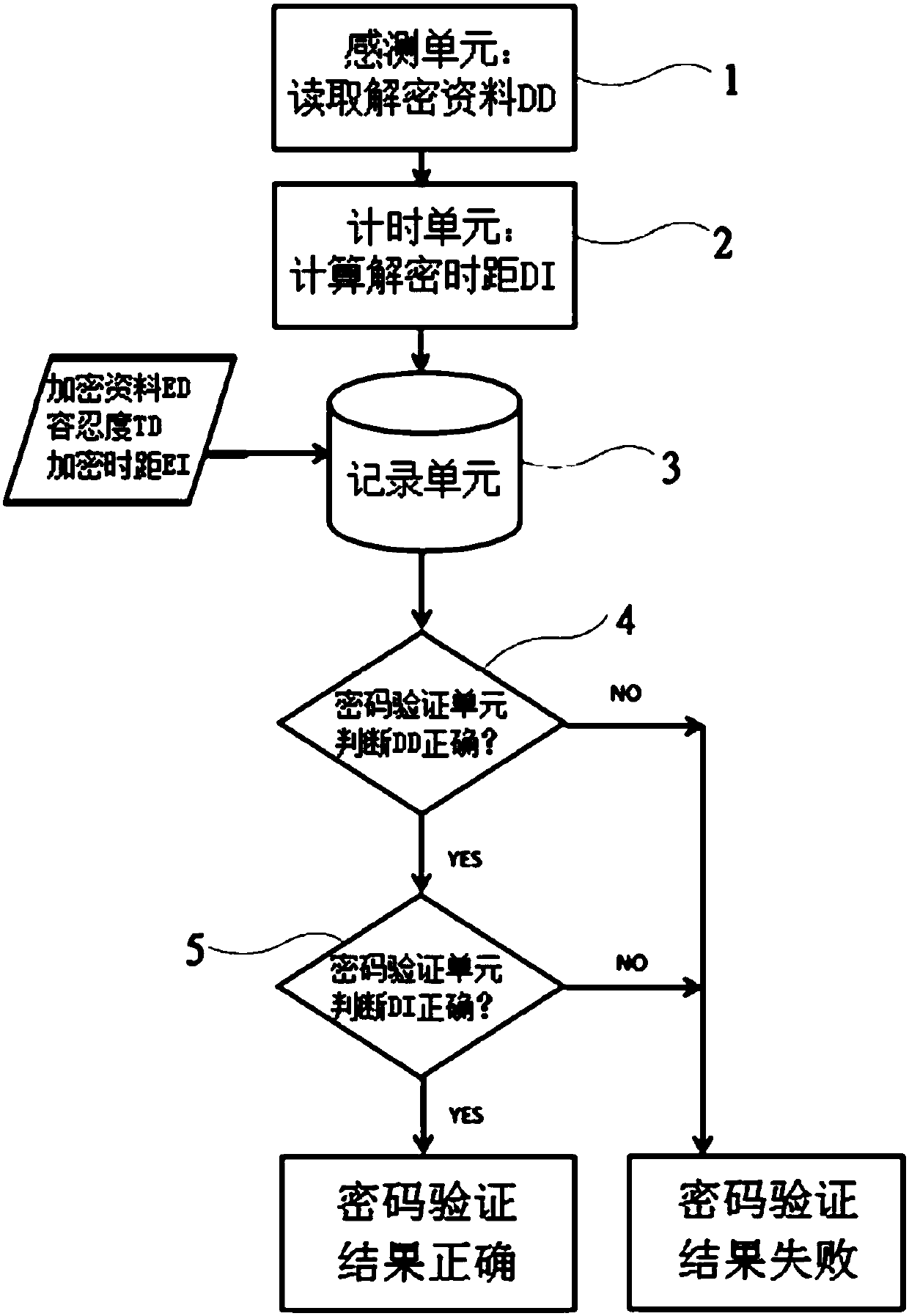
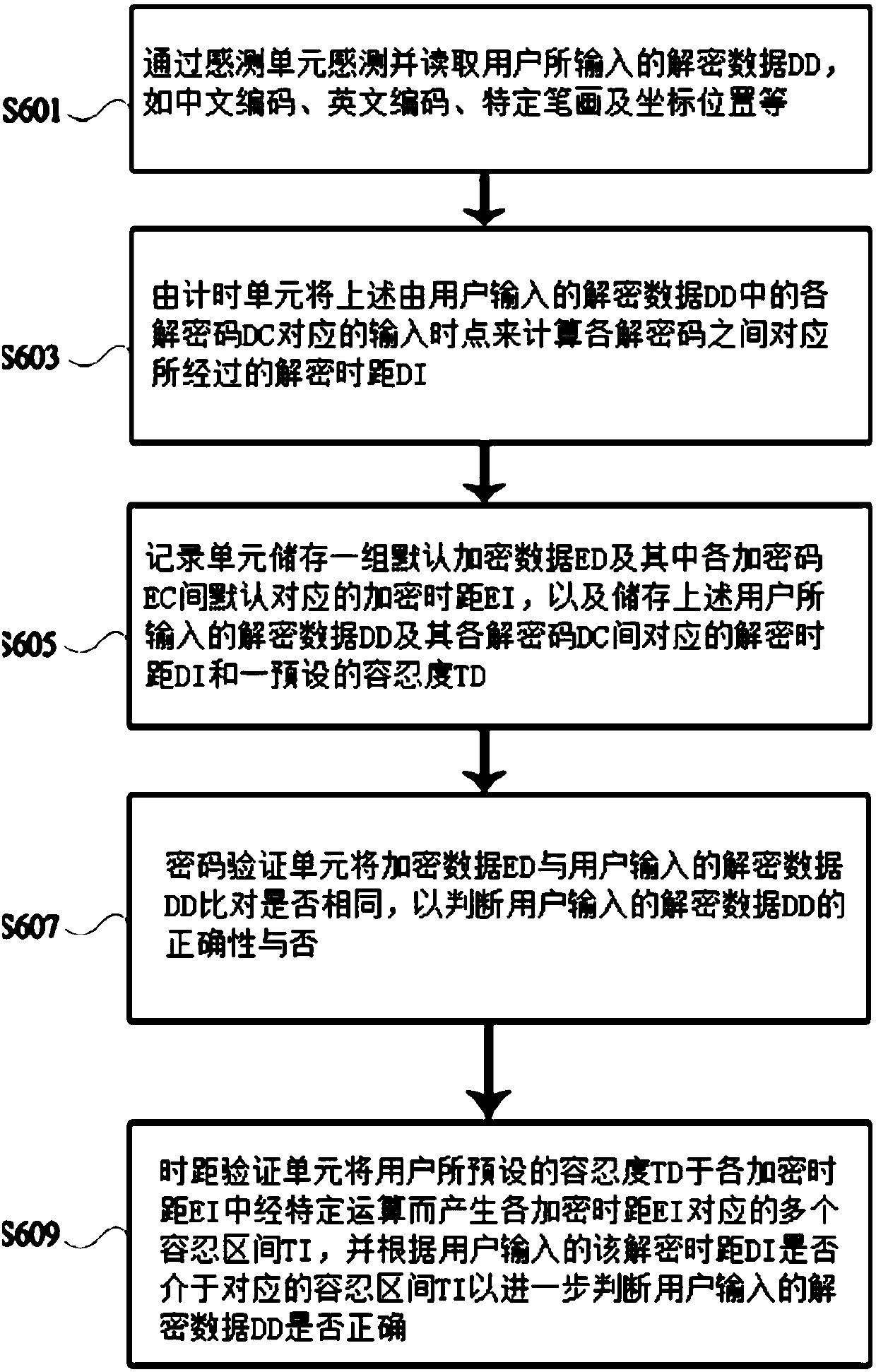
[0020] like figure 1 , figure 2 and image 3 as shown, figure 1 For the password verification flow chart, figure 2 For the password verification step, image 3 It is a schematic diagram of the tolerance interval for time distance verification, please also refer to figure 1 and figure 2 illustrate, figure 1 Each process in the corresponding figure 2 The detailed description of the steps can make the input verification method of the present invention clear flow diagram, as well as the corresponding step description of the flow and the relationship between each step. First, from the description of the sensing unit 1 in the flow chart and the corresponding step S601, the input verification method of the present invention senses and reads the decrypted data DD input by the us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com