Internal threat detection method and system based on user subjective and objective data fusion
A data fusion and threat detection technology, applied in transmission systems, electrical components, etc., can solve problems such as restricting the practicability of internal threat detection systems, low alarm quality, and failure of security defenses, so as to improve real-time update capabilities and reduce false alarm rates. effect on the false negative rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
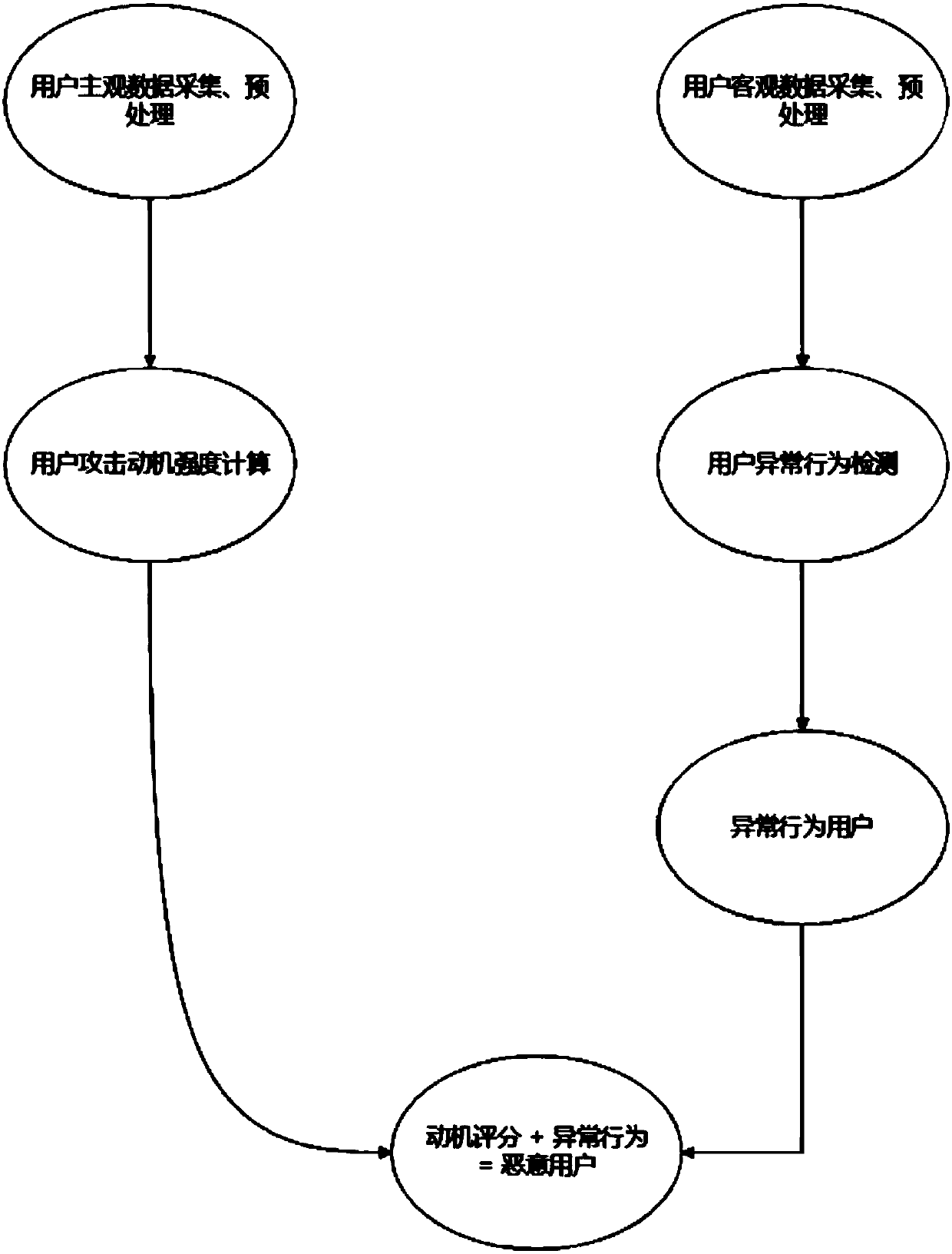
[0057] Based on the enrichment of internal threat detection data dimensions, the present invention uses misuse detection and anomaly detection classifiers cooperatively to design a new type of internal threat detection method with significantly reduced false positives and false positives. The present invention is designed as follows:
[0058] 1. User subjective data collection method
[0059] The core of internal threat detection data enrichment is to expand the subjective data set that characterizes individual user characteristics on the basis of existing user objective data. Subjective data comes from the state of the user in actual life and work, not the behavior traces in the information system. The subjective data mainly comes from the data of the human resource management department:
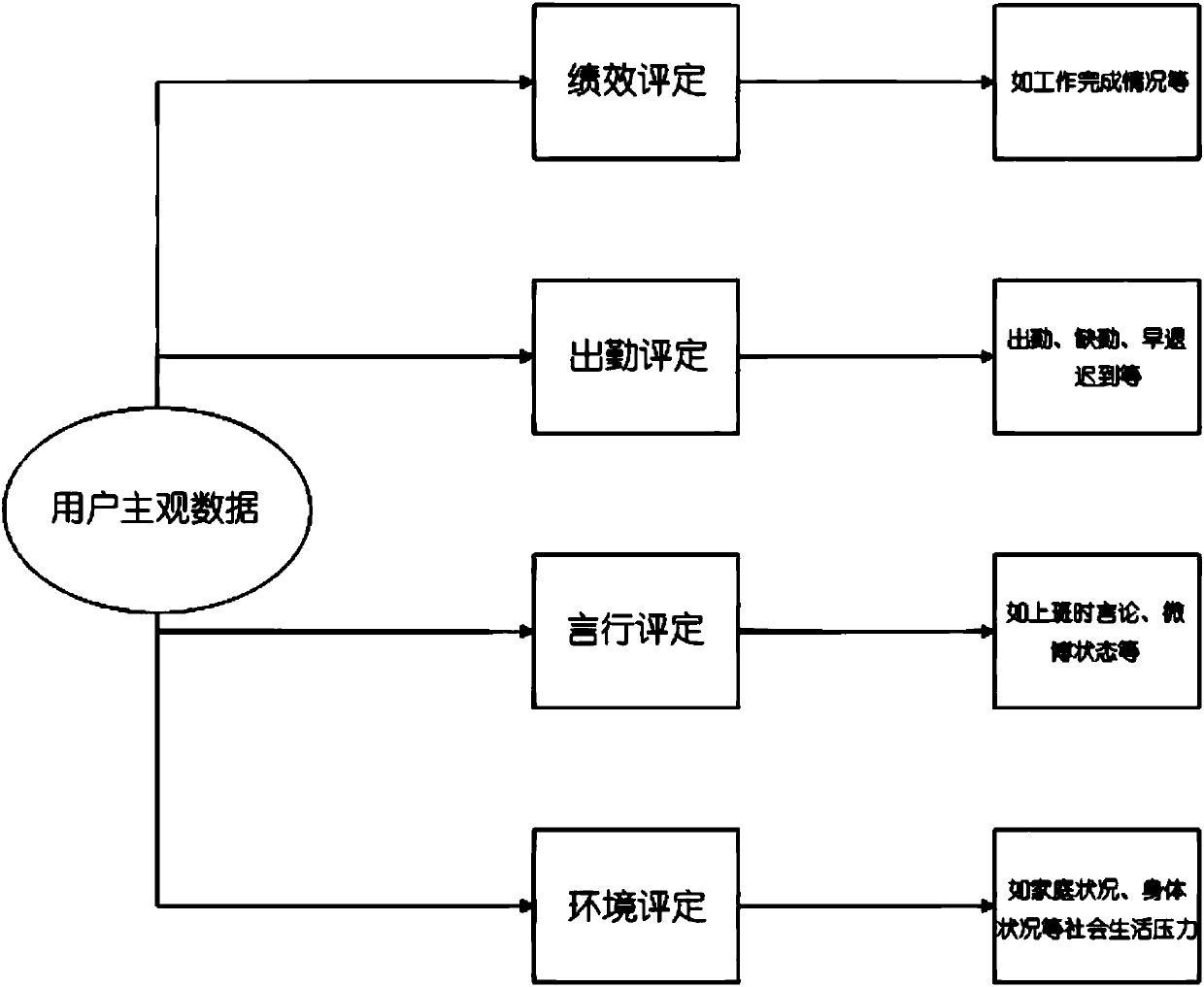
[0060] Such as figure 2 As shown, user subjective data collection mainly comes from the following four areas:
[0061] ●Performance evaluation: it mainly reflects the actual work stat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com