Anti-counterfeit and traceability two-dimensional code generation method, terminal and medium
A two-dimensional code and password technology, which is applied in the field of anti-counterfeiting and traceability two-dimensional code generation, can solve the problems of troublesome operation, high cost, and restrictions on promotion, and achieve the effect of simple operation and low cost.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
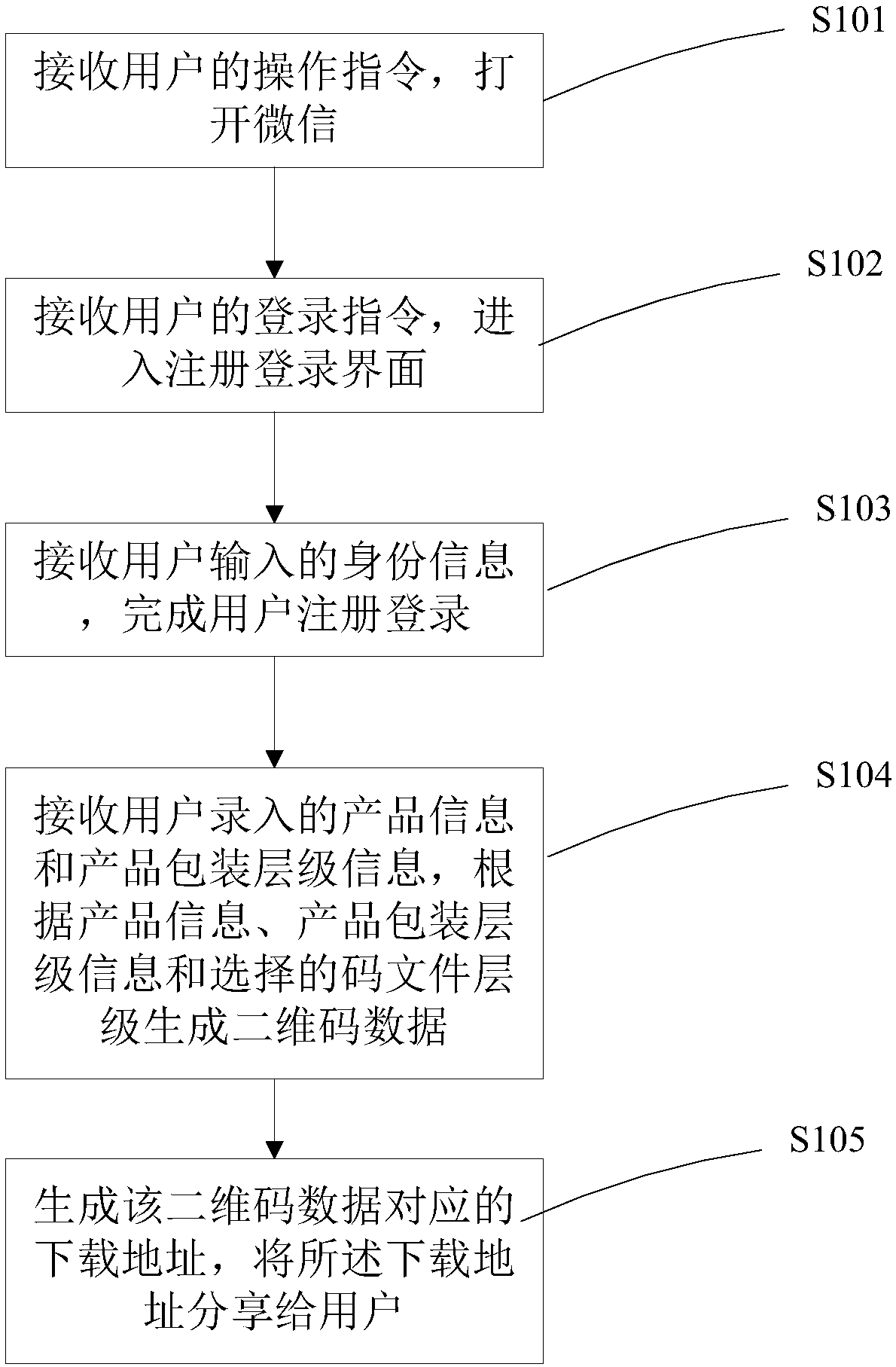
[0063] see figure 1 , Embodiment 1 provides a method for generating an anti-counterfeit and traceable two-dimensional code, including:
[0064] S101: Receive an operation instruction from the user, and open WeChat;
[0065] Specifically, users can follow and enter the official account through the WeChat scan function. This method directly applies for the QR code on the WeChat platform, which is convenient to use.
[0066] S102: Receive a login instruction from the user, and enter the registration login interface;
[0067] S103: Receive the identity information input by the user, and complete the user registration and login;
[0068] Specifically, for a user logging in for the first time, registration is required. When registering, the identity information entered includes company name, phone number, email address, user name, etc. During the registration process, SMS verification or email verification can also be performed. When the verification is passed, the registration...
Embodiment 2
[0076] The method provided in Embodiment 2 is based on the methods provided in other embodiments, and after sharing the download address with users, it further includes:
[0077] Receive the user's scan code command to obtain the query QR code;
[0078] Call the product information and product flow information corresponding to the query QR code in the database;
[0079] Display the product information.
[0080] Specifically, the product flow information includes production information entered in each process during the product production process, including production parameters, production conditions, production personnel information, and the like. This method has the function of traceability. Users can scan and identify the QR code, read the detailed information of the QR code, product authenticity, flow direction, how to use and other information, which is convenient for users to track the product.
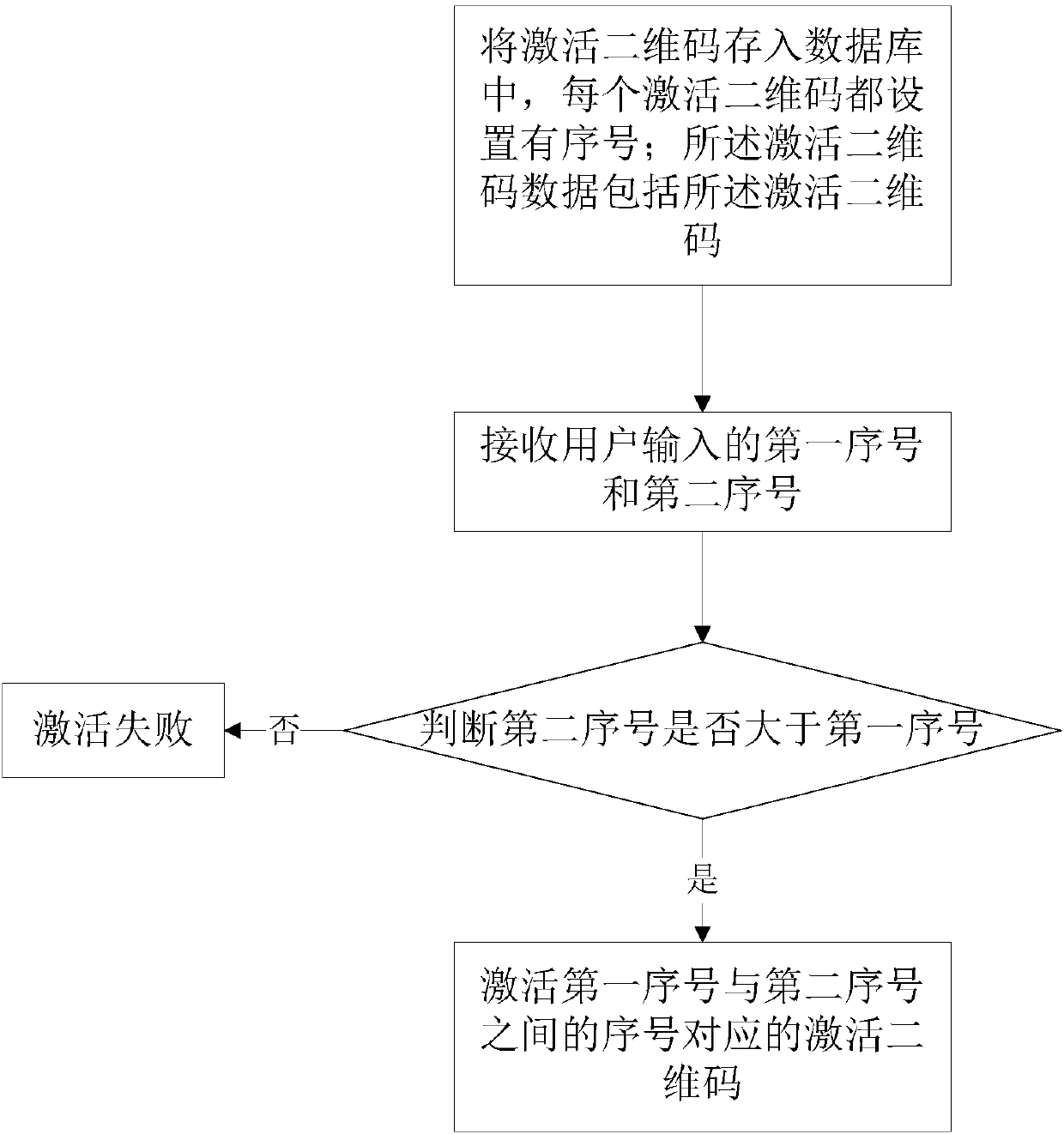
[0081] The method can also generate a sample code of a two-dimensional co...
Embodiment 3
[0090] The method provided in Embodiment 3 is based on the methods provided in other embodiments, and after the two-dimensional code data is shared with users, it also includes:
[0091] receiving the user's address acquisition instruction to obtain the download address of the two-dimensional code data;
[0092] Receive the user's password setting instruction, save the password entered by the user, and obtain the file extraction password;
[0093] receiving a forwarding instruction from the user, and forwarding the download address to the specified user;
[0094] Receive the access address input by the user, when the access address is the download address of the two-dimensional code data, receive the password input by the user, and download the two-dimensional code data when the input password is equal to the file extraction password.
[0095] This function realizes the function of downloading QR code data. The QR code applicant can forward the generated QR code to other use...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com