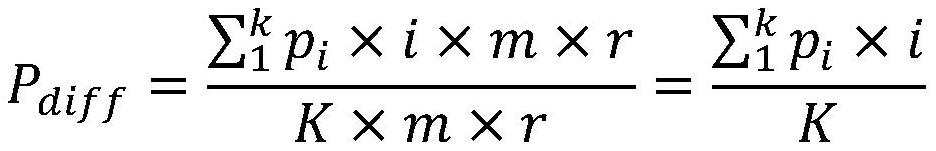A privacy-preserving k-means clustering method
A clustering method and privacy protection technology, which is applied in the field of privacy protection k-means clustering, can solve the problems of inapplicable database and less data mining work, and achieve the effect of wide application range and good clustering accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
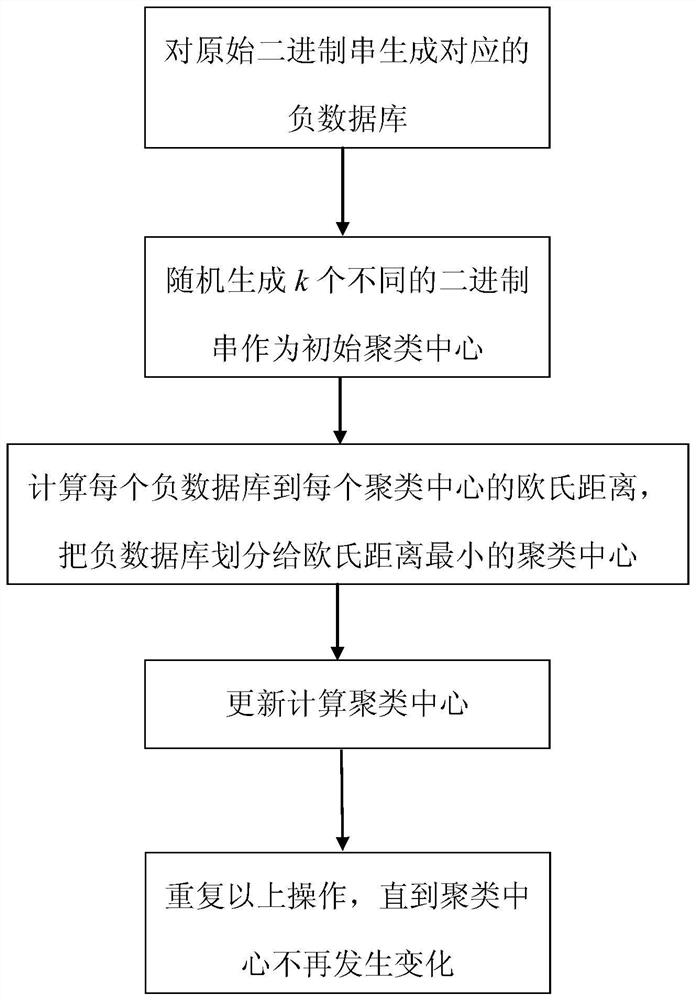
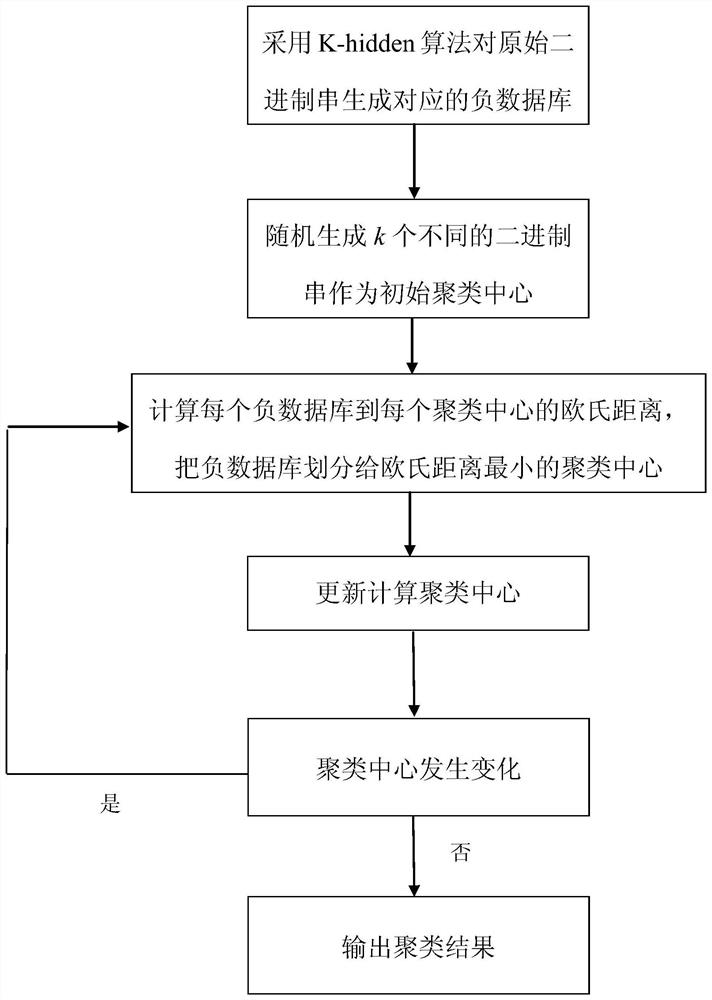
[0029] The present invention is described in detail below in conjunction with accompanying drawing and embodiment, a kind of method for privacy protection k-means clustering based on negative database of the present embodiment comprises:
[0030] Step 1. Convert each piece of data X in the database that needs to be clustered into a binary string. Here, take the iris data set, a commonly used data set for clustering, as an example. There are 150 instances in the iris data set, and each instance contains 4 Attributes, all floating point numbers. Here, the floating-point number is multiplied by 10 and converted into a decimal number, and then the decimal number is converted into a binary number. Since the length of each binary string must be the same, the remaining bits are filled with 0. For example, the value of a certain attribute is 3.5, which is 10011 when it is converted into binary number. If the maximum value of this attribute has six digits, add 0 in front to make up six...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com