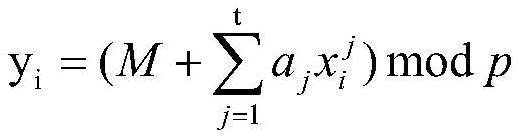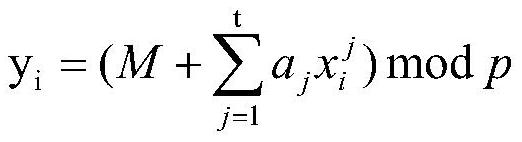A method for protecting the private key of encrypted currency
A technology of currency and encryption, applied in the field of protection of private keys of cryptocurrency, can solve the problems of lack of private key protection methods and loss emergency protection methods, affecting deflation, and cannot be retrieved, so as to reduce risks, improve security, and protect effect of rights
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] In order to make the purpose, technical solution and advantages of the present invention clearer, the embodiments of the present invention will be further described below in conjunction with the accompanying drawings.
[0021] Please refer to figure 1 , the embodiment of the present invention provides a kind of protection method of cryptocurrency private key, it is characterized in that, comprises the following steps:
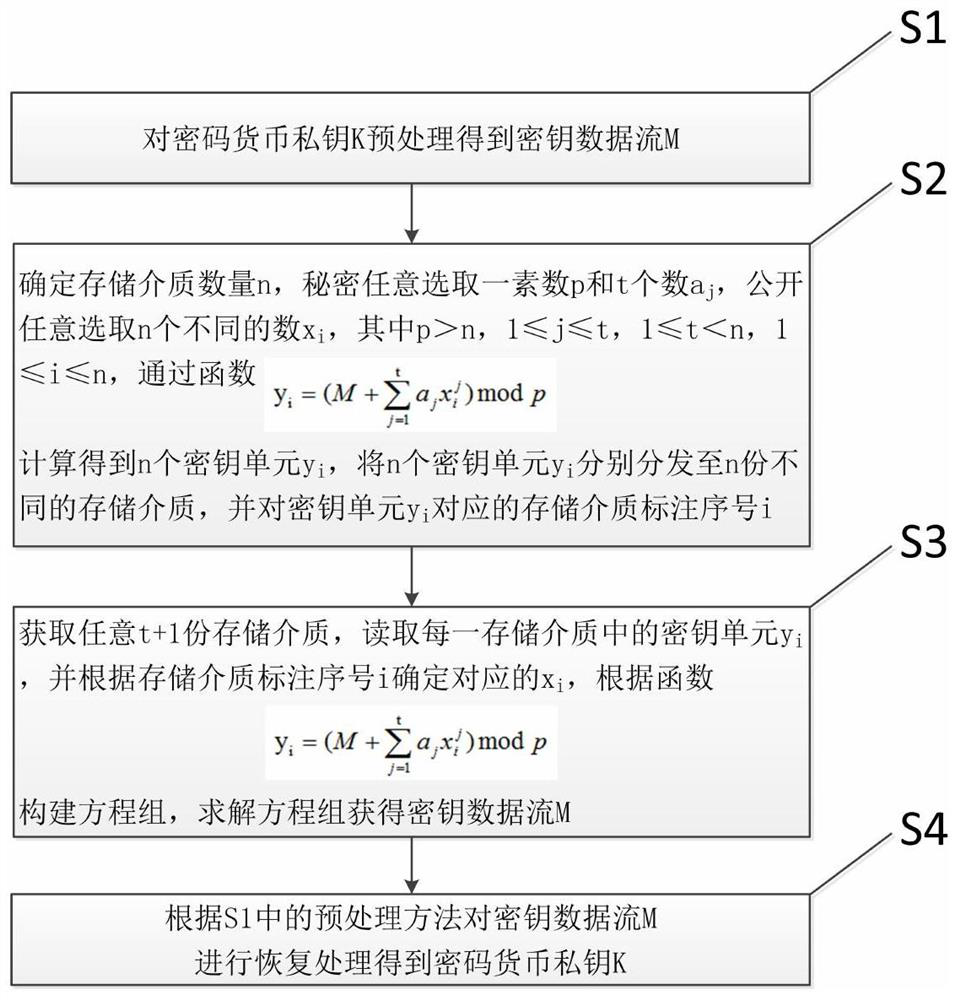
[0022] S1 preprocesses the encrypted currency private key K to obtain the key data stream M;
[0023] S2 Determine the number n of storage media, secretly select a prime number p and t number a j , openly choose n different numbers x i , where p>n, 1≤j≤t, 1≤t
[0024]
[0025] Calculate n key units y i , the n key units y i respectively distributed to n different storage media, and the key unit y i The corresponding storage medium is marked with a serial number i;
[0026] S3 obtains any t+1 storage medium, and re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com