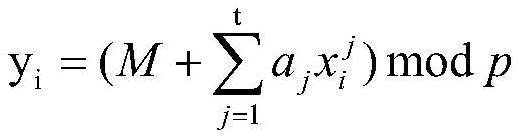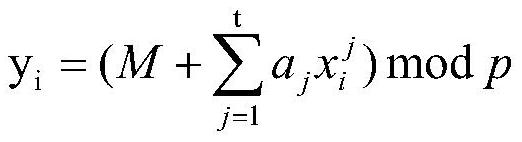Patents
Literature
50results about How to "Protection precision" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Camera and electronic equipment
InactiveCN103533225APrevent candidProtect rightsTelevision system detailsColor television detailsCamera lensPhysics
The invention relates to the field of electronic components for a computer, particularly to a camera and a piece of electronic equipment. The camera comprises a camera body and a liquid crystal electronic control dimming layer, wherein a lens is arranged on the camera body, the liquid crystal electronic control dimming layer is correspondingly arranged outside the lens and is used for enabling the lens to receive the rays of light from the outside through the liquid crystal electronic control dimming layer, and the liquid crystal electronic control dimming layer is electrically connected with the camera body through a switch. The camera provided by the invention is provided with the liquid crystal electronic control dimming layer at the front end of the lens, so that the camera cannot shoot the outside image even if being controlled by a hacker or through a Trojan horse program under the condition that the liquid crystal electronic control dimming layer is closed, as a result, the effect of preventing a lawbreaker from secretly shooting by using the camera is achieved, the right of a user is protected, and the user is prevented from being damaged.
Owner:BOE TECH GRP CO LTD +1
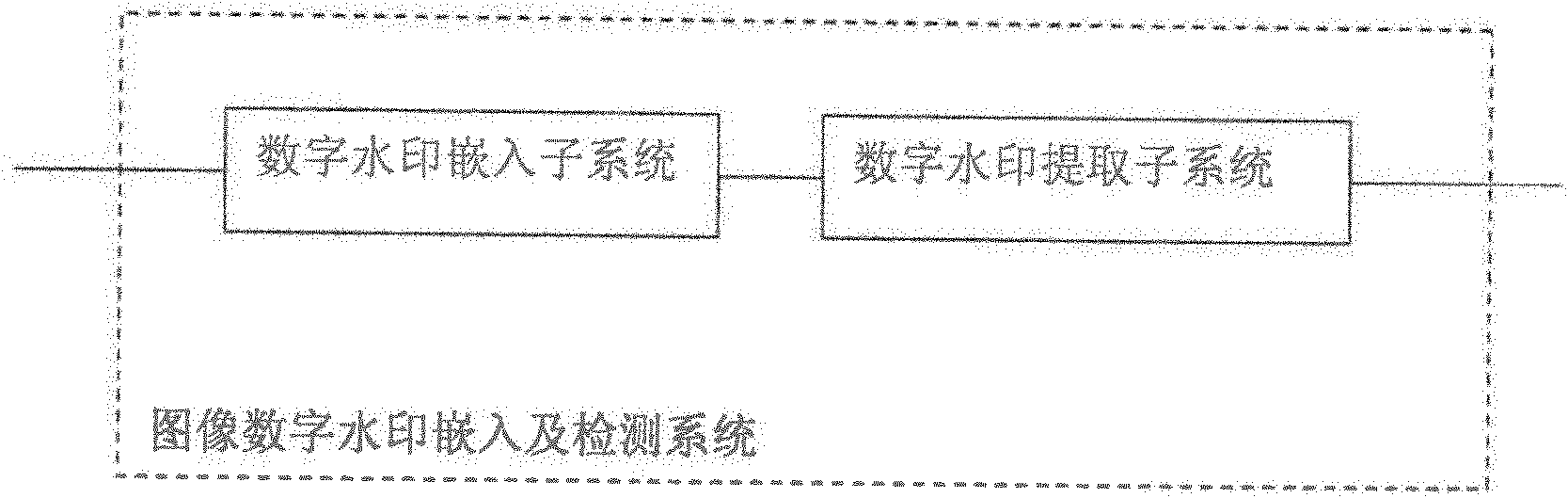
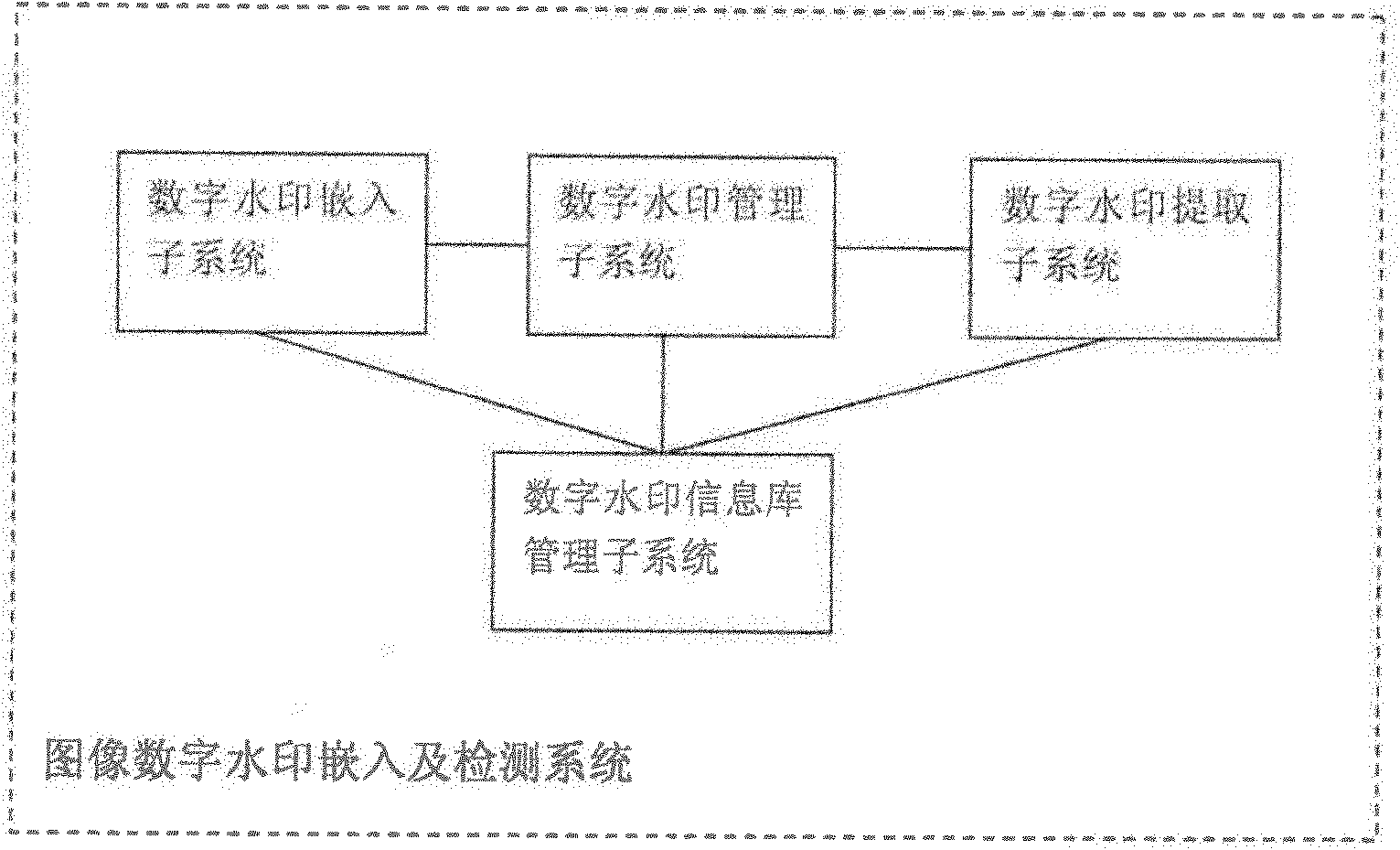
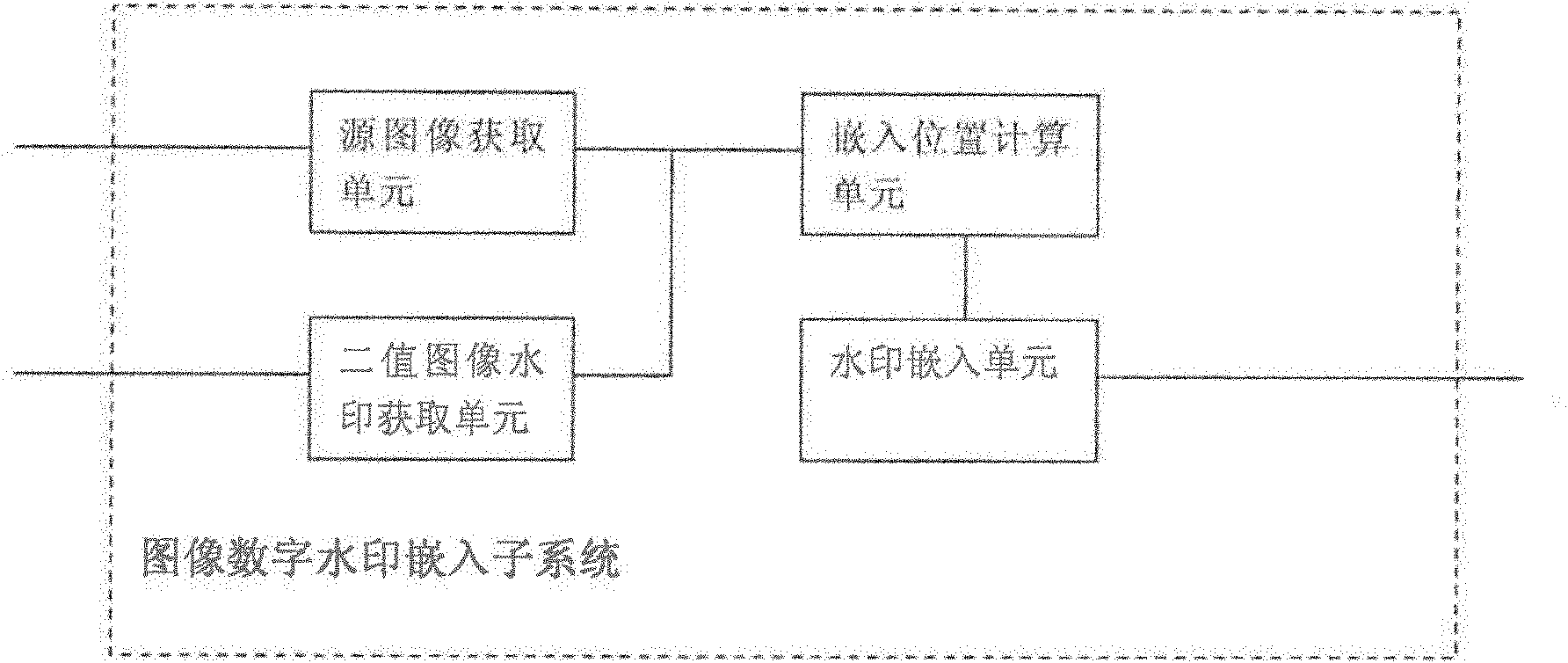
Image digital watermark embedding and detecting system
InactiveCN102609890AEliminate malicious attacksIndestructibleImage data processing detailsProgram/content distribution protectionInformation repositoryThird party
The invention provides an image digital watermark embedding and detecting system which comprises a digital watermark embedding subsystem and a digital watermark detection subsystem. The digital watermark embedding subsystem comprises a binary image watermark acquisition unit, a source image acquisition unit, an embedded position calculating unit and a watermark embedding unit; and a digital watermark extraction subsystem comprises a unit for acquiring an image to be detected, an extraction position calculating unit and a watermark extraction unit. The image digital watermark embedding and detecting system provided by the invention can also comprise a digital watermark management subsystem and a digital watermark information base management subsystem. The image digital watermark embedding and detecting system can be applied to a third-party application system with the copyright authentication qualification so as to provide copyright protection and authentication for image information transmitted on the Internet.
Owner:北京中盈信安科技发展有限责任公司
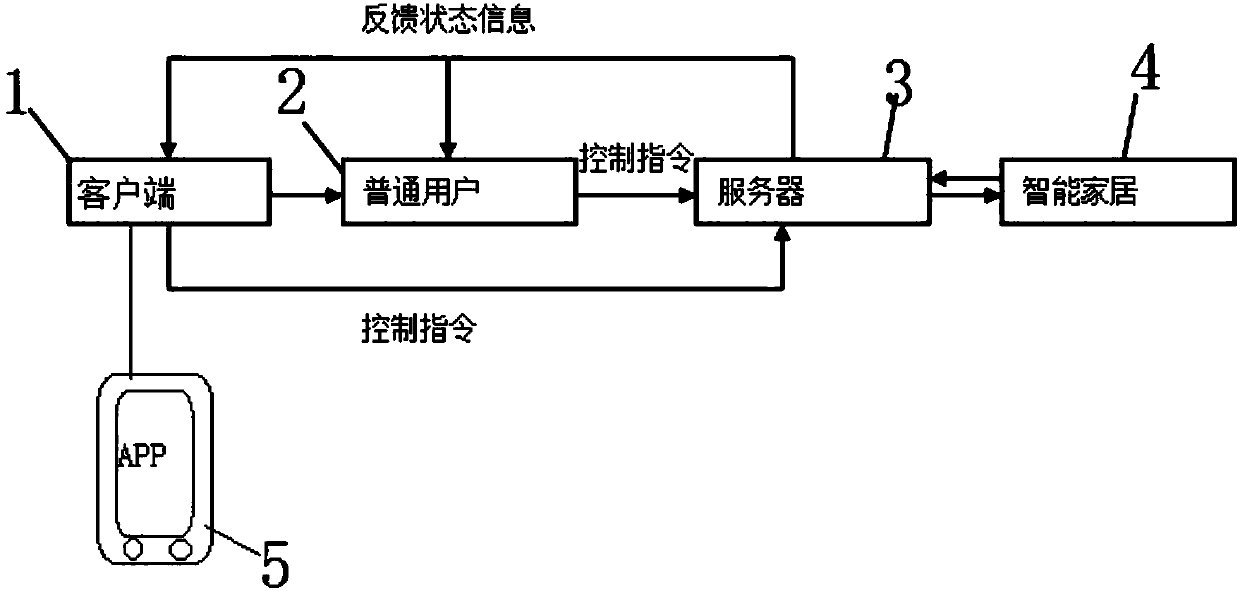
Intelligent household equipment system networking and remote monitoring and managing method based on Internet of Things
InactiveCN104168159ABring promotion effectProtection of technological achievementsData switching by path configurationRemote monitoring and controlMonitoring program
The invention discloses an intelligent household equipment system networking and remote monitoring and managing method based on the Internet of Things and relates to a network architecture and monitoring and managing method for an intelligent household system. The intelligent household equipment system networking and remote monitoring and managing method based on the Internet of Things is characterized in that a management platform, with a household server as the service core, based on a driving program is arranged; different intelligent household equipment systems broadcast the information such as driving program links of the intelligent household equipment systems according to the equipment plug and play protocol, after the server receives a request message for having access to the network, equipment is noticed to register relevant information for having access to the network, a specific monitoring program is run to be in interaction with the equipment systems; for a non-intelligent equipment system, a manual registration networking scheme is provided by the server; a task management mechanism and an event monitoring mechanism are maintained by a service program, and thus linkage between pieces of equipment is achieved; the monitoring program is in interaction with the equipment systems through an equipment driving program, and various communication modes are supported; a driving interface protocol is developed normatively by the equipment driving program, and the whole architecture, the method and the event of the equipment systems are described; mobile applications are in interaction with the server according to a uniform monitoring protocol.
Owner:吴志辉
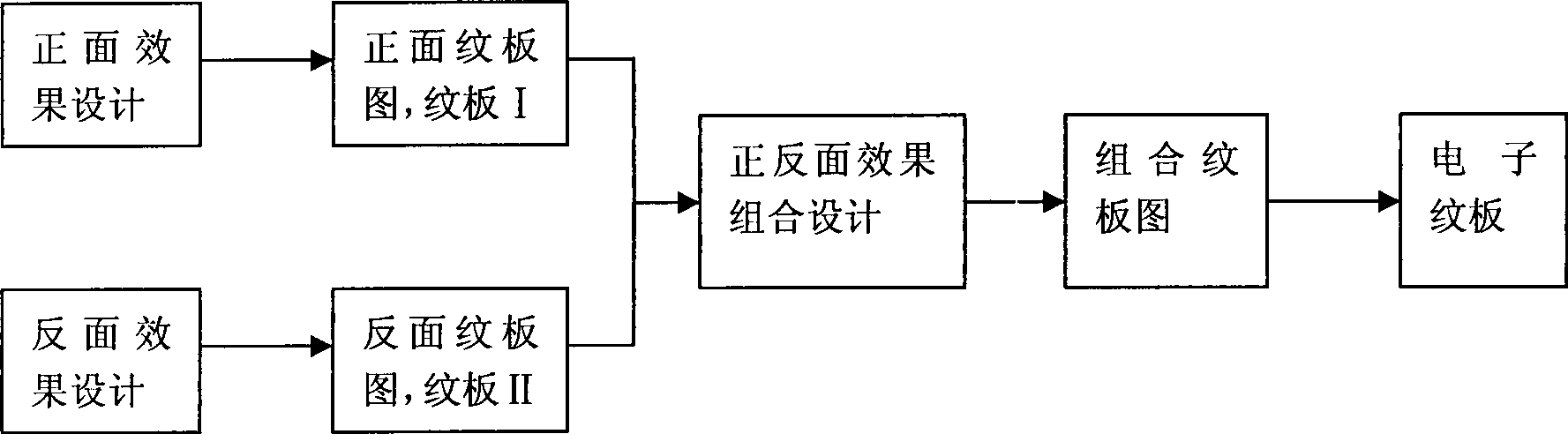
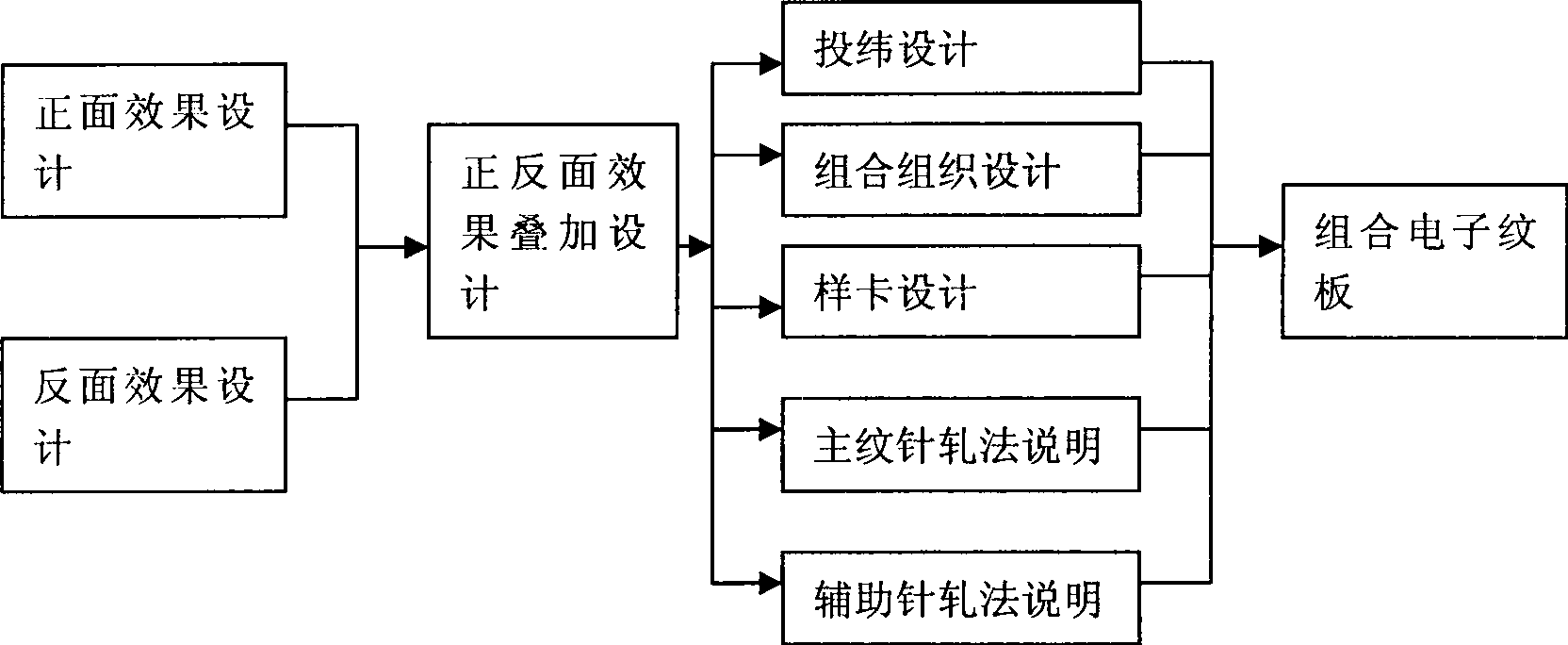
Design method of two-sided different effect digital jacquard dress fabric
InactiveCN101457433ARich varietyProtection precisionPattern making devicesCard-punching apparatusPunchingEngineering
The invention discloses a design method for double-faced different-effect digital jacquard weave garment material. The design method for the double-faced different-effect digital jacquard weave garment material is characterized in that the method comprises the steps as follows: (1) the front face effect design is carried out on the fabric to obtain a front pattern and the back face effect design is carried out on the fabric to obtain a back pattern; (2) the front pattern and the back pattern are superimposed to be displayed in one plan of weave, and then picking design, composite weave design, scale design, major weave needle-punching introduction and accessorial needle-punching introduction are carried out; (3) a composite digital weave plate is generated. The method is applicable to garment material development to weave double-faced different-effect digital jacquard weave garment material with different colors, patterns and stylistic characteristics on the front and back faces.
Owner:JIAXING YUELONG JACQUARD & WEAVING +1
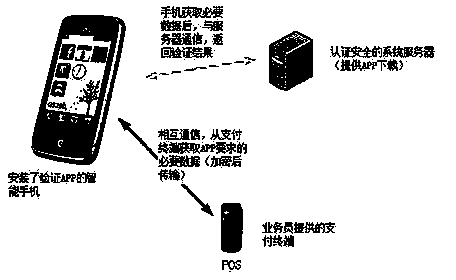
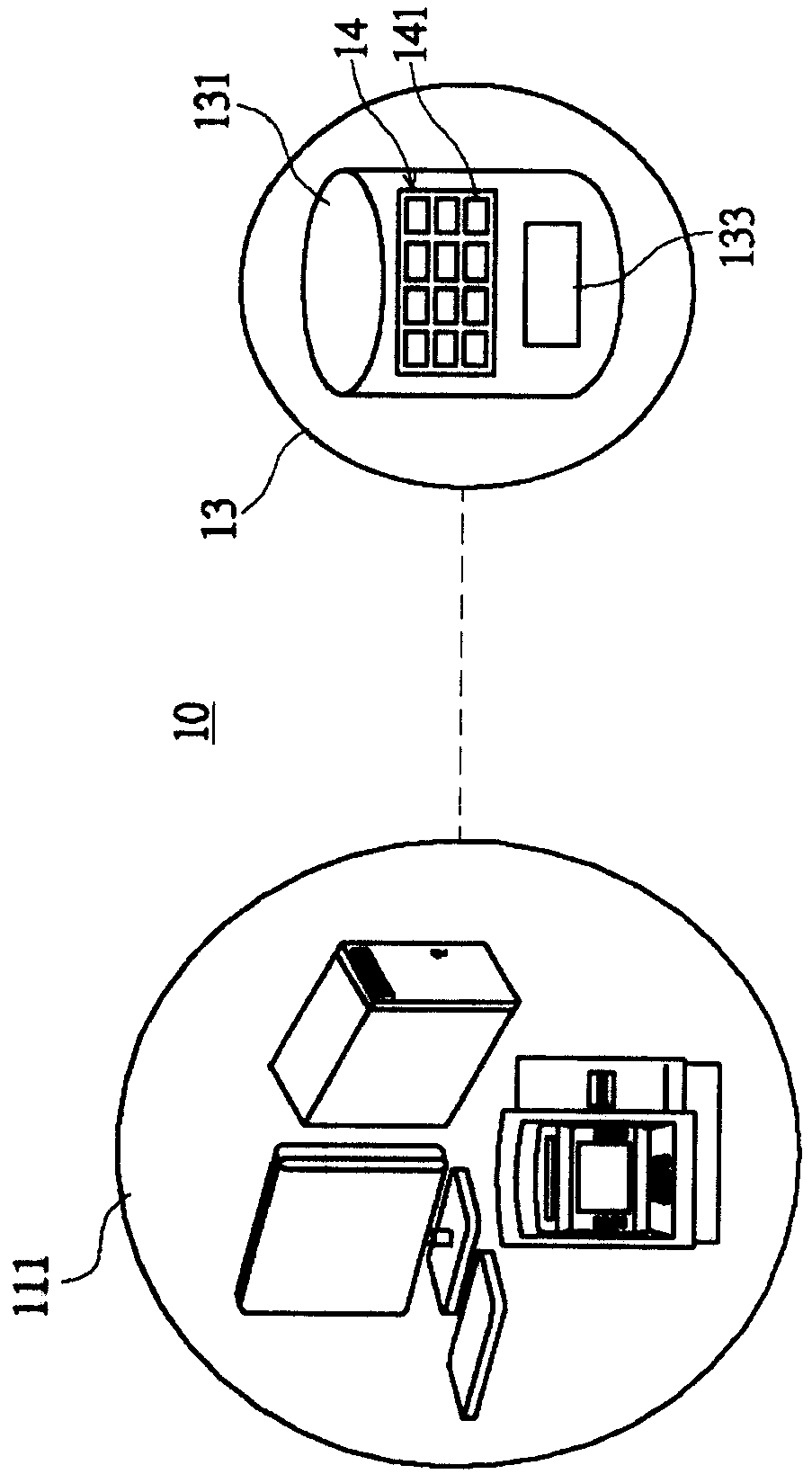
Electronic payment terminal verification method and system
InactiveCN103745353AConfirm securityProtection securityPoint-of-sale network systemsProtocol authorisationRelevant informationData information
The invention relates to an electronic payment terminal verification method, which is characterized by comprising the steps: providing a system server, wherein a database of POS (point-of-sale) terminals which pass security certification is stored on the system server; downloading and installing software which authenticates the security of a POS terminal by a user; obtaining security data information of the POS terminal through which a card needs to be swiped, transmitting the security data information to the system server for verification, and returning a result to the user by the system server after verification. By adopting the electronic payment terminal verification method and system, the security of the payment terminal can be confirmed, the security of relevant information of the card of a card holder who swipes the card, the doubt of the person who swipes the card is eliminated, the rights of the person who swipes the card are protected, and the payment environment is favorably improved.
Owner:FUJIAN LANDI COMML EQUIP CO LTD
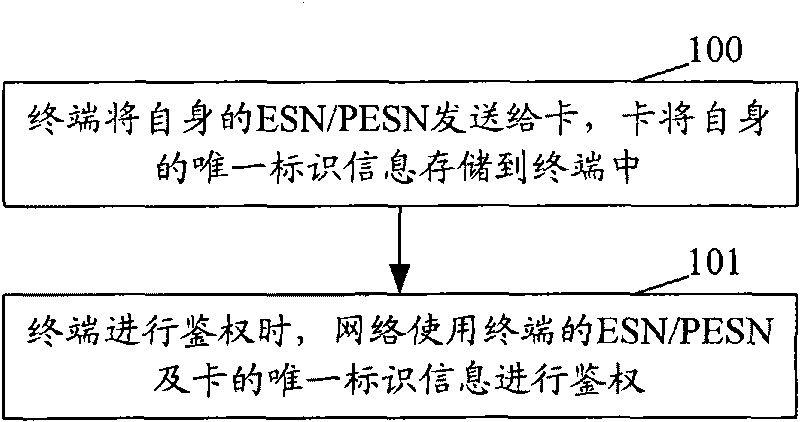
Method and system for realizing interlocking of phone and card
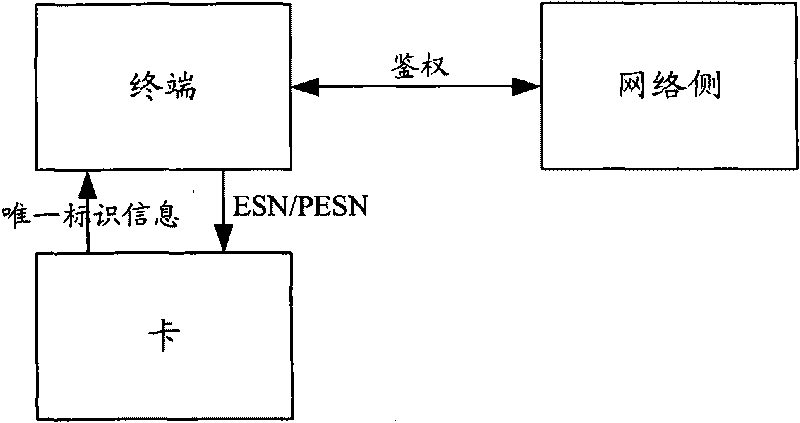
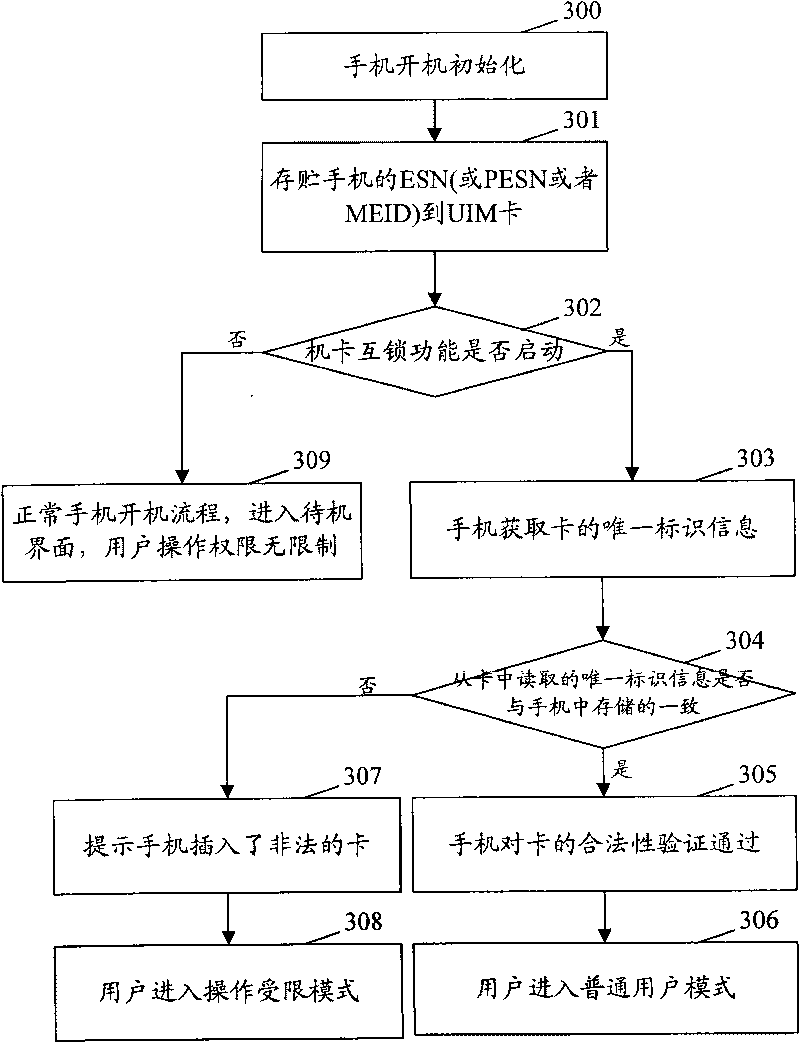
InactiveCN101711023AAchieve interlockProtection precisionSecurity arrangementNetwork data managementComputer hardwareService development
The invention provides a method and a system for realizing the interlocking of a phone and a card. The method comprises that: a terminal sends a personal ESN (or PESN) to the card; the card stores personal unique identification information in the terminal; and when the terminal performs authentication, a network performs the authentication by using the ESN (or PESN) of the terminal and the unique identification information of the card. The method of the invention realizes the fully interlocking of the phone and the card, namely, only the terminal in a corresponding relation stored in the network can use the card corresponding to the corresponding relation and the card in the corresponding relation can only be used on the terminal. The method of the invention utilizes conventional parameters of the terminal and the card, not only brings convenience to the related service development of operators so that confidentiality is relatively higher and users cannot cancel the interlocking even though knowing the interlocking principle of the phone and the card, but also protects the right of the operators to the largest extent.
Owner:ZTE CORP
Method and system for loading third-party software
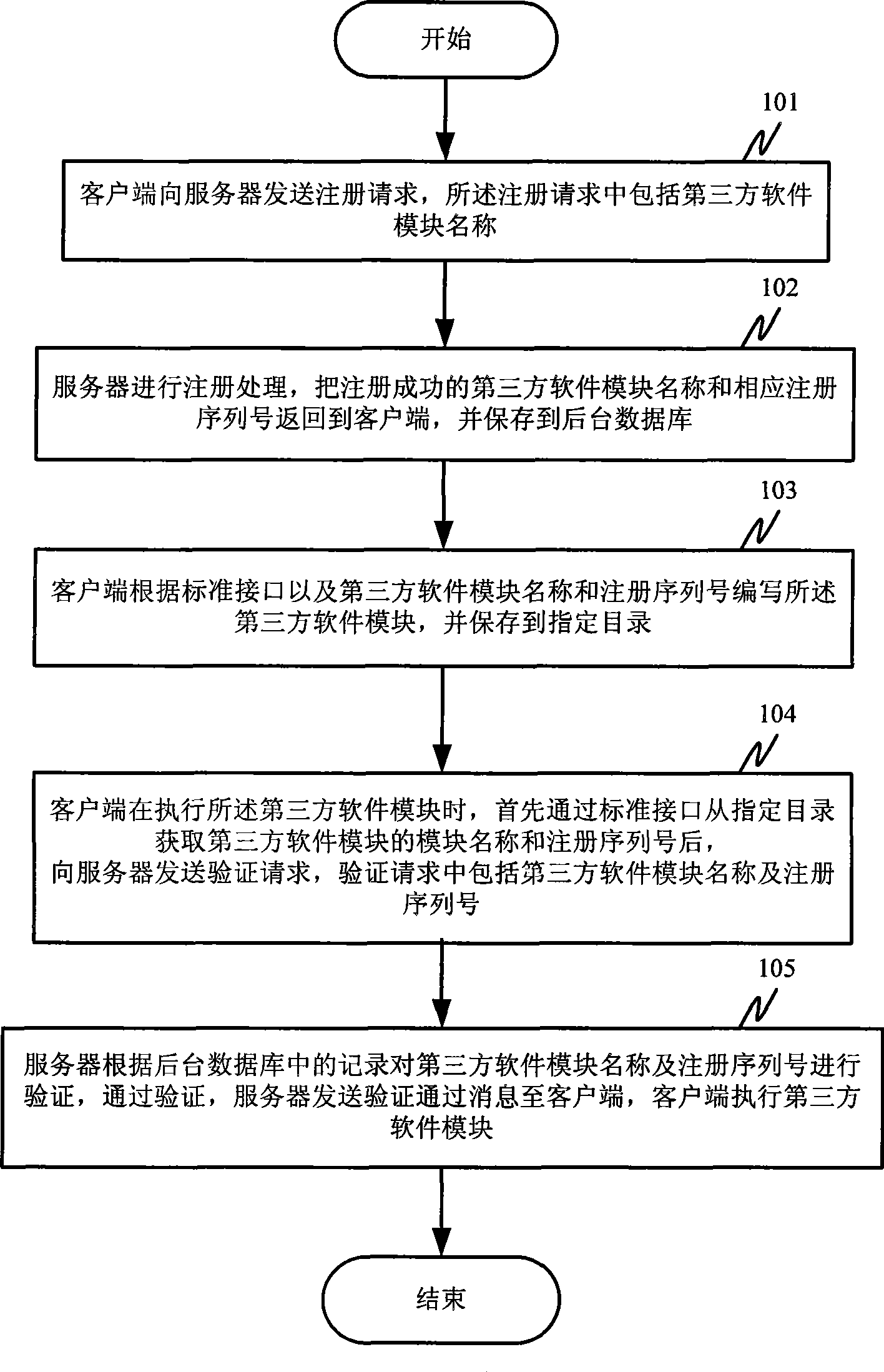
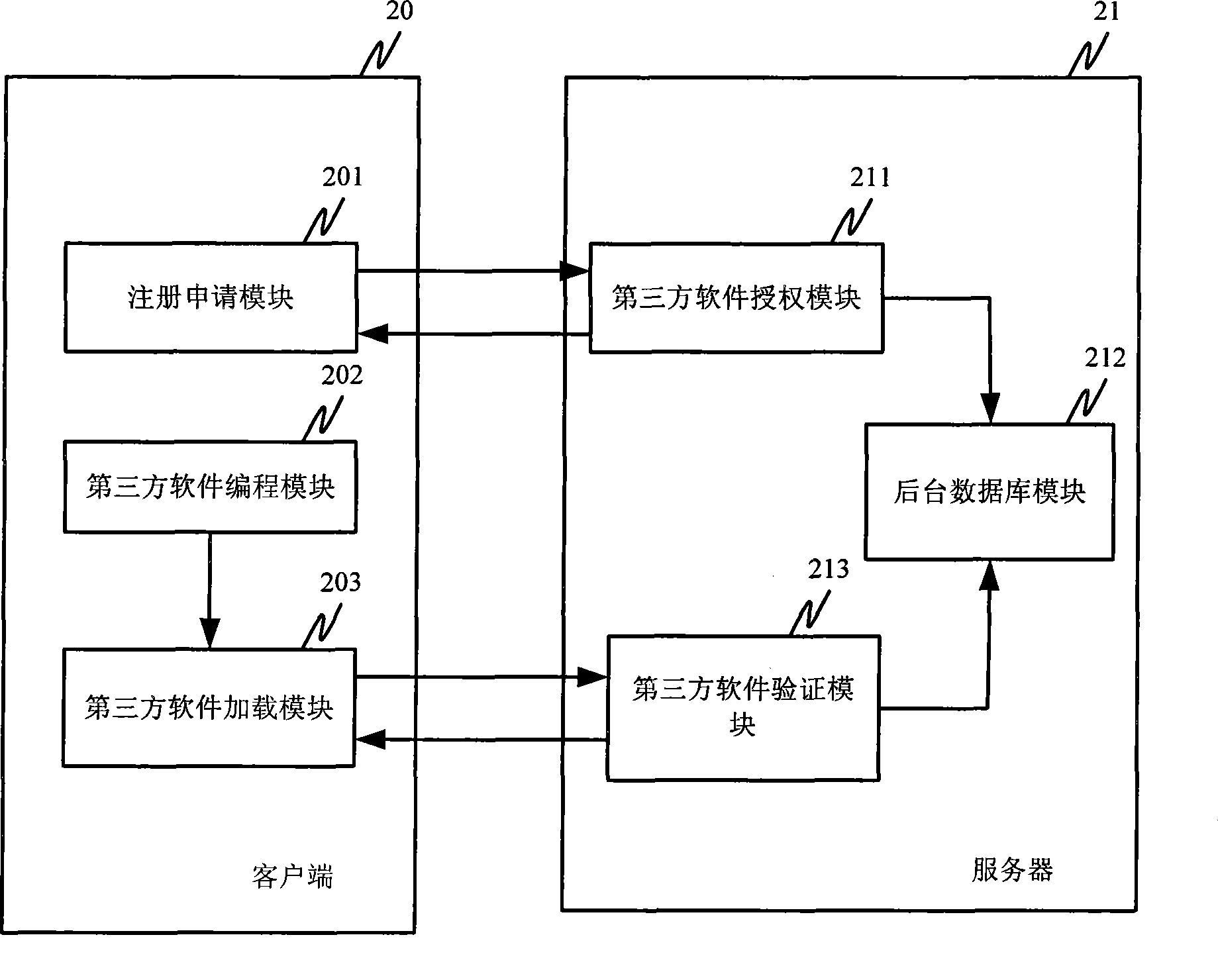
ActiveCN101398873ARealize managementProtect rightsComputer security arrangementsTransmissionClient-sideThird party
The invention provides a method and a system for loading third-party software. The method includes the following steps: (1) a registering request is sent to a server by a client terminal and the registering request includes the module name of the third-party software; (2) the server carries out registering treatment and returns the module name of the third-party software, which is successfully registered, and the corresponding registering sequence number to the client terminal and stores to a background database; (3) when the client executes the module of the third-party software, the client terminal sends the validating request which includes the module name of the third-party software and the registering sequence number to the server; (4) the server receives the validating request and validates the module name of the third-party software and the registering sequence number according to the record in the background database; if the validation is passed, then the server sends validation passing information to the client terminal and the client terminal executes the module of the third-party software. Management on the third-party software can be better realized by the method and the system for loading the third-party software provided by the invention.
Owner:SHENZHEN TRANSSION HLDG CO LTD
Instant communication-based smart home control method
InactiveCN107819673AImprove home intelligenceImprove securityData switching by path configurationAutomatic controlUser Privilege
The invention belongs to the field of smart homes, and discloses an instant communication-based smart home control method. The method comprises the steps that an administrator is set in a client, wherein the administrator has the rights of setting the number of ordinary users and the permissions of the common users, and the ordinary users can send control instructions to a server in the permissions of the ordinary users; the user can receive the control instructions of the administrator and the ordinary users and feed back state information of a smart home; and the smart home executes the first received instruction and sends the working state information to the server. According to the method, facilities related to home life are efficiently integrated by means of a network communication technology and an automatic control technology, an efficient control method for residential facilities and family schedule affairs is constructed, the home intelligence, security, convenience and comfort are improved, and an environment-friendly and energy-efficient comprehensive smart home network control system is achieved.
Owner:安徽省雨龙家具有限公司
Account management system and method with secret function
InactiveCN101030239AEffective controlAvoid churnDigital data authenticationComputer securityManagement system
Owner:SHOOTER DIGITAL +1
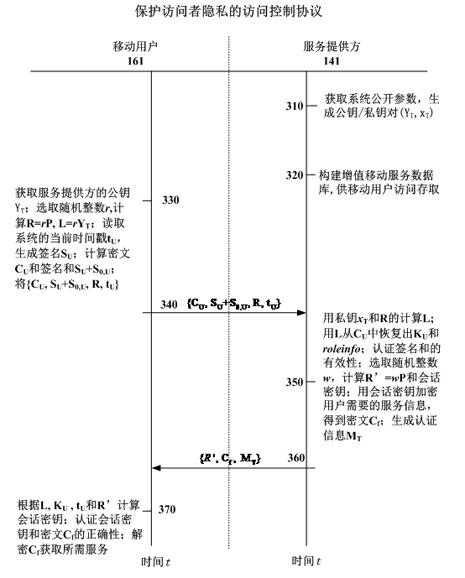
Access control method for protecting access privacy of user in mobile value-added service system
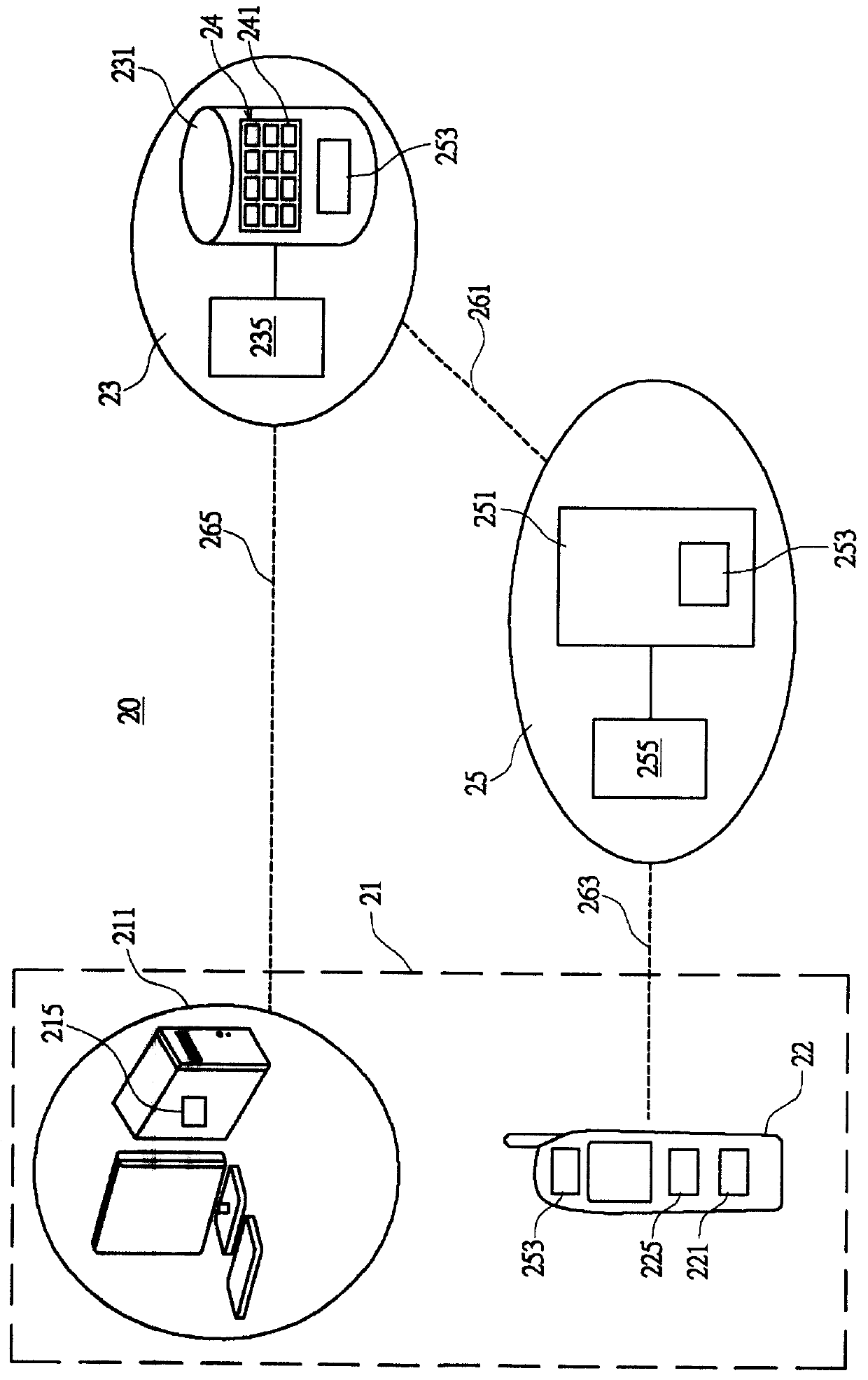
InactiveCN102665205AProtection precisionSuitable for development requirementsPublic key for secure communicationSecurity arrangementSurrogate keyRole management
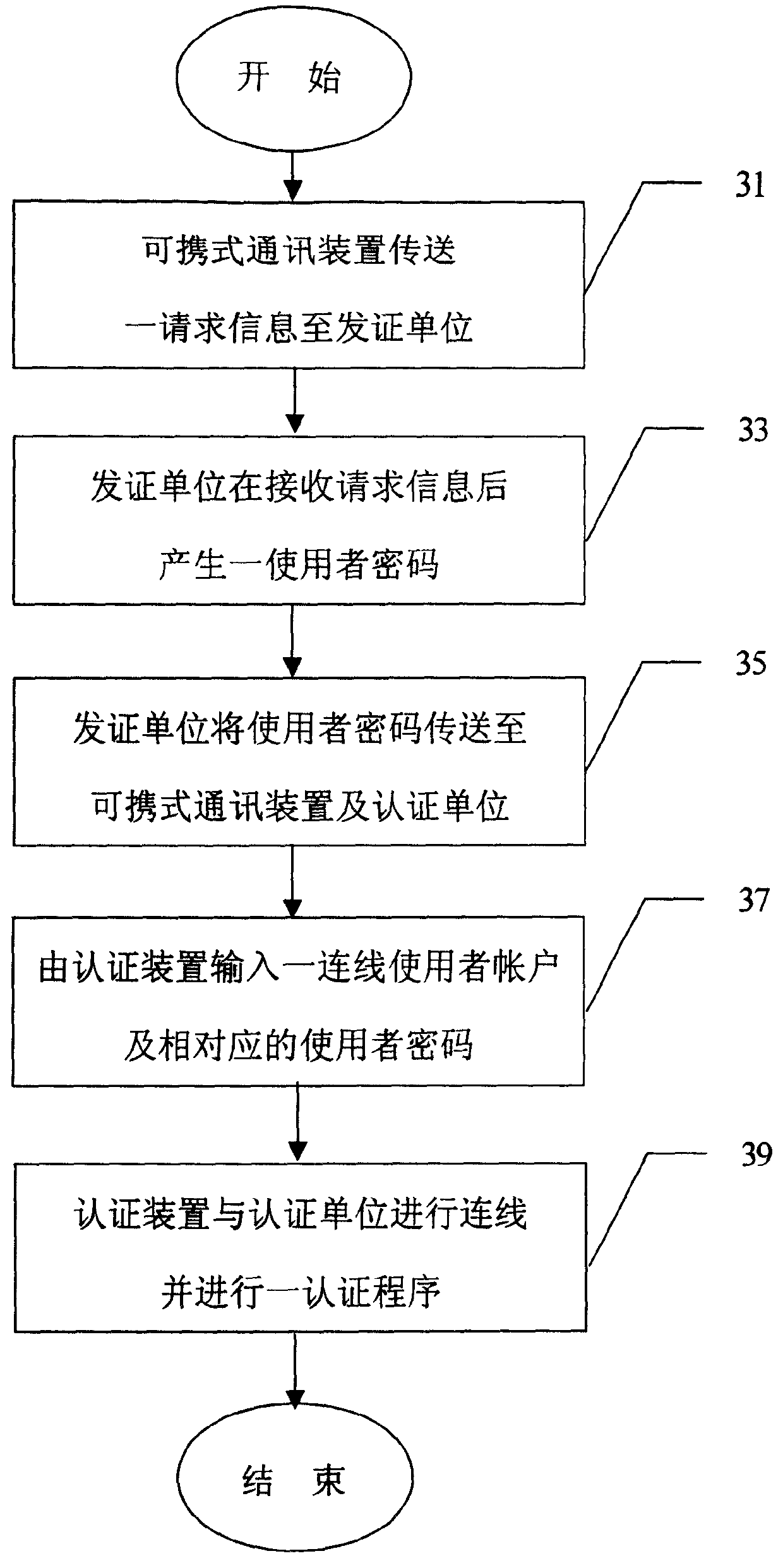
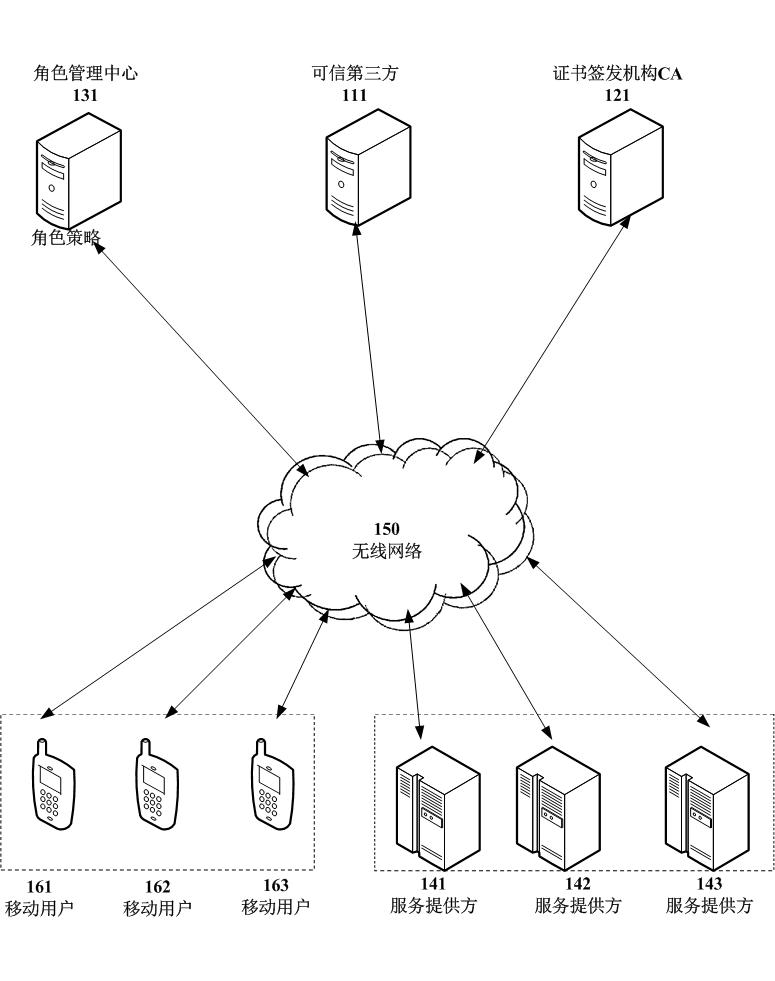
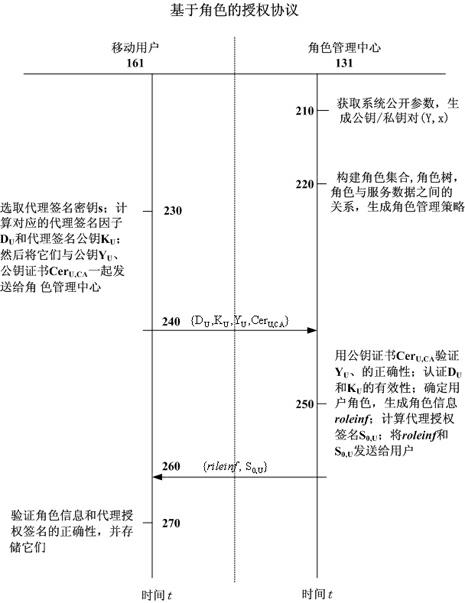
The invention relates to the technical field of mobile value-added services, in particular to an access control method for protecting access privacy of a user in a mobile value-added service system. The method comprises system initialization, role-based authorization, certification and secret key consultation, tracking of the user and revocation of a user role. A role management center is required to implement honestly the authorization of the agent key and the opening of the anonymity, in particular, the role management center can not forge request information of the mobile user and protects interest of the user, and besides, a service provider does not know personal preferences of legal users to the mobile value-added service, so that the requirement of the system is reduced, the legitimate interests of users are safeguarded, the privacy right of users is protected and the method is suitable for development requirements of existing value added services.
Owner:JINAN UNIVERSITY
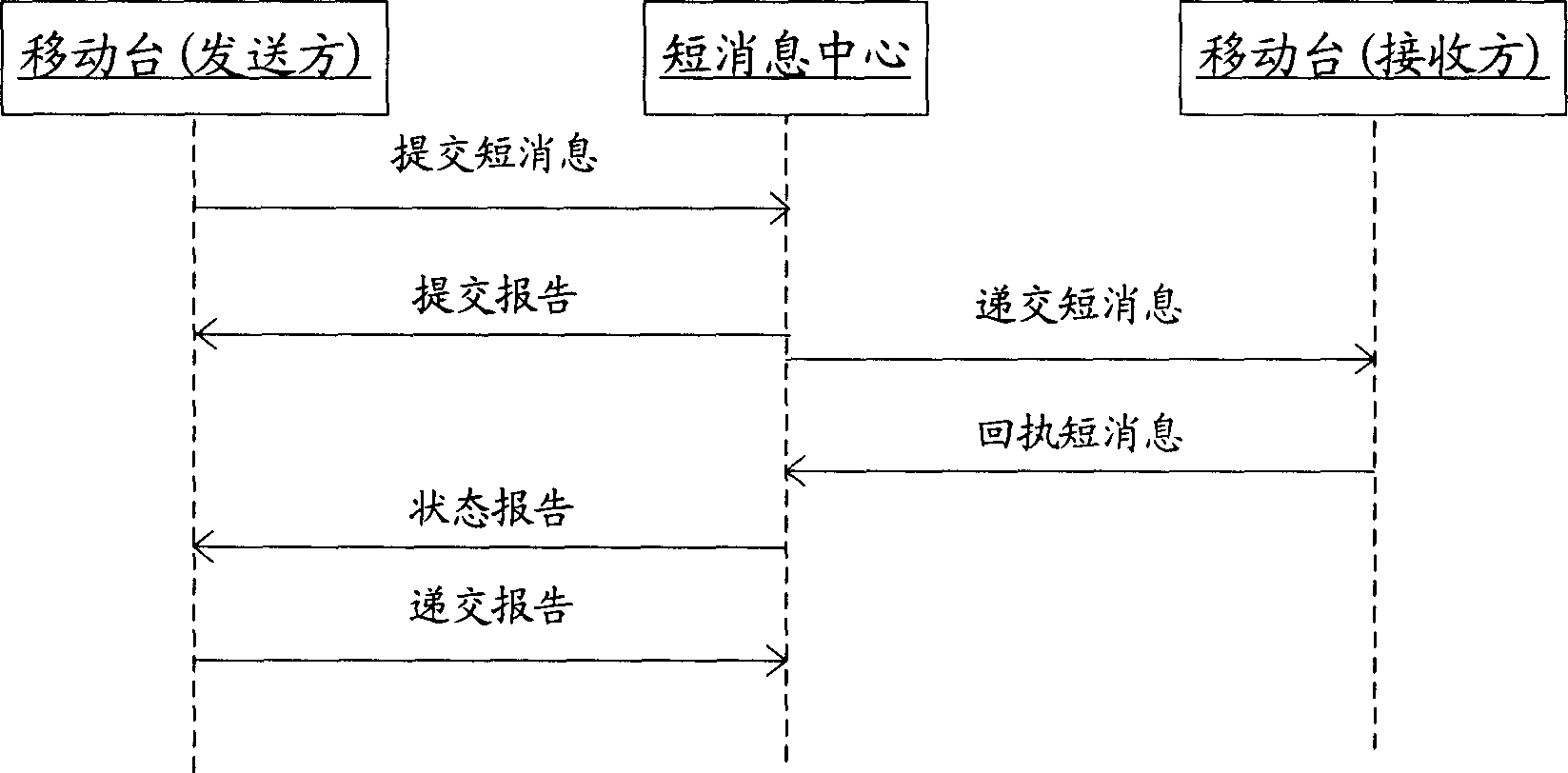
Short message receipt processing method and system
ActiveCN1809179AProtection precisionRadio/inductive link selection arrangementsMessaging/mailboxes/announcementsProcess systemsHandling system
This invention discloses one short message feedback process method, which comprises the following steps: short message receive mobile platform sets feedback short message permit label according to short message feedback label and short message and answers back the short message center with short message; short message center processes feedback short message according to feedback message permit and requirement label. This invention also discloses one short message process system, which comprises the following parts: mobile platform to send or receive short message and set short message requirement feedback and permit label; short message center to process short message according to short message permit label.
Owner:HUAWEI TECH CO LTD
Upgrading method of electric energy meter program
InactiveCN103455358AImprove securityProtection precisionProgram loading/initiatingElectricity meterEmbedded system
The invention aims to an upgrading method of electric energy meter program, aiming to reduce possibility of upgraded programs being copied and prevent illegal program from being downloaded to a target meter. The technical scheme includes a, editing and generating an HEX document to be upgraded into executable upgrading device, deleting Bootloader code during editing to make upgrading codes into incomplete upgrading codes and encrypting the incomplete upgrading codes; b, running the upgrading device on computers to enable the upgrading device to log in the target meter and to verify effectiveness of the target meter, if pass, then go to Step C, if not, then stop upgrading; c, utilizing the upgrading device to download the incomplete upgrading codes into the target meter; d, utilizing the target meter to run the received incomplete upgrading codes to check whether Bootloader codes exist in the meter or not and verify the Bootloader codes. If the result is yes, then the upgradation is succeeded, if the result is no, then the upgradation is failed.
Owner:HEXING ELECTRICAL
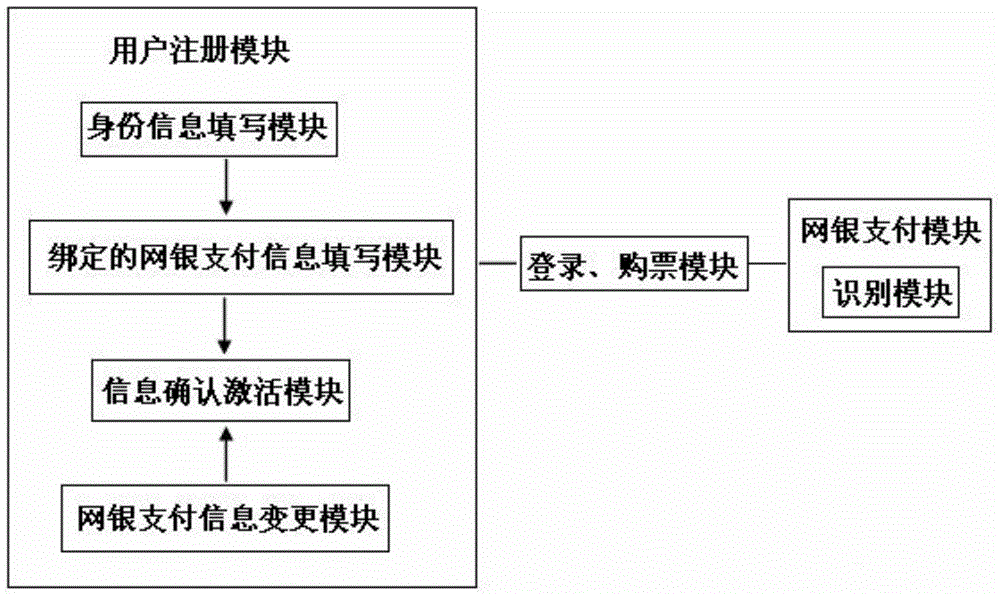
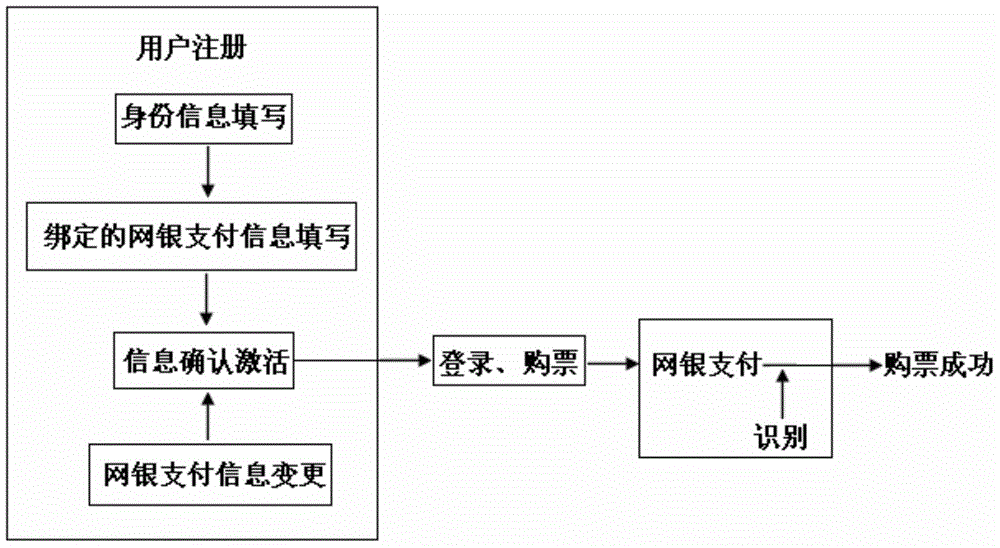
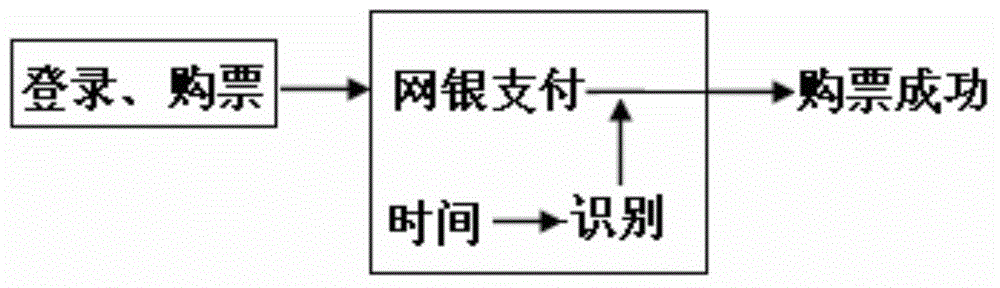
Online ticketing system
InactiveCN104680410AProtection of rights and opportunitiesReduce wastePayment architectureBuying/selling/leasing transactionsSpecific timePanic buying
The invention discloses an online ticketing system. The online ticketing system comprises a user registration module and an E-bank payment module, wherein the user registration module comprises an identification information filling module and a bound E-bank payment information filling module; the E-bank payment module comprises an identification module for indentifying E-bank payment information. By controlling on or off of the identification module, a person only can buy a ticket on the internet per se or buy the ticket for others. The identification module can be started according to special time or / and special line, only when identified E-bank payment information is consistent with the bound E-bank payment information in the controlled period or / and line, ticketing payment operation can be carried out, panic buying and hoarding of train tickets or air tickets by online scalpers can be effectively eradicated completely, right and opportunity of fair ticketing of passengers can be effectively protected, and waste of valuable power resources can be avoided.
Owner:SHANGHAI QIMOU ENERGY SOURCE TECH DEV
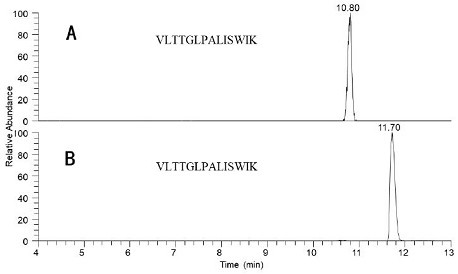
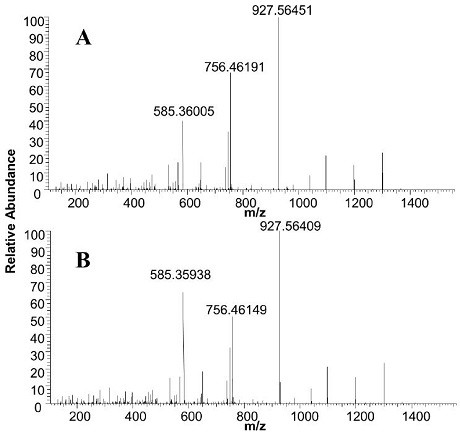
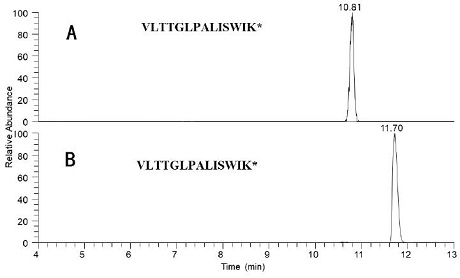
Method for quantitatively detecting melittin by liquid chromatography-tandem mass spectrometry
InactiveCN111855883AOvercome the drawbacks of analytical methodsAchieve accurate quantificationComponent separationBee productsPhysical chemistry
The invention relates to the field of detection, in particular to a method for quantitatively detecting melittin by liquid chromatography-tandem mass spectrometry, which comprises the step of detecting a characteristic peptide fragment of melittin in a sample to be detected by liquid chromatography-tandem mass spectrometry, wherein the sequence of the characteristic peptide fragment is VLTTGLPALISWIK. The method has high accuracy, precision and sensitivity, is high in stability, is suitable for accurate quantification of melittin in complex matrixes, and has important practical significance for protecting rights and interests of melittin consumers and maintaining healthy development of the bee product industry.
Owner:BEE RES INST CHINESE ACAD OF AGRI SCI
Self-locking compact sliding mechanism
InactiveCN102305225APrecise positioningSmall footprintFluid-pressure actuator safetyEngineeringSelf locking
The invention relates to a self-locking compact sliding mechanism which comprises a permanent connecting baseplate, an air cylinder installing transition plate, an air cylinder mounting plate, an air cylinder, an in-place stop dog I, a connecting block, a linear guide assembly, a front end connecting block of an air cylinder rod, a fastening bolt, a locking nut, an in-place stop II and a protection box, wherein the upper part of an air cylinder body is connected and arranged on the front end surface of the permanent connecting baseplate by virtue of the air cylinder installing transition plate and the air cylinder mounting plate; the sliding block in the linear guide assembly is positioned on the permanent connecting baseplate, and is slidably matched with a linear guide; the protection box is arranged on the outer side of the straight line slide guide; the front end of an air cylinder expansion link and a connecting block on the front end of the cylinder rod are fixed by the locking nut, and the connecting block on the front end of the air cylinder is connected with the protection box by the fastening bolt; the in-place stop dog I is connected to the protection box by the connecting block; and the in-place stop dog II corresponds to the in-place stop dog I so as to be fixed on the air cylinder mounting plate. The sliding mechanism provided by the invention has the advantages of compact structure, high intensity, welding space saving, stable product quality and improved work efficiency is improved.
Owner:TIANJIN FUZHEN IND EQUIP
Rapid intelligent comparison and security detection method for big data of mobile malicious software
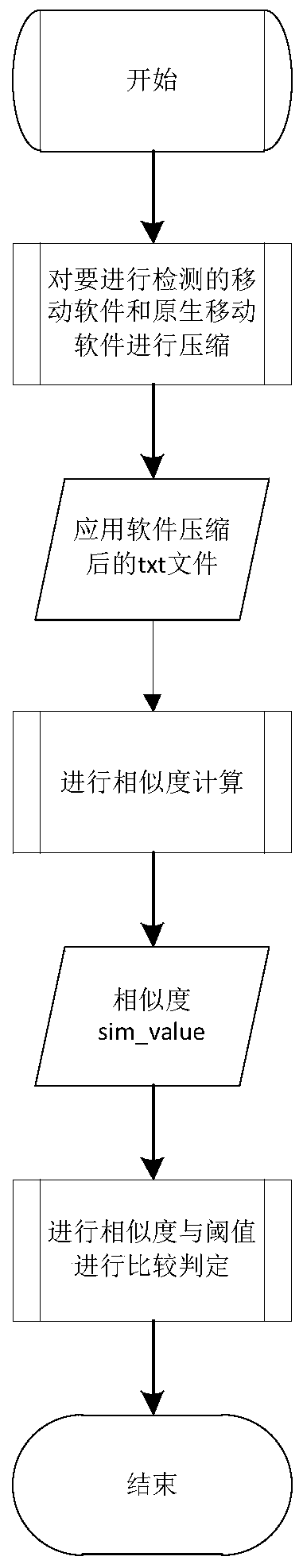
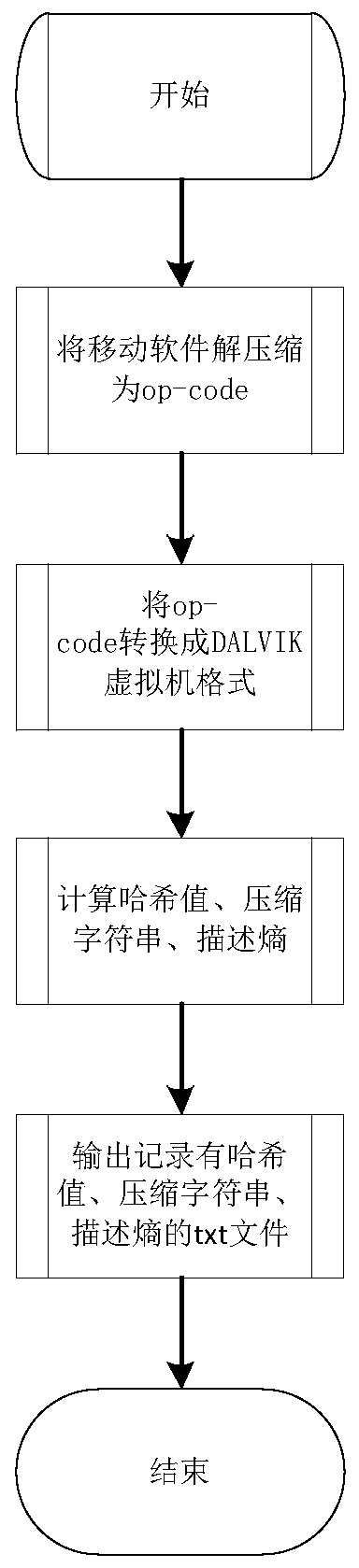
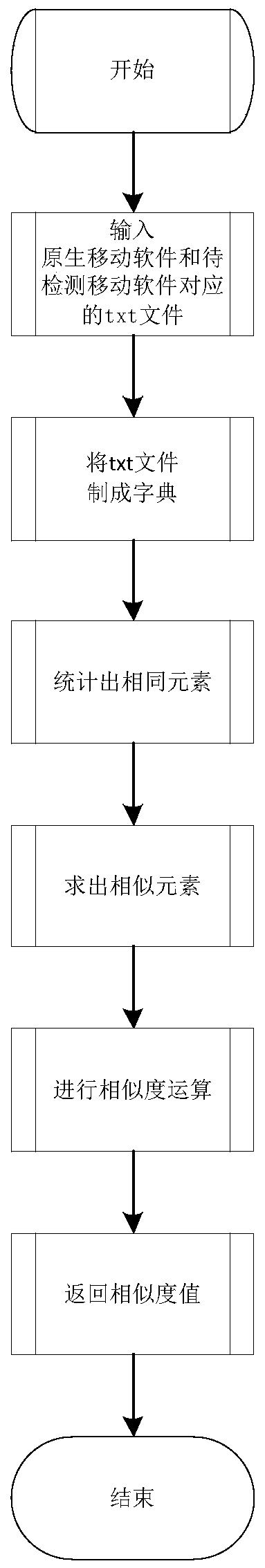
ActiveCN109858249AProtection precisionProtect interestsPlatform integrity maintainanceComputer networkAttack
The invention discloses a rapid intelligent comparison and security detection method for big data of mobile malicious software. As the mobile software application develops rapidly, many popular mobileapplications are copied or repackaged. An attacker may repackage the application to insert advertising profits or disseminate malware. Massive mobile software codes form big data, and the comparativecalculation volume of similarity is very huge. According to the method, the compressed character string, the description entropy and the hash value method are combined to provide a rapid intelligentcomparison detection algorithm; the similarity between the mobile application software is obtained through calculation, if the similarity between the mobile application software is greater than or equal to a preset threshold, the condition that the detection program has suspicion of repackaging or plagiarism is considered, further whether the detected mobile software has malicious attack codes ornot is analyzed, and finally the rapid security detection of the big data of the mobile software is realized.
Owner:JINAN UNIVERSITY
Hardware circuit encryption device realized through CPLD
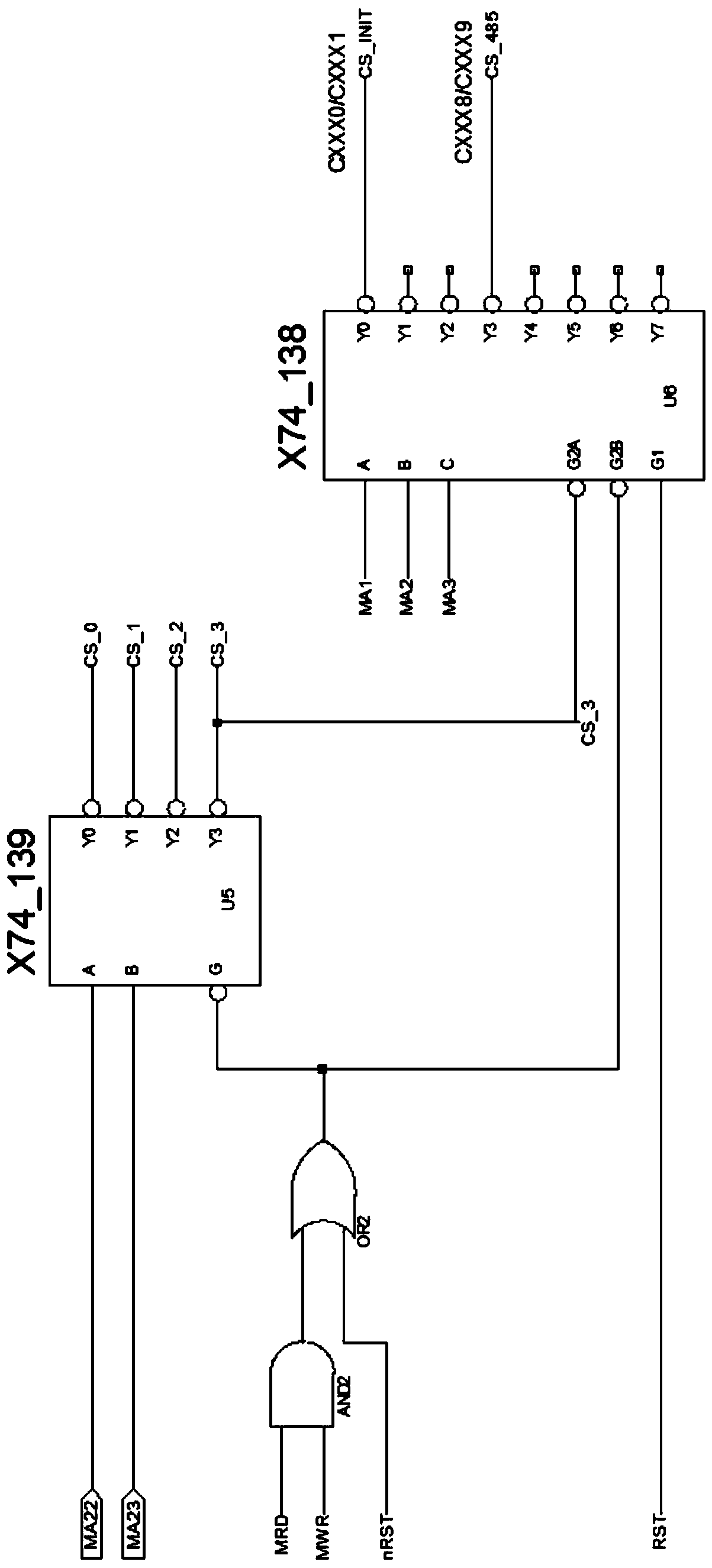
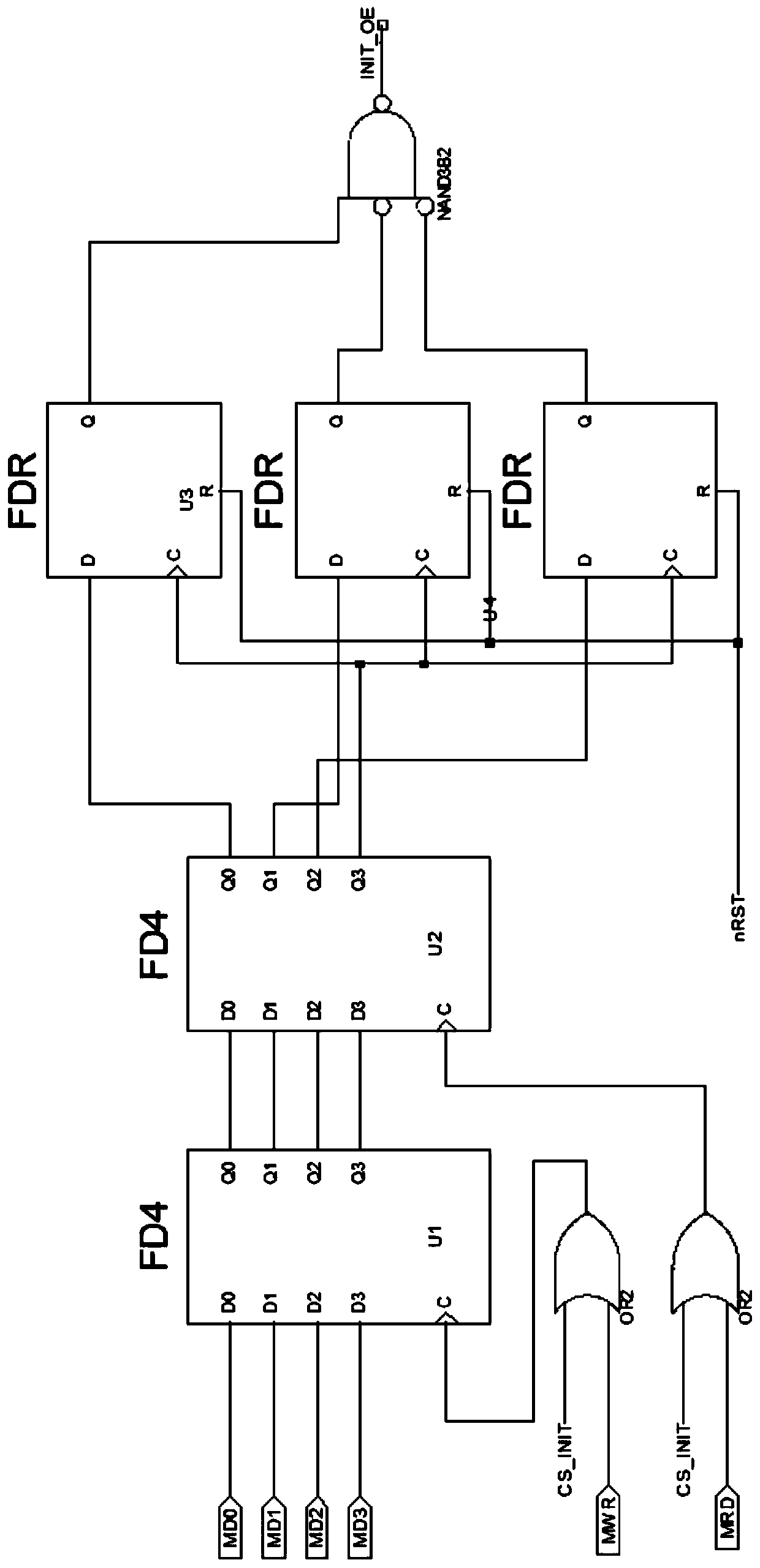
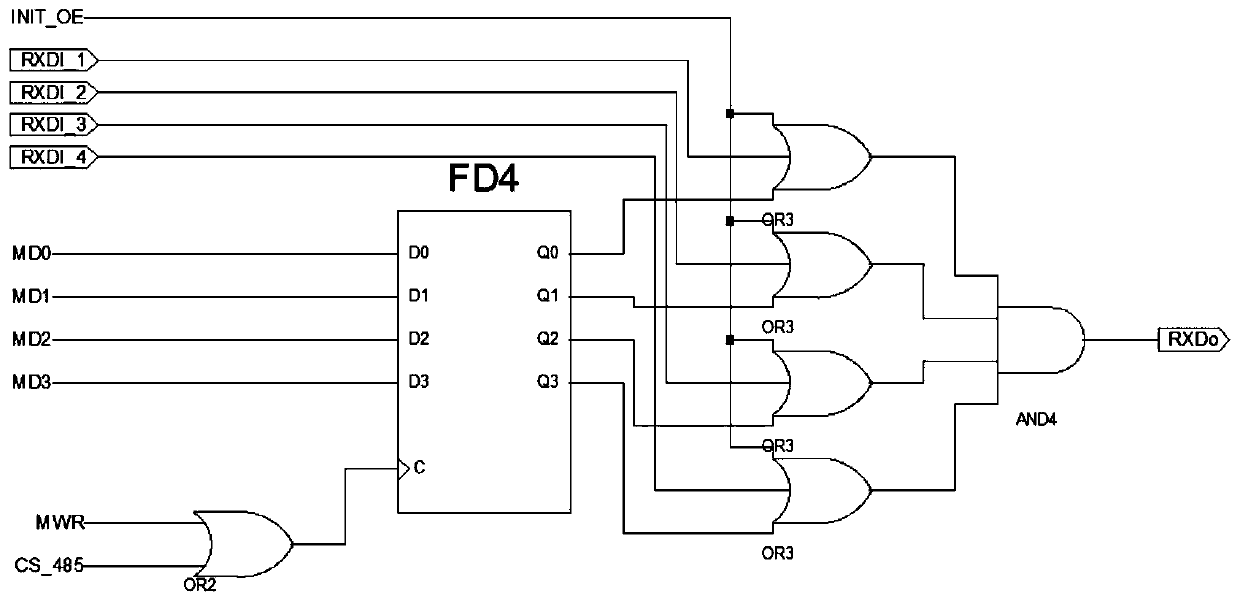
ActiveCN111079167AImprove plasticityGive full play to the characteristicsDigital data protectionEnergy efficient computingComputer architectureControl signal
The invention discloses a hardware circuit encryption device realized through a CPLD (Complex Programmable Logic Device), and aims to solve the problems of increased volume and high cost of a hardwarecircuit mainboard of a business gateway. A decoding module comprises a second-fourth decoder and a third-eighth decoder and is used for carrying out address decoding on an input address; a cryptographic number writing module comprises five D triggers, two OR gates and an NAND gate; the two OR gates are used for receiving a control signal, the output of the two OR gates is used as trigger signalsof the first D trigger and the second D trigger, the output of the first D trigger is used as the input of the second D trigger, and the output of the second D trigger is used as the input of the restthree D triggers; a communication pipeline control module comprises a D trigger, a two-input OR gate, four three-input OR gates and a four-input AND gate, the two-input OR gate is used for receivingcontrol signals, the output of the two-input OR gate serves as the input of the D trigger, the output of the D trigger serves as the input of the three-input OR gate, and the output of the three-inputOR gate serves as the input of the four-input AND gate.
Owner:XINZHONGXIN ELECTRONICS HARBIN
Additional shaft guide rail structure of universal industrial robot
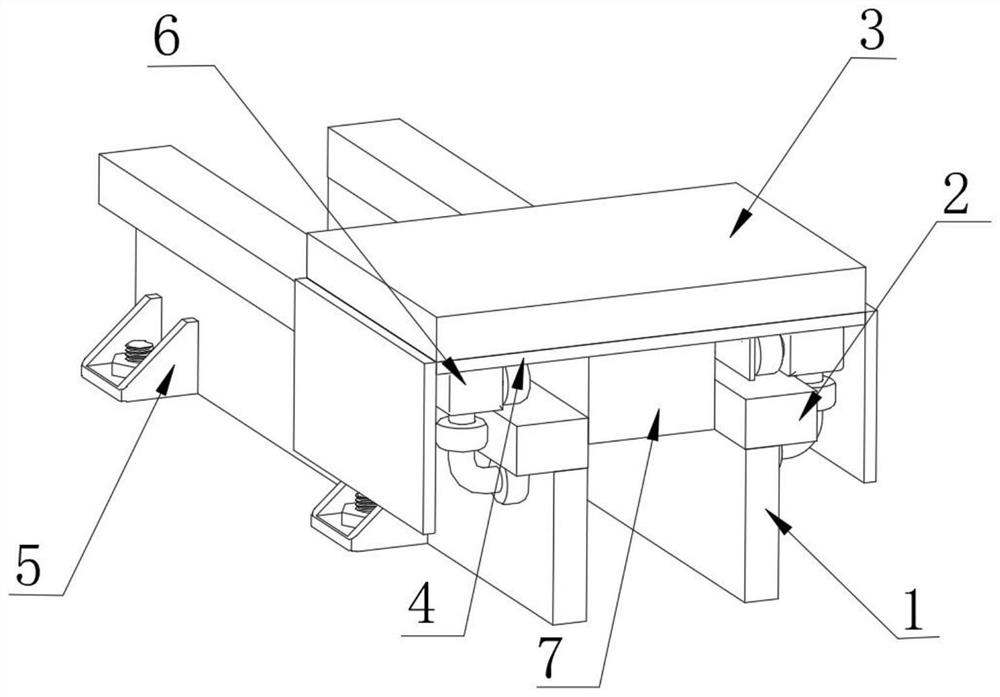
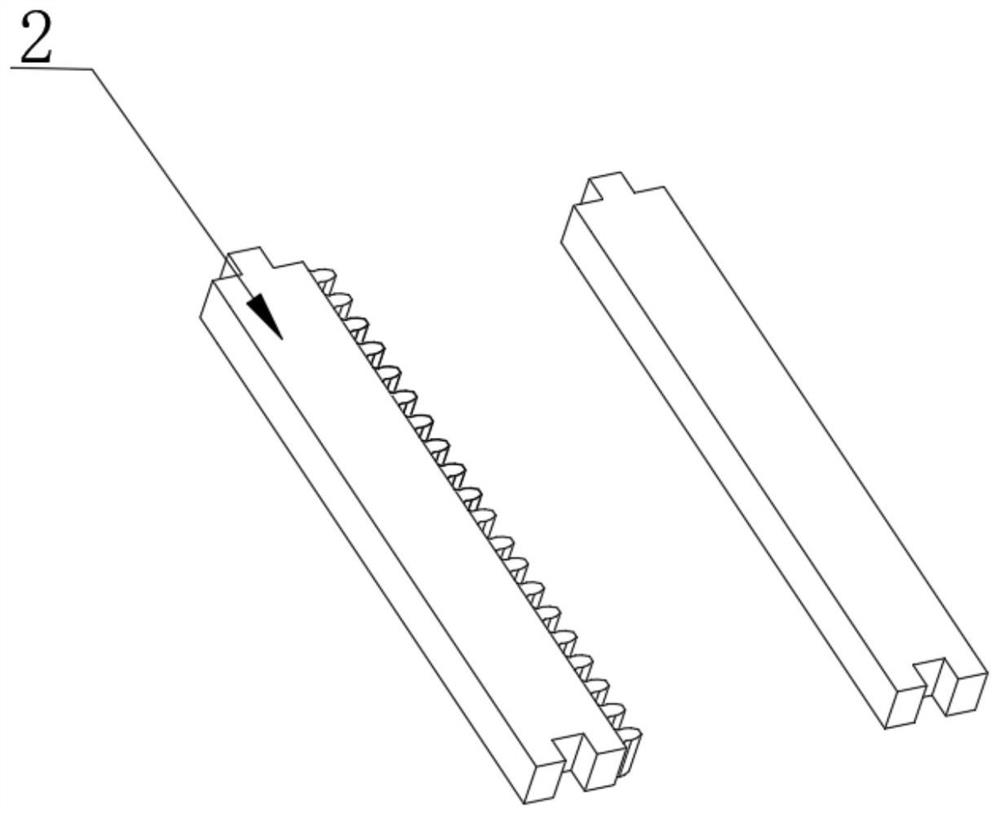
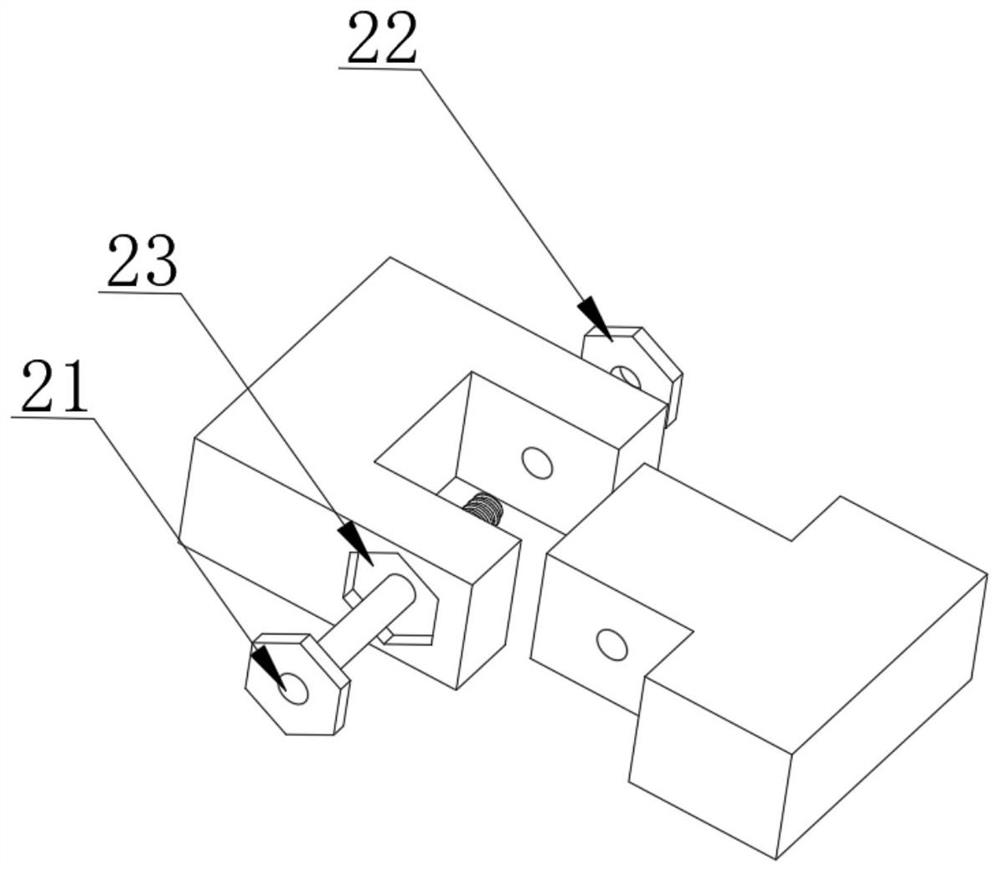
InactiveCN113334350AAvoid pollutionProtection precisionManipulatorStructural engineeringIndustrial robotics
The invention discloses an additional shaft guide rail structure of a universal industrial robot. The structure comprises a fixed steel block, a fixed base is welded to the side surface of the fixed steel block, a guide rail is welded to the top of the fixed steel block, a sliding block is placed at the top of the guide rail, a driving plate is fixedly mounted at the top of the sliding block, a robot mounting base is fixedly mounted at the top of the driving plate, a driving system is used for driving the driving plate, and a tightening system is used for tightening the sliding block along the guide rail. According to the structure, each important part is provided with a protection mechanism, a buffer device is arranged between the guide rail, and the bearing tightening device is arranged so that external interference is prevented, the precision of the system can be improved, the service lifetime of the system is prolonged, the operation cost is reduced, the length of the guide rail can be randomly increased and reduced in the later stage due to the structural characteristics of the guide rail, the operation is simple, and the practicability is high.
Owner:JIANGSU UNIV OF SCI & TECH
Painting management method based on block chain and NFC security identification technology
PendingCN110033059AImprove securityProtection precisionCo-operative working arrangementsDigital data protectionData connectionSide chain
The invention provides a painting management method based on a block chain and an NFC security identification technology, and the method comprises the following steps: S1, building a decentralized cloud storage platform system which is used for storing painting attribute information and carrying out distributed data storage and calculation, a block chain network system, and an application layer management system; setting a corresponding NFC label or QR code information on each specific picture; S2, uploading the attribute information of each specific painting to a block chain network system, wherein the block chain network system comprises a block chain main chain and a plurality of block chain side chains which are in data connection with the main chain and are divided according to different areas, uploading the related information of the painting to the block chain system to be stored, it can be well guaranteed that the information is not tampered at will, the painting safety degreeis improved, and the property rights and interests of consumers can be better protected.
Owner:深圳市步云科技有限公司
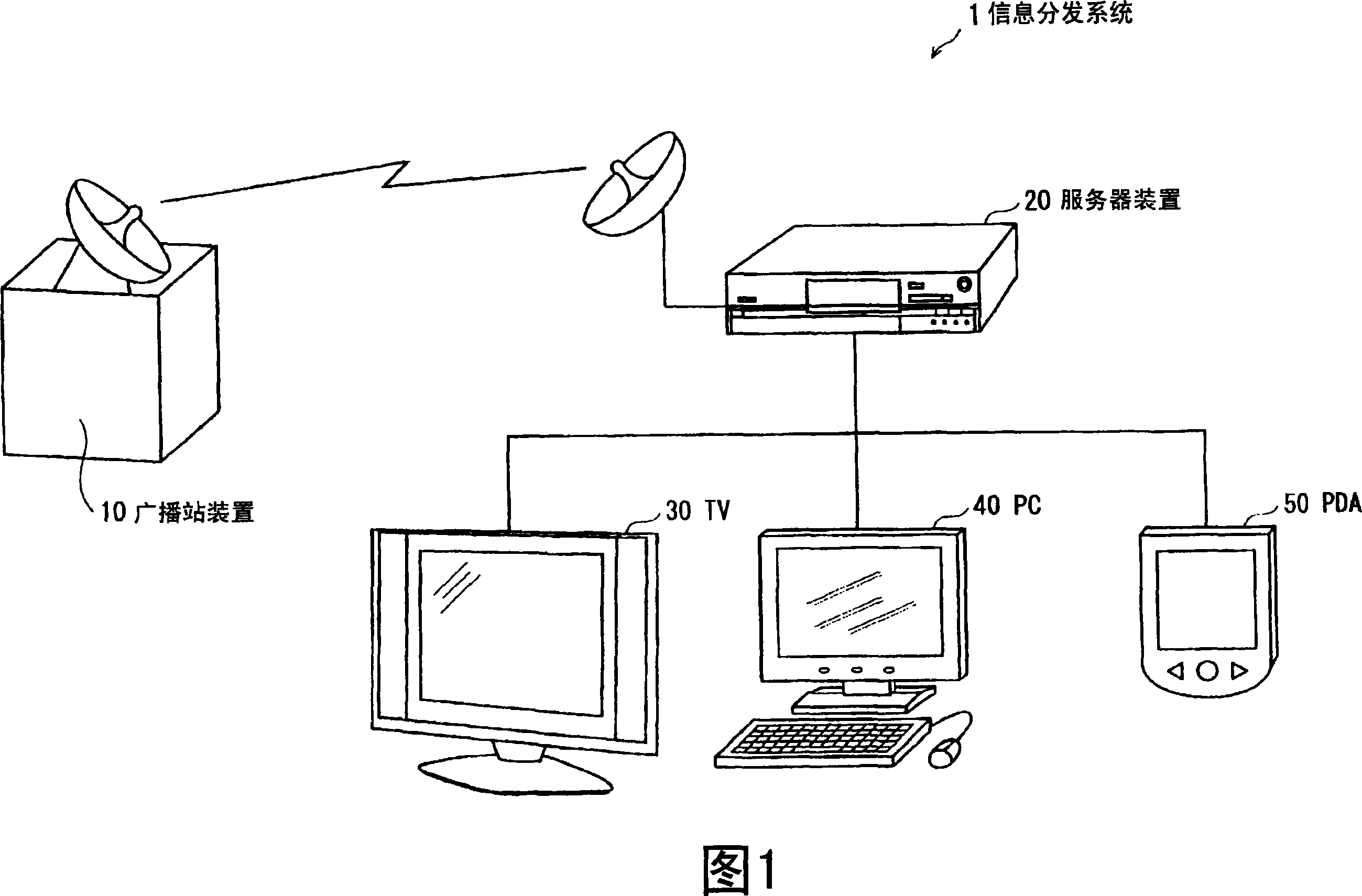
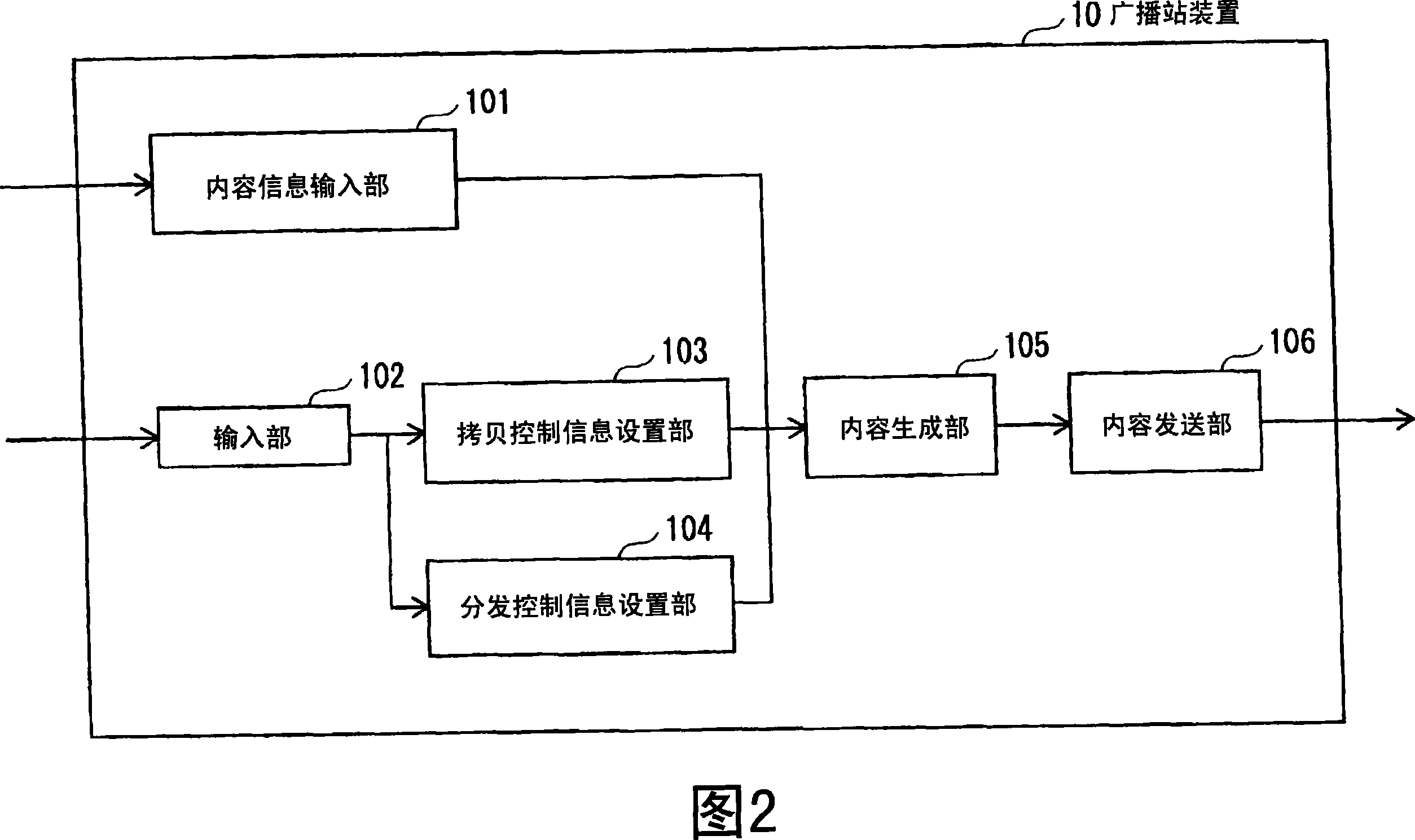
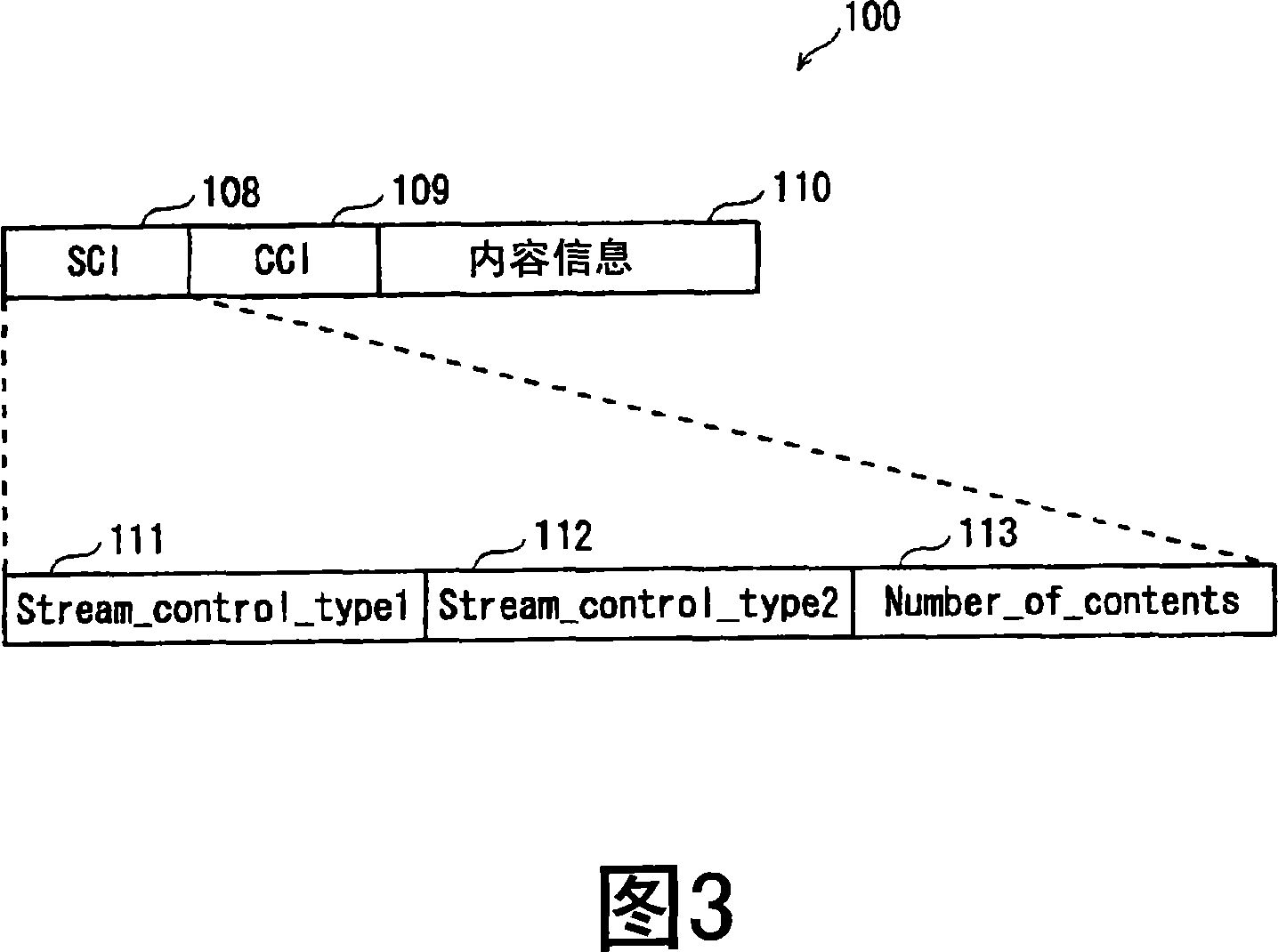
Information distribution device and information distribution method
InactiveCN101107853AProtection precisionConvenience guaranteedAnalogue secracy/subscription systemsComputer security arrangementsContent distributionDistribution control
In order to protect a content holder, a server device (20) holds distribution control information defining a content of the number of terminals to which the same part of the content can be simultaneously distributed. When a reproduction request of the content is received from a plurality of terminals, content distribution to the respective terminals is controlled without exceeding the number of terminals defined in the distribution control information.
Owner:PANASONIC CORP
Forage tumbling device capable of shaking off forage and sweeping off forage
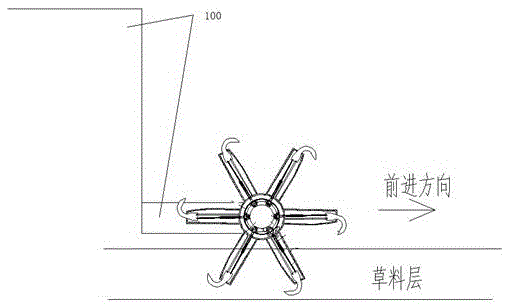
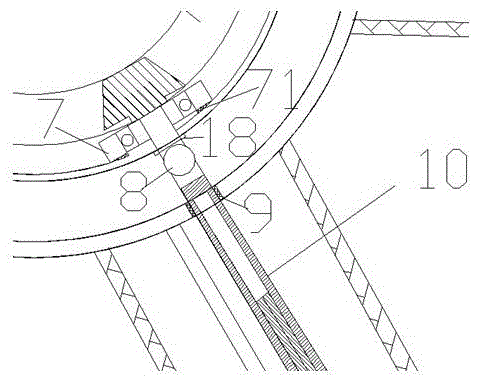
The invention provides a forage tedding device capable of shaking off forage and sweeping off forage. The forage tedding device comprises an executing part and a connecting part, wherein the executing part is used for executing the tedding operation, and comprises an outer supporting barrel (2), an inner supporting barrel (3) and six overturning hook parts (1), the overturning hook parts (1) are uniformly fixed on the cylindrical surface of the outer supporting barrel (2) along the circumferential direction, and the six overturning hook parts (1) are arranged on the cylindrical surface of the outer supporting barrel (2) along the circumferential direction in a manner that every two overturning hook parts are spaced from a 60-degree angle, so that the six overturning hook parts (1) are uniformly distributed on the cylindrical surface of the outer supporting barrel (2) along the circumferential direction.
Owner:江苏叠石桥家纺产业集团有限公司
Intelligent antitheft oil tank with automatic leakage stoppage warning function
ActiveCN109733187AHigh sensitivitySimple structureAnti-theft devicesLarge containersFuel tankOil storage
The invention provides an intelligent antitheft oil tank with an automatic leakage stoppage warning function. The intelligent antitheft oil tank comprises an oil tank body, a leakage stoppage controldevice, an oil quantity detecting device, a warning device, a leakage stoppage device and a leakage stoppage driving device, wherein the leakage stoppage driving device, the warning device and the oilquantity detecting device are connected with the leakage stoppage control device; the leakage stoppage driving device is connected with the leakage stoppage device; the leakage stoppage device comprises a leakage stoppage structure and a leakage stoppage containing container; the leakage stoppage containing container is arranged inside the oil tank body; and the leakage stoppage structure is arranged in the leakage stoppage containing container in a compression state. The oil quantity detecting device can be used for detecting the oil quantity in real time; the sensitivity is high; the leakage stoppage driving device and the leakage stoppage device are simple in structure; the leakage stoppage effect is good; the response is fast; fuel oil is prevented from being stolen at low cost; the property right and interests of vehicle owners are effectively protected; the labor cost for oil tank guarding is reduced; and the fighting on oil stealing crime is indirectly realized. The intelligentantitheft oil tank can also be used for burglary prevention on liquid in containers such as large-scale oil storage tanks.
Owner:QILU UNIV OF TECH
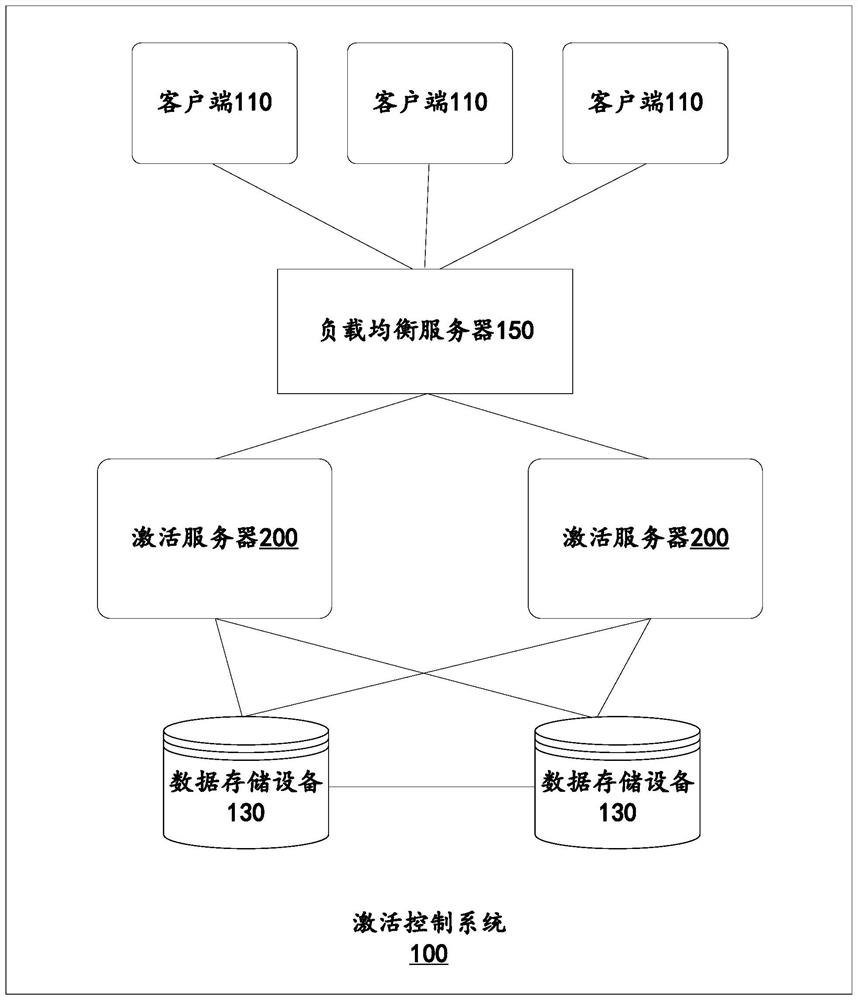
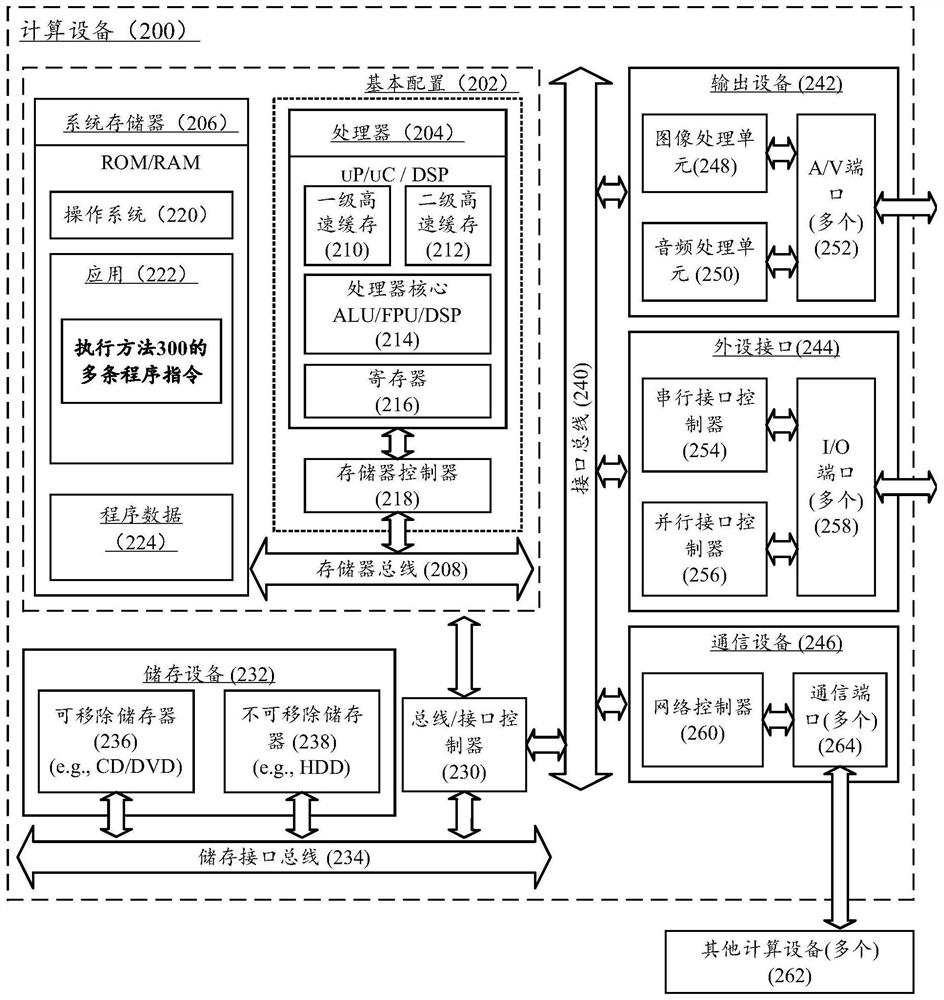
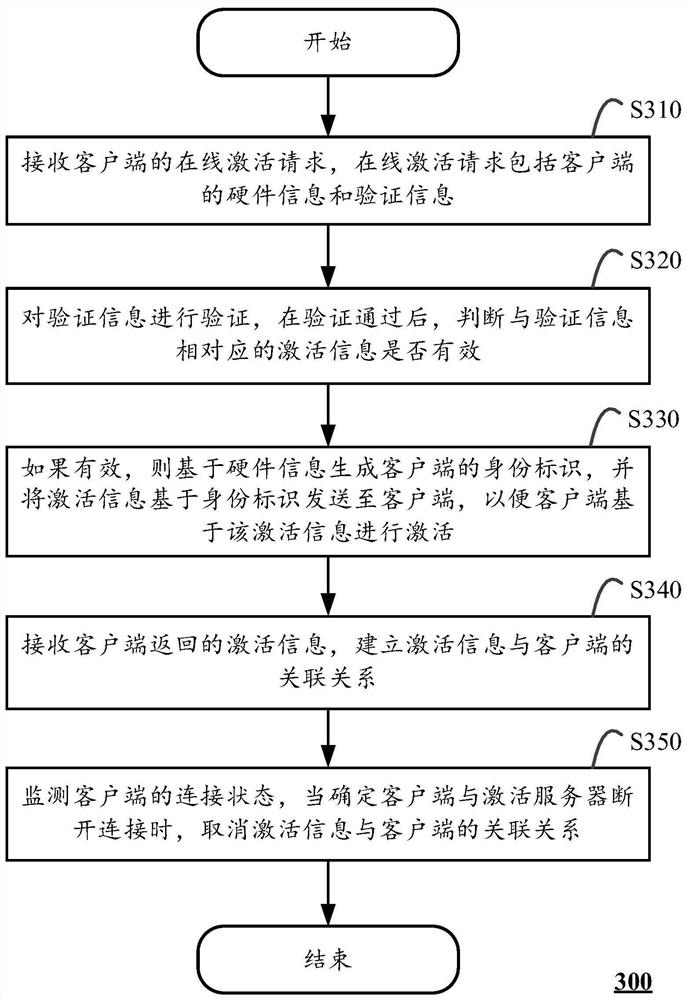
Activation control method and system and computing device
ActiveCN112866419AMaximize utilizationSave resourcesTransmissionComputer networkComputer engineering
The invention discloses an activation control method, which is executed in an activation server and comprises the following steps: receiving an online activation request of a client, the online activation request comprising hardware information and verification information of the client; verifying the verification information, and judging whether activation information corresponding to the verification information is valid or not after the verification is passed; if the activation information is valid, generating identity label of the client based on the hardware information, and sending the activation information to the client based on the identity label, so that the client can perform activation based on the activation information; receiving activation information returned by the client, and establishing an association relationship between the activation information and the client; and monitoring the connection state of the client, and cancelling the association relationship between the activation information and the client when determining that the client is disconnected from the activation server. The invention also discloses a corresponding system and a computing device. According to the technical scheme of the invention, the use efficiency of the activation code can be improved.
Owner:UNIONTECH SOFTWARE TECH CO LTD
Digital file sharing and content security protection method matched with mobile terminal authentication
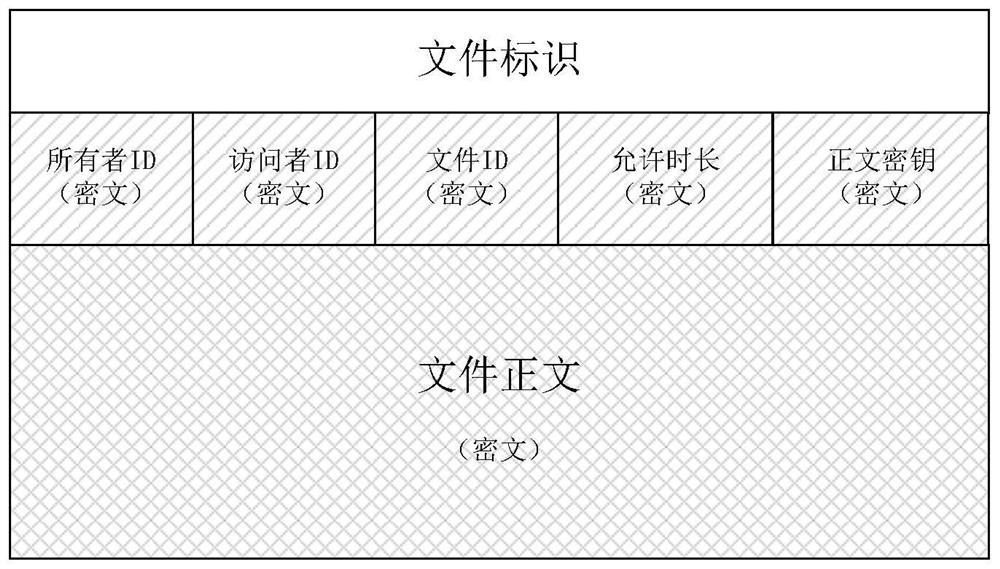
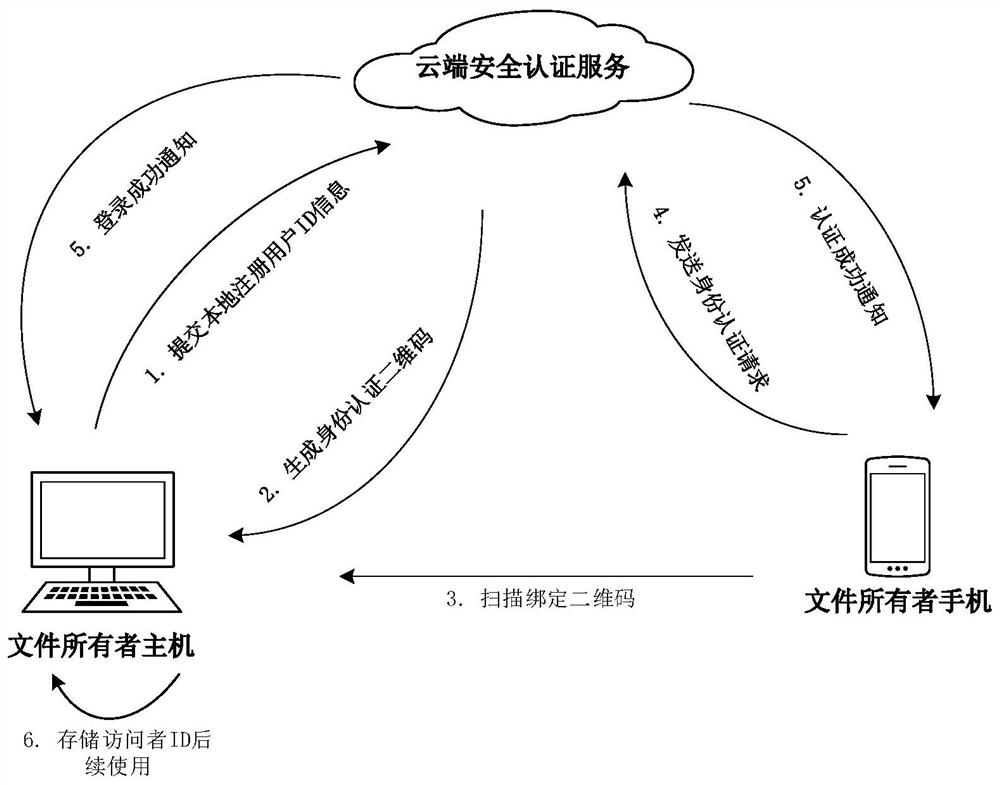
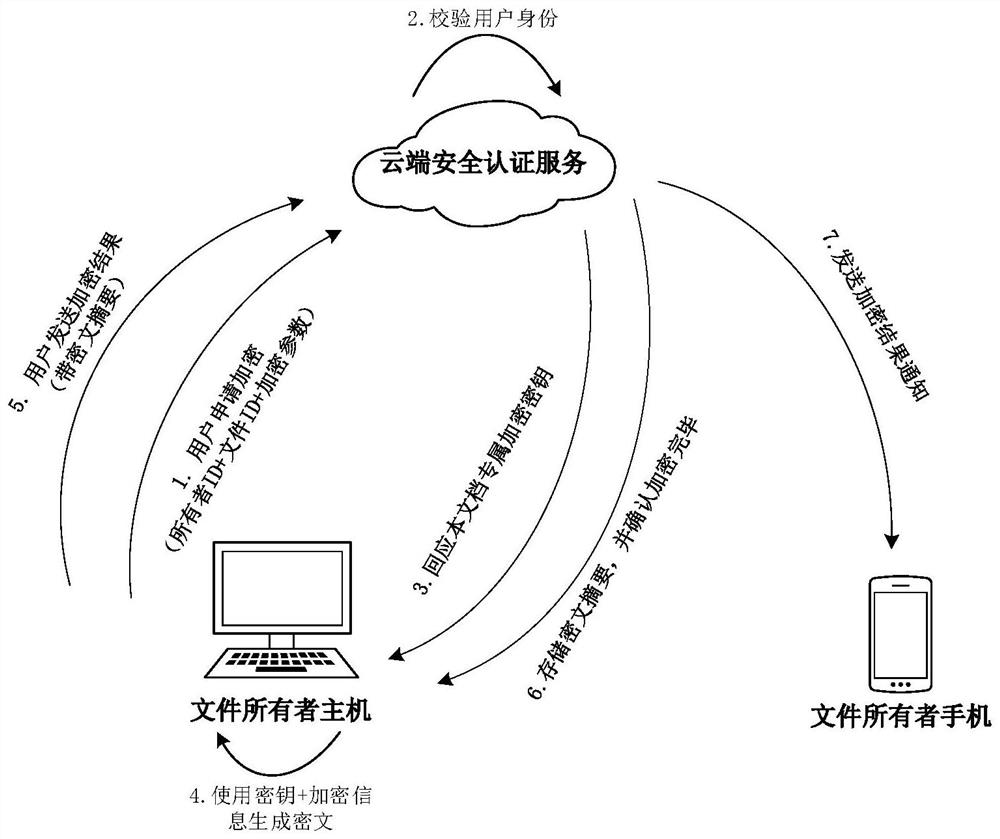
PendingCN113486376APromote disseminationPrevent leakageDigital data protectionPayment architectureCiphertextInternet privacy
The invention provides a digital file sharing and content security protection method matched with mobile terminal authentication, and relates to the field of computer information security. The method comprises the following steps: obtaining ciphertext information of an encrypted file by first host decryption software; if the user identity ID of the first host is inconsistent with both the owner ID in the ciphertext information and the visitor ID in the ciphertext information, or both the user identity ID of the first host and the visitor ID in the ciphertext information are empty, initiating a decryption application for the encrypted file to the cloud, and performing identity authentication on the cloud through the first mobile terminal; receiving a decryption permission returned by the cloud after the first host passes the identity authentication; opening the encrypted file in the memory based on the decryption permission and controlling the access duration; and if the access duration exceeds the allowed access duration, automatically closing the shared encrypted file. The method is matched with mobile terminal authentication and access duration control, so that the file can be conveniently spread on the Internet, and the benefit of a file owner can be protected.
Owner:大连九锁网络有限公司
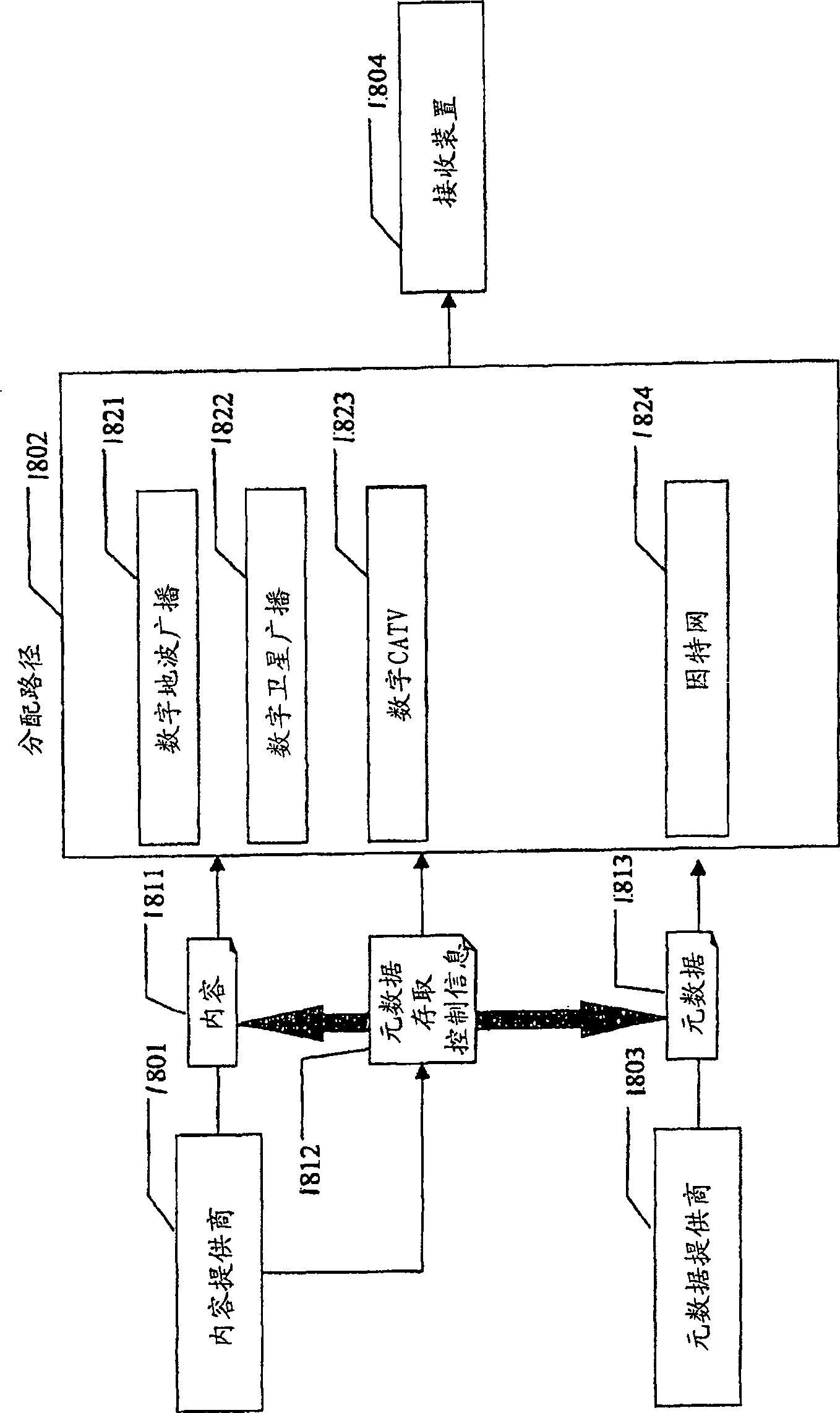
Meta data access control system, method thereof, reception device, and transmission device
Prevents the provision of metadata that is not permitted by the content-providing meta, and prevents the exploitation of content through metadata that is not the intent of the content-providing meta. The metadata checking unit checks metadata. The content checking unit checks the content and the providing element of the content. The metadata access control information checking unit checks the metadata access control information indicating the relationship between the content accessible to the content and the metadata, and at the same time checks the issuer of the metadata access control information. The metadata judgment unit performs metadata judgment on whether the content provider can trust the publisher of the metadata access control information. If it can be determined that the metadata is reliable, the metadata utilization unit utilizes the metadata.
Owner:PANASONIC CORP
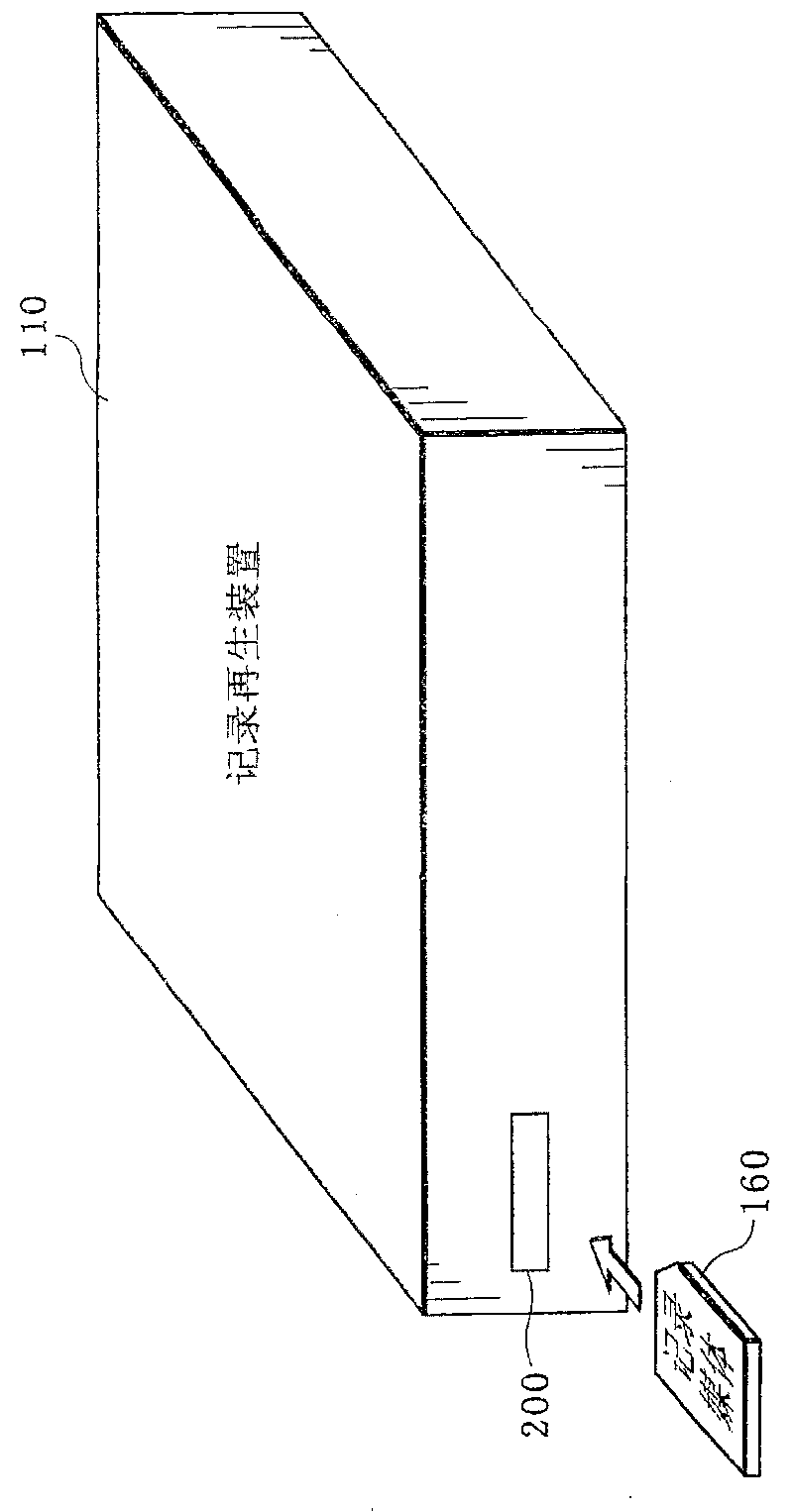
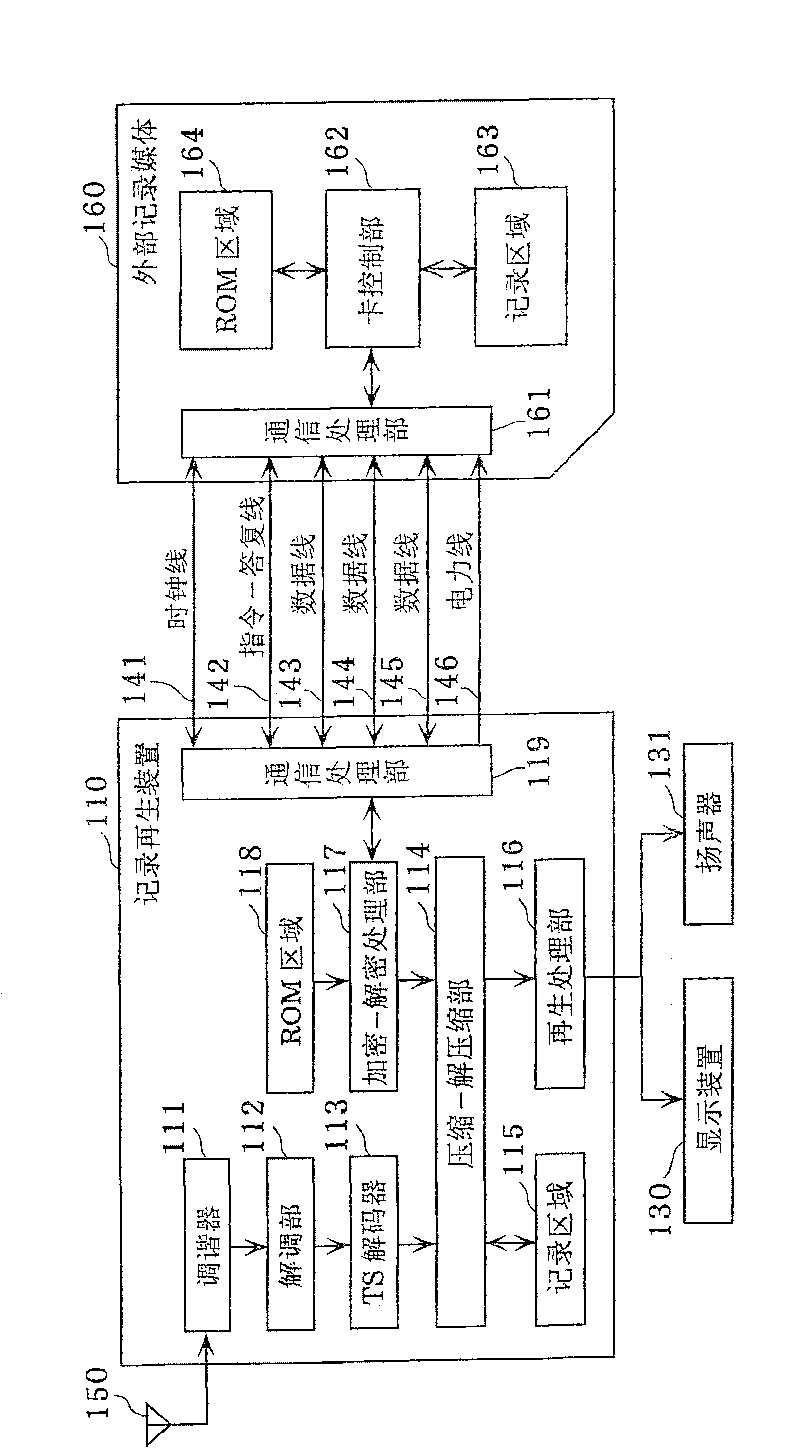
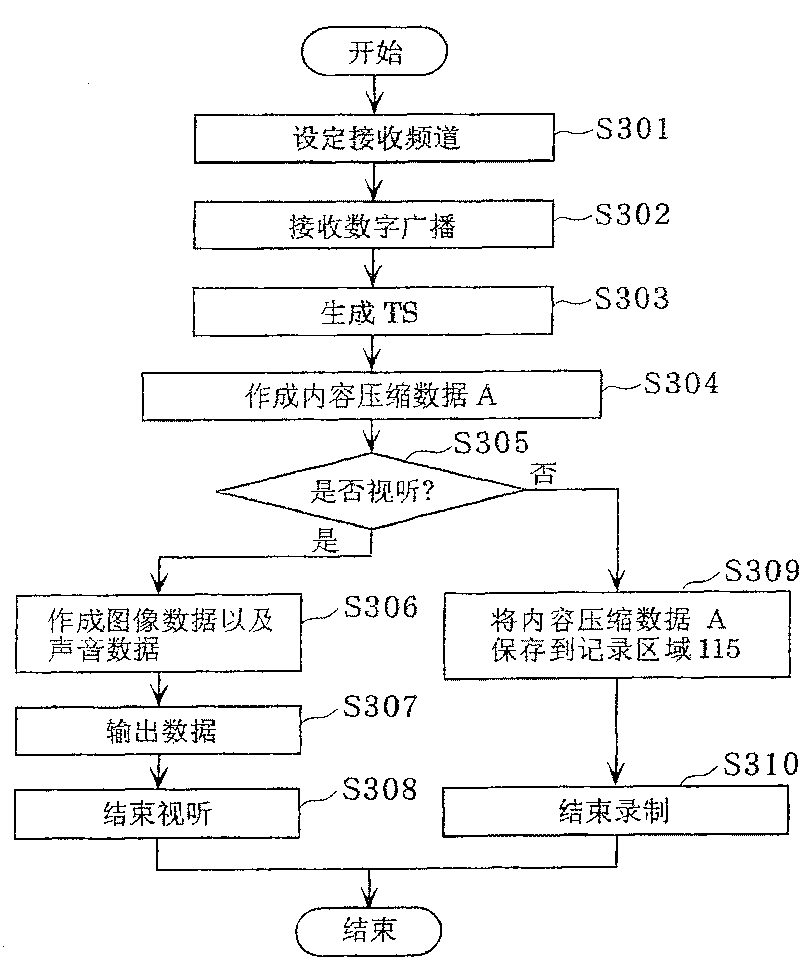
Recording/reproduction device
InactiveCN1965363BQuality improvementProtection precisionUnauthorized memory use protectionProgram/content distribution protectionComputer hardwareRecording media
The present invention provides a recording and reproduction device capable of preventing content having details identical to the details of outputted content from being reproduced simultaneously withthe outputted content, and allowing the content to be reproduced in high quality. A recording / reproduction device (110) includes a recording area (115), a communication processing unit (119) capable of outputting the related content having details identical to details of the content recorded in the recording area (115) into an external recording medium (160), and an encoding / decoding processing unit (117) capable of obtaining unique information of the external recording medium (160). The encoding / decoding processing unit (117) changes a state of content recorded in the recording area (115) into a state irreproducible unless using unique information of the content, when the related content is outputted to the external recording medium (160); then reproduces the content recorded in the recording area (115) using the unique information, when the encoding / decoding processing unit (117) obtains the unique information.
Owner:PANASONIC CORP
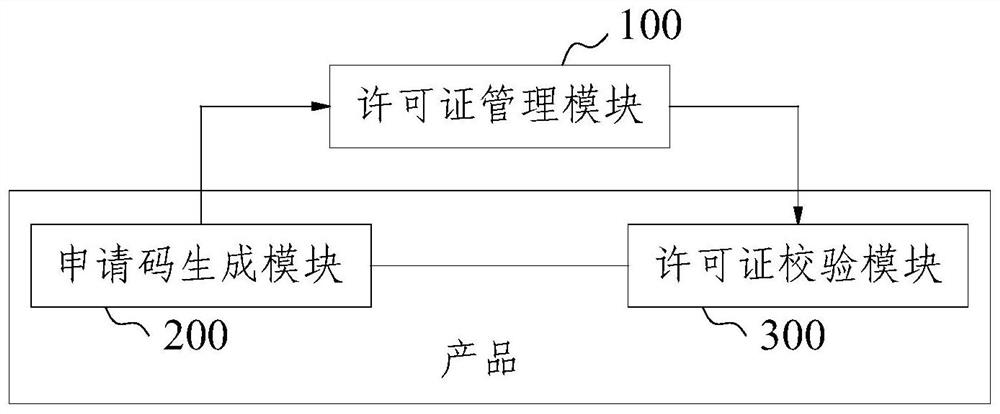
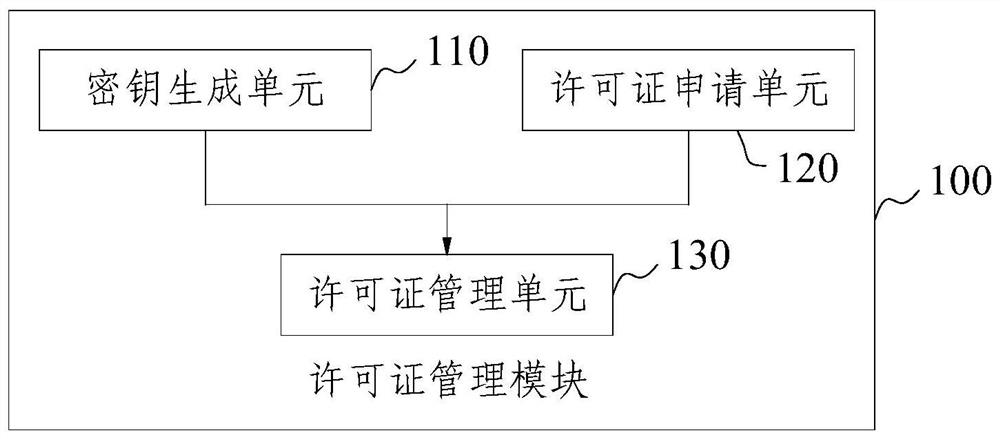
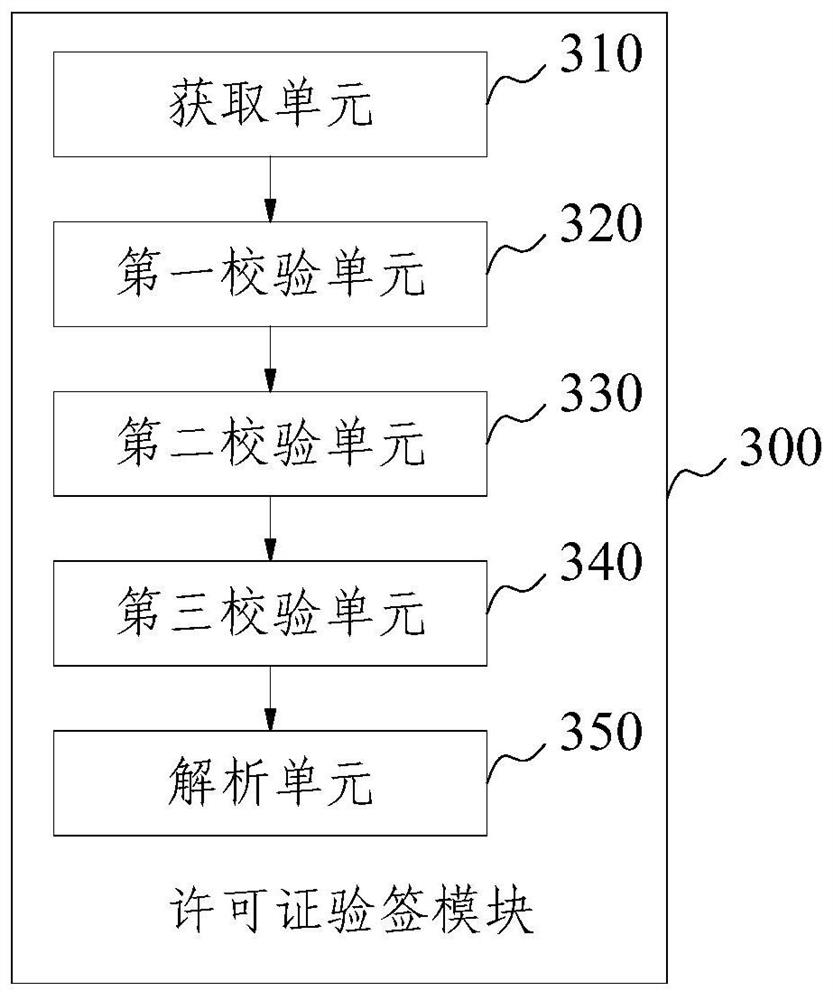
Software license verification system and method based on digital signature
The invention provides a software license verification system and method based on a digital signature, and relates to the technical field of digital signatures, and the system comprises a license management module which is used for generating an asymmetric key pair composed of a private key and a public key, obtaining application information, approving the application information based on the private key, and generating a software license after approval is passed; wherein the application information comprises an application code of the product, contract information and various restriction information of product use; the application code generation module and the license verification module are integrated in a product, the application code generation module is used for generating an application code, and the license verification module is used for obtaining a software license, a public key and application information, verifying the software license based on the public key, and verifying the application information based on current software and hardware information. The method can adapt to increasingly complex cloud service environments and effectively protect property rights of various software and hardware products in a software and offline implementation mode.
Owner:INSPUR SOFTWARE TECH CO LTD
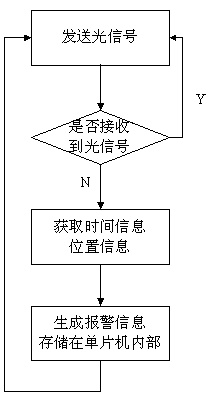
A protection system and packaging method for express parcels
ActiveCN106846519BProtect the safety of transportationProtection precisionFranking apparatusMicrocontrollerEngineering
Owner:NANJING INST OF TECH
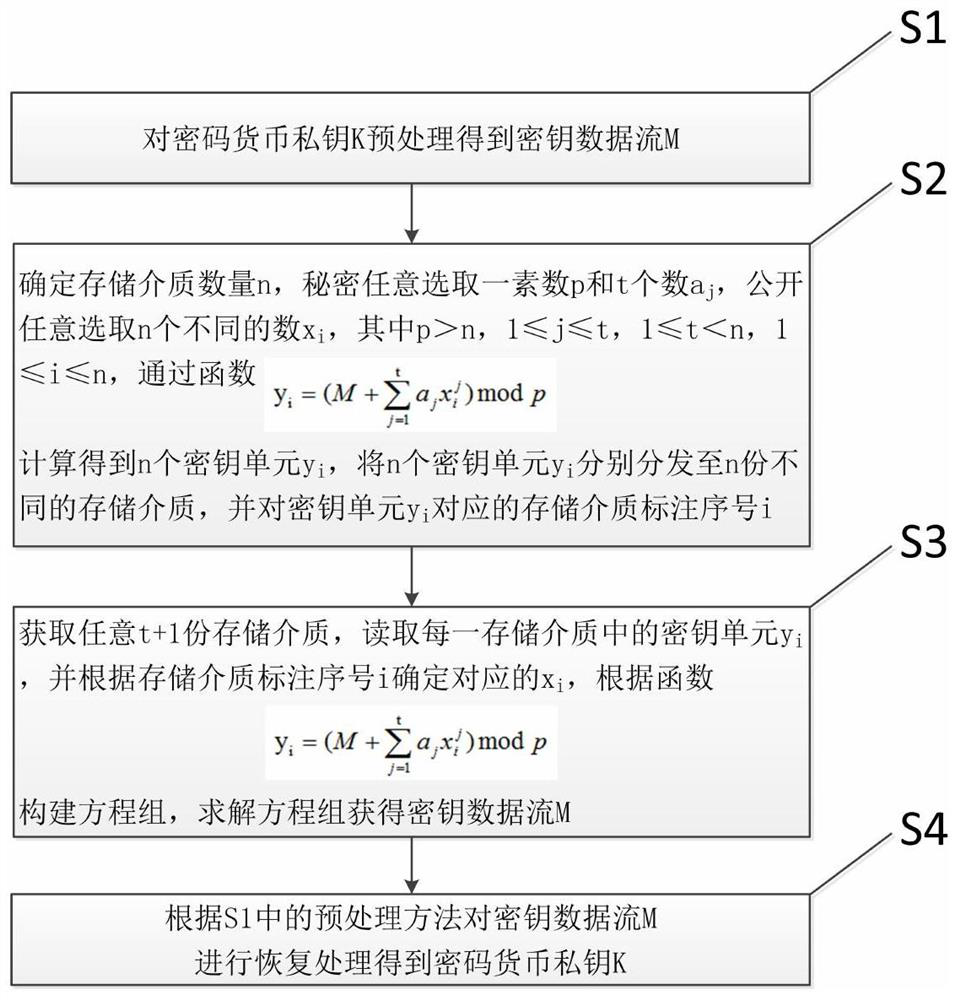
A method for protecting the private key of encrypted currency
ActiveCN108320143BImprove securityProtection precisionPayment protocolsPayment circuitsComputer networkData stream
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
Contents using device, and contents using method
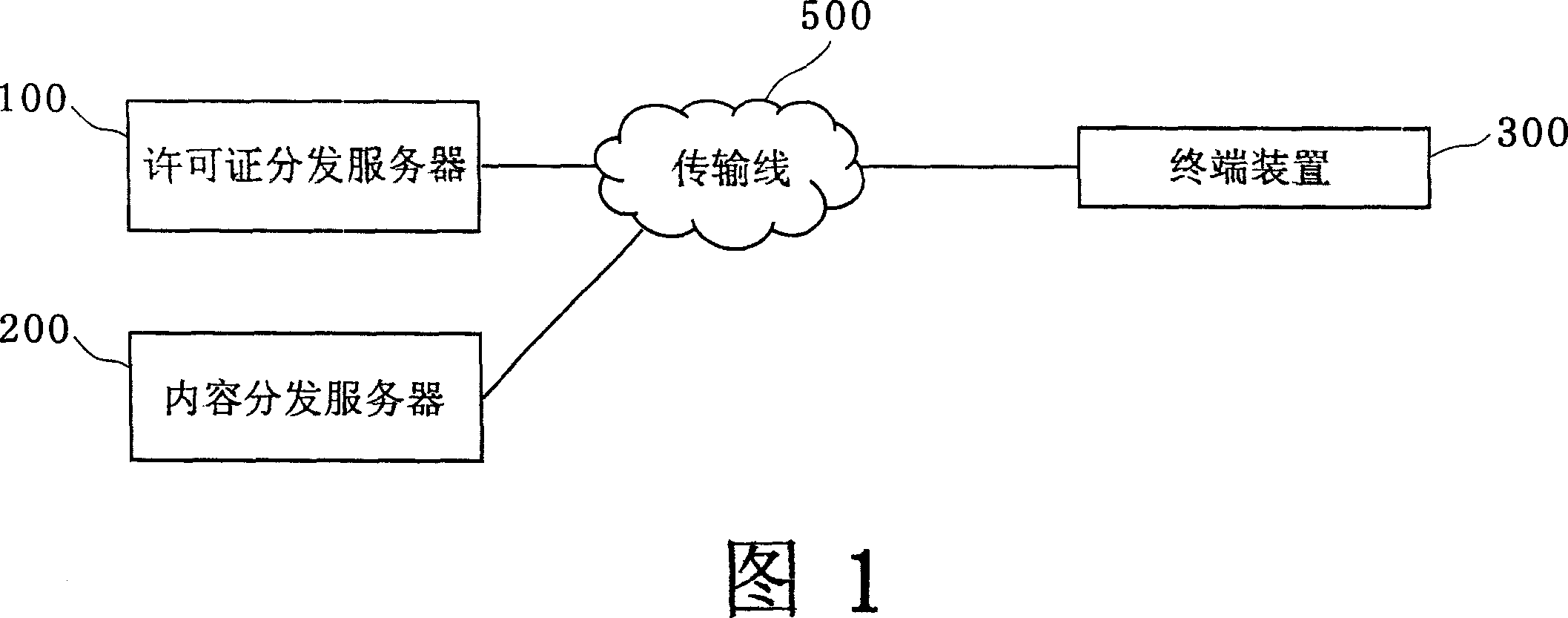
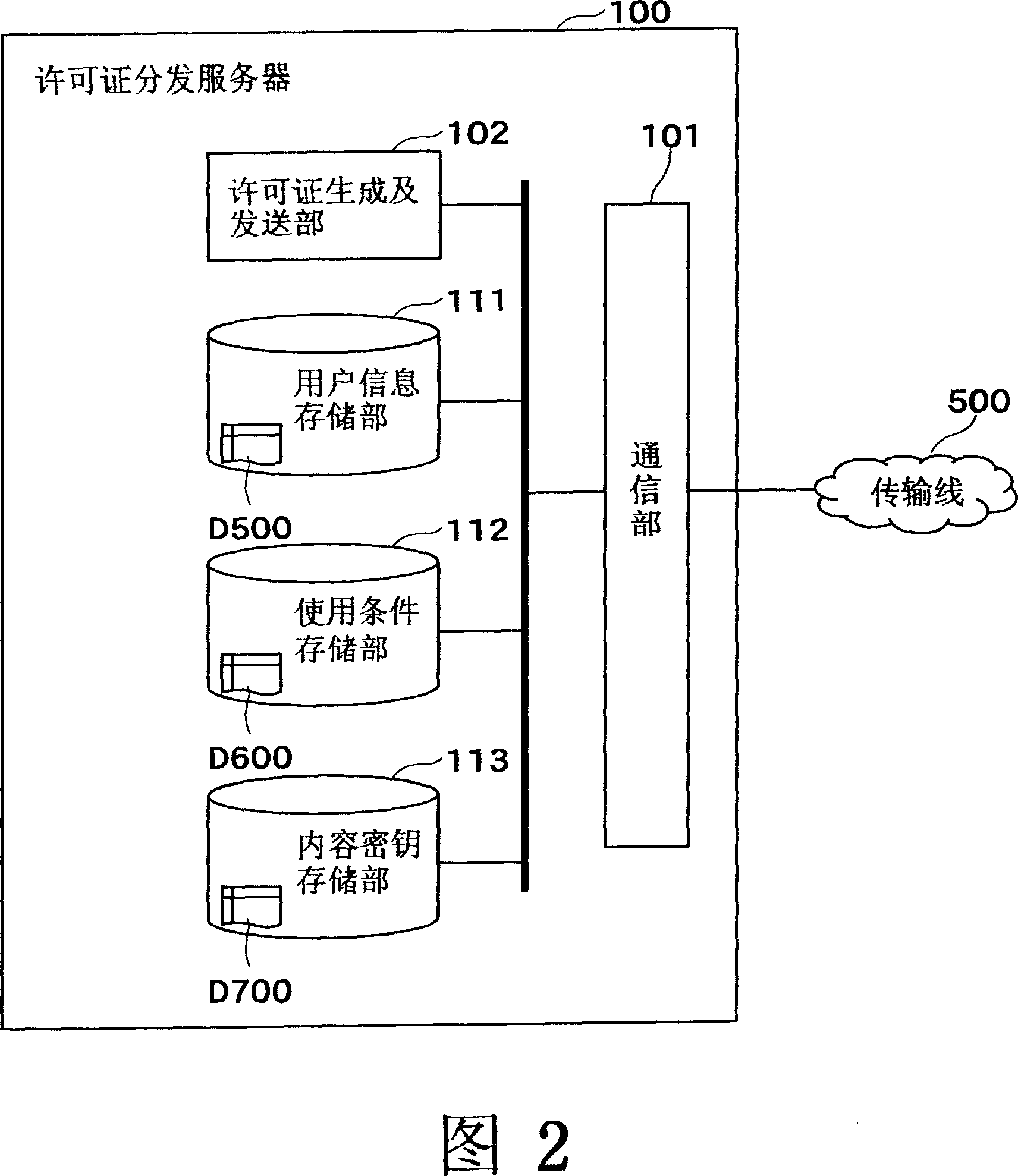
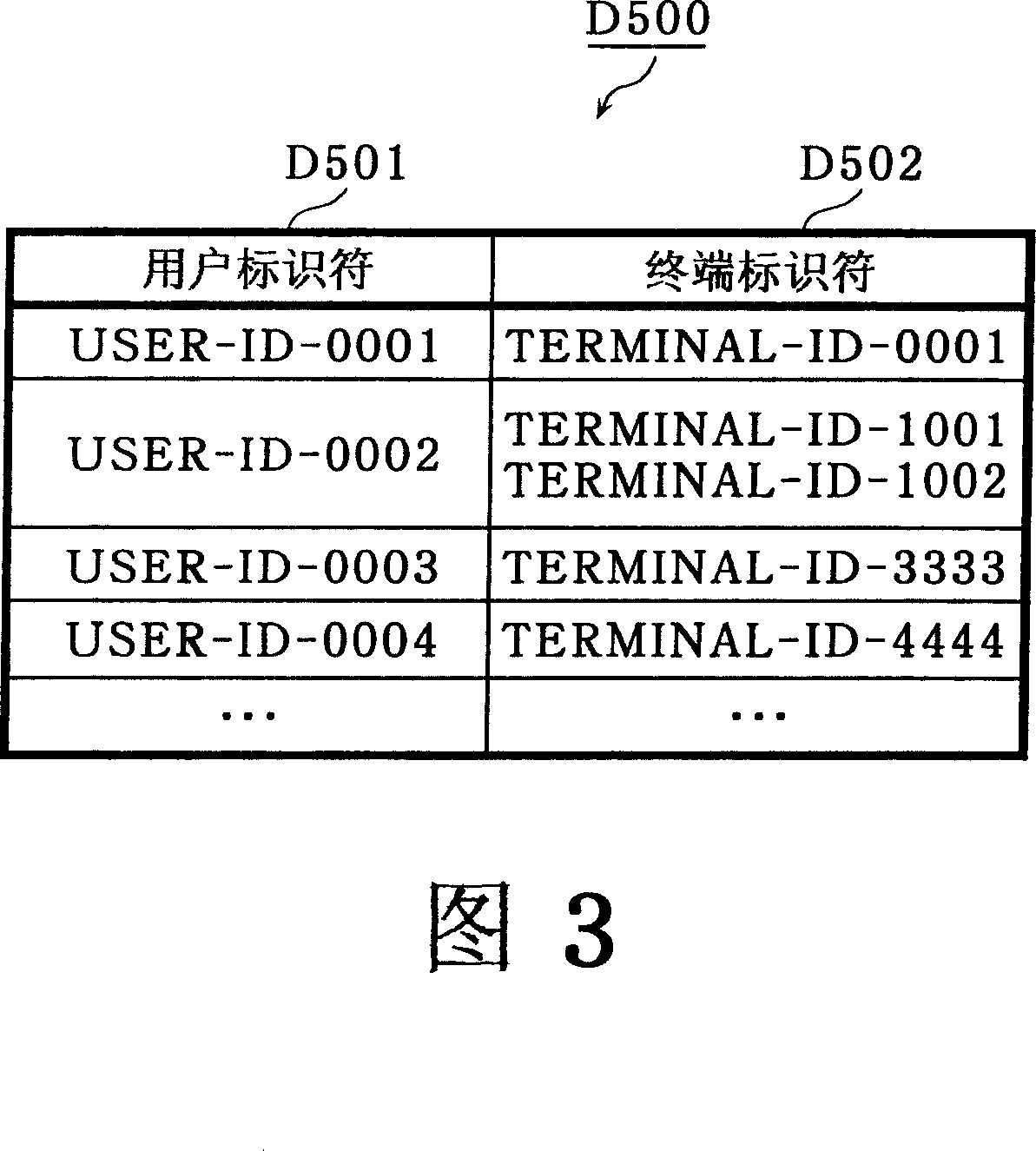
InactiveCN101052969AProtection precisionRestraining Improper Use of RightsDigital data protectionProgram/content distribution protectionLicense reinstatementTerminal equipment
A contents using device (or a terminal device) (300) comprises a license processing unit (305) for deciding a contents using propriety on the basis of a license using condition, a contents reproduction unit (304) for using the contents decided to be usable by the terminal device (300), limit means (or the contents reproduction unit (304)) for limiting the license corresponding to the contents so that the license cannot be used by another, because it is in use, for the time period after the contents reproduction unit (304) started the use of the contents and before the use is normally ended, an event detection unit (307) for detecting a predetermined event to forcibly quit the use of the contents having occurred for the time period from the start to the normal end of the use of the contents, limit relaxation propriety deciding means (or a recovery / penalty decision unit) (309) for deciding whether or not the predetermined event is contrary to the will of a user, and limit relaxing means (or a license recovery unit) (306) for relaxing the limit to the contents use in case the recovery / penalty decision unit (309) decided the contrary to the will of the user.
Owner:PANASONIC CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com