Rapid intelligent comparison and security detection method for big data of mobile malicious software
一种恶意软件、安全检测的技术,应用在电数字数据处理、计算机安全装置、计算机零部件等方向,能够解决错误率高等问题,达到保护产权和利益的效果
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
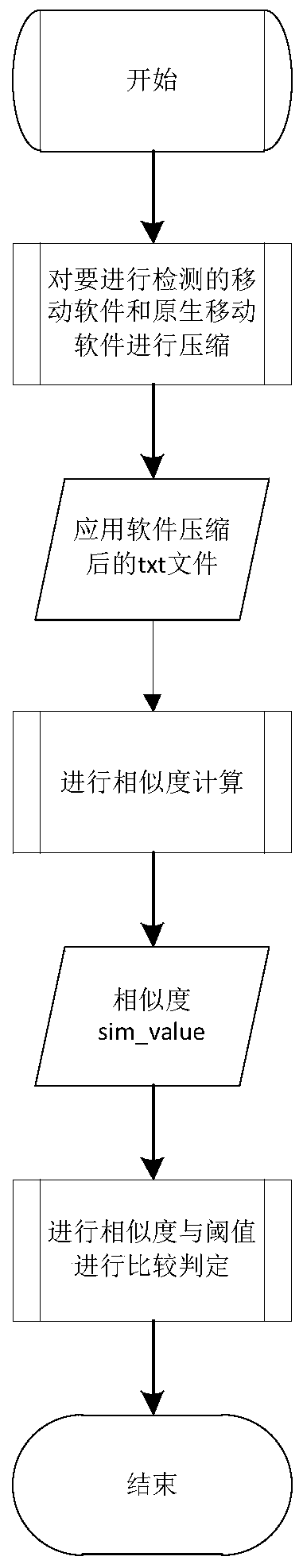
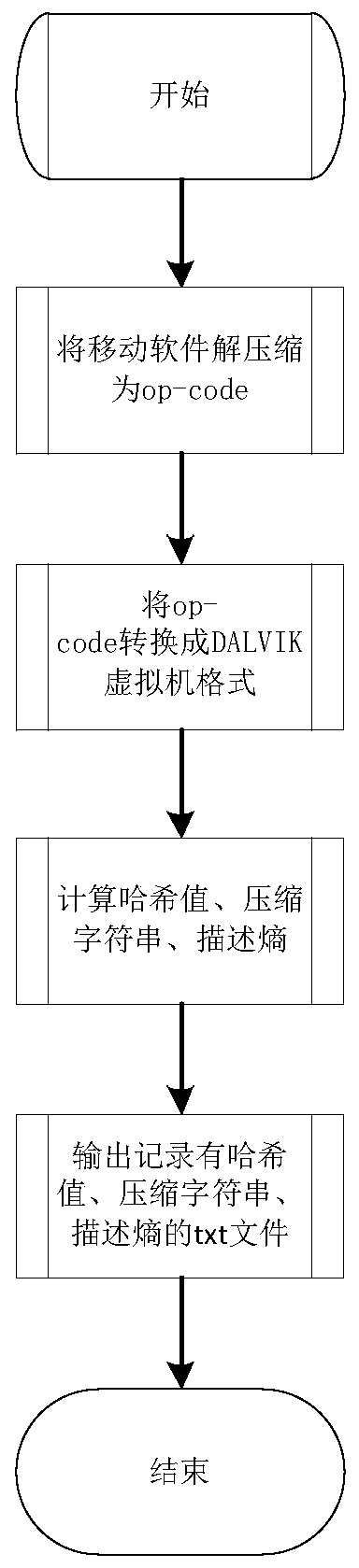
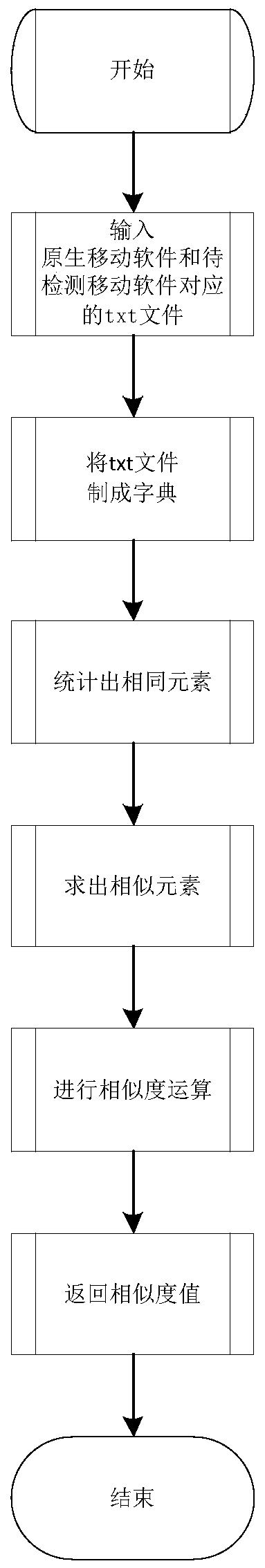
[0043] This embodiment discloses a fast intelligent comparison and security detection method for mobile malware big data. By combining compressed character strings, description entropy and function hash values, the Hdsim algorithm and the entropy_descpt_sim algorithm are proposed to calculate the similarity of mobile software. In order to determine whether the mobile software is a repackaged program, whether it contains malicious attack code;
[0044] The function hash value is the unique identifier of the function. The equal hash value of two functions means that the functions of the two functions are the same, that is, the two functions are the same;
[0045] The entropy describes the semantic structure of a string and the degree of disorder of the subsequence in the entire sequence, and it also defines the abstract state of the combination and distribution of the sequence;
[0046] The compressed string is the compression of the expression in the function, one statement cor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com