Hardware circuit encryption device realized through CPLD
An encryption device and hardware circuit technology, which is applied in computer security devices, electrical digital data processing, instruments, etc., can solve the problems of complex structure, cost increase, and increase in the size of the main board of the business gateway hardware circuit, and achieve good encryption effect , low cost, good effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
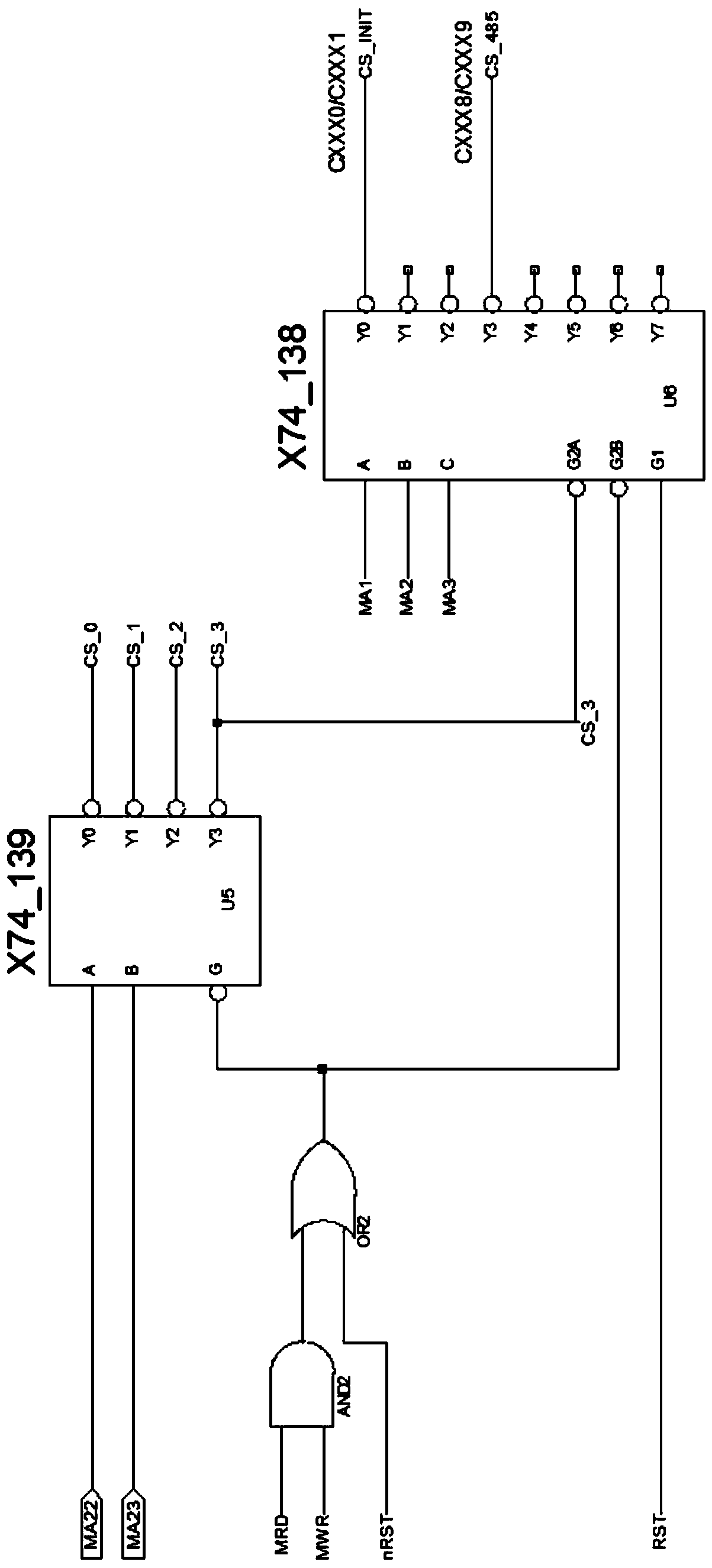
[0018] Specific implementation mode one: combine Figure 1 to Figure 3 This embodiment will be described. The hardware circuit encryption device implemented by CPLD described in this embodiment is suitable for CPLD, and the device includes a decoding module, a password writing module and a communication channel control module.
[0019] Such as figure 1 As shown, the decoding module is a gate circuit decoder realized by a 24 decoder and a 38 decoder, and is used for address decoding of input addresses MA23, MA22, MA3, MA2, MA1; The decoding module specifically includes an AND gate, an OR gate, a 24 decoder and a 38 decoder; the two input terminals of the AND gate are respectively used to receive the read control signal and the write control signal, and the output terminal of the AND gate One input end of the OR gate is connected, the other input end of the OR gate is used to receive the reset signal, and the output end of the OR gate is simultaneously connected with an enable...
specific Embodiment approach 2
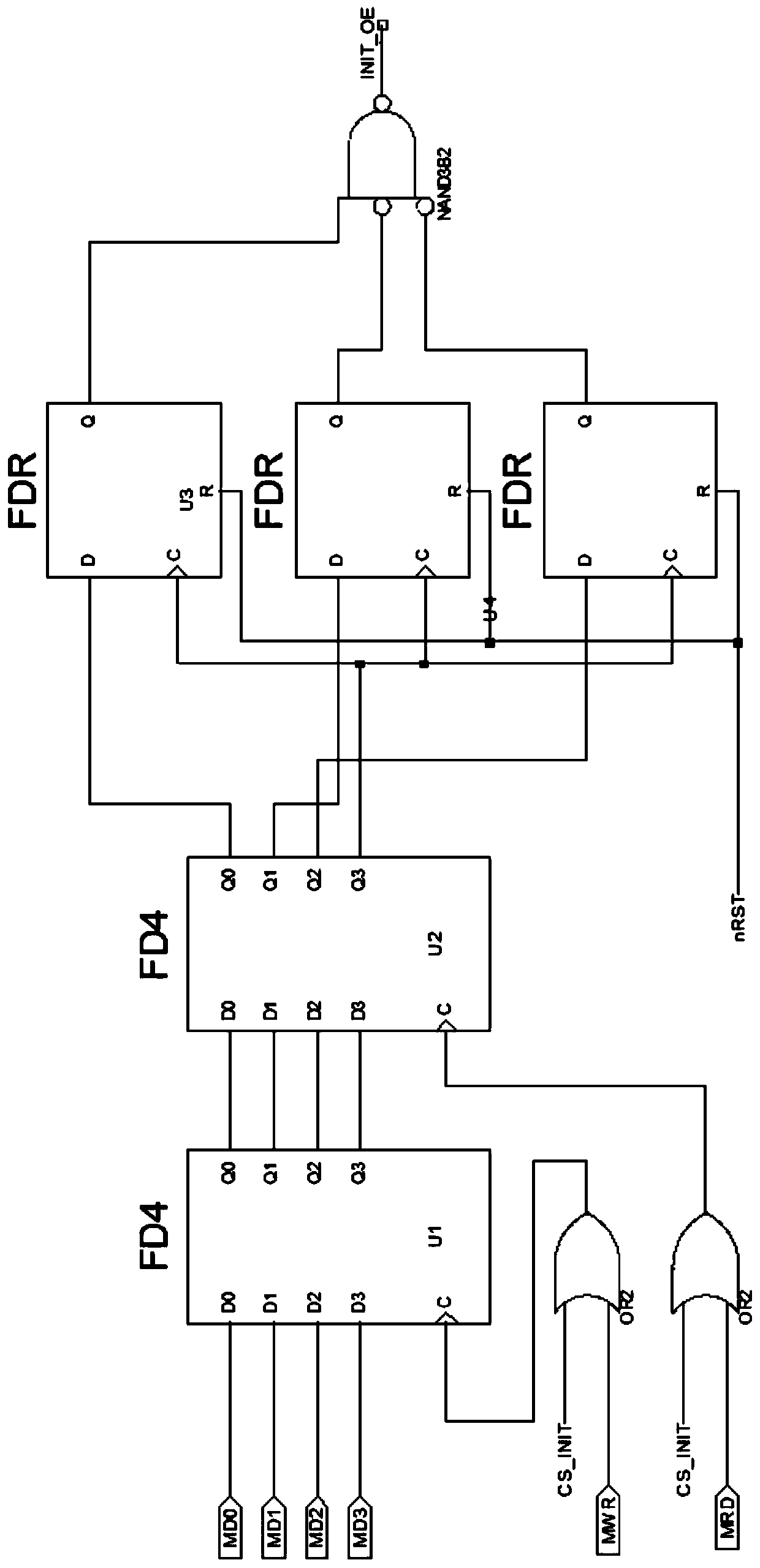
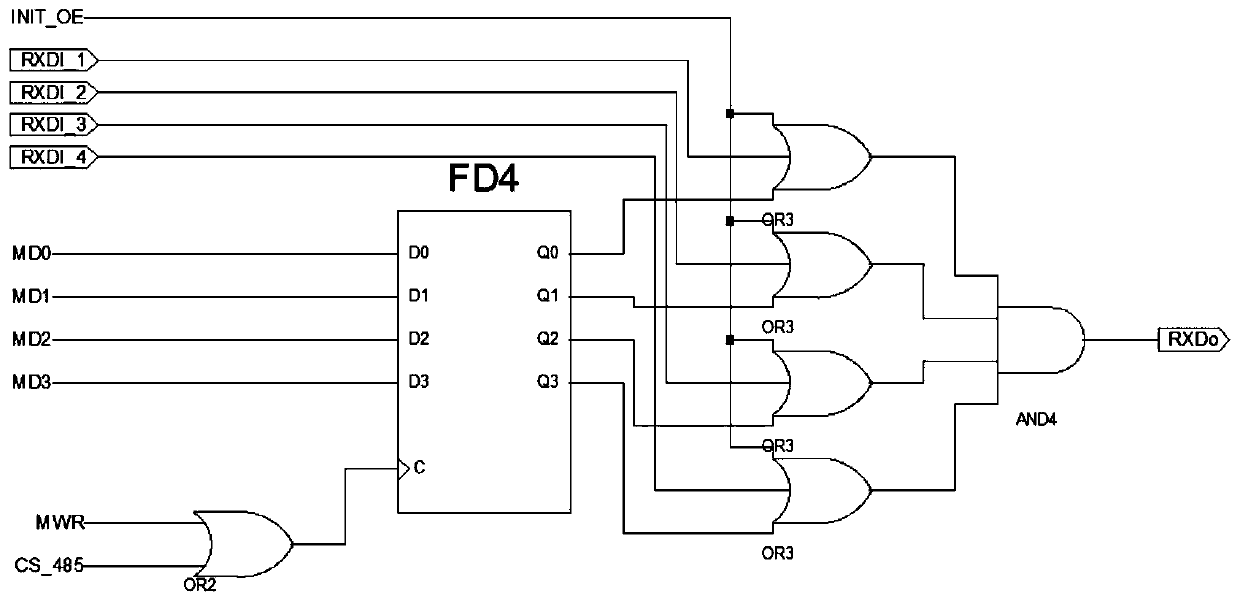
[0028] Specific implementation mode two: combination Figure 1 to Figure 4 This embodiment will be described. In order to realize the confidential control of the internal logic of the CPLD chip so that external programs cannot control the entire product, this embodiment provides an encryption method that cooperates with the above encryption device, and the encryption method is implemented by a computer program embedded in the CPU.
[0029] Such as Figure 4 As shown, the encryption method includes the following steps:
[0030] When the enable signal CS_INIT changes from high level to low level, the preset data 1 goes to IO port MD0, the preset data 0 goes to IO port MD1, the preset data 0 goes to IO port MD2, and the preset data 1 goes to IO port MD2. On the IO port MD3;
[0031] Write data to the occupied address 0CXXX0h or 0CXXX1h;
[0032] Read data from the occupied address 0CXXX0h or 0CXXX1h;
[0033] Preset data 1 to IO port MD0, preset data 0 to IO port MD1, preset...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com