Micro blog secluded key user analysis method based on topic transferring entropy
A key user and analysis method technology, applied in special data processing applications, instruments, electrical digital data processing, etc., can solve the problems of low recognition of hidden key users, unsuitable analysis, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044]In order to make the purpose, technical solution and advantages of the present invention more clear and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions.
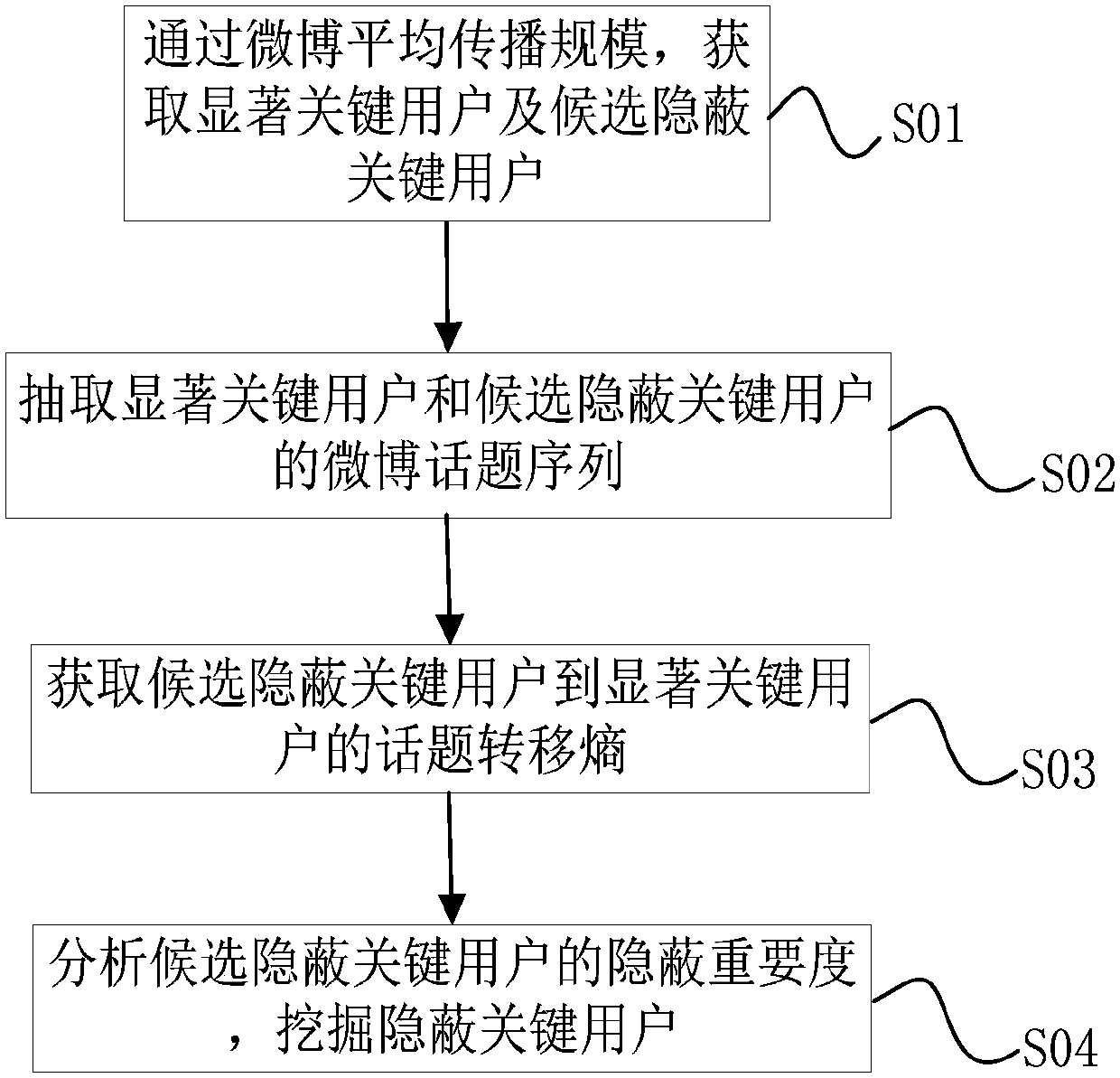
[0045] The analysis of key users on the microblog network mostly relies on the retweeting relationship automatically marked by the microblog system, which is not suitable for analyzing key users whose importance is relatively hidden, such as the behind-the-scenes manipulators who hype microblogs, and the direct forwarding of microblogs and other behaviors are very difficult. It is difficult to find such users. For this reason, embodiment one of the present invention, see figure 1 As shown, a microblog concealed key user analysis method based on topic transfer entropy is provided, including:
[0046] S01) Obtain significant key users and candidate hidden key users through the average spread scale of Weibo;
[0047] S0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com