Blockchain evidence storage method and device
A technology of chain storage and blockchain, which is applied in the field of blockchain, can solve problems such as the inability to guarantee the originality of evidence files
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
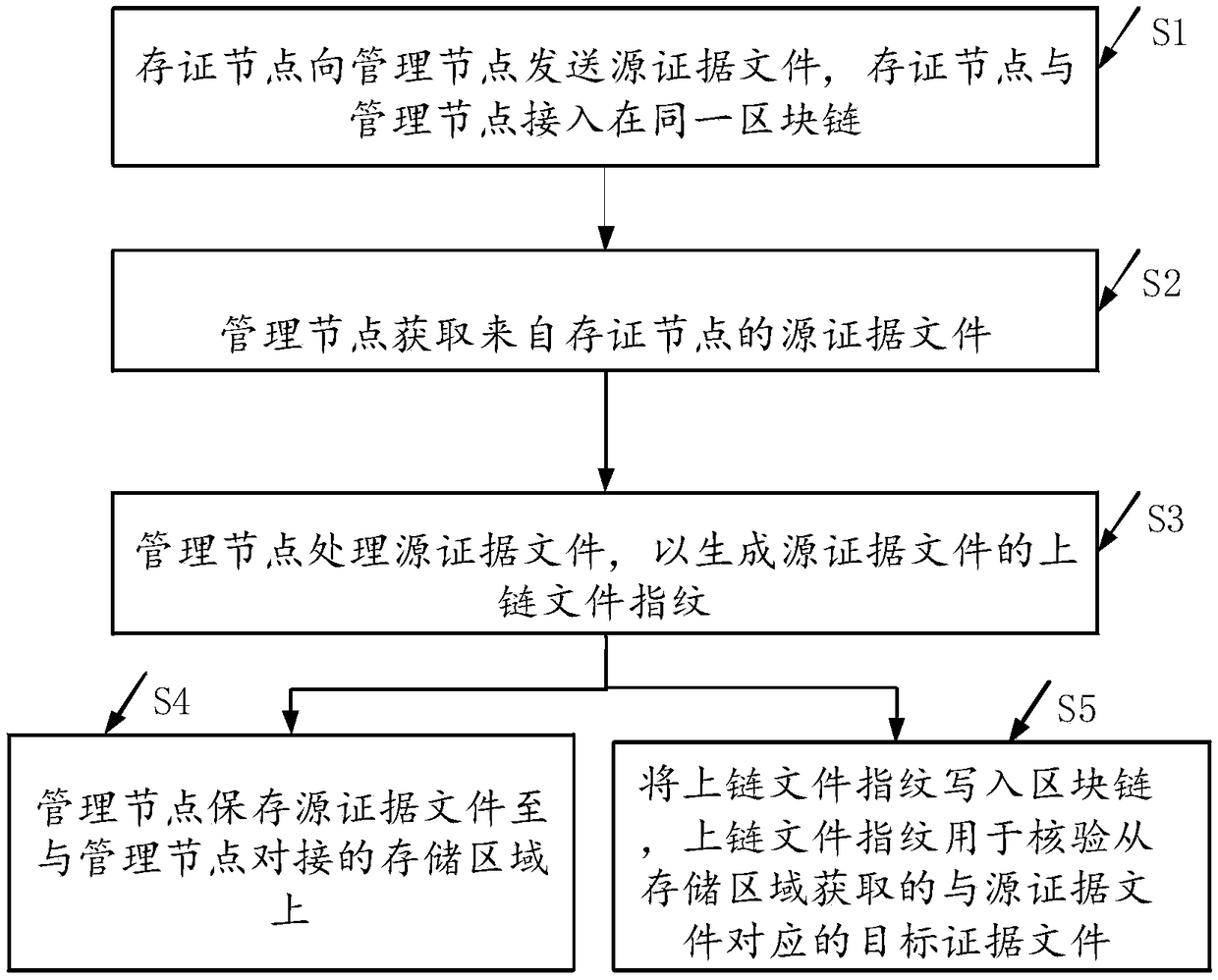
[0142] After step S8, after the management node issues the target evidence file extracted from the storage area to the forensic node, the forensic node determines whether verification is required. For verification, a verification request is initiated to the management node, and the verification request carries the target evidence file issued by the management node, so that the management node verifies the target evidence file from the forensic node through the following process:
[0143] Step 1. The management node receives the verification request from the forensic node, and extracts the target evidence file from the verification request, and the forensic node is connected to the blockchain.
[0144] According to the target evidence file uploaded by the user to the management node on the verification interface of the evidence acquisition node, the evidence acquisition node sends the target evidence file of the management node to the management node, and requests the management...
Embodiment approach 2
[0153] Implementation Mode 2: The management node can verify the evidence files extracted from the storage area before the management node sends the evidence files extracted from the storage area to the forensics node. The specific implementation process is as follows:
[0154] Step 1': the management node obtains the first forensic evidence for extracting the target evidence file from the forensics node, and the forensics node is connected to the block chain;
[0155] Step 2': the management node extracts the evidence file from the storage area according to the first evidence collection certificate, and obtains the on-chain file fingerprint of the source evidence file from the block chain according to the first evidence collection certificate;
[0156] Step 3': The management node verifies the target evidence file according to the fingerprint of the file on the chain, and obtains the verification result of the target evidence file;
[0157] Step 4': The management node sends ...
Embodiment approach 3
[0164] Embodiment 3. The forensics node can verify the evidence files extracted by the management node from the storage area. The implementation process is as follows:
[0165] Step 1": The management node obtains the second forensic credential from the forensic node for extracting the target evidence file. Specifically, the first forensic credential may be the same as the first forensic credential, for example, the evidence number of the target evidence file.
[0166] Step 2": the management node extracts the target evidence file from the storage area according to the second evidence collection credential.
[0167] Step 3": The management node generates the fingerprint of the file to be verified according to the target evidence file. Specifically, the fingerprint of the file to be verified is generated in the same way as the fingerprint of the file on the chain. The fingerprint of the file to be verified is: based on the same method of generating the fingerprint of the file on...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com