A method for encrypting and decrypting electronic government affairs
An e-government and coding technology, which is applied to electrical components and key distribution, can solve problems such as the inability to achieve single sign-on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
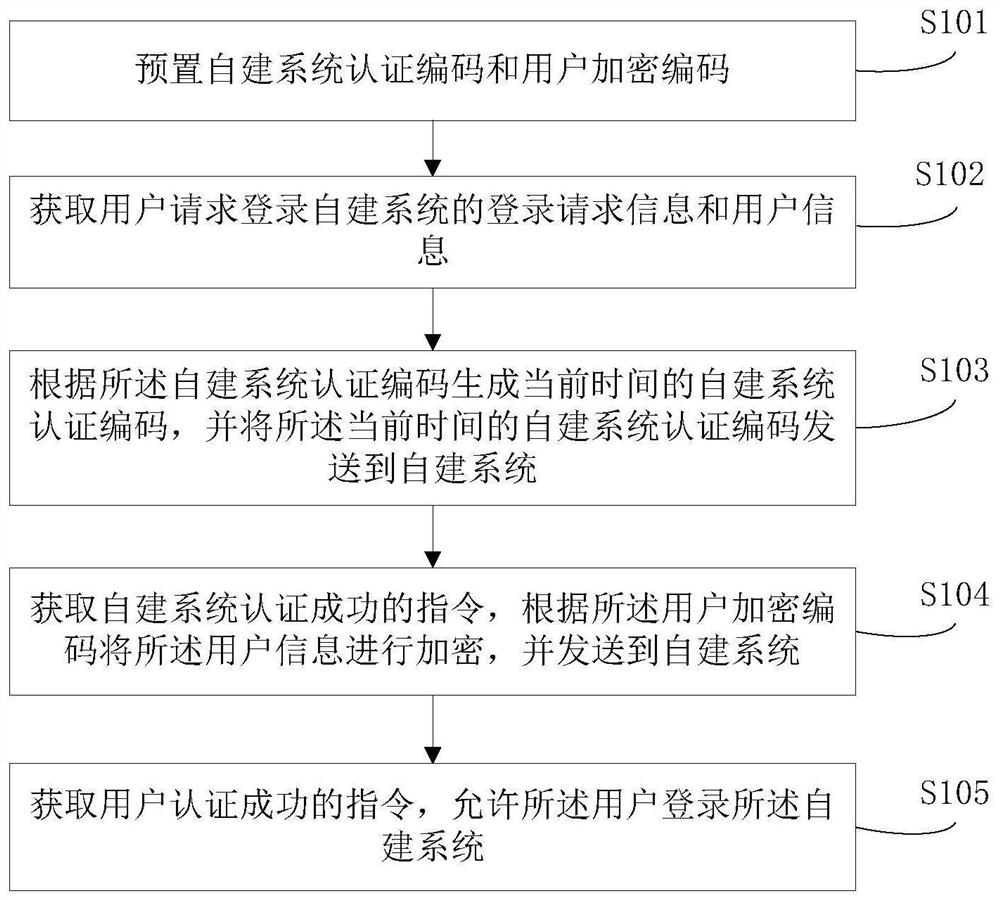
[0051] figure 1 Shown is a flowchart of a method for encrypting e-government affairs according to an embodiment of the present invention, and the method includes steps:
[0052] S101, presetting the self-built system authentication code and user encryption code;
[0053] The self-built system refers to the system built by each government department, which is the decryption terminal of the present invention;
[0054] In the e-government unified identity authentication system, the encryption end is generally placed in the government service network, and the decryption end is placed in the self-built system;
[0055] The government service network (that is, the encryption terminal) gathers all government service items, and each government service item corresponds to a different self-built system. By logging into the government service network, the user selects the self-built system where the government service item needs to be handled, and Enter the corresponding user name and ...
Embodiment 2
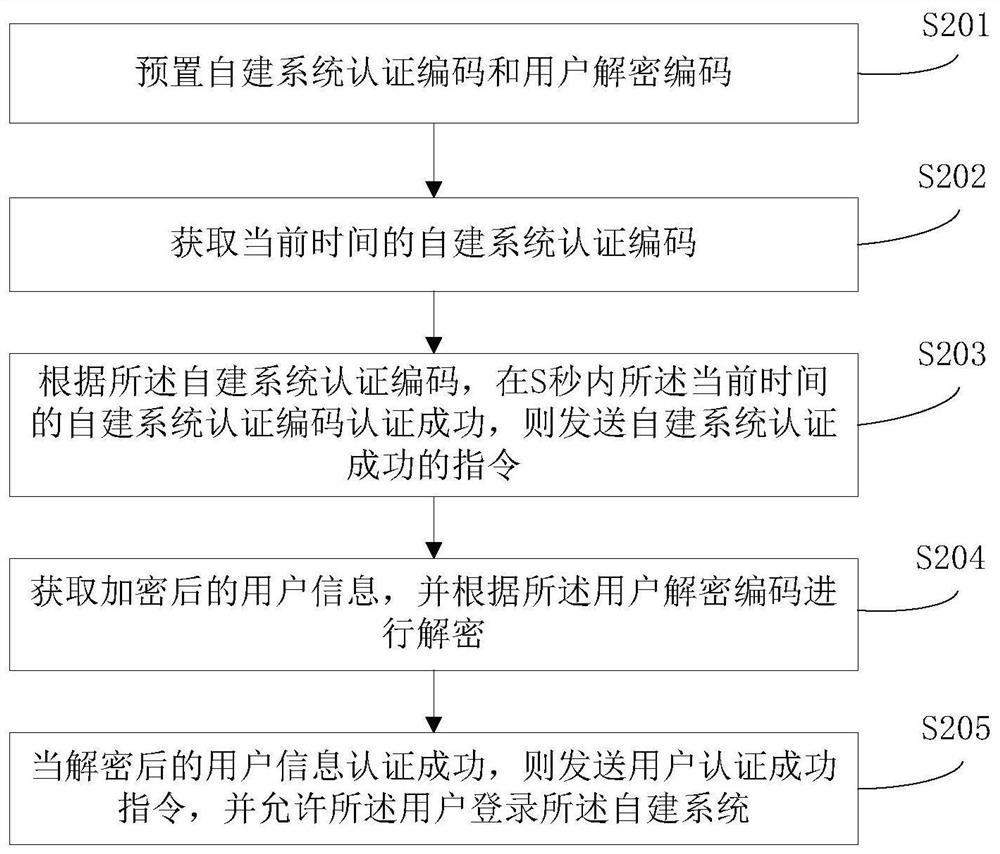
[0090] figure 2 Shown is a flow chart of a method for decrypting e-government affairs of the present invention, said method comprising steps:
[0091] S201, presetting the self-built system authentication code and user decryption code;
[0092] In the e-government unified identity authentication system, the encryption end is generally placed in the government service network, and the decryption end is placed in the self-built system;
[0093] The self-built system refers to the system built by each government department, which is the decryption terminal of the present invention;
[0094] The government service network gathers all government service items, and each government service item corresponds to a different self-built system. Users log in to the government service network, select the self-built system where the government service item needs to be handled, and enter the corresponding user name and Password and authentication, the authentication process is divided into...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com