File access method, device and equipment and readable storage medium
A file access and access method technology, applied in electrical components, transmission systems, etc., can solve problems that affect system performance, deadlock, and affect user experience.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
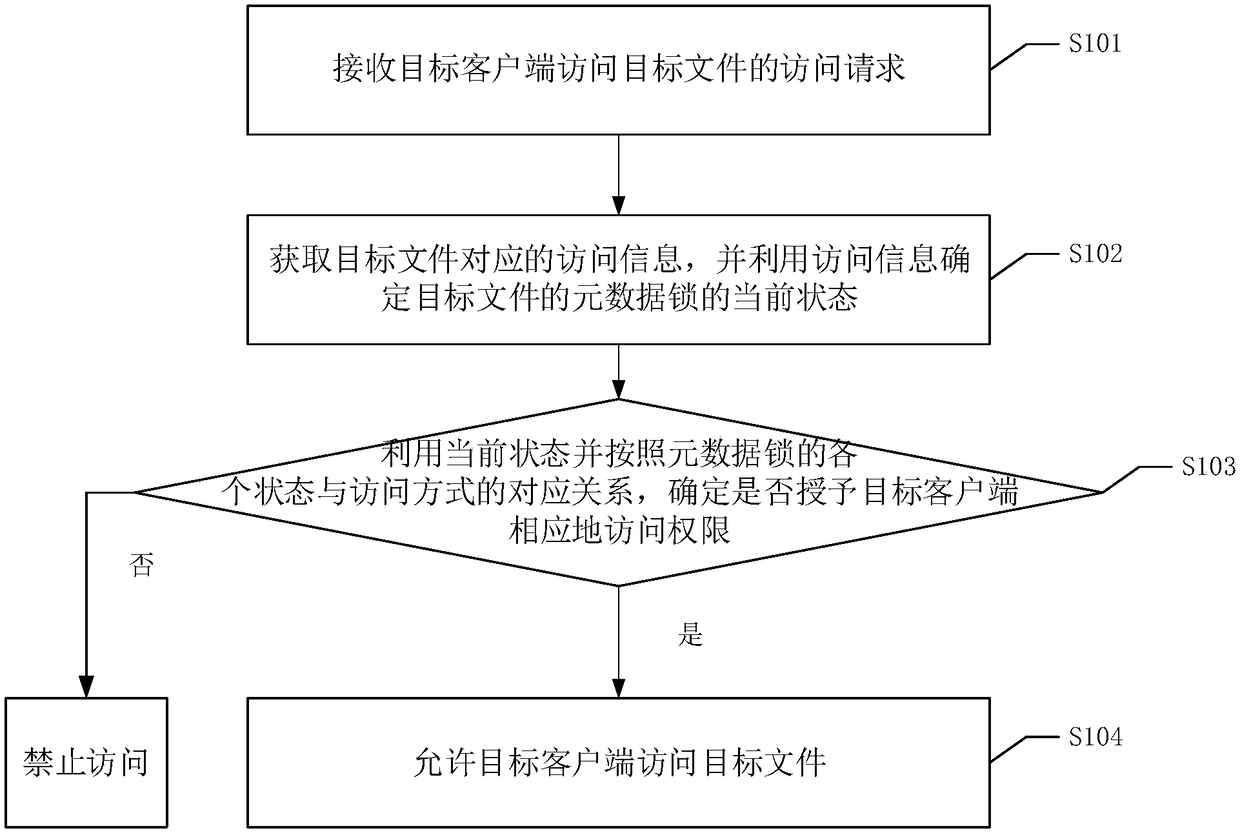
[0050] Please refer to figure 1 , figure 1 It is a flowchart of a file access method in an embodiment of the present invention, which can be used in a distributed storage system, and the method includes the following steps:
[0051] S101. Receive an access request from a target client to access a target file.
[0052] Wherein, the access request includes an access method for requesting access to the target file.
[0053]Under the operation of the user or driven by the internal program, the target client sends an access request to the server to access the target file. Wherein, the target client is any client. The access request may include a method of accessing the target file, and the access method includes at least one of common access methods such as read, cache read, write, cache write, delete, copy, and move. In addition, the target file refers to any file stored in the distributed system such as pictures, documents, tables, audio, and video that can be accessed by the...
Embodiment 2
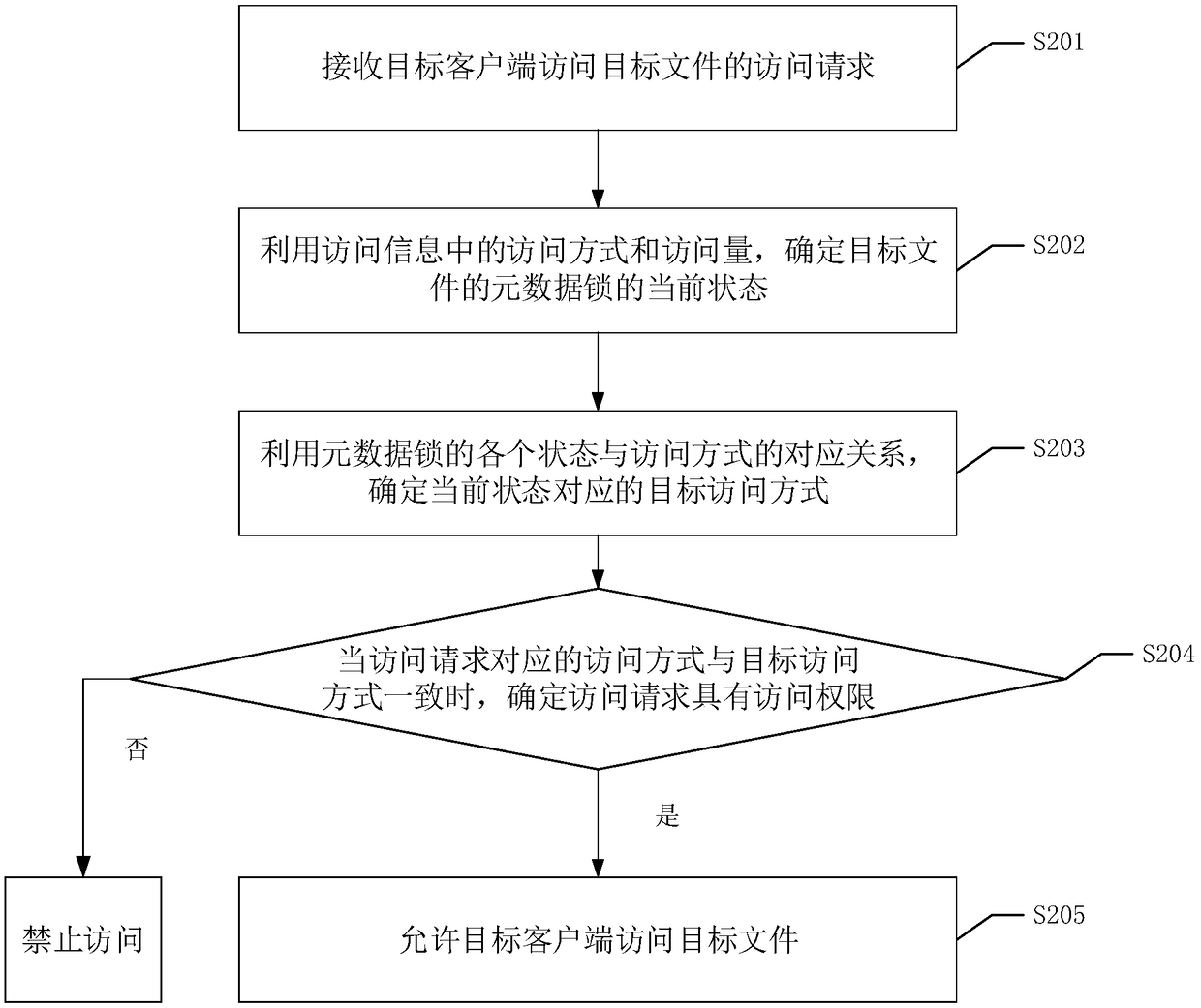
[0069] Please refer to figure 2 , figure 2 It is a flowchart of another file access method in the embodiment of the present invention, which can be used in a distributed storage system. The method includes the following steps:
[0070] S201. Receive an access request from a target client to access a target file.
[0071] S202. Determine the current status of the metadata lock of the target file by using the access mode and access amount in the access information.
[0072] Wherein, the state of the metadata lock includes an idle state, an exclusive state and a shared state.
[0073] Corresponding relationship between the corresponding access mode and corresponding access amount and the state of the metadata lock can be pre-specified, and the current state of the metadata lock can be directly determined when the access information is obtained.
[0074] Specifically, the current state of the metadata lock of the target file is determined by using the access mode and the amou...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com