Method and device for implementing IOAM package
A configuration request and configuration information technology, applied in the field of communication, can solve problems such as increasing the burden on network administrators, error-prone, and complex
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
application example 1
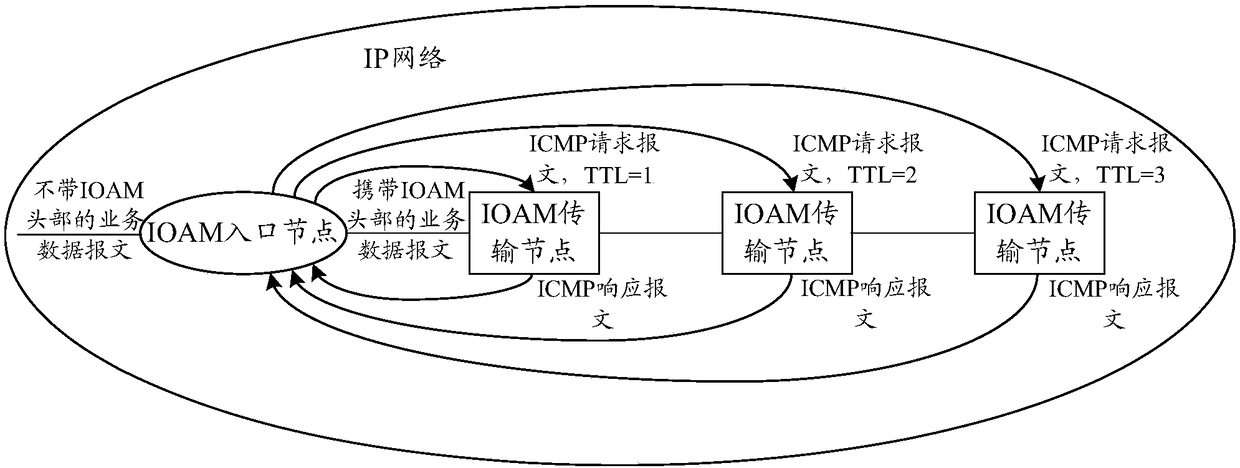
[0060] image 3 It is a schematic diagram of implementing IOAM encapsulation in an IP network. In this application example, the IOAM entry node and the IOAM transmission node need to perform the following steps:
[0061] Step 11: The IOAM ingress node sends an ICMP request message carrying IOAM configuration request information.
[0062] Figure 4 Is the format diagram of the ICMP message, such as Figure 4 As shown, the ICMP message contains an 8-bit type field and an 8-bit code field. The IETF standard specifies some values of these two fields. For example, type 8 code 0 means ICMP Ping request, type 0 code 0 means ICMP Ping response, type 10 code 0 for router solicitation, type 9 code 0 for router advertisement, etc. By defining the types and code values that have not yet been specified, such as specifying type 19 code 0 to represent an IOAM configuration request, and type 20 code 0 to represent an IOAM configuration response, the ICMP request message can be made to...
application example 2
[0068] Image 6 It is a schematic diagram of implementing IOAM encapsulation in an MPLS network. In this application example, the IOAM entry node and the IOAM transmission node need to perform the following steps:
[0069] Step 21: The IOAM ingress node sends an LSP Ping request message carrying IOAM configuration request information.
[0070] Figure 7 is the format diagram of the LSP Ping message, such as Figure 7As shown, the LSP Ping request message includes a set of TLVs, and by adding a Type field to represent the new TLV of the IOAM configuration request, the LSP Ping request message can be made to carry the IOAM configuration request information.
[0071] Step 22: The IOAM transit node responds to the request, and replies to the IOAM ingress node with an LSP Ping response message carrying the IOAM configuration information of the node.
[0072] According to the LSP Ping mechanism, the sending node can send the LSP Ping request message to each node on the transmiss...
application example 3
[0076] Figure 8 It is a schematic diagram of using LoopBack to realize IOAM encapsulation in the Ethernet network. Figure 9 It is a schematic diagram of using LinkTrace to realize IOAM encapsulation in the Ethernet network. In this application example, the IOAM entry node and the IOAM transmission node need to perform the following steps:
[0077] Step 31: The IOAM entry node sends a LoopBack request message or a LinkTrace request message carrying the IOAM configuration request information.
[0078] Figure 10 is the format diagram of the LoopBack message, Figure 11 is the format diagram of the LinkTrace message, such as Figure 10 with Figure 11 Shown, LoopBack request message or LinkTrace request message all comprise a group of TLVs, by adding a Type field to represent the new TLV of IOAM configuration request, just can make LoopBack request message or LinkTrace request message carry IOAM configuration request information.
[0079] Step 32: The IOAM transfer node r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com