Method and device for sending and displaying messages, method and device for identity authentication
A technology for identity authentication and sending messages, applied in the field of information processing, can solve problems such as privacy leakage, unfavorable users, loss of personal property of the receiver, etc., and achieve the effect of ensuring privacy and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
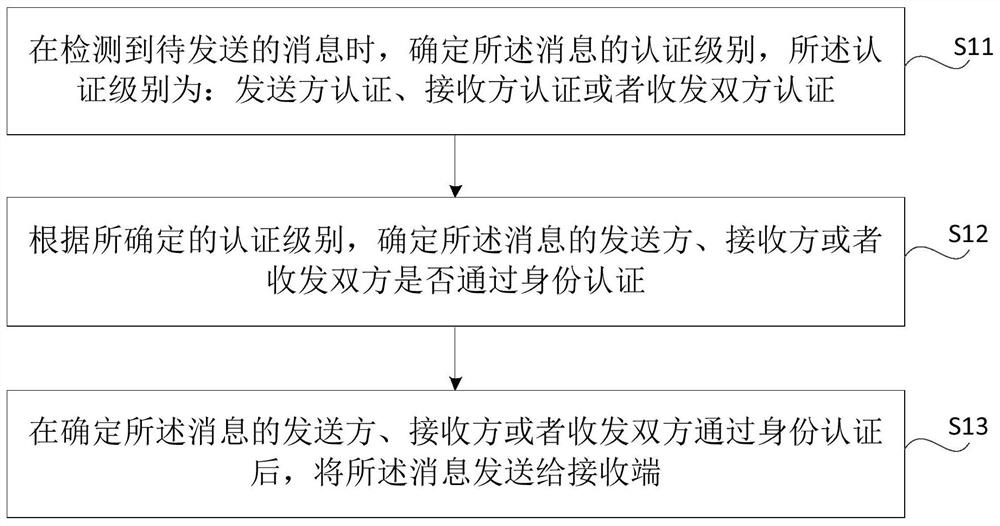
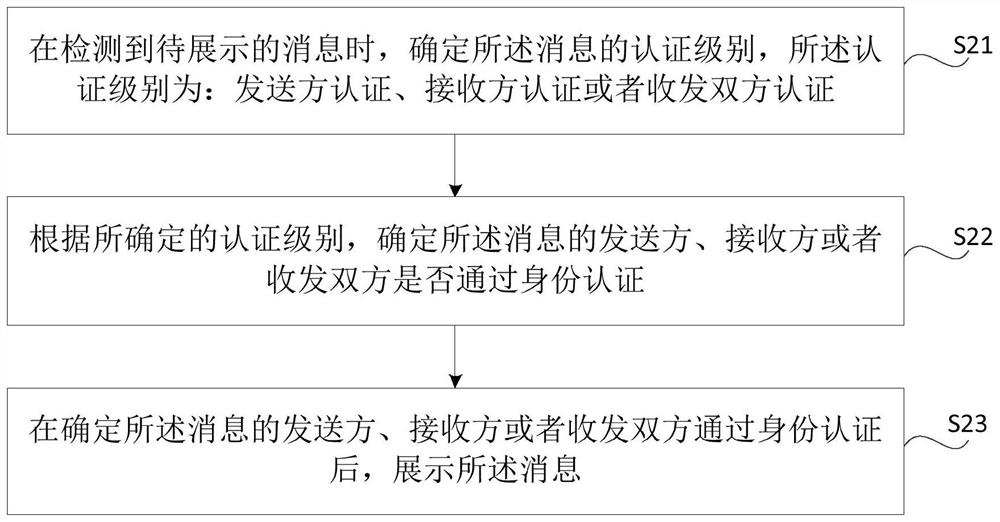
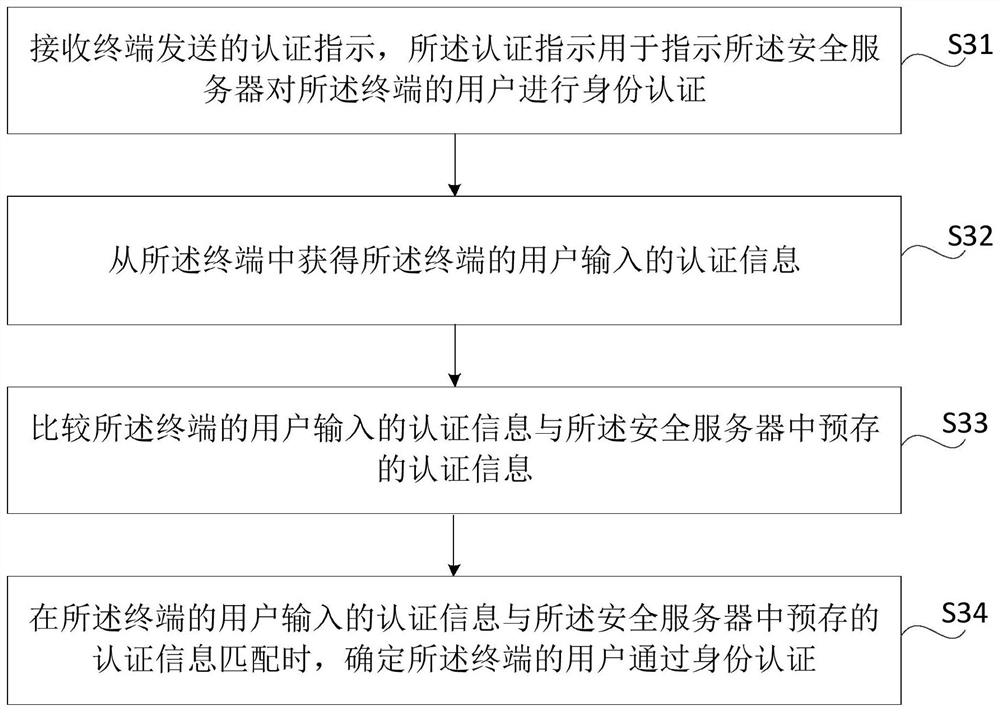
[0106] The first implementation mode: detecting whether at least one of the one or more phrases that make up the message matches at least one of the preset keywords; at least one of the one or more phrases matches the When at least one of the preset keywords matches, the authentication level of the message is determined according to the matched keywords.
[0107] The second implementation mode: detecting whether at least one of the one or more phrases that make up the message matches at least one of the preset keywords; at least one of the one or more phrases matches the When at least one of the preset keywords matches, prompting the user at the sending end to input an authentication level; determining the authentication level input by the user at the sending end as the authentication level of the message.
[0108] A third implementation manner: obtaining the user input authentication level of the sending end; determining the authentication level of the user input at the sendi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com