Malicious code family homology analysis based on semi-supervised density clustering
A homology analysis and semi-supervised clustering technology, applied in the field of data mining, can solve the problem of inability to accurately realize the division and visualization of malicious code families, and achieve the effect of accurate family division
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in further detail below with reference to the accompanying drawings.
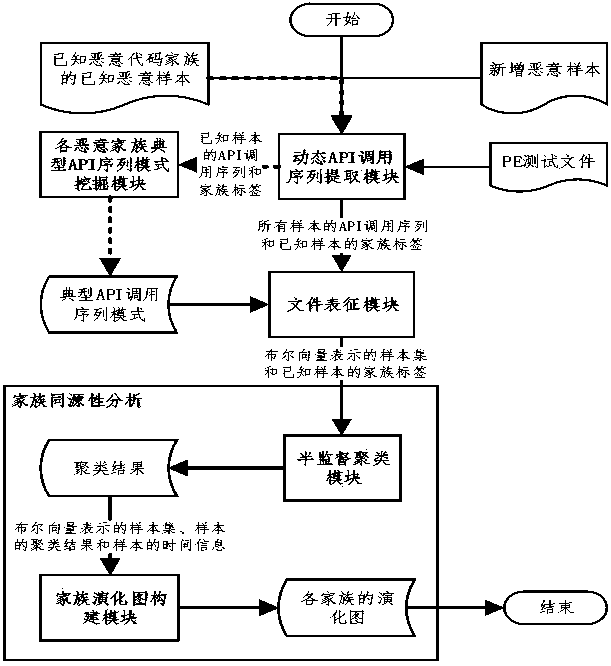
[0030] figure 1 The overall design scheme of the malicious code family homology analysis model proposed by the present invention is mainly divided into the following modules: dynamic API call sequence extraction module, typical API sequence pattern mining module, file characterization module, and semi-supervised family clustering module and family evolution graph building blocks.
[0031] feature mining stage, figure 1 The middle dotted line marks the process, and its workflow is to use the dynamic API call sequence extraction module to extract the API call sequences of known malicious samples of known malicious code families, and then use the family labels of known malicious samples to mine the API call sequence data. A typical API call sequence pattern that can ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com