Node authentication method and device based on non-interactive zero-knowledge proof
An authentication method and node technology, applied in the computer field, can solve problems such as poor user experience and low node authentication efficiency, and achieve the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
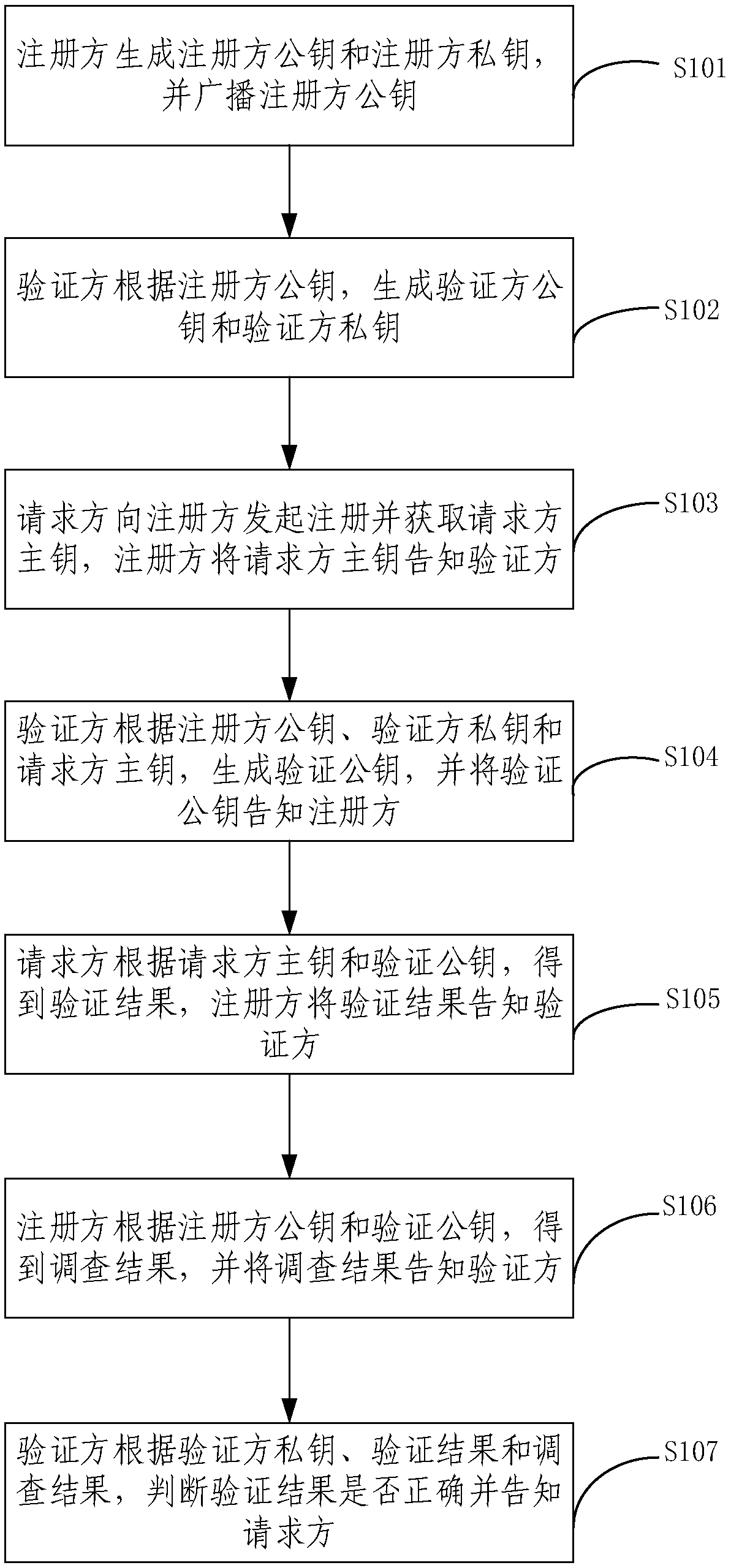
[0036] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
[0037] At present, the mobile crowd sensing network can greatly enrich the functions of people. As independent individuals in society, people will not only use the perception data in the network, but also actively "produce" data and upload it to the network for other users to use. Users start as the main body of data perception, collection, analysis and mining, complete the whole process spontaneously, and then complete the perception tasks published on the network. However, when many users share perception data in order to cooperate to complete the same task, they need to cooperate with each other, that is, node authentication.
[0038] In the traditional node authentica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com