Registration method and device based on service architecture
A registration request and algorithm technology, applied in the field of registration methods and devices based on service-oriented architecture, can solve problems such as low security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0090] Embodiment 1: The security parameter includes a token, and the token is generated based on an asymmetric key.
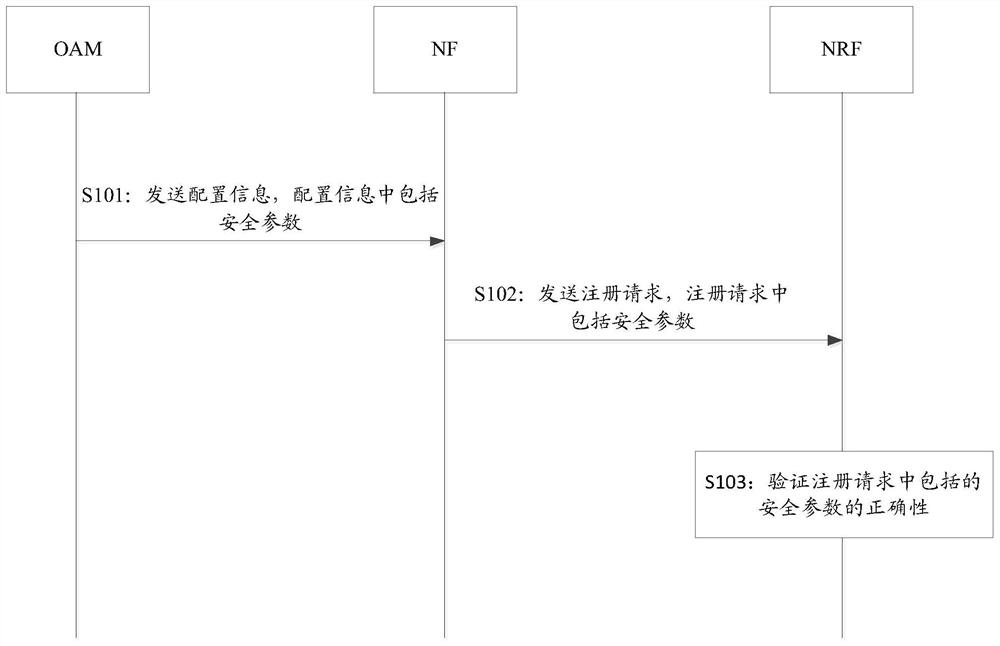
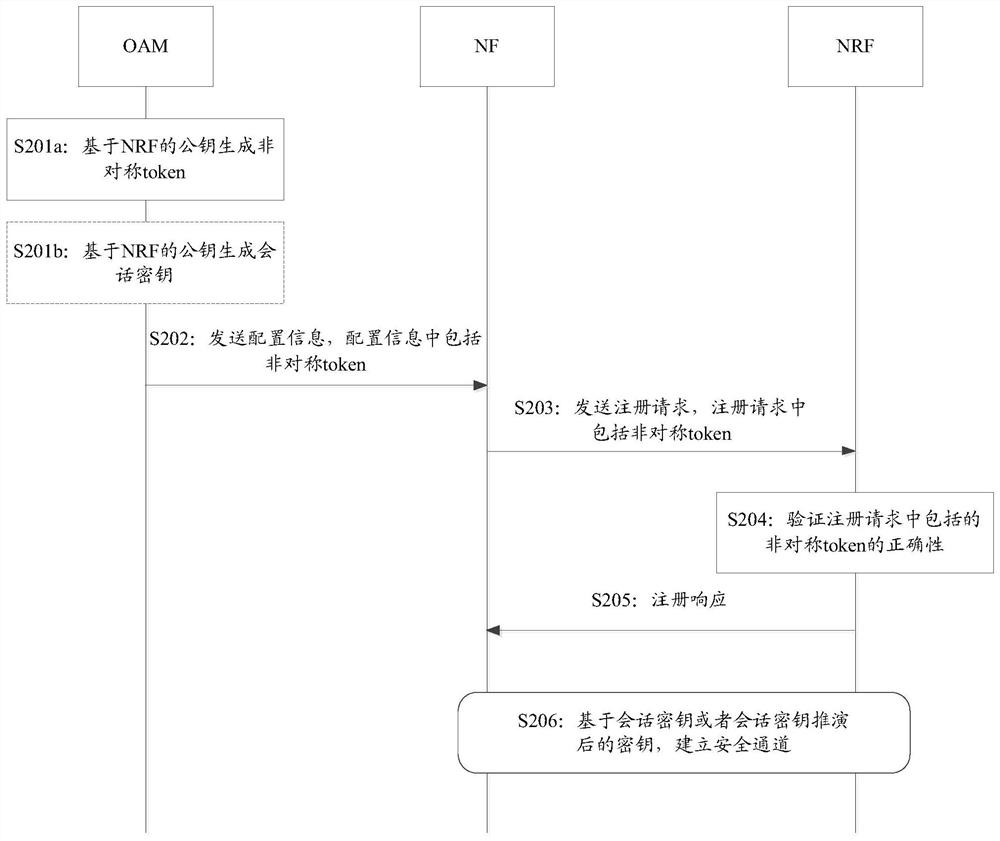
[0091] image 3 Shown is the flow chart of the security registration implementation based on the service-oriented architecture provided by Embodiment 1 of this application, refer to image 3 shown, including:
[0092] S201a: OAM generates an asymmetric token.
[0093] In this embodiment of the application, the OAM can generate an asymmetric token based on the public key (PKnrf) of the NRF.
[0094] Among them, the OAM generates an asymmetric token, and the OAM needs to store the OAM public key (PKoam), the OAM private key (SKoam) and the NRF public key (PKnrf) in advance. Wherein, the PKnrf may be initially pre-set in the OAM, or may be obtained from the NRF during the interaction between the OAM and the NRF. NRF also needs to save Pkoam, PKnrf and NRF's private key (SKnrf) in advance. Wherein, the Pkoam may be initially pre-set in the NRF, or may be sent...
Embodiment 2
[0116] Embodiment 2: The security parameters include token, and the token is generated based on a symmetric key.
[0117] Figure 4 Shown is a flow chart of implementing the secure registration method provided in Embodiment 2 of the present application. Figure 4 The implementation flow chart of the security registration method shown is the same as image 3 The implementation process of the security registration method shown is similar, and the only difference lies in the calculation method of the token. The difference will be described below. For the same or similar points, please refer to the description of the first embodiment above.
[0118] S301a: The OAM generates a symmetric token.
[0119] In the embodiment of the present application, the OAM may generate a symmetric token based on the symmetric key (k) shared between the OAM and the NRF.
[0120] Wherein, when the OAM generates the symmetric token based on the symmetric key (k) shared between the OAM and the NRF, b...
Embodiment 3
[0136] Embodiment 3: The security parameter includes MAC.
[0137] Figure 5 Shown is a flow chart of implementing the secure registration method provided in Embodiment 3 of the present application. Figure 5 The implementation flow chart of the security registration method shown is the same as Figure 4 The implementation process of the security registration method shown is similar, and the only difference is that the security parameter generated by OAM is MAC without generating token, and NRF only verifies MAC without token. Only the differences will be described below, and for the same or similar points, reference can be made to the relevant description of the second embodiment above.
[0138] S401: The OAM generates a MAC.
[0139] In the embodiment of the present application, the OAM may generate a MAC based on the symmetric key (k) shared between the OAM and the NRF.
[0140] In the case where the OAM generates the MAC based on the symmetric key (k) shared between th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com