Data security interaction method based on host characteristic confusion
A data security and interactive method technology, applied in the direction of electronic digital data processing, program control design, instruments, etc., can solve data leakage and other problems, and achieve the effect of content concealment and data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment
[0037] In order to illustrate more clearly, the specific embodiment of the present invention is as follows:
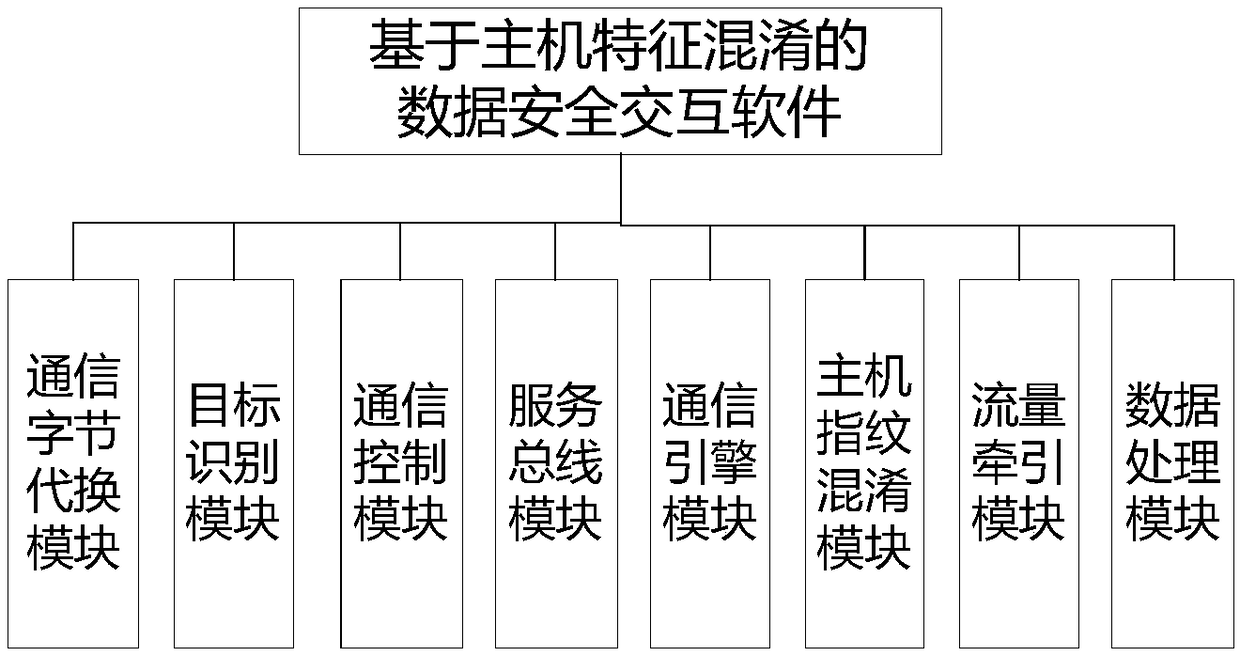
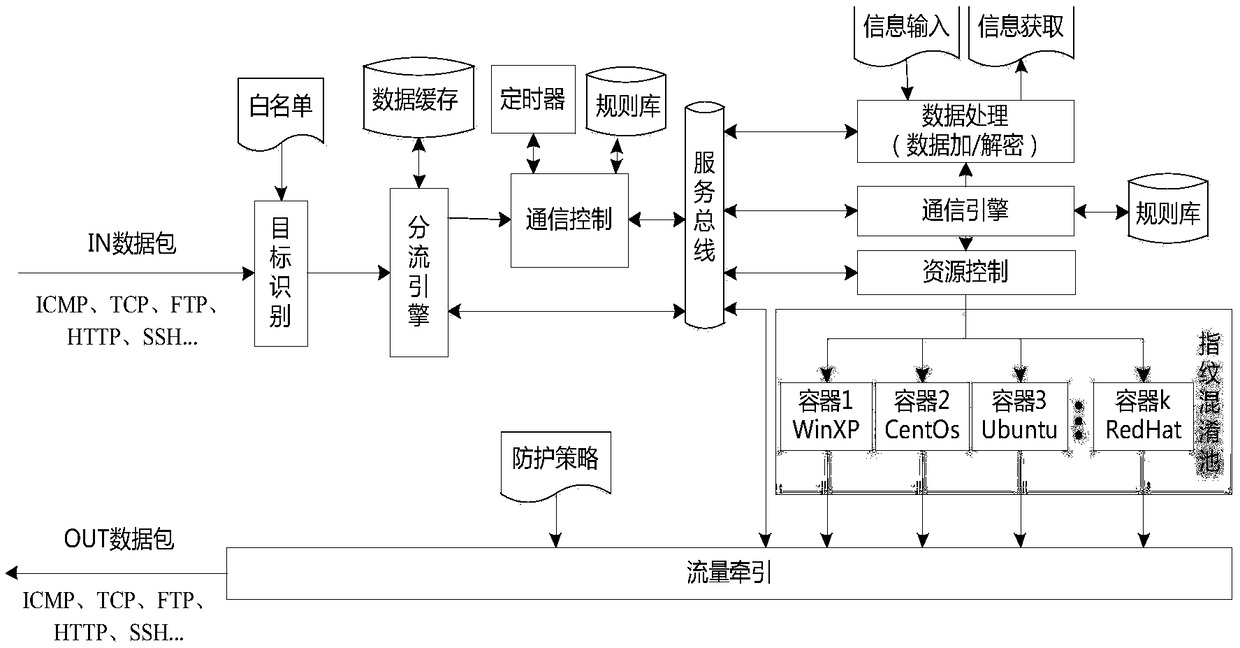
[0038] Such as figure 2 As shown, a data security interaction method based on host feature confusion is characterized in that it includes the following steps:
[0039] (1) Before communication, the system uses the fingerprint information of the host to construct a communication byte substitution table T, sends it to the source and the sink, and stores it in the databases of both parties. The communication byte substitution table structure consists of four columns, the first column is the primary key index, the second column is the host fingerprint information, the third column is the data content, and the fourth column is the description information of the mapping;
[0040] Wherein, the host fingerprint information stored in the database includes: operating system architecture type, system version number, running service type, service interface number, browser type, ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap