An Android application security protection method based on dynamic virtual instruction transformation
A virtual instruction and application security technology, applied in the direction of program/content distribution protection, etc., can solve the problems of static analysis and dynamic analysis that cannot completely resist attackers, cannot effectively solve memory dump, and fixed principle.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
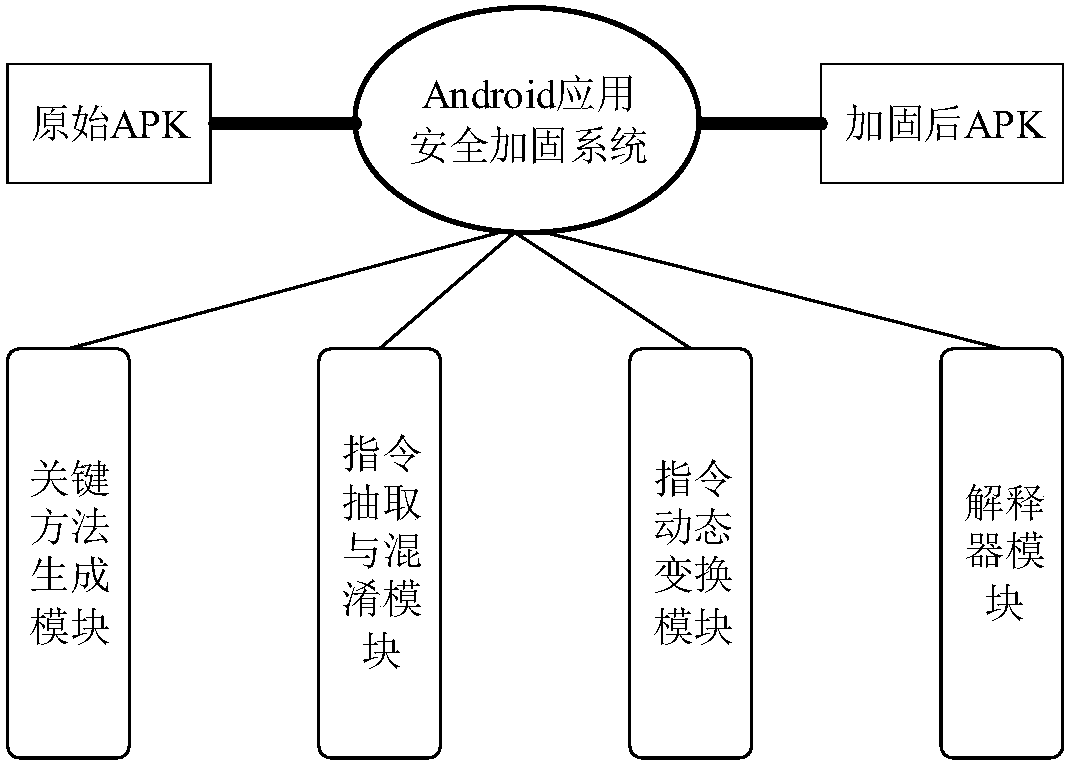
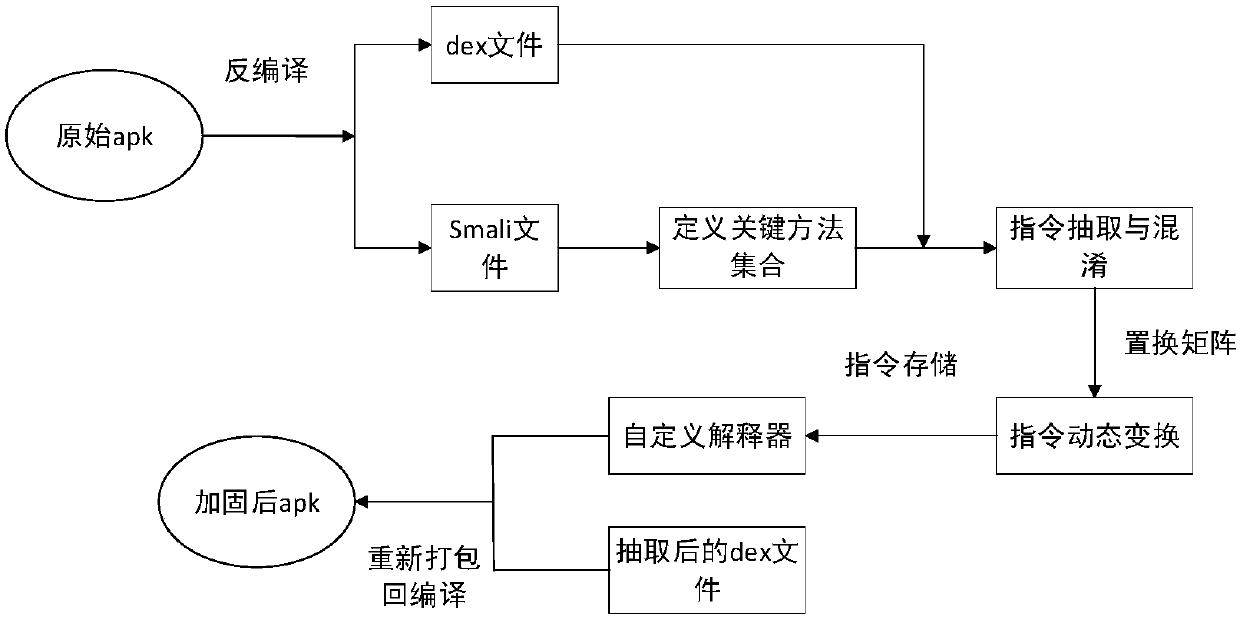
[0022] The Android application security protection method based on the dynamic virtual instruction set of the present invention comprises the following steps:
[0023] 1. Determine the protected object in the Android application. The protected object is the key method in the Android application. The key method includes two parts. The first part is provided by the developer. The developer provides which methods they think are very important during the running of the program Need to be protected, the second part is given by the present invention, the present invention analyzes the application program and takes the method of accessing system sensitive resources as the key method.
[0024] 2. According to the set of key methods obtained in step 1, extract information such as method instructions of key methods from the DEX file. The key method in the program is a class method belonging to a certain class. Its related information is stored in the class data area of the class it be...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap