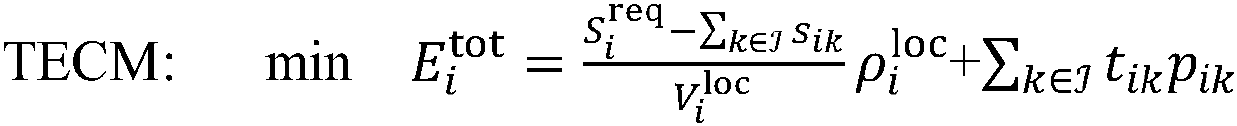Multi-access computing shunting method based on simulated annealing with safety guarantee
A simulated annealing and security guarantee technology, applied in the field of communication, can solve problems such as security overflow and malicious eavesdropping by mobile users
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0079] The present invention will be further described below in conjunction with the accompanying drawings.
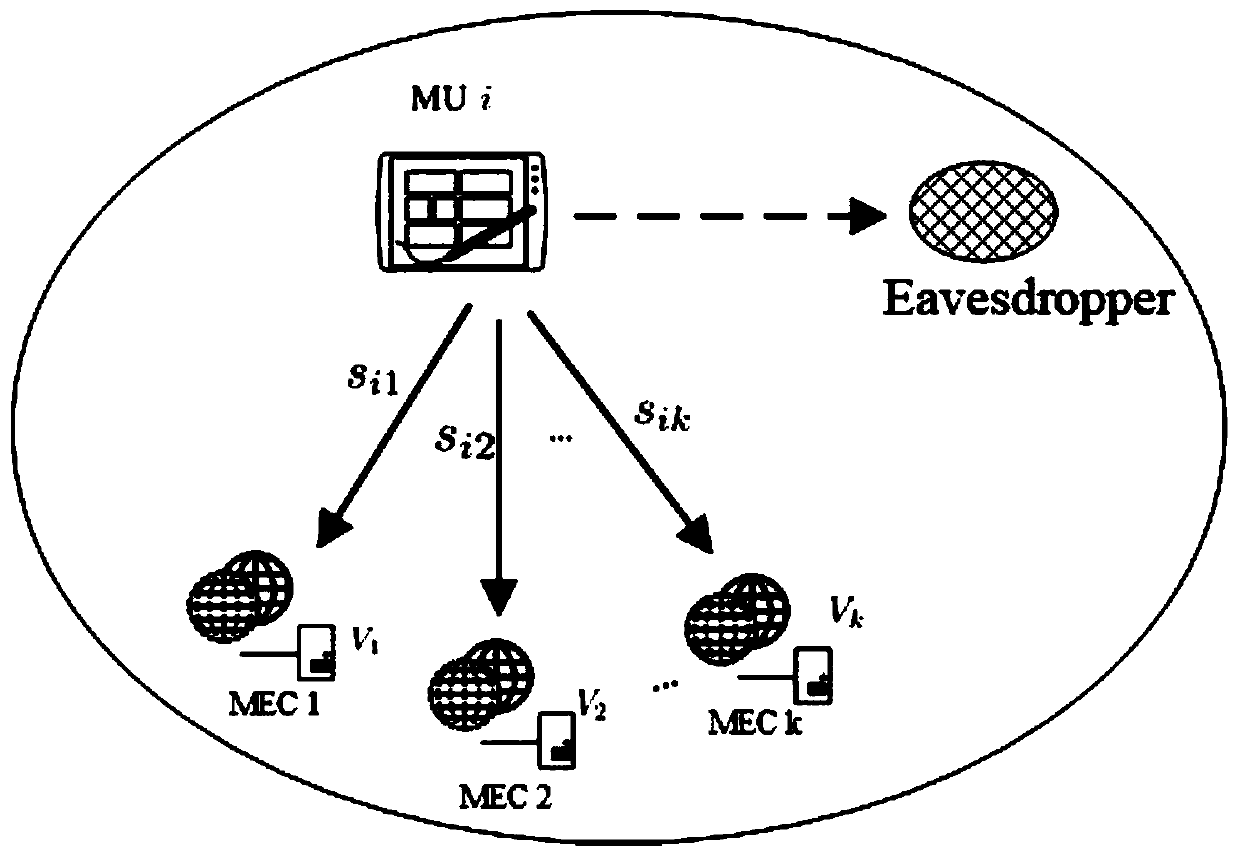
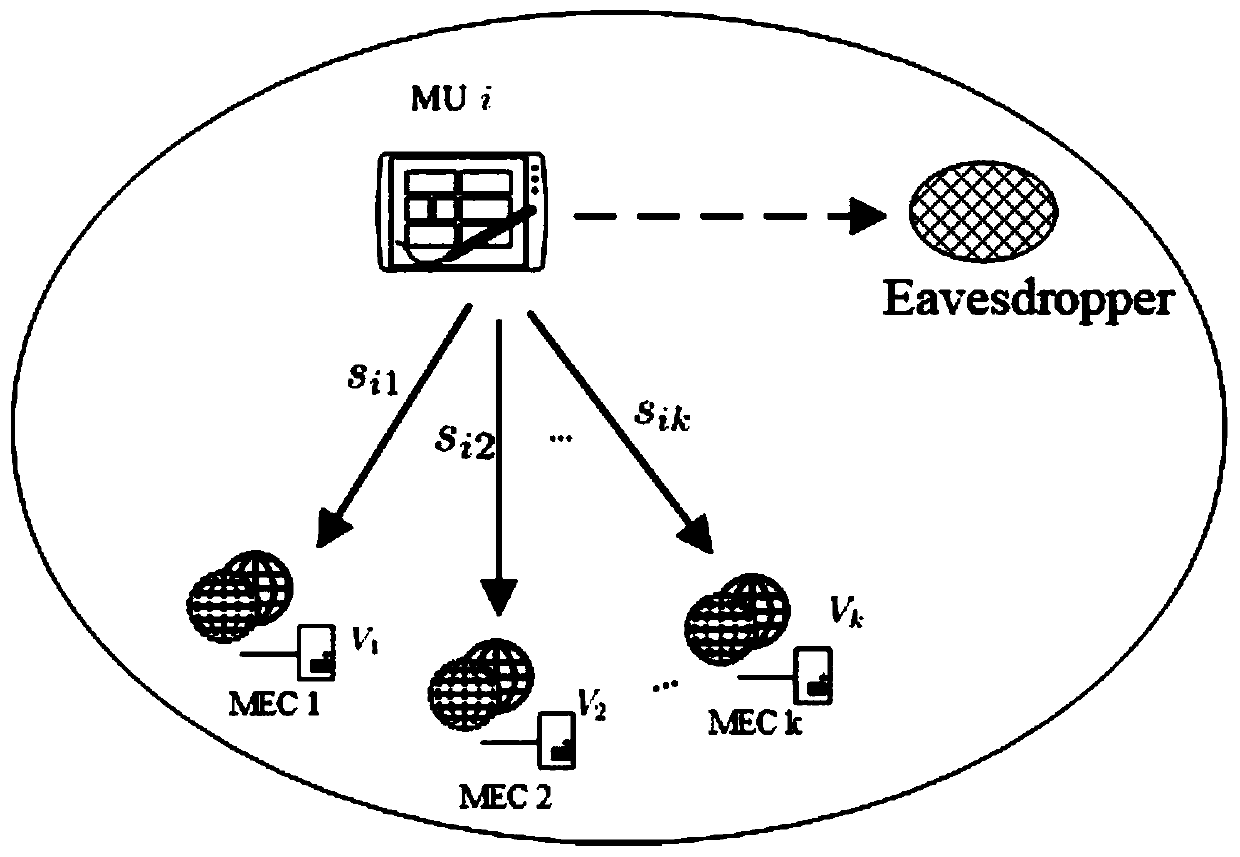
[0080] refer to figure 1 , a simulated annealing-based multi-access computing shunt method with security guarantees. The implementation of this method can minimize the total energy consumption of the system and improve the utilization rate of wireless resources of the entire system under the premise of meeting the security requirements at the same time. The present invention can be applied to wireless networks, such as figure 1 in the scene shown. Designing an optimization method for this problem includes the following steps:
[0081] (1) Consider a mobile user i (Mobile User, MU i), which is within the service range of K base stations (Base Station, BS), and each base station is equipped with an edge computing server (Edge Server) that can provide mobile user i provides computing offloading services, edge servers use collection Indicates that the total amount of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com