Plaintext shared data auditing method and system supporting privacy information hiding
A technology of privacy information and shared data, applied in the field of cloud computing security, can solve problems such as the reliability and integrity of shared data cannot be fully trusted, blockage of data release audit process, large calculation and transmission pressure, etc., to reduce the cost of communication The probability of bottlenecks, the avoidance of unrecoverable files, and the effect of avoiding storage overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
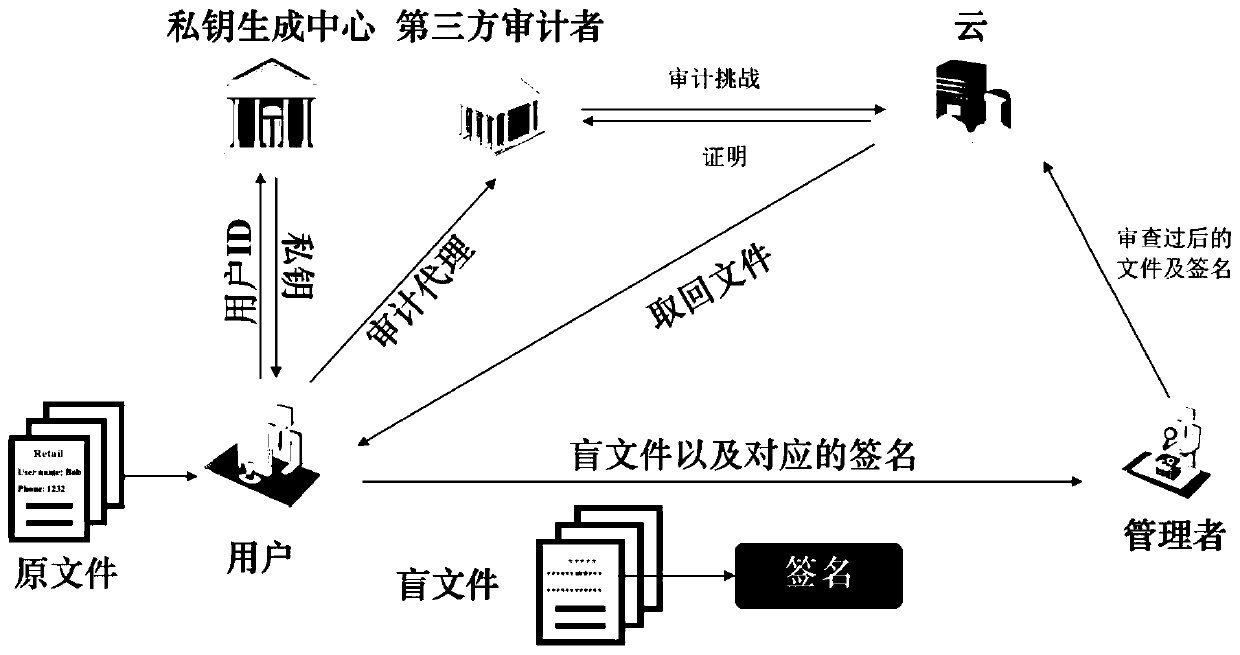
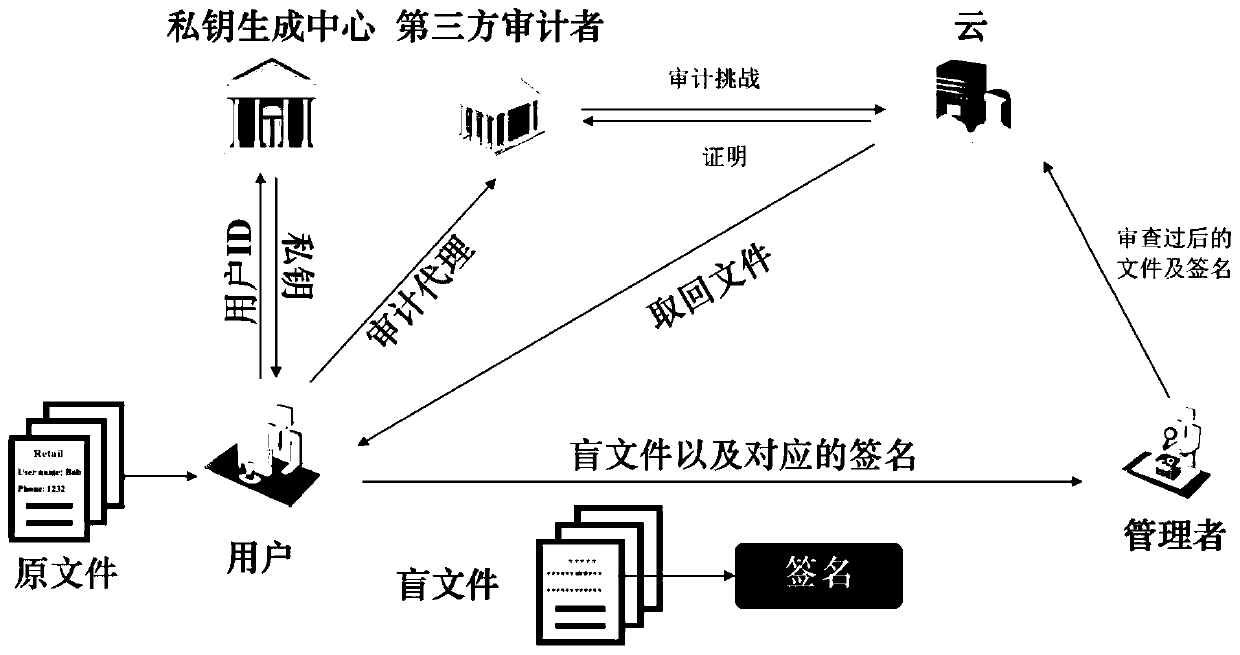
[0031] The plaintext shared data audit system that supports the plaintext shared data audit method for privacy information hiding provided in this embodiment, such as figure 1 shown, including:
[0032] Private key generation center, used to initialize the system;
[0033] The client is used to extract the private key from the private key generation center, and generate the blind file, file label and corresponding signature of the file, and submit it to the management end;
[0034] The management terminal is used to review the files according to the received blind files, file tags and corresponding signatures, and upload the blind files, file tags and corresponding signatures to the cloud when the review is passed;
[0035] Cloud, used to store blind files, file labels and corresponding signatures submitted by the management terminal;
[0036] The third-party audit terminal is used to audit the integrity of files based on blind files, file labels and corresponding signatures...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com