Comprehensive audit supervision system
A supervision system and monitoring system technology, applied in database management systems, website content management, structured data retrieval, etc., can solve the problems of insufficient comprehensive analysis and comprehensive management capabilities of audit information, endangering interests, and many security problems, and achieve defense External intrusion and internal illegal illegal operation, good reliability and ease of use, the effect of improving the safety operation factor
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] In order to deepen the understanding of the present invention, the present invention will be further described below in conjunction with the examples, which are only used to explain the present invention, and do not constitute a limitation to the protection scope of the present invention.
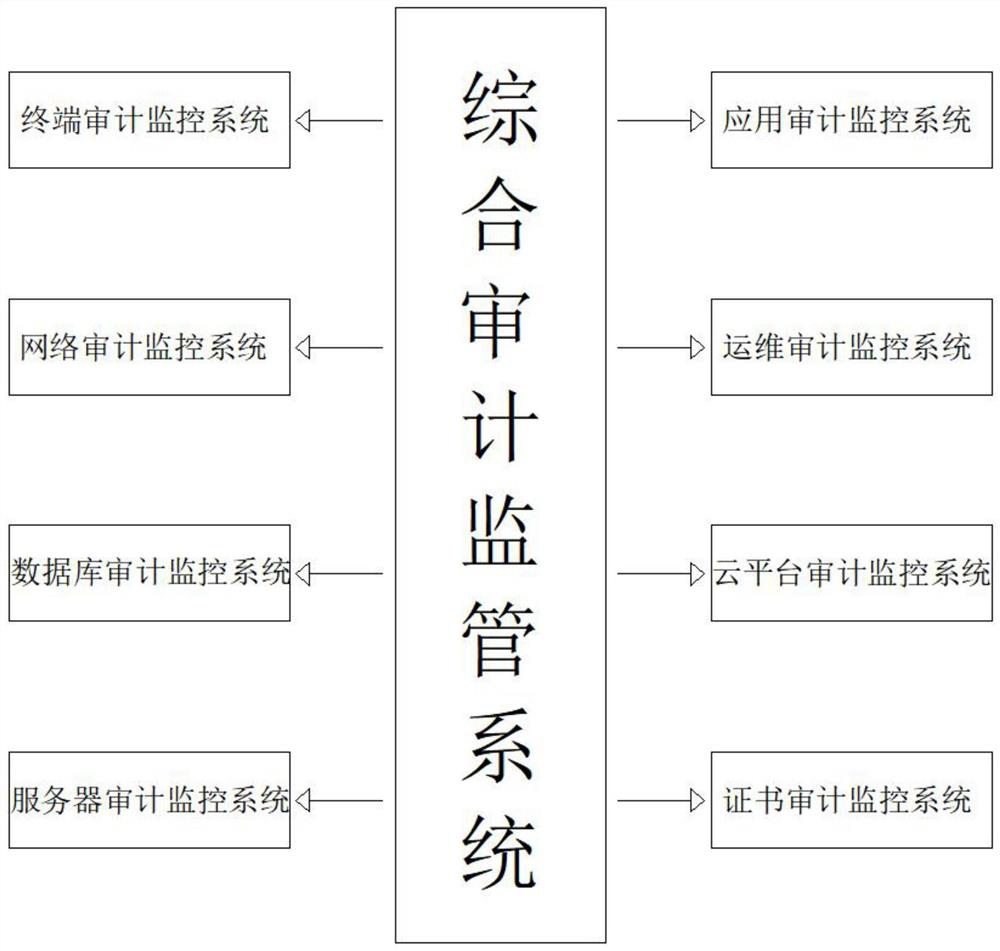
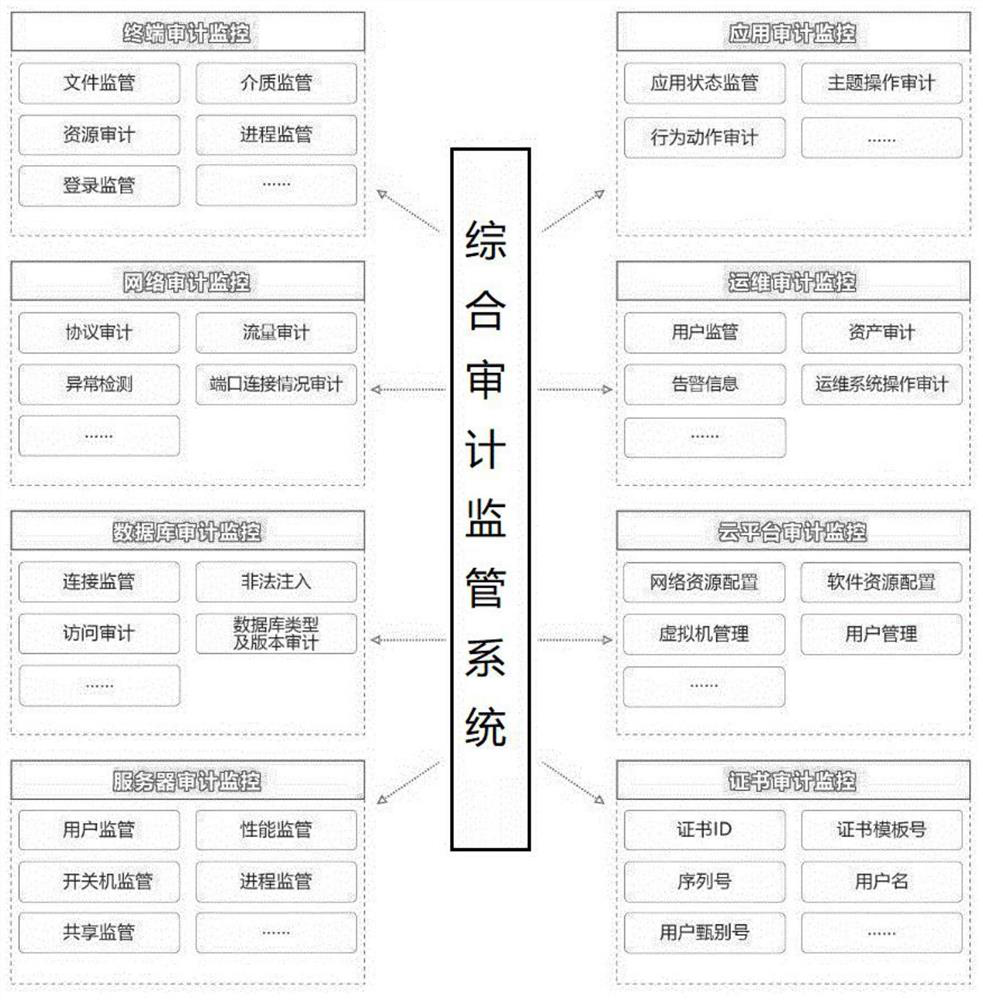
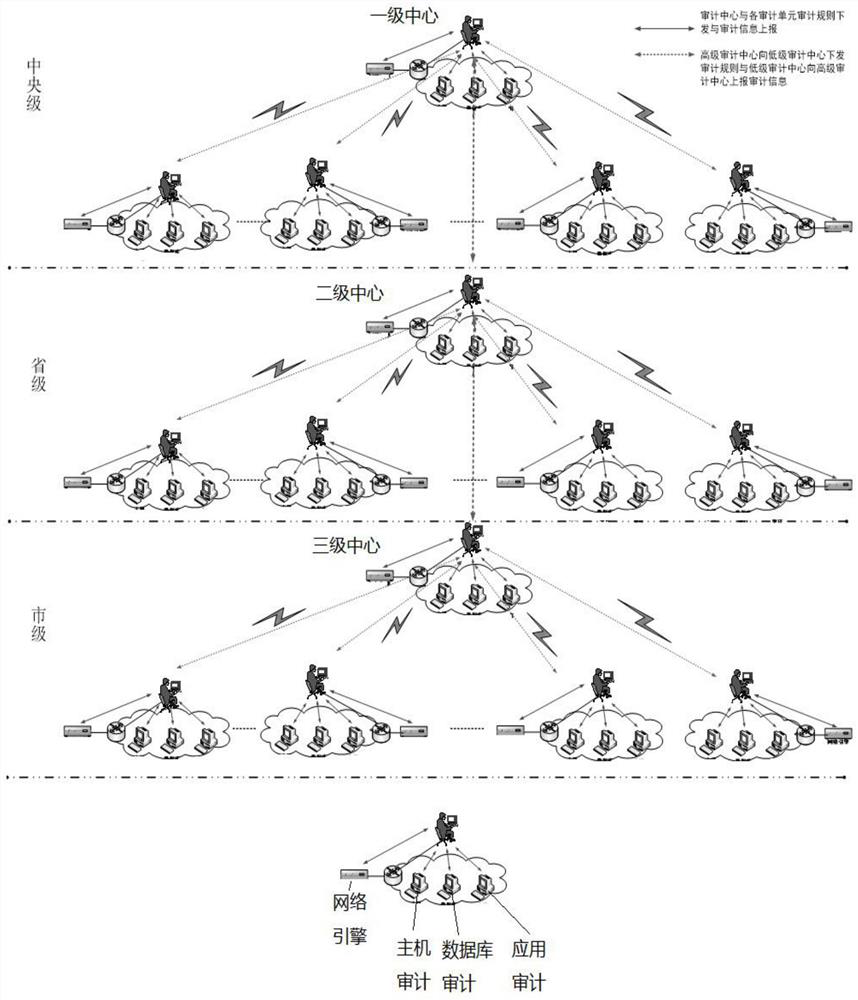
[0020] according to figure 1 , 2 , 3, the present embodiment proposes a comprehensive audit supervision system, including hardware and software and functional systems, the hardware and software and functional systems, the hardware and software including audit center, audit terminal, audit interface, network engine and database engine, the functional system includes a terminal audit monitoring system, a network audit monitoring system, a database audit monitoring system, a server audit monitoring system, a cloud platform audit monitoring system, a certificate audit monitoring system, an operation and maintenance audit monitoring system, and an application audit monitoring system; The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com