A voice retrieval method and system
A retrieval system and speech technology, applied in audio data retrieval, transmission system, speech analysis, etc., can solve the problem of low security of hash digest, improve retrieval efficiency, retrieval accuracy, good robustness and differentiation , the effect of improving safety
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
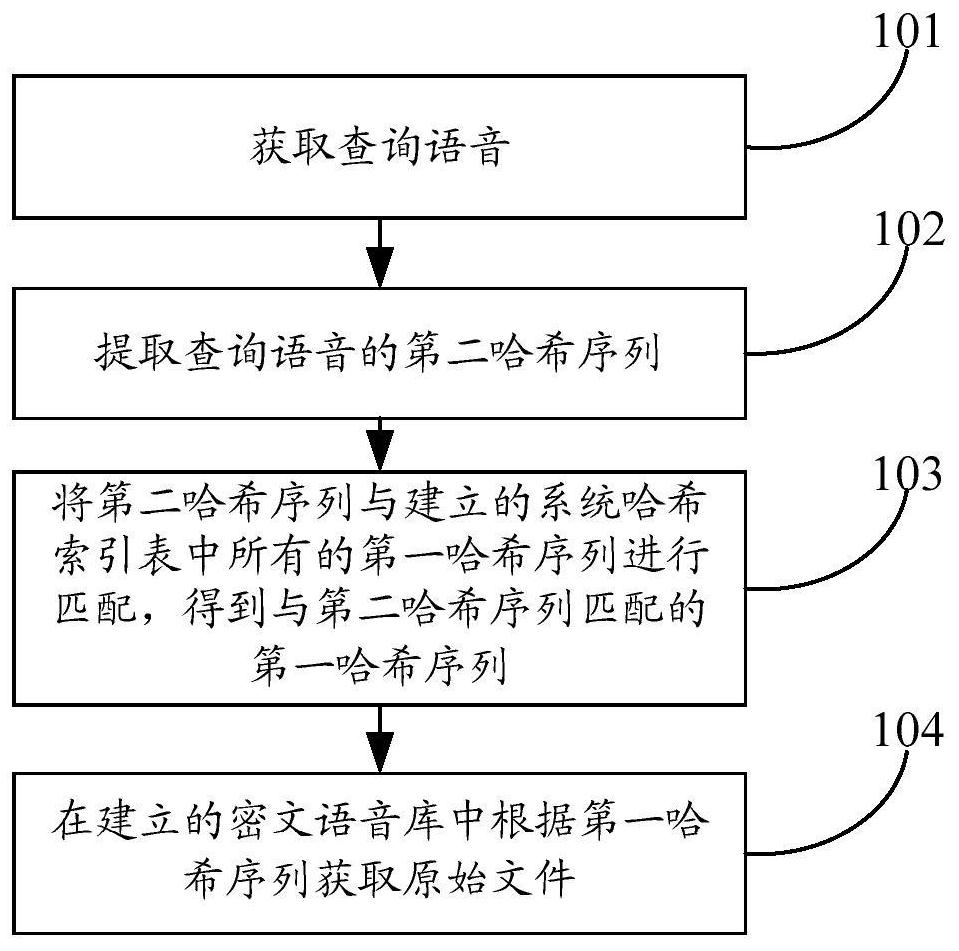
[0072] This embodiment provides a voice retrieval method. Before performing speech retrieval, it is necessary to establish a ciphertext speech library and a system hash index table in the cloud.
[0073] The establishment of ciphertext speech database includes:
[0074] 1. Obtain the original file. The original file includes a speech signal s(t).
[0075] 2. Encrypt the original file to obtain the encrypted file and upload the encrypted file to the voice database in the cloud to obtain the ciphertext voice database. Specifically, it includes: encrypting the original file with a two-dimensional chaotic map encryption algorithm, obtaining the encrypted file and uploading the encrypted file to the voice library in the cloud to obtain the ciphertext voice library.
[0076] Using the two-dimensional chaotic map encryption algorithm to encrypt the original file specifically includes:
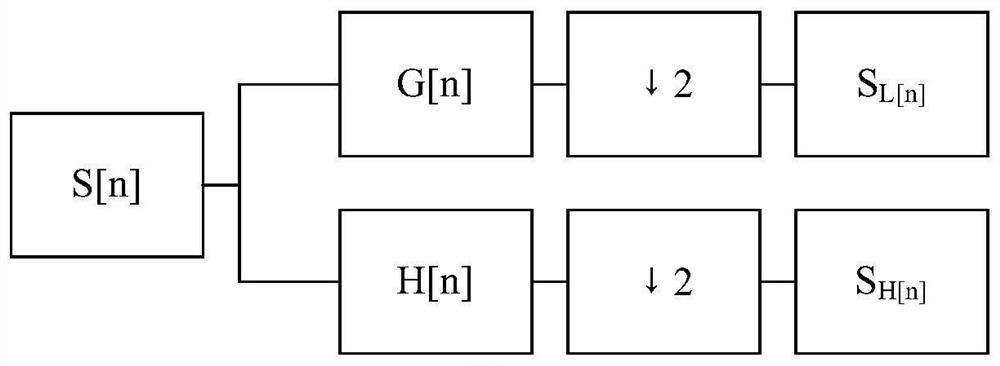
[0077] Set two initial values: when k=1, x k-1 = 1.0,x k = 1.2. Difference equation via 2D ...
Embodiment 2
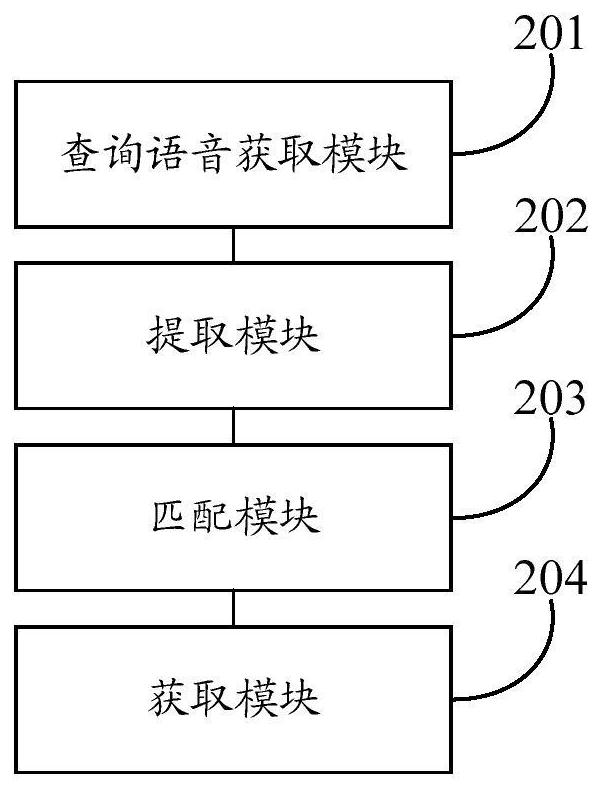
[0146] This embodiment provides a voice retrieval system. It is necessary to establish the ciphertext speech database and the system hash index table before performing speech retrieval, so the ciphertext speech database establishment module and the system hash index table establishment module are executed first.
[0147] The ciphertext speech database building module is used to establish the ciphertext speech database.
[0148] The ciphertext voice library building module includes:
[0149] The original file obtaining unit is used to obtain the original file. The original file includes a speech signal s(t).
[0150] The encryption unit is used to encrypt the original file to obtain the encrypted file and upload the encrypted file to the voice library in the cloud to obtain the ciphertext voice library.
[0151] Cryptographic unit, including:
[0152] The encryption sub-unit is used to encrypt the original file using the two-dimensional chaotic map encryption algorithm to o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com