Method for controlling other systems based on single-point contract execution
A contract and single-point technology, applied in transmission systems, instruments, data processing applications, etc., can solve the problems of no unified operation control command, inability to control other software/hardware systems, and inability to complete verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
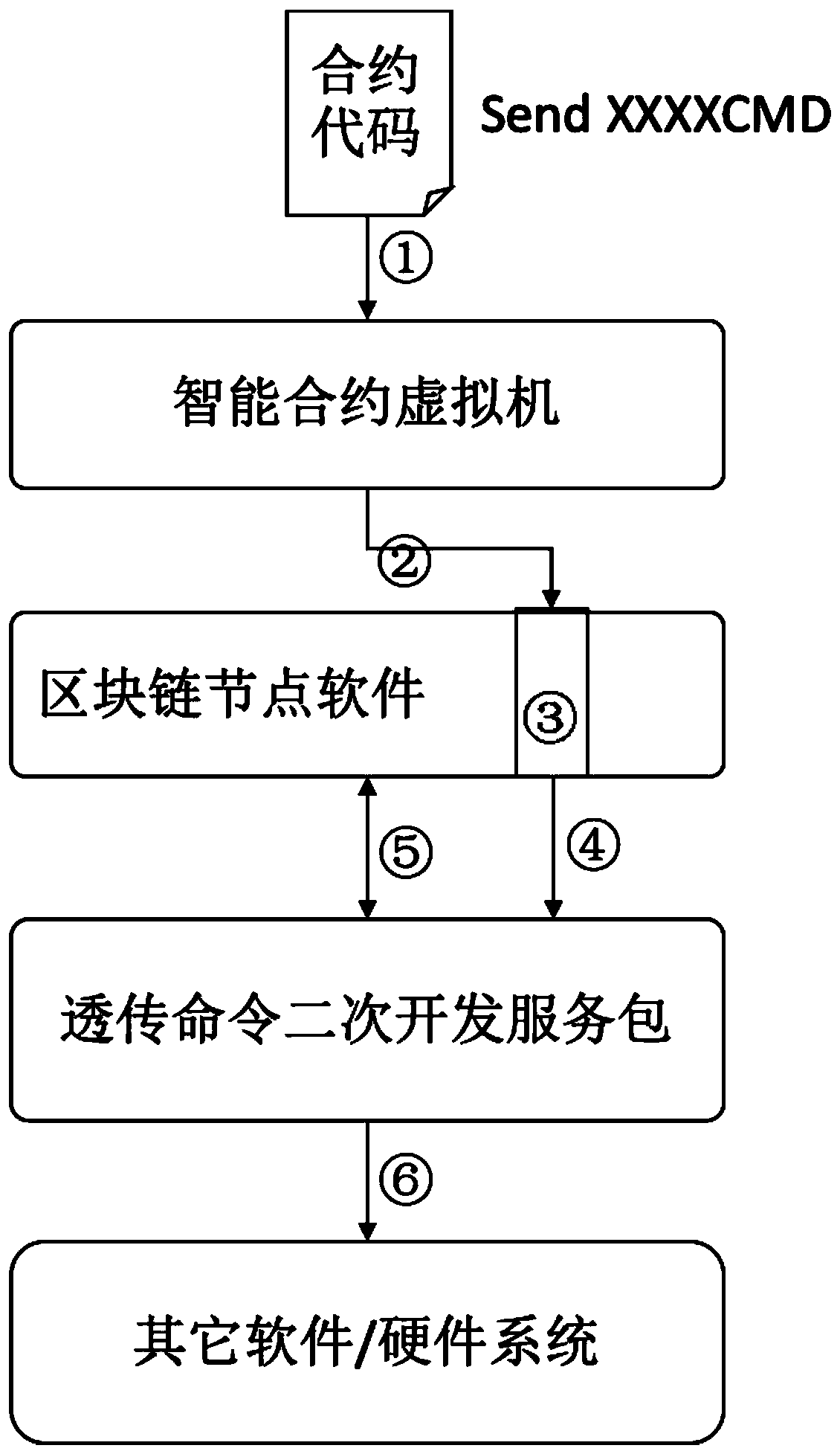
[0026] Example 1: See Figure 1-2 , a method for controlling other systems based on single-point execution contracts, including the following steps:
[0027] A. When the contract developer writes the single-point execution contract code, he integrates the commands that need to be transparently transmitted into the contract code;
[0028] B. The virtual machine executes the contract code, executes to the line that needs the transparent transmission command, calls the transparent transmission channel command input interface, and passes the command to the blockchain node;
[0029] C. The blockchain node does not do any processing on the command, and calls the secondary development service package of the transparent transmission command (the node that executes the contract must deploy the service developed by the package) interface to continue to pass the command downward;
[0030] D. The code in the secondary development service package controls other software / hardware according...
Embodiment 2
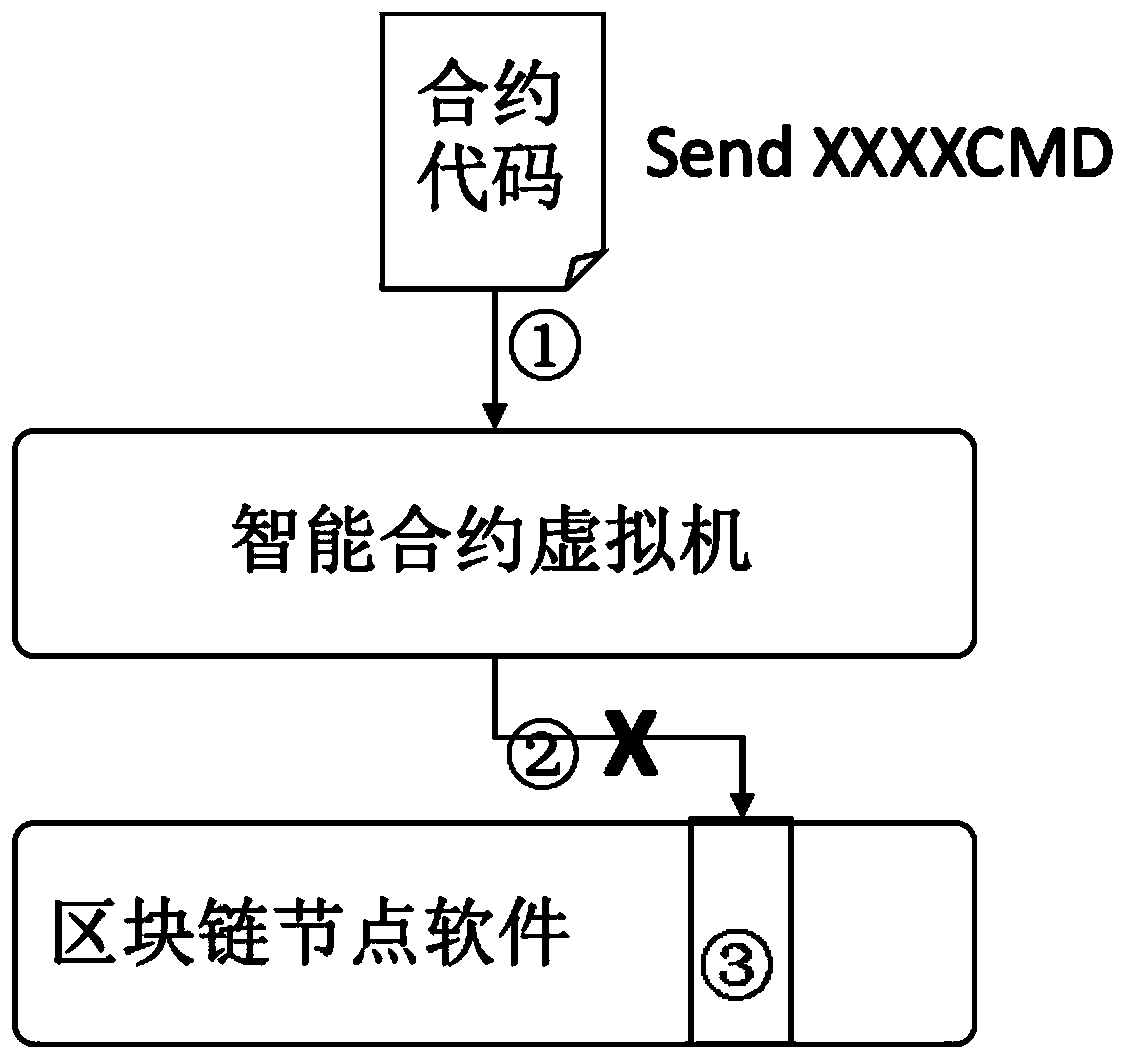
[0036] Embodiment 2: On the basis of Embodiment 1: it also includes the contract verification node process, the specific steps are as follows: 1) After receiving the broadcasted contract return transaction, start the contract virtual machine to execute the contract verification process; 2) The virtual machine executes the contract code, Execute to the line where the transparent transmission command is required, and call the transparent transmission channel command to pass in the interface. Since it is a contract verification process, the virtual machine does not pass the transparent transmission command downward; 3) The virtual machine continues to execute other codes of the contract for contract verification; 4) After the contract is fully verified successfully, it will be added to the package and continue to verify other transactions.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com