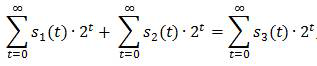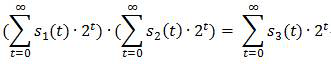Unified identity authentication method based on block chain
A technology of identity authentication and blockchain, which is applied in the transmission system, digital transmission system, encryption device with shift register/memory, etc., can solve the problems of lack of guarantee of transaction security and leakage of user identity information, and achieve the goal of solving the problem of encryption The effect of key distribution, ensuring continuity, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
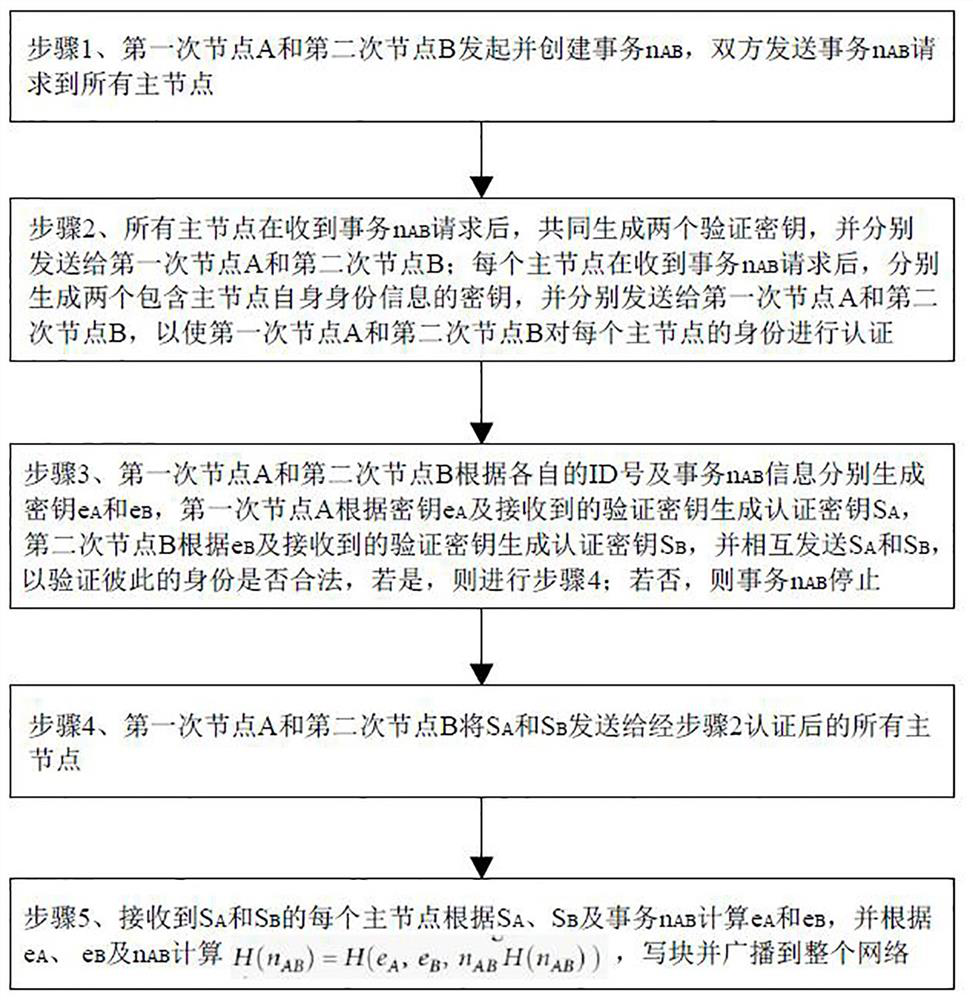
[0026] A unified identity authentication method based on the block chain, the block chain includes a primary node (kgc) and the secondary node, the main node is equivalent to the miners in the block chain, the secondary node is the user in the block chain, when two Before the user is transaction, it is necessary to effectively and reliably verify each other, and it is not possible to disclose your identity. In order to realize the security and confidentiality of the identity authentication of the transaction in the block chain, it provides the following methods:
[0027] Step 1, the first node A and the second node B initiate and create a transaction N AB (Ie the transaction information required between A and B), both sides verify the transaction N AB The legality (including the price of the transaction), after the certification of both parties, bo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com