APT attack behavior analysis and detection method and device based on cascade attack chain model
A technology of behavior analysis and detection methods, applied in the field of network security, to achieve the effect of lowering the threshold of requirements, simplifying the complexity of analysis, and making up for the excessive dependence on manual analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] In order to make the purpose, technical solution and advantages of the present invention more clear and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions.
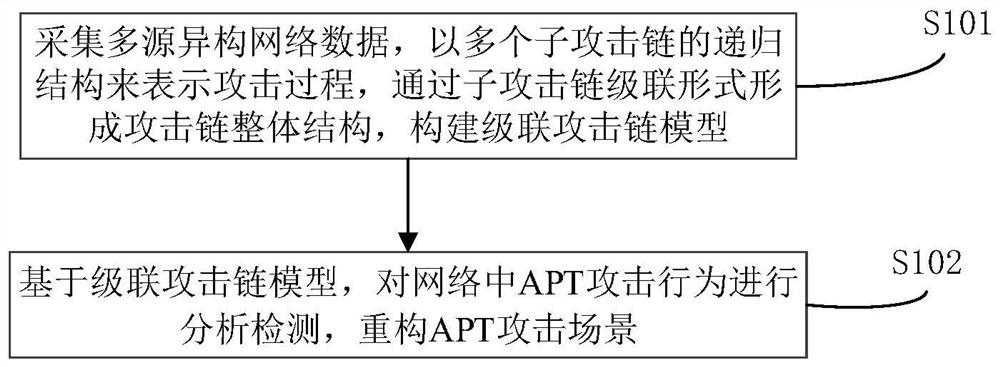
[0033] In view of the fact that the detection model in the existing network attack detection is difficult to meet the analysis of attack behavior requirements and is inconvenient for actual application, in the embodiments of the present invention, see figure 1 As shown, an APT attack behavior analysis and detection method based on the cascade attack chain model is provided, including the following content:
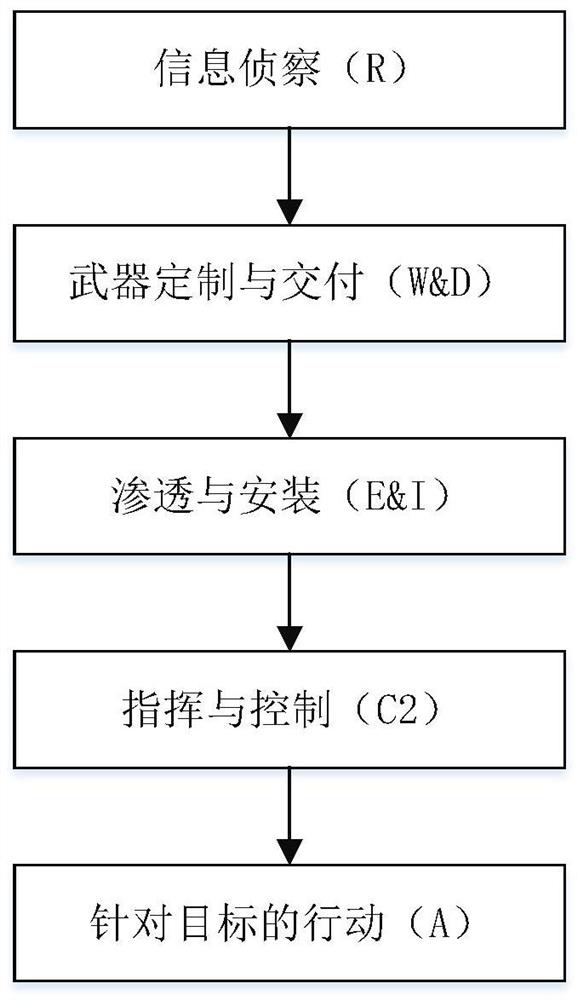
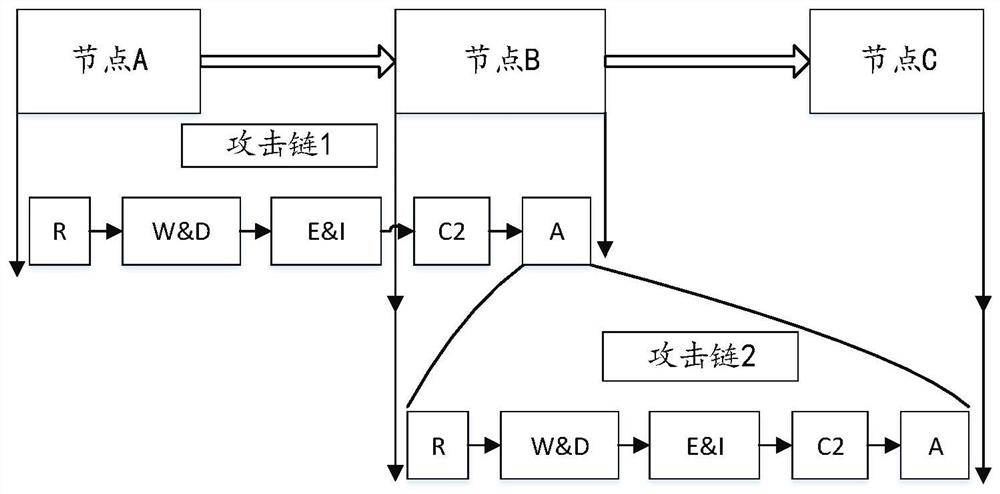
[0034] S101) Collect multi-source heterogeneous network data, represent the attack process with a recursive structure of multiple sub-attack chains, form the overall structure of the attack chain through the cascading form of the sub-attack chains, and build a cascaded attack chain model;
[0035] S102) Based on t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com