Encrypted gallery management system and implementation method thereof
A technology of management system and implementation method, applied in the field of encrypted gallery management system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
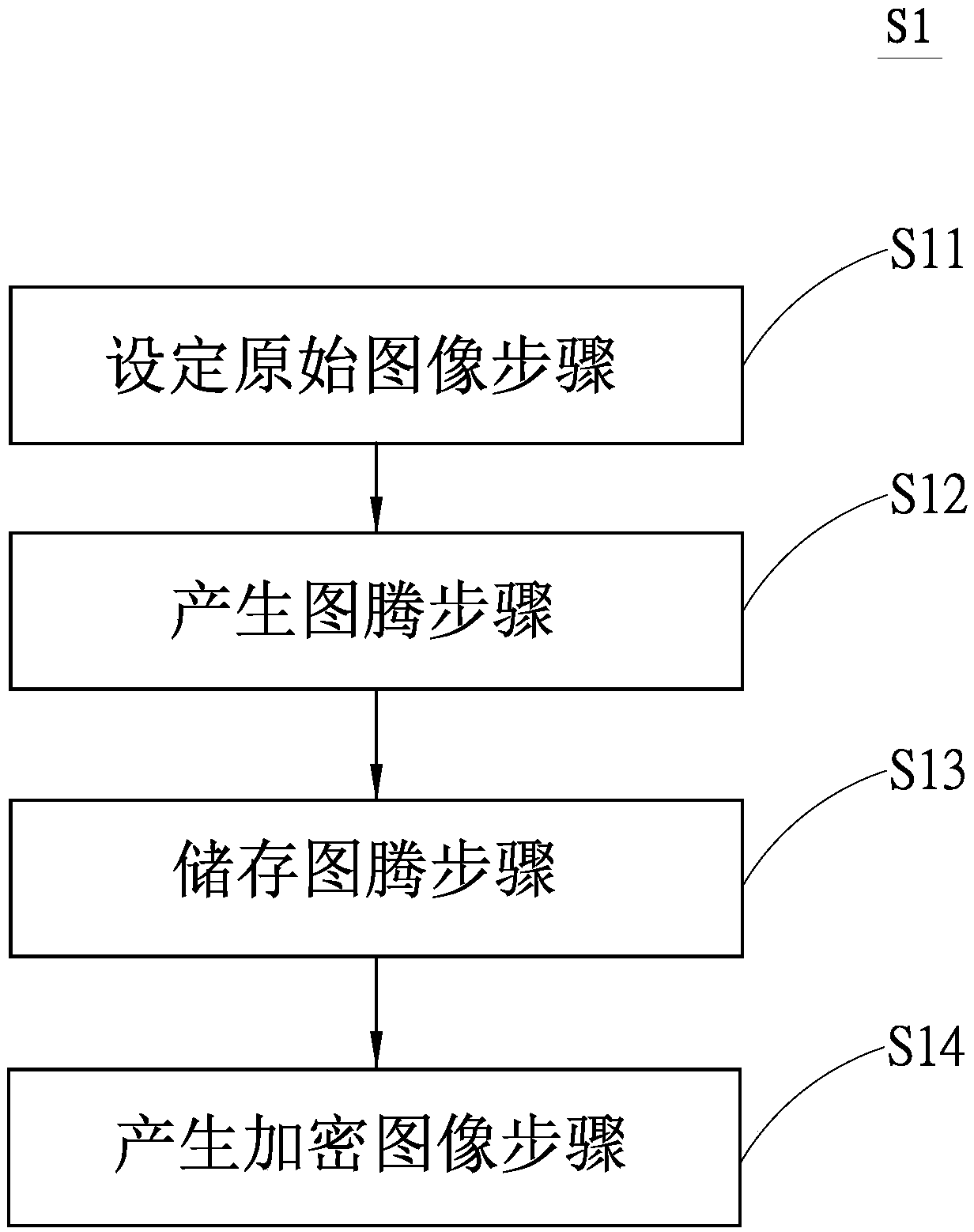
Embodiment approach S2
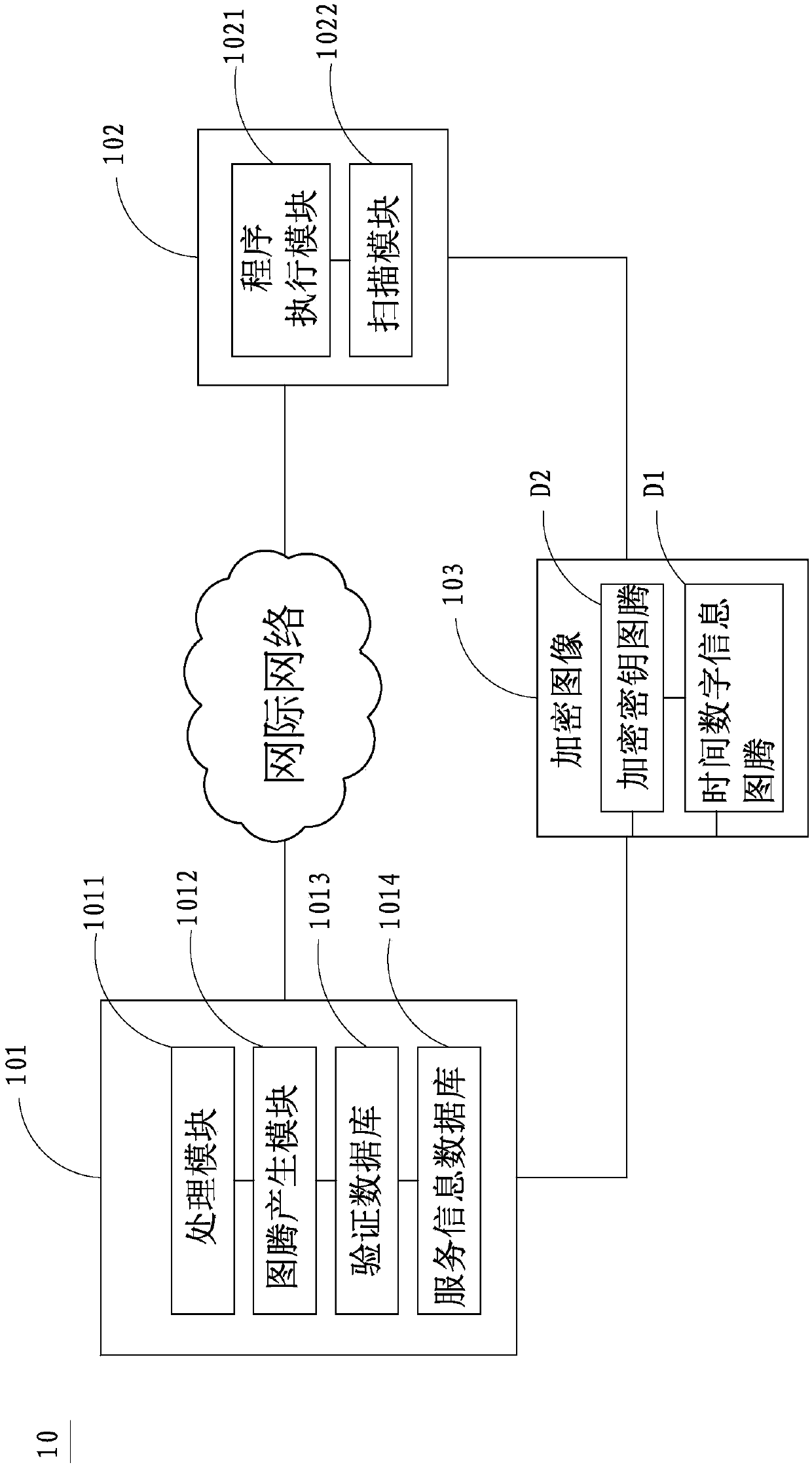
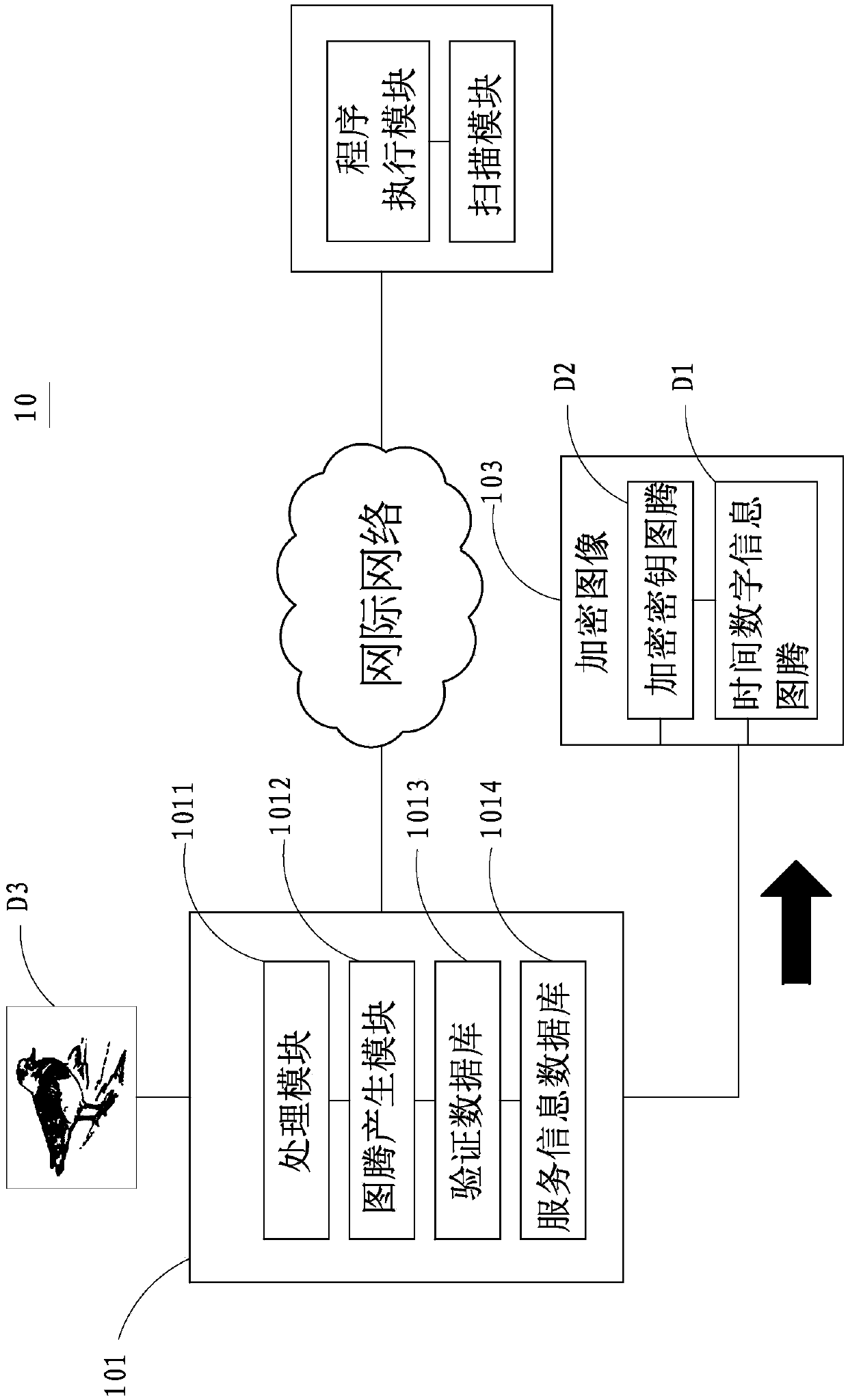
[0057] see Figure 4 , shown in the figure is the implementation flowchart of the present invention, and please refer to Figure 5~Figure 6 , shown in the figure is the implementation schematic diagram (two)~(three) of the present invention, as shown in the figure, the implementation method S2 of the encrypted gallery management system of the present invention, as follows:
[0058] (1) Scan encrypted image Step S21: After an information device 102 scans an encrypted image 103 with its scanning module 1022, a program execution module 1021 of the information device 102 analyzes the obtained encrypted image 103 to obtain a time number Information totem D1, and an encryption key totem D2;
[0059] (2) Return the totem step S22: the information device 102 transmits the time digital information totem D1 and the encryption key totem D2 to the management server 101, wherein the information device 102 can pass the time through an Internet or a short-distance transmission technology. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com