Third-party authorized login method and device
A login method and login request technology, applied in the communication field, can solve the problems of poor scalability and achieve fast access and strong scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
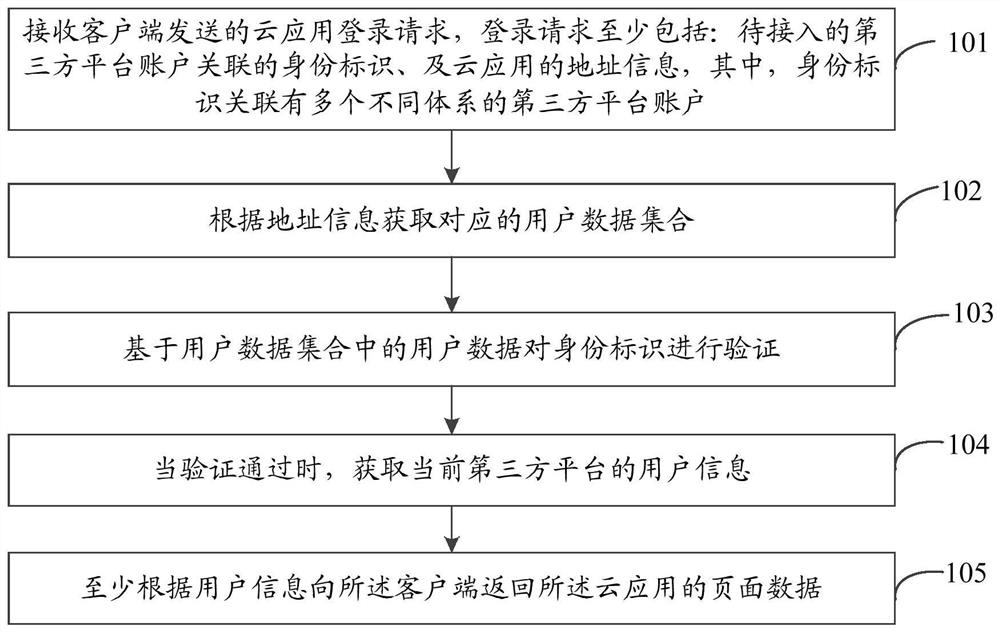
[0032] The following will clearly and completely describe the technical solutions in the embodiments of the application with reference to the drawings in the embodiments of the application. Apparently, the described embodiments are only some of the embodiments of the application, not all of them. Based on the embodiments in this application, all other embodiments obtained by those skilled in the art without making creative efforts belong to the scope of protection of this application.
[0033] Embodiments of the present application provide a third-party authorized login method and device, which can improve the accuracy of video risk assessment and the efficiency of video review and release. Each will be described in detail below. It should be noted that the sequence of the following embodiments is not intended to limit the preferred sequence of the embodiments.
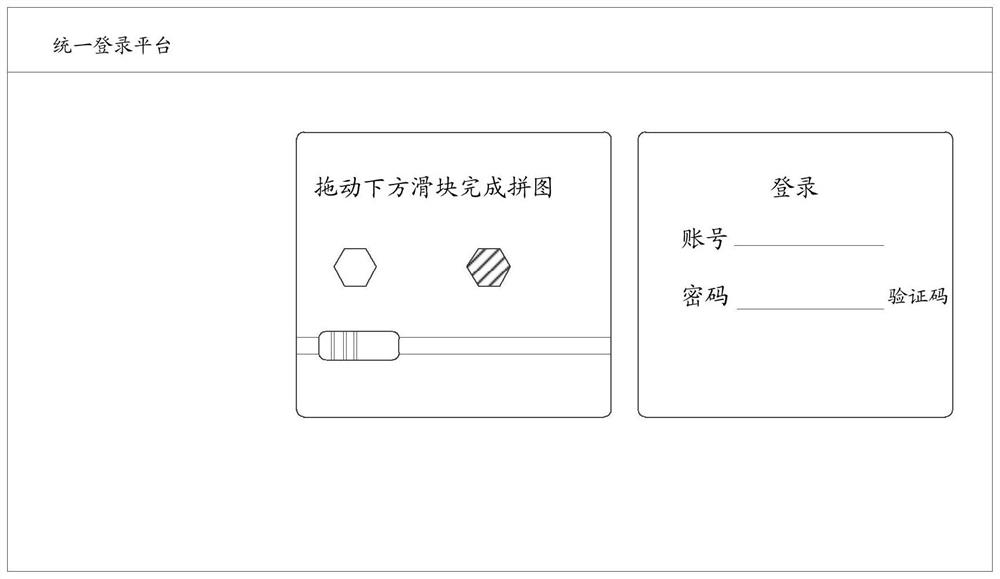
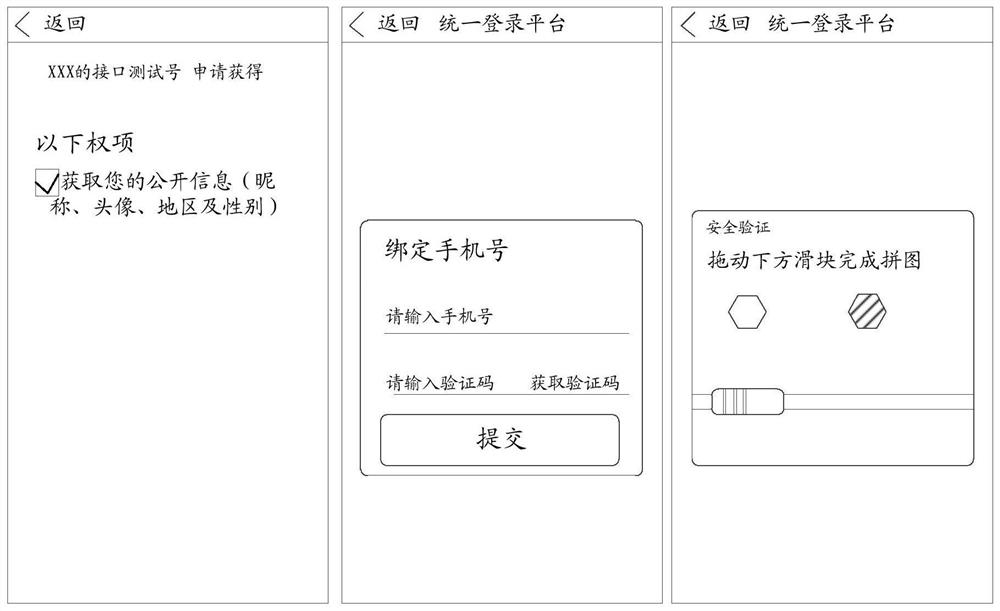
[0034] In one embodiment, description will be made from the perspective that the third-party authorization login d...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap