Financial management method with remote access function
A technology of financial management and remote access, applied in communication between programs, program control design, data processing applications, etc., can solve problems such as inconvenience and event troubles, and achieve the effects of accurate identity determination, data security, and data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
[0036] Example 1
[0037] This embodiment provides a financial management method with remote access function, and realizes the present invention through basic necessary technical features, so as to solve the problems raised in the technical background part of this application document.
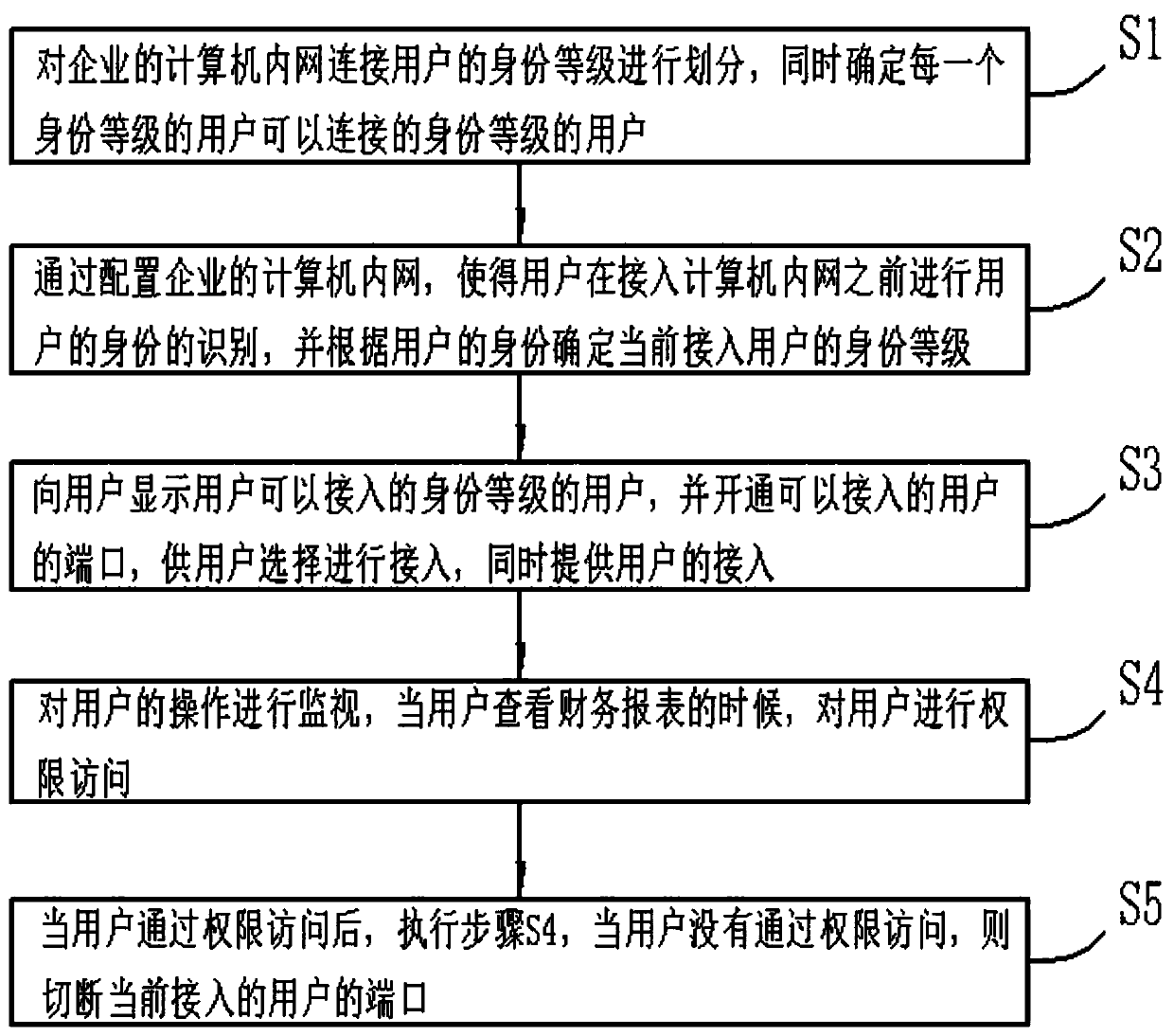
[0038] Specific, such as figure 1 As shown, the embodiment of the present invention provides a financial management method with remote access function, including the following steps:
[0039] S1: Divide the identity levels of users connected to the company's computer intranet, and determine the identity levels that users of each identity level can connect to;
[0040] For example, for users at the financial director level, users of all employee levels in the financial department can be connected, while the employee level cannot connect to users of any level. The users that can be connected to a specific user level are set by those skilled in the art according to the needs of each company. set.
[0041]...
Example Embodiment
[0049] Example 2
[0050] This example is based on Example 1 and optimizes the implementation in Example 1, so that this example is more stable and has better performance during operation, but it is not limited to the one described in this example. Implementation mode.
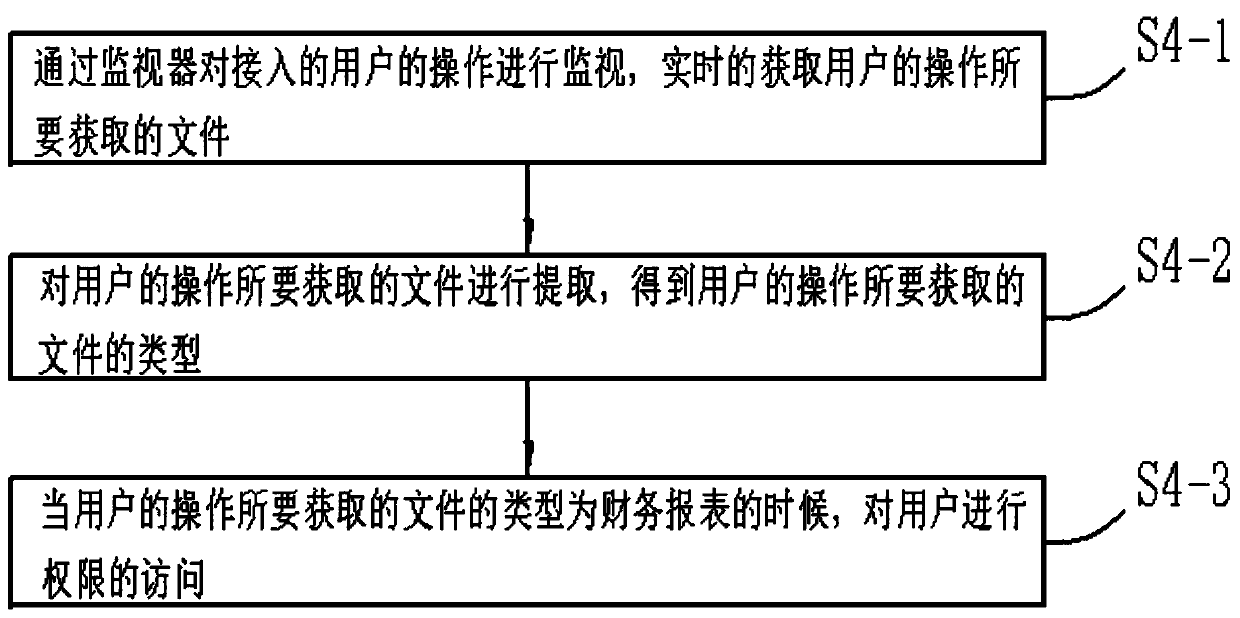
[0051] Specifically, in step S4, the following steps are included:
[0052] S4-1: Monitor the operation of the accessed user through the monitor, and obtain the files required by the user's operation in real time;
[0053] The server monitors the user's operation through a built-in monitor, and when the user selects a file, the server obtains file information from the accessed user.
[0054] S4-2: Extract the file to be obtained by the user's operation, and obtain the type of the file to be obtained by the user's operation;
[0055] The server extracts the acquired file, that is, extracts the suffix of the file, converts the format of the file according to the suffix of the file, and finally extracts the keyword of the ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap