Internet of Things access method and device
An access method and access device technology, applied in the data field, can solve problems such as inability to guarantee data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
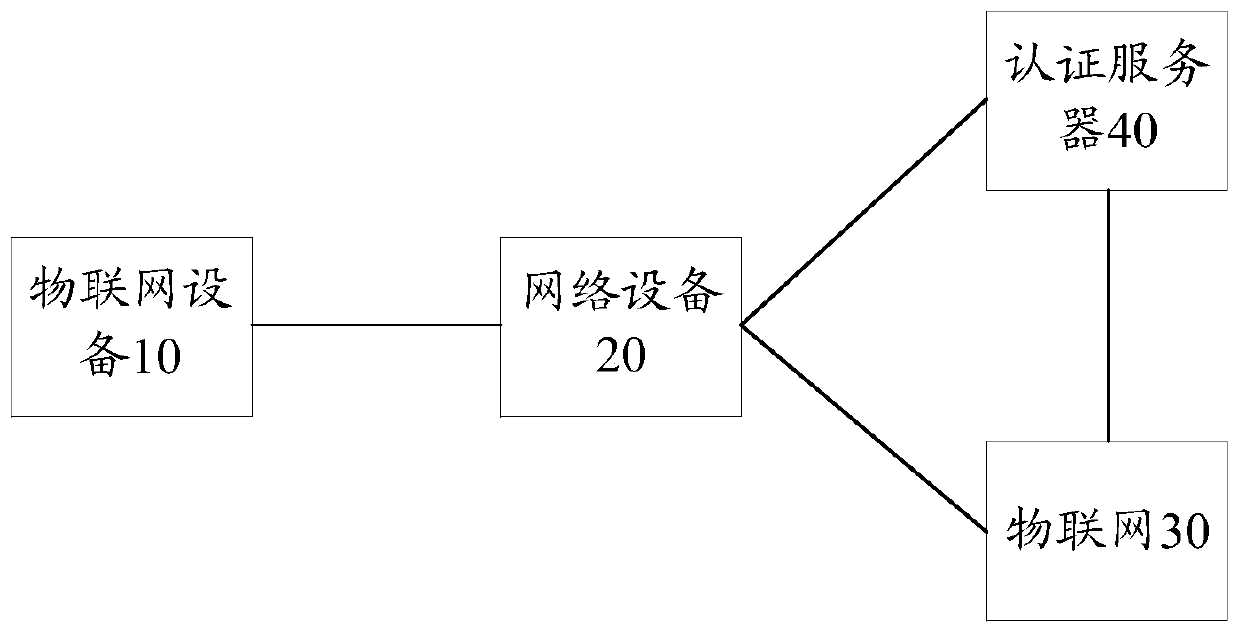
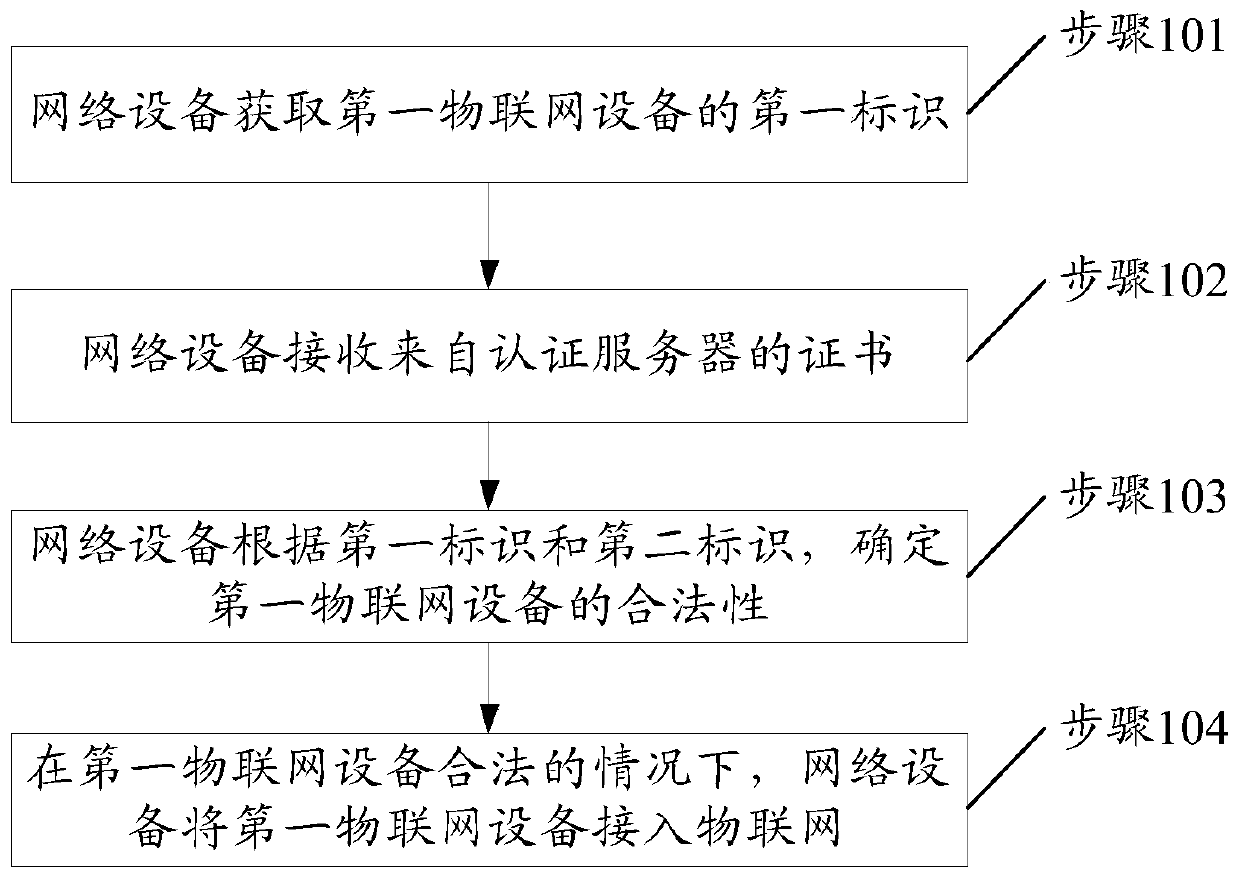
[0059] In a possible embodiment, based on figure 2 In the communication system shown, in the case where the network device is a gateway device connected to the first IoT device, such as Figure 4 As shown, step 101 can be implemented through the following steps 201-202.
[0060] Step 201, the first IoT device sends an access request to the gateway device. Correspondingly, the network device receives the access request from the first IoT device.
[0061] Wherein, the access request includes the first identifier.
[0062] The gateway device stores multiple communication protocols, such as wired protocols and wireless protocols. Wherein, the wired protocol may include 485, 232 and other protocols. Wireless protocols can include WIFI, Lora, NB-IOT, Zigbee, DL / T 645, CJ / T188, Modbus RT U and other protocols. After the gateway device 20 is connected to the device 10, it can perform data interaction with the device 10 through the above-mentioned communication protocol, so as to...
Embodiment 2
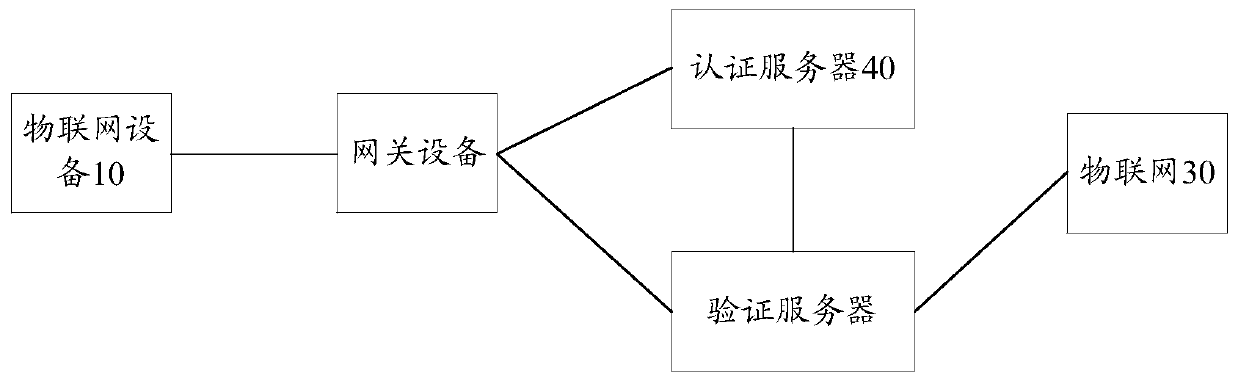
[0090] In a possible embodiment, based on figure 2 In the communication system shown, in the case where the network device is an authentication server, such as Figure 5 As shown, step 101 can be implemented through the following steps 301 and 302.
[0091] Step 301, the verification server receives the first information sent by the gateway device.
[0092] Wherein, the first information is obtained by the gateway device encrypting the first identifier by using a second preset encryption algorithm after receiving the access request sent by the first IoT device. The access request includes a first identification. The access request is used to identify that the first IoT device needs to access the IoT.
[0093] It should be noted that, in step 301, the interaction process between the gateway device and the verification server can refer to step 1 and step 2 for details:
[0094] Step 1. The gateway device receives an access request from the first IoT device.
[0095] Step 2...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap