Registration method and device, and authentication method and device
An authentication method and user authentication technology, applied in the field of computing and authentication, which can solve the problems of difficulty in taking into account user experience and security, poor security, and high environmental requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
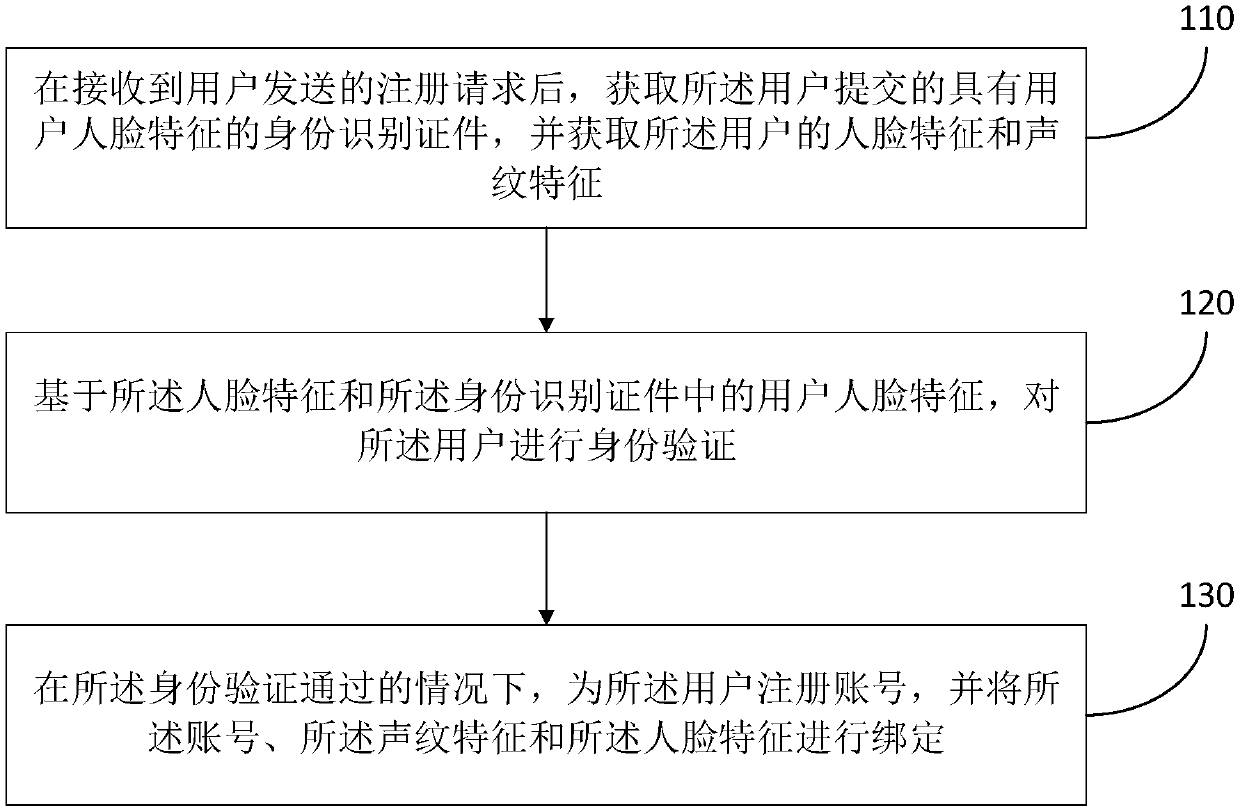
[0098] This embodiment discloses a registration method, which is applicable to scenarios requiring user registration and authentication, for example, the method is applicable to identity authentication of drivers or passengers on a taxi-hailing application platform. Specifically, as figure 1 As described, the registration method of this embodiment includes the following steps:
[0099] S110. After receiving the registration request sent by the user, obtain the identification certificate submitted by the user with the user's facial features, and obtain the user's facial features and voiceprint features.
[0100] The aforementioned identification certificate is a certificate used to identify the identity of the user, for example, the identification certificate may be the user's ID card, driver's license, or passport. The aforementioned face features and voiceprint features are feature data acquired in real time.
[0101] The aforementioned facial features and voiceprint featur...
Embodiment 2
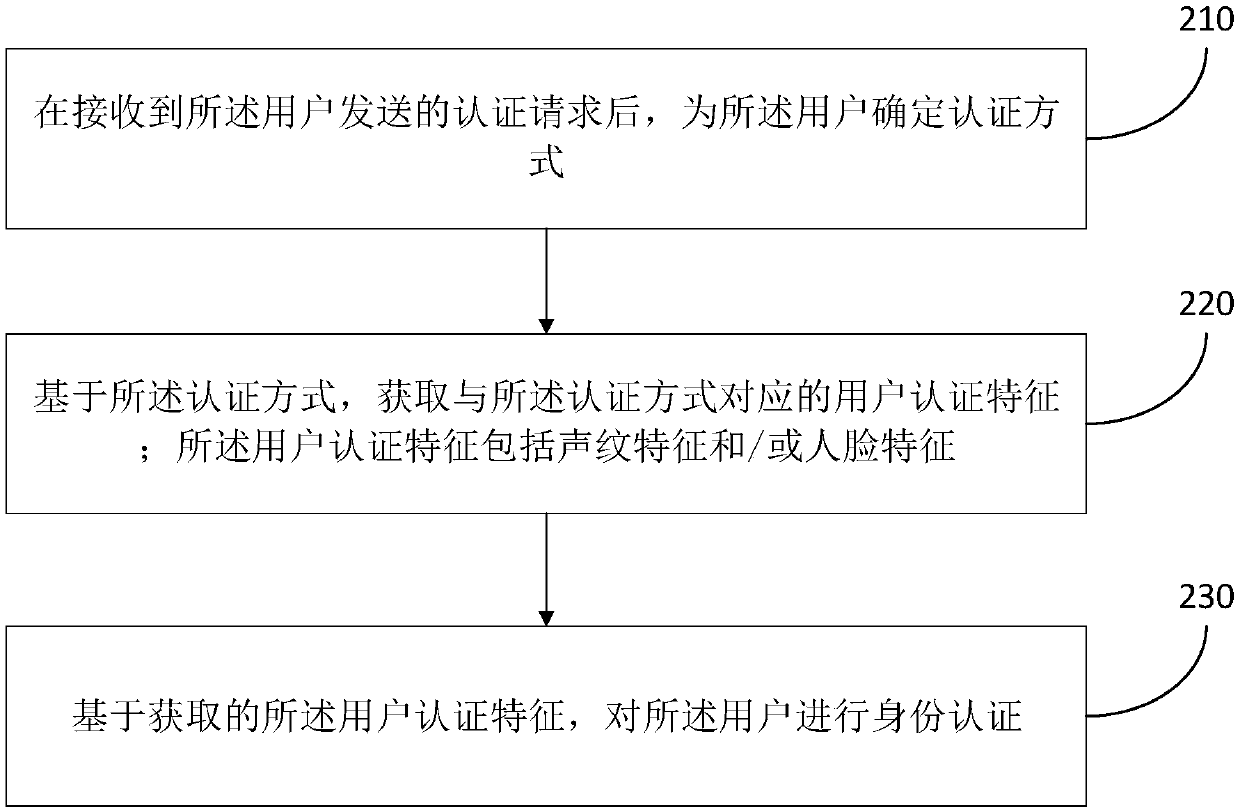
[0114] This embodiment discloses a registration method, which is executed after the user registration in Embodiment 1 is completed, and is used for user authentication. Specifically, such as figure 2 As described, the registration method of this embodiment includes the following steps:
[0115] S210. After receiving the authentication request sent by the user, determine an authentication mode for the user.
[0116] The above authentication methods include the following: the first authentication method using the pre-stored voiceprint features for authentication, the second authentication method using the pre-stored voiceprint features and facial features for authentication, and the pre-stored facial features. The third authentication method for authentication.
[0117] It can be seen from Embodiment 1 that the pre-stored facial features include the first facial features of the user when performing a predetermined action, and the second facial features of the user when making...
Embodiment 3
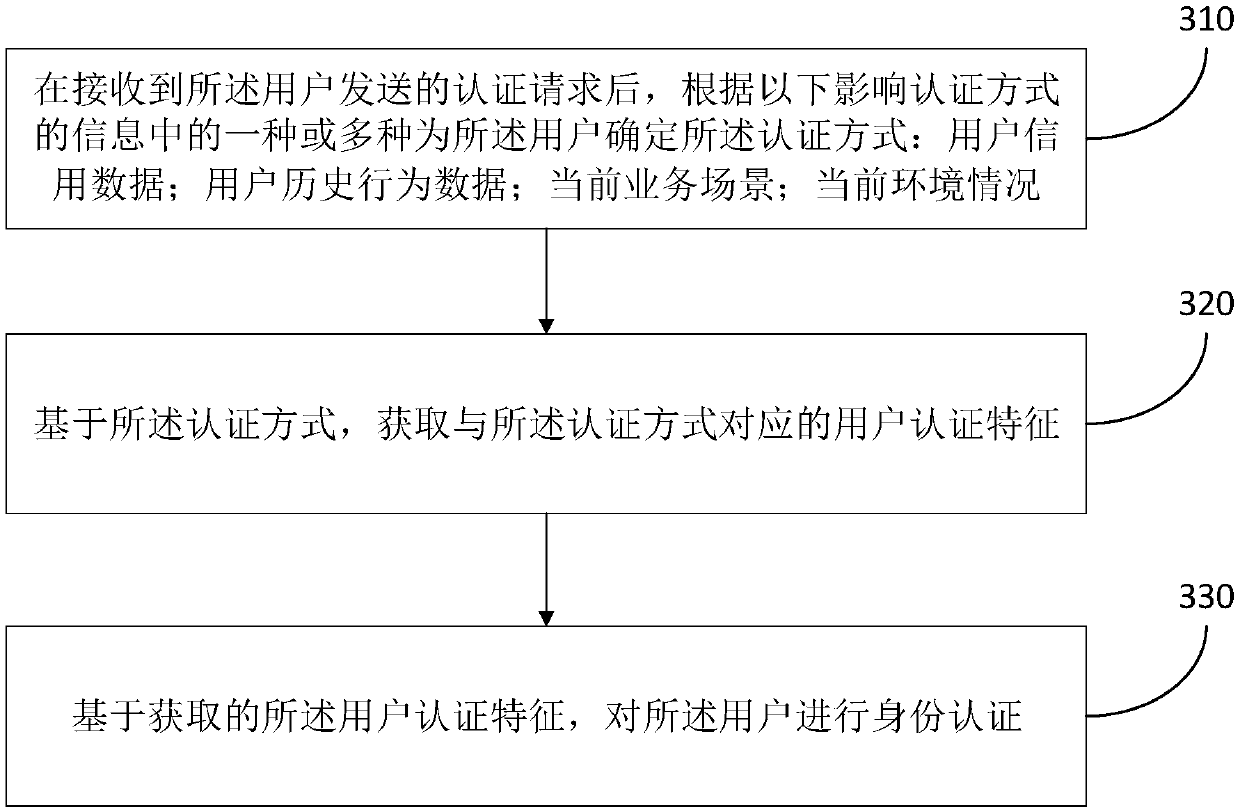
[0127] This embodiment discloses a registration method. On the basis of the above two embodiments, the method discloses a specific implementation scheme for determining an authentication mode. Specifically, such as image 3 As described, the registration method of this embodiment includes the following steps:
[0128] S310. After receiving the authentication request sent by the user, determine the authentication method for the user according to one or more of the following information affecting the authentication method: user credit data; user historical behavior data; current business scenario ;Current environmental conditions.
[0129] The above-mentioned user credit data may include third-party credit data such as Zhima Credit of the user. The above-mentioned user historical behavior data may include user complaint data and complaint data, especially the user's serious or continuous complaint data. In addition, when the method of this embodiment is applied to the taxi-ha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com