Method and device for protecting mobile storage equipment, equipment and storage medium
A mobile storage device and protection status technology, applied in the direction of internal/peripheral computer component protection, etc., can solve problems such as file outflow, computer blue screen, kernel compatibility issues, etc., and achieve the effect of reducing the probability of blue screen and low impact on system performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
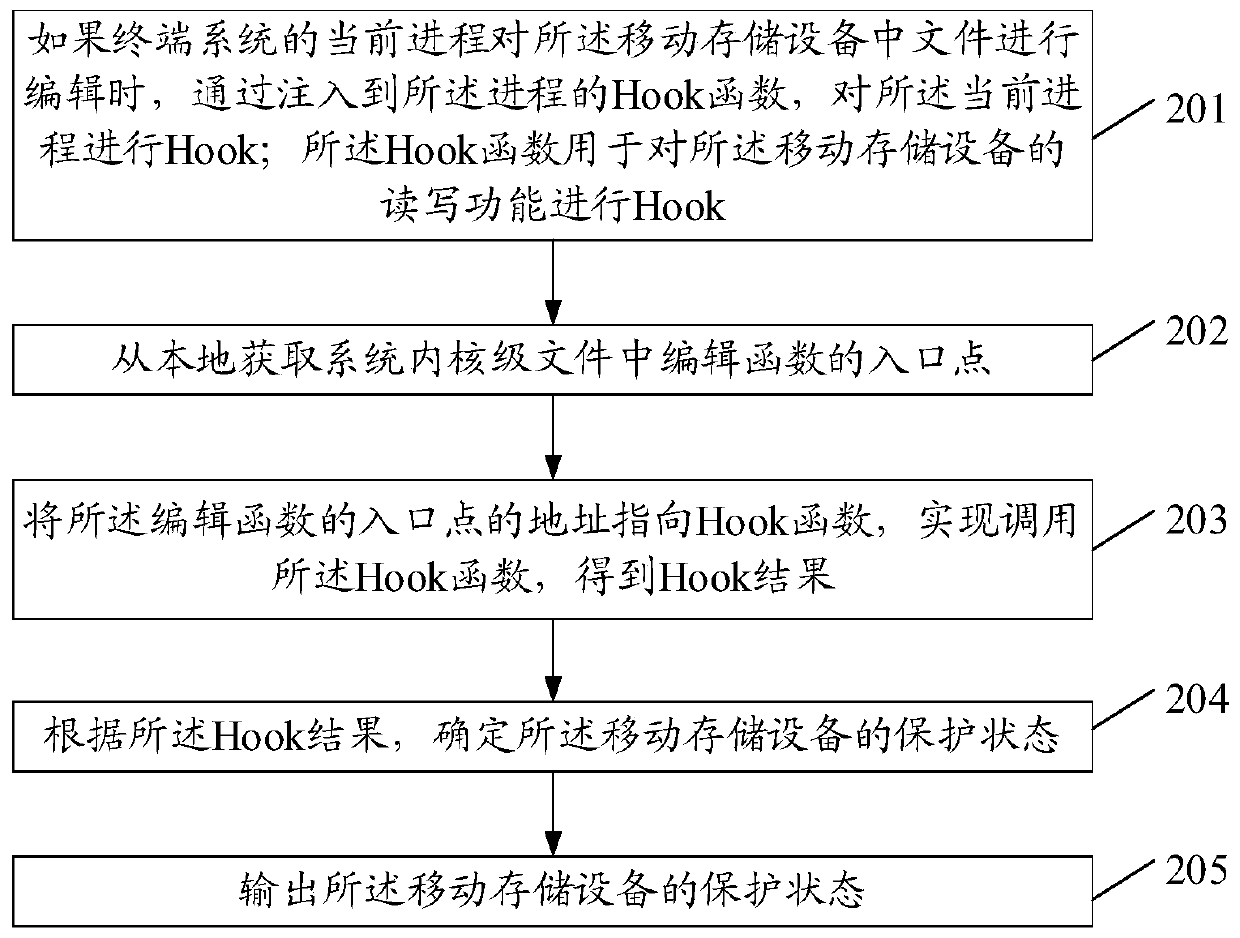
Image
Examples
Embodiment Construction
[0031] The technical solution of the present application will be further described in detail below in conjunction with the accompanying drawings and embodiments.
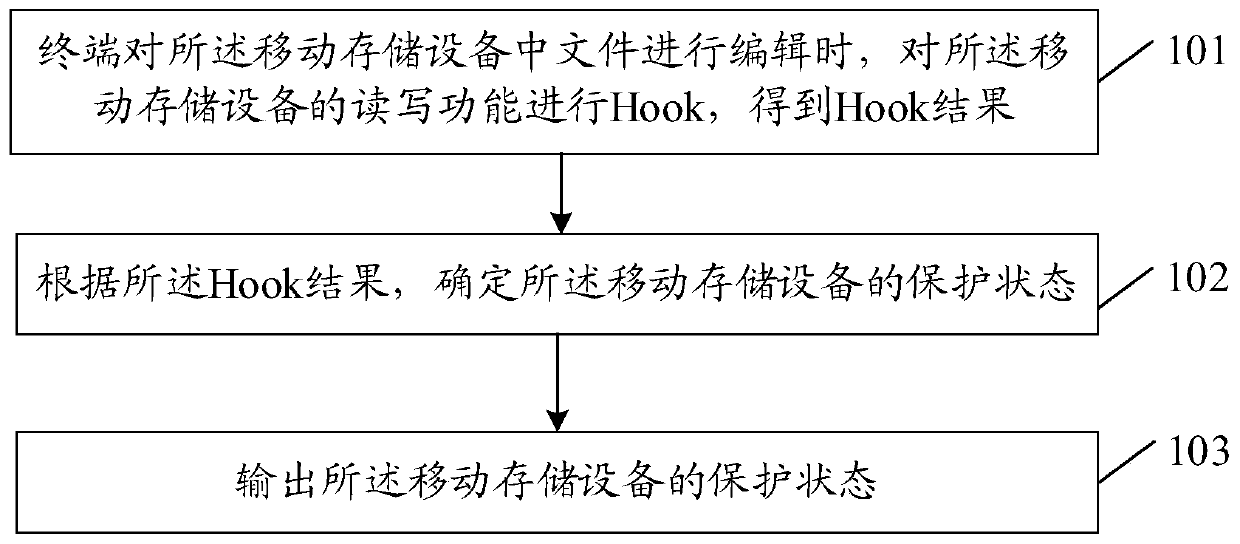
[0032] An embodiment of the present application provides a method for protecting a mobile storage device, the operation method is applied to a terminal, figure 1 It is a schematic diagram of the implementation flow of a method for protecting a mobile storage device according to an embodiment of the present application, as shown in figure 1 As shown, the method includes:
[0033] Step 101: When the terminal edits the file in the mobile storage device, hook the read and write functions of the mobile storage device to obtain a hook result;
[0034] Here, the terminal is an electronic device capable of editing files in a mobile storage device, and the electronic device may include a notebook computer, a desktop computer, and the like. The mobile storage device is a device that can move all storable types of data betwe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com