Isolation attack method and system for distributed virtual network
A virtual network and distributed technology, applied in the field of isolated attack methods and systems for distributed virtual networks, can solve problems such as massive network structure prediction attacks, lack of dynamic deployment security protection strategies, and lack of control methods for traffic data.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
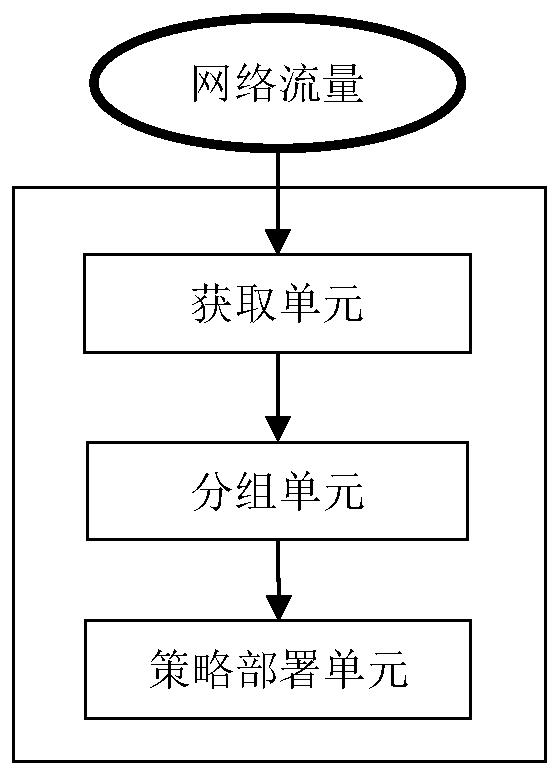
Image
Examples
Embodiment Construction
[0042] The preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings, so that the advantages and features of the present invention can be more easily understood by those skilled in the art, and the protection scope of the present invention can be more clearly defined.
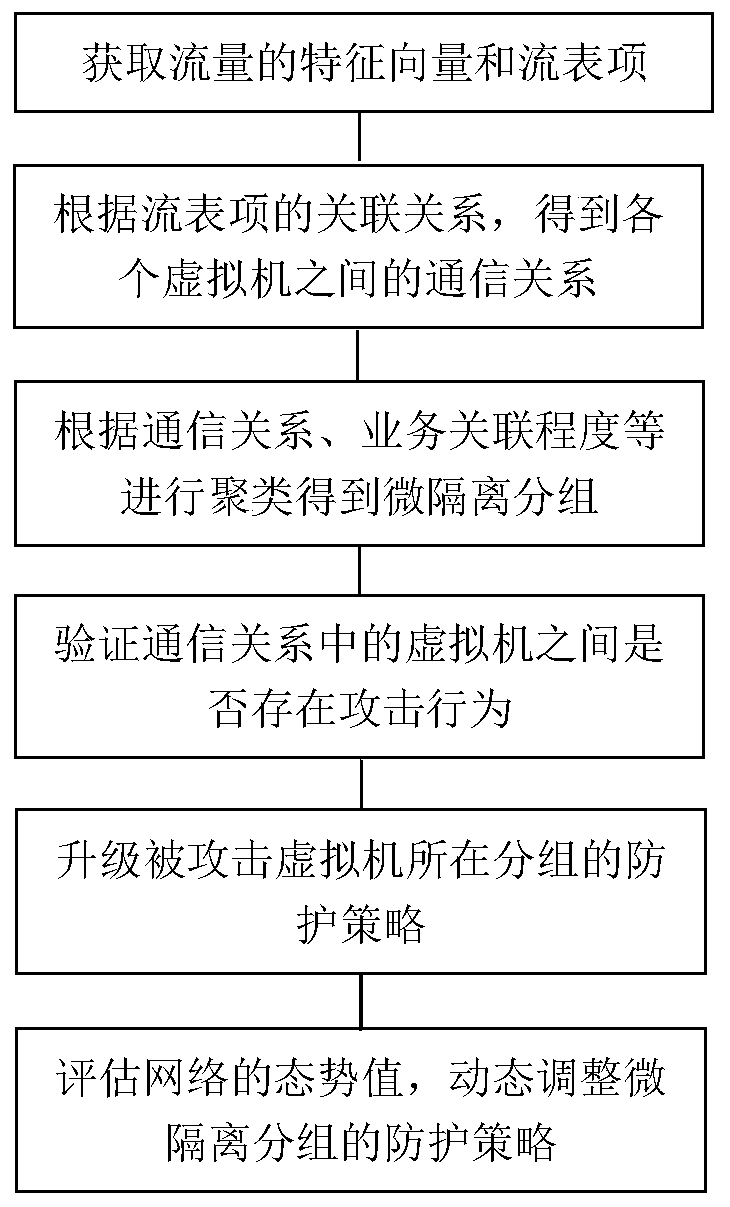
[0043] figure 1 A flow chart of the method for isolating attacks of a distributed virtual network provided by this application, the method comprising:
[0044] Obtain traffic data in the distributed virtual network, use the OpenFlow protocol to collect traffic statistics, analyze and extract feature vectors and flow entries in the traffic data, and obtain each virtual machine in the distributed virtual network according to the association relationship of the flow entries communication relationship;
[0045] Before obtaining the communication relationship of each virtual machine in the distributed virtual network, it also includes obtaining all ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com